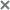Viewing information about a host
To view information about a host with the Endpoint Agent component:
- Select the Assets section in the application web interface window.
- Go to the Endpoint Agents tab.
- Select the host for which you want to view information.
This opens a window containing information about the host.
The window contains the following information:
- Recommendations group:
- Clicking the Alerts link opens the Alerts section with the search condition containing the selected host.
- Clicking the Events link opens the Threat Hunting section with the search condition containing the selected host.
- Clicking the Events affected by prevention rules link opens the Threat Hunting section with the search condition containing the selected host and the Blocked application (prevention rule) event type.
If you only use the KATA functionality (the KATA key), only the Alerts link is displayed in the recommendations section.
- On the Details tab, the Host section displays the following information:
- Name is the name of the host with the Endpoint Agent component.
- IP is the IP address of the host where the Endpoint Agent component is installed.
- OS—Version of the operating system on the host with the Endpoint Agent component installed.
- On the Details tab, the Endpoint Agent section displays the following information:
- Version—Version of the Endpoint Agent component installed.
- Activity is the activity indicator of the Endpoint Agent component. Possible values:
- Normal activity for hosts from which latest data was recently received.
- Warning for hosts from which latest data was received a long time ago.
- Critical inactivity for hosts from which latest data was received an extremely long time ago.
- Server—Name of the SCN or PCN server. Only displayed in distributed solution and multitenancy mode.
- Connected to server—Name of the Central Node server.
- Last connection—time of the last connection to the Central Node, SCN, or PCN server.
- License key status—For example, "OK".
- On the Prevention rules tab, you can see MD5 or SHA256 hashes for files that were prevented from running or opening on the host. The following information is displayed:
- Name—Name of the file.
- State—State of the prevention rule.
- Hash—Hashing algorithm.
If you are using only KATA functionality (the KATA key), the Prevention rules tab is not displayed.
- On the Tasks tab, you can see which tasks were run on the host. The following information is displayed:
- Time created—Task creation date and time.
- Name—Task name.
- Details—Full path to the file or data stream for which the task was created.
- State—Task completion status.
If you are using only KATA functionality (the KATA key), the Tasks tab is not displayed.
Clicking the link with the host name opens a list in which you can select one of the following actions:
- Run the following tasks:
- Kill process.
- Delete file.
- Get file.
- Get forensics.
- Quarantine file.
- Run application.
- New prevention rule.
- Isolate from network.
- Find events.
- Find alerts.
- Filter by this value.
- Exclude from filter.
- Copy value to clipboard.
The list of available actions depends on the type of Endpoint Agent component: for Windows, Linux, or Mac (for details, see the Operating principle of the application section).
Clicking the link with the IP opens a list in which you can select one of the following actions:
- Find events.
- Find alerts.
- Copy value to clipboard.
If you are using only KATA functionality (the KATA key), the following actions are available in the list that is displayed by clicking the host name and IP address links:
- Find alerts.
- Copy value to clipboard.