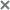Kaspersky Anti Targeted Attack Platform Interface
The application is managed through the web interface. Sections of the application web interface differ depending on the role of the user: Administrator or Senior security officer (Senior security officer, Security officer, Security auditor).
The window of the application web interface contains the following:
- Sections in the left part and in the lower part of the application web interface window.
- Tabs in the upper part of the application web interface window for certain sections of the application.
- The workspace in the lower part of the application web interface window.
Sections of the application web interface window
The application web interface provides the following sections for users with the Senior security officer, Security officer, and Security auditor roles:
- Dashboard. Contains Kaspersky Anti Targeted Attack Platform Monitoring data.
For users with the Security auditor role, the Dashboard window contains the following sections: Alerts, System health.
- Alerts. Contains information about alerts in the network of the tenant to which you have access.
- Network traffic events. Information about events and aggregate events in network traffic.
- Threat Hunting. Contains information about events found on hosts of the tenant to which you have access.
- Tasks. Contains information about tasks that you can use to manage files and application on hosts.
- Prevention. Contains information about policies that you can use to manage preventions of files running on selected hosts.
- Custom rules: TAA, Intrusion detection, IOC, YARA, Sandbox. Contains information for managing user-defined rules.
- Storage: Files, and Quarantine. Contains information for managing objects in quarantine and Storage.
- Assets. Contains information about computers with the Kaspersky Endpoint Agent component and their settings.
- Network map: Network interactions map, Topology map, Network sessions. Contains information about the interaction of devices at different periods of time, diagrams of physical connections of devices in the network and information about network sessions.
- Risks and anomalies. Contains information about the risks to which the resources of the information system are exposed.
- Reports: Generated reports and Templates. Contains a report builder and a list of generated reports about alerts.
- Logs: Application messages. Contains information about application performance.
- Settings: Connectors, Secrets, IOC scanning schedule, Endpoint Agents, KPSN reputation database, Notification rules, VIP status, Exclusions, Allow rules, Sandbox servers, Passwords for archives, and License. Contains information about connector settings, secrets, the IOC scan schedule, Endpoint Agent component settings, and the settings for publishing objects in KPSN and assigning the VIP status to alerts based on information contained in alerts, the list of allowed objects, and IDS, TAA (IOA), and ICAP rules excluded from scanning, passwords of archives, and added keys.
For users with the Security auditor role, the web interface of the application contains the following sections in addition to those listed above:
- Operating mode. Contains information about PCN and SCN servers and about tenants in distributed solution and multitenancy mode.
- Sensor servers. Contains information about Central Node components and Sensor components connected to them.
- Sandbox servers. Contains information about the connection of the Central Node component to Sandbox components.
- External systems. Contains information about application integration with mail sensors.
- Server configuration. Contains information about the sizing parameters of the application.
Workspace of the application web interface window
The workspace displays the information you choose to view in the sections and on the tabs of the application web interface window. It also contains control elements that you can use to configure how the information is displayed.