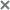Operating principle of the application
The Kaspersky Anti Targeted Attack Platform application includes three functional blocks:
- Kaspersky Anti Targeted Attack (hereinafter also referred to as "KATA"), which detects threats on the perimeter of the enterprise IT infrastructure.
- Kaspersky Endpoint Detection and Response (hereinafter also referred to as "KEDR"), which provides protection for the local area network of the organization.
- Network Detection and Response (hereinafter also referred to as "NDR"), which provides protection of the corporate LAN.
You can use the full functionality of the application (KATA + NDR key and KEDR key) or partial functionality (only KATA/KATA + NDR key or only KEDR key).
Principle of operation of Kaspersky Anti Targeted Attack
Kaspersky Anti Targeted Attack includes the following components:
- Sensor.
- Central Node.
- Sandbox.
Sensor, Central Node and Sandbox interoperate as follows:
- The Sensor component receives mirrored SPAN, ERSPAN, RSPAN traffic, objects and metadata of HTTP, FTP, SMTP, and DNS protocols, HTTP and FTP traffic data, as well as HTTPS traffic data (if the administrator has configured SSL certificate replacement on the proxy server), copies of email messages, and does the following with the gathered data:
- Scans Internet traffic for signs of intrusion into the corporate IT infrastructure using the Intrusion Detection System technology (hereinafter also referred to as IDS).
IDS technology can recognize and detect network activity in 80 protocols, particularly in 53 application layer protocols of the TCP/IP model, detecting suspicious traffic and network attacks. Supported protocols include TCP, UDP, FTP, TFTP, SSH, SMTP, SMB, CIF, SSL, HTTP, HTTP/2, HTTPS, TLS, ICMPv4, ICMPv6, IPv4, IPv6, IRC, LDAP, NFS, DNS, RDP, DCERPC, MS-RPC, WebSocket, Citrix and others.
- Checks the reputation of files and URLs against the Kaspersky Security Network database (hereinafter also referred to as "KSN") or Kaspersky Private Security Network (hereinafter also referred to as "KPSN").
- Sends objects and files to be scanned by the Central Node component.
You can also use a mail sensor as a Sensor component, which is a server or virtual machine on which Kaspersky Secure Mail Gateway (KSMG) or Kaspersky Security for Linux Mail Server (KLMS) is installed.
- Scans Internet traffic for signs of intrusion into the corporate IT infrastructure using the Intrusion Detection System technology (hereinafter also referred to as IDS).
- The Central Node component scans files and objects using anti-virus databases, YARA rule databases created by Kaspersky Anti Targeted Attack users, and if necessary, sends files and objects to be scanned by the Sandbox component.
- The Sandbox component analyzes the behavior of objects in virtual operating systems to detect malicious activity and signs of targeted attacks on corporate IT infrastructure, and sends scan results to the Central Node server.
If any threats are detected, the Central Node server records relevant information in the alert database. You can view the alert table in the Alerts section of the application web interface or by generating an alert report.
Alert information can also be published to a SIEM system that is used in your organization, as well as external systems. Information on Sandbox component alerts can be published in the local reputation database of Kaspersky Private Security Network.
Principle of operation of Kaspersky Endpoint Detection and Response
Kaspersky Endpoint Detection and Response includes the following components:
- Central Node.
- Endpoint Agent.
The component may be represented by any of the following applications: Kaspersky Endpoint Agent for Windows, Kaspersky Endpoint Security for Windows, Kaspersky Endpoint Security for Linux, Kaspersky Endpoint Security for Mac.
- Sandbox.
Optional component.
The Sensor component can be used as a proxy server for outgoing connections from Kaspersky Endpoint Agent.
The Endpoint Agent and Central Node components interoperate as follows:
One of the applications that represents the Endpoint Agent component is installed on individual computers within the corporate IT infrastructure and continuously monitors processes, open network connections, and files being modified. The monitoring data are sent to the Central Node server. Events are generated based on these data.
- Kaspersky Endpoint Agent for Windows transmits data about the following events to the Central Node server: Process started, Process terminated, Module loaded, Connection to remote host, Blocked application (prevention rule), Document blocked, File changed, System event log, Registry modified, Port listened, Driver loaded, Process: interpreted file run, Process: console interactive input, Detection, Detection processing result, AMSI scan.
- Kaspersky Endpoint Security for Windows transmits data about the following events to the Central Node server: Process started, Process terminated, Module loaded, Connection to remote host, Blocked application (prevention rule), Document blocked, File changed, System event log, Registry modified, Port listened, Driver loaded, Process: interpreted file run, Process: console interactive input, Detection, Detection processing result, AMSI scan, DNS, Code injection, Named pipe, WMI, LDAP.
- Kaspersky Endpoint Security for Linux transmits data about the following events to the Central Node server: Process started, Process terminated, Blocked application (prevention rule), Document blocked, File changed, System event log, Detection, Detection processing result, Code injection, DNS.
- Kaspersky Endpoint Security for Mac transmits data about the following events to the Central Node server: Process started, Process terminated, File changed, Detection, Detection processing result.
Endpoint Agent for the NDR functionality connects separately and does not send observation information to the Central Node server.
The Kaspersky Endpoint Agent for Windows can be integrated with Endpoint Protection Platform (hereinafter also "EPP") applications:
- Kaspersky Endpoint Security for Windows.
- Kaspersky Security for Windows Server.
- Kaspersky Security for Virtualization Light Agent for Windows.
Information about compatibility of Kaspersky Endpoint Agent for Windows versions with EPP applications is provided in the Compatibility of Kaspersky Endpoint Agent for Windows versions with EPP applications section.
In this case, Kaspersky Endpoint Agent also sends information about threats detected by the EPP applications and results of threat processing by these applications to the Central Node server.
EPP applications, Kaspersky Endpoint Agent, and Central Node components interoperate as follows:
- EPP applications send information about detected threats and results of threat processing to Kaspersky Endpoint Agent.
Kaspersky Endpoint Security for Windows can also supply Kaspersky Endpoint Agent for Windows with information about third-party applications with Antimalware Scan Interface support (hereinafter also referred to as "AMSI") sending objects (for example, PowerShell scripts) to Kaspersky Endpoint Security for Windows for additional scanning.
- Kaspersky Endpoint Agent sends data gathered while monitoring processes, open network connections, and files being modified, as well as data received from EPP applications, to the Central Node server.
The Central Node server processes received data and displays the corresponding events in the application web interface.
EPP application data processing generates Detection, Detection processing result, AMSI scan events (when Kaspersky Endpoint Agent for Windows is integrated with Kaspersky Endpoint Security for Windows).
Events arriving at the Central Node server are marked by TAA (IOA) rules. As a result of this markup, alerts can be generated for events that require user attention. If you have the Sandbox component, you can also automatically send files from Kaspersky Endpoint Agent hosts to be scanned by the Sandbox component in accordance with Kaspersky TAA (IOA) rules.
When the Central Node server is integrated with Kaspersky Endpoint Agent for Windows and Kaspersky Endpoint Security for Windows, you can do the following to react to detected threats:
- Manage files and applications by running the following tasks on Kaspersky Endpoint Agent hosts: Kill process, Get forensics, Start YARA scan, Run application, Get file, Delete file, Quarantine file, Restore file from quarantine, Manage services, Get disk image, Get memory dump.
- Configure policies for preventing the running of files and processes on selected hosts.
- Isolate individual hosts from the network.
- Work with TAA (IOA) rules to classify and analyze events.
- Work with OpenIOC compliant files (IOC files) to search for signs of targeted attacks, infected and probably infected objects on hosts and in the Alerts database.
- Perform Threat Response actions using the API.
When the Central Node server is integrated with Kaspersky Endpoint Security 11.4 for Linux and Kaspersky Endpoint Security for Mac, you can do the following to react to detected threats:
- Manage files and applications by running Get file, Run application tasks.
- Work with TAA (IOA) rules to classify and analyze events.
- Perform the following Threat Response actions using the API: Managing the application run task.
When the Central Node server is integrated with Kaspersky Endpoint Security 12 for Linux, you can do the following to react to detected threats:
- Manage files and applications by running Get file, Run application, Delete file, Kill process tasks.
- Isolate individual hosts from the network.
- Work with OpenIOC compliant files (IOC files) to search for signs of targeted attacks, infected and probably infected objects on hosts and in the Alerts database.
- Perform the following Threat Response actions using the API: Host network isolation management, Managing the application run task.
When the Central Node server is integrated with Kaspersky Endpoint Security 12.2 for Linux, you can do the following to react to detected threats:
- Manage files and applications by running Get file, Run application, Delete file, Kill process, Quarantine file, Restore file from quarantine tasks.
- Configure policies for preventing the running of files and processes on selected hosts.
- Isolate individual hosts from the network.
- Work with OpenIOC compliant files (IOC files) to search for signs of targeted attacks, infected and probably infected objects on hosts and in the Alerts database.
- Perform the following Threat Response actions using the API: Host network isolation management, Managing the application run task, Managing prevention rules.
The principle of operation of Kaspersky Anti Targeted Attack Platform is shown in the following picture.
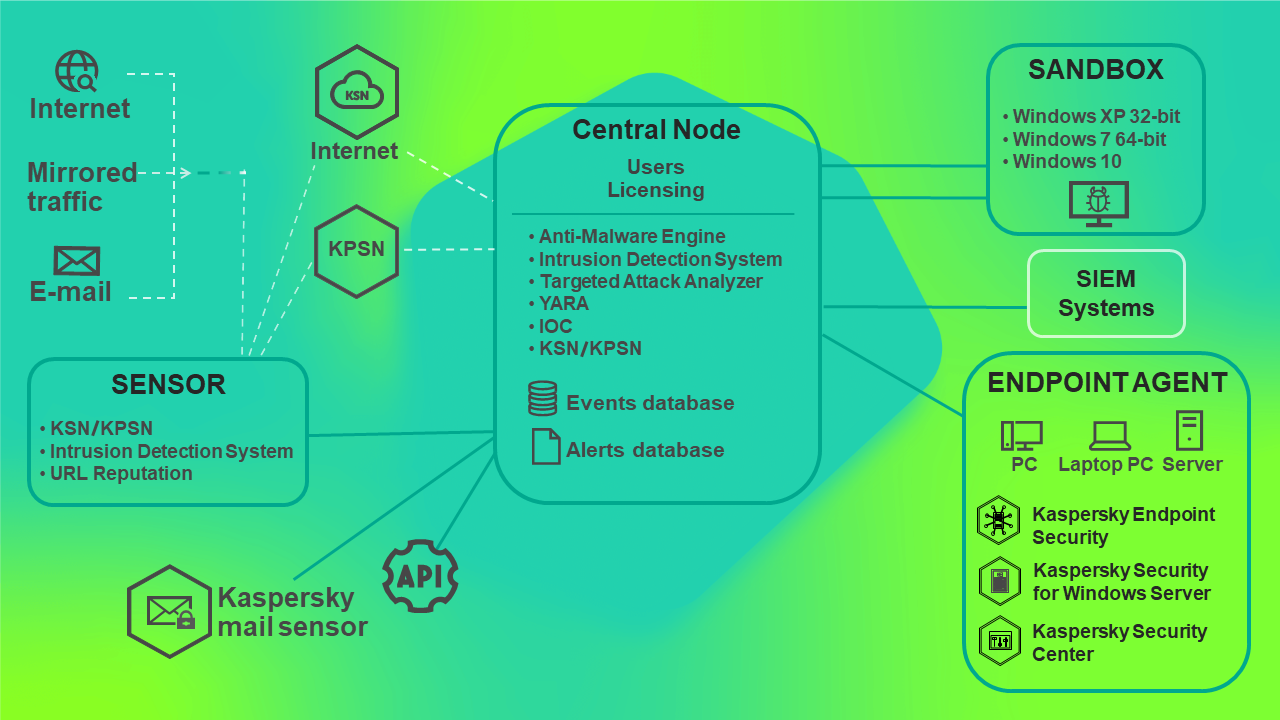
Principle of operation of Kaspersky Anti Targeted Attack Platform
You can configure settings of each Central Node component individually or manage several components in a centralized way in distributed solution mode.
A distributed solution is a two-tier hierarchy of Central Node servers. This structure sets apart a primary control server known as the Primary Central Node (PCN) and secondary servers known as Secondary Central Nodes (SCN).
The principle of operation of Kaspersky Anti Targeted Attack Platform in distributed solution mode is shown in the following picture.
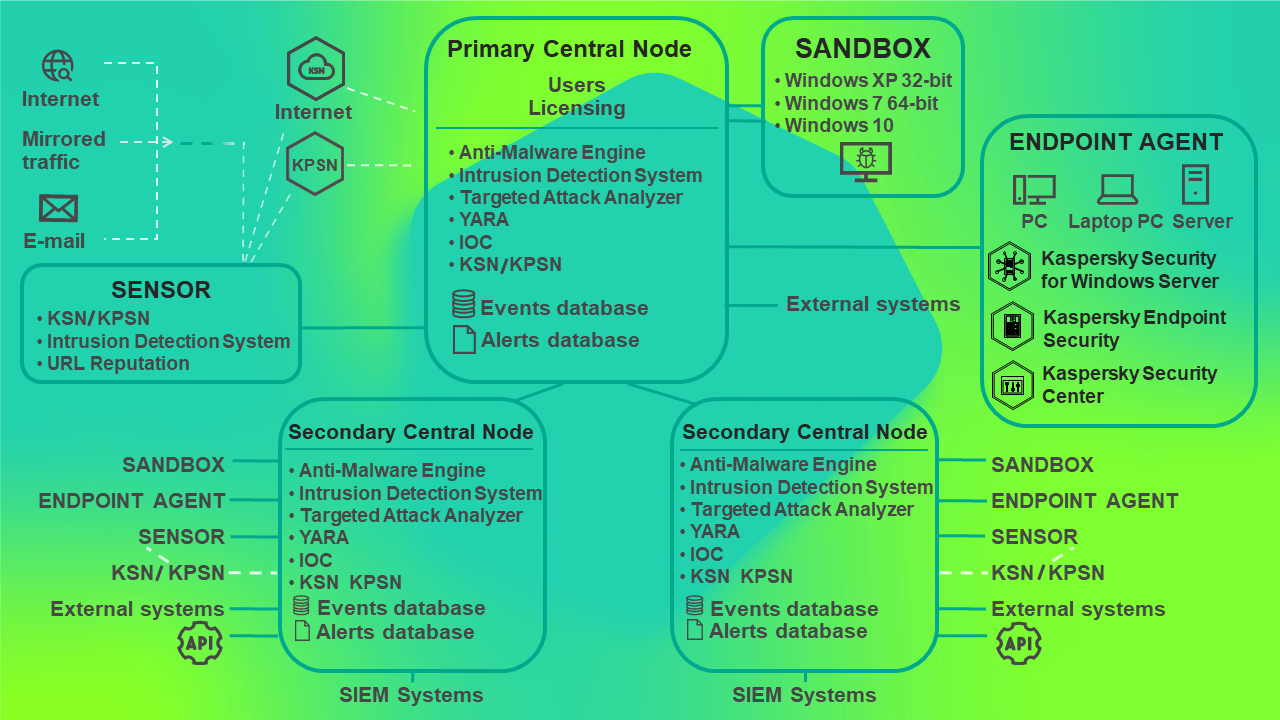
Principle of operation of Kaspersky Anti Targeted Attack Platform in distributed solution mode