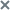Contents
- Configuring event sources
- Configuring receipt of Auditd events
- Configuring receipt of KATA/EDR events
- Configuring Kaspersky Security Center event receiving in CEF format
- Configuring receiving Kaspersky Security Center event from MS SQL
- Creating an account in the MS SQL database
- Configuring the SQL Server Browser service
- Creating a secret in KUMA
- Configuring a connector
- Configuring the KUMA Collector for receiving Kaspersky Security Center events from an MS SQL database
- Installing the KUMA Collector for receiving Kaspersky Security Center events from the MS SQL database
- Configuring receipt of events from Windows devices using KUMA Agent (WEC)
- Configuring audit of events from Windows devices
- Configuring centralized receipt of events from Windows devices using the Windows Event Collector service
- Granting permissions to view Windows events
- Granting permissions to log on as a service
- Configuring the KUMA Collector for receiving events from Windows devices
- Installing the KUMA Collector for receiving events from Windows devices
- Configuring forwarding of events from Windows devices to KUMA using KUMA Agent (WEC)
- Configuring receipt of events from Windows devices using KUMA Agent (WMI)
- Configuring receipt of PostgreSQL events
- Configuring receipt of IVK Kolchuga-K events
- Configuring receipt of CryptoPro NGate events
- Configuring receipt of Ideco UTM events
- Configuring receipt of KWTS events
- Configuring receipt of KLMS events
- Configuring receipt of KSMG events
- Configuring receipt of PT NAD events
- Configuring receipt of events using the MariaDB Audit Plugin
- Configuring receipt of Apache Cassandra events
- Configuring receipt of FreeIPA events
- Configuring receipt of VipNet TIAS events
- Configuring receipt of Sendmail events
- Configuring receipt of Nextcloud events
- Configuring receipt of Snort events
- Configuring receipt of Suricata events
- Configuring receipt of FreeRADIUS events
- Configuring receipt of zVirt events
- Configuring receipt of Zeek IDS events
Configuring event sources
This section provides information on configuring the receipt of events from various sources.
Configuring receipt of Auditd events
KUMA lets you monitor and audit the Auditd events on Linux devices.
Before configuring event receiving, make sure to create a new KUMA collector for the Auditd events.
Configuring the receipt of Auditd events involves the following steps:
- Installation of KUMA collector in the network infrastructure.
- Configuring the event source server.
- Verifying receipt of Auditd events by the KUMA collector.
You can verify that the Auditd event source server is configured correctly by searching for related events in the KUMA web interface.
Installing KUMA collector for receiving Auditd events
After creating a collector, in order to configure event receiving using rsyslog, you must install a collector on the network infrastructure server intended for receiving events.
For details on installing the KUMA collector, refer to the Installing collector in the network infrastructure section.
Page topConfiguring the event source server
The rsyslog service is used to transmit events from the server to the KUMA collector.
To configure transmission of events from the server to the collector:
- Make sure that the rsyslog service is installed on the event source server. For this purpose, execute the following command:
systemctl status rsyslog.serviceIf the rsyslog service is not installed on the server, install it by executing the following command:
yum install rsyslogsystemctl enable rsyslog.servicesystemctl start rsyslog.service - In the /etc/rsyslog.d
folder, create the audit.conf file with the following content:$ModLoad imfile$InputFileName /var/log/audit/audit.log$InputFileTag tag_audit_log:$InputFileStateFile audit_log$InputFileSeverity info$InputFileFacility local6$InputRunFileMonitor*.* @<KUMA collector IP address>:<KUMA collector port>If you want to send events over TCP, instead of the last line in the file insert the following line:
*.* @@<KUMA collector IP address>:<KUMA collector port>. - Save the changes to the audit.conf file.
- Restart the rsyslog service by executing the following command:
systemctl restart rsyslog.service
The event source server is configured. Data about events is transmitted from the server to the KUMA collector.
Page topConfiguring receipt of KATA/EDR events
You can configure the receipt of Kaspersky Anti Targeted Attack Platform events in the KUMA
.Before configuring event receipt, make sure to create a KUMA collector for the KATA/EDR events.
When creating a collector in the KUMA web interface, make sure that the port number matches the port specified in step 4c of Configuring export of Kaspersky Anti Targeted Attack Platform events to KUMA, and that the connector type corresponds to the type specified in step 4d.
To receive Kaspersky Anti Targeted Attack Platform events using Syslog, in the collector Installation wizard, at the Event parsing step, select the [OOTB] KATA normalizer.
Configuring the receipt of KATA/EDR events involves the following steps:
- Configuring the forwarding of KATA/EDR events
- Installing the KUMA collector in the network infrastructure
- Verifying receipt of KATA/EDR events in the KUMA collector
You can verify that the KATA/EDR event source server is configured correctly by searching for related events in the KUMA web interface. Kaspersky Anti Targeted Attack Platform events are displayed as KATA in the table with search results.
Configuring export of KATA/EDR events to KUMA
To configure export of events from Kaspersky Anti Targeted Attack Platform to KUMA:
- In a browser on any computer with access to the Central Node server, enter the IP address of the server hosting the Central Node component.
A window for entering Kaspersky Anti Targeted Attack Platform user credentials opens.
- In the user credentials entry window, select the Local administrator check box and enter the Administrator credentials.
- Go to the Settings → SIEM system section.
- Specify the following settings:
- Select the Activity log and Detections check boxes.
- In the Host/IP field, enter the IP address or host name of the KUMA collector.
- In the Port field, specify the port number to connect to the KUMA collector.
- In the Protocol field, select TCP or UDP from the list.
- In the Host ID field, specify the server host ID to be indicated in the SIEM systems log as a detection source.
- In the Alert frequency field, enter the interval for sending messages: from 1 to 59 minutes.
- Enable TLS encryption, if necessary.
- Click Apply.
Export of Kaspersky Anti Targeted Attack Platform events to KUMA is configured.
Configuring Kaspersky Anti Targeted Attack Platform integration with KUMA
Page topCreating KUMA collector for receiving KATA/EDR events
After configuring the event export settings, you must create a collector for Kaspersky Anti Targeted Attack Platform events in the KUMA web interface.
For details on creating a KUMA collector, refer to Creating a collector.
When creating a collector in the KUMA web interface, make sure that the port number matches the port specified in step 4c of Configuring export of Kaspersky Anti Targeted Attack Platform events to KUMA, and that the connector type corresponds to the type specified in step 4d.
To receive Kaspersky Anti Targeted Attack Platform events using Syslog, in the collector Installation wizard, at the Event parsing step, select the [OOTB] KATA normalizer.
Page topInstalling KUMA collector for receiving KATA/EDR events
After creating a collector, to configure receiving Kaspersky Anti Targeted Attack Platform events, install a new collector on the network infrastructure server intended for receiving events.
For details on installing the KUMA collector, refer to the Installing collector in the network infrastructure section.
Page topConfiguring Kaspersky Security Center event receiving in CEF format
KUMA allows you to receive and export events in the CEF format from Kaspersky Security Center Administration Server to the KUMA SIEM system.
Configuring the receipt of Kaspersky Security Center events in the CEF format involves the following steps:
- Configuring the forwarding of Kaspersky Security Center events.
- Configuring the KUMA Collector.
- Installing the KUMA collector in the network infrastructure.
- Verifying receipt of Kaspersky Security Center events in the CEF format in the KUMA collector
You can verify if the events from Kaspersky Security Center Administration Server in the CEF format were correctly exported to the KUMA SIEM system by using the KUMA web interface to search for related events.
To display Kaspersky Security Center events in CEF format in the table, enter the following search expression:
SELECT * FROM `events` WHERE DeviceProduct = 'KSC' ORDER BY Timestamp DESC LIMIT 250
Configuring export of Kaspersky Security Center events in CEF format
Kaspersky Security Center allows you to configure the settings for exporting events in the CEF format to a SIEM system.
The function of exporting Kaspersky Security Center events in the CEF format to SIEM systems is available with Kaspersky Endpoint Security for Business Advanced license or above.
To configure export of events from Kaspersky Security Center Administration Server to the KUMA SIEM system:
- In Kaspersky Security Center console tree, select the Administration server node.
- In the workspace of the node, select the Events tab.
- Click the Configure notifications and event export link and select Configure export to SIEM system from the drop-down list.
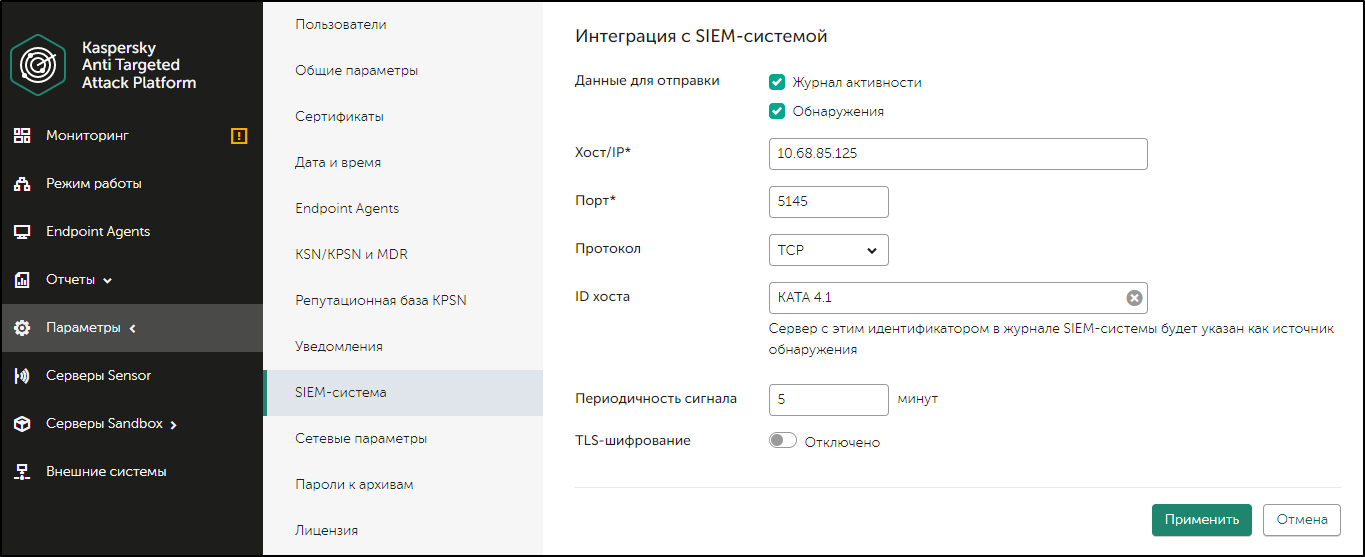
The Properties: Events window opens. By default the Events export section is displayed.
- In the Events export section, select the Automatically export events to SIEM system database check box.
- In the SIEM system drop-down list select ArcSight (CEF format).
- In the corresponding fields, specify the address of the KUMA SIEM system server and the port for connecting to the server. Select TCP/IP as the protocol.
You can click Export archive and specify the starting date from which pre-existing KUMA events are to be exported to the SIEM system database. By default, Kaspersky Security Center exports events starting from the current date.
- Click OK.
As a result, the Kaspersky Security Center Administration Server automatically exports all events to the KUMA SIEM system.
Configuring export of Kaspersky Security Center events to the KUMA SIEM system
Page topConfiguring KUMA collector for collecting Kaspersky Security Center events
After configuring the export of events in the CEF format from Kaspersky Security Center Administration Server, configure the collector in the KUMA web interface.
To configure the KUMA Collector for Kaspersky Security Center events:
- In the KUMA web interface, select Resources → Collectors.
- In the list of collectors, find the collector with the [OOTB] KSC normalizer and open it for editing.
- At the Transport step, in the URL field, specify the port to be used by the collector to receive Kaspersky Security Center events.
The port must match the port of the KUMA SIEM system server.
- At the Event parsing step, make sure that the [OOTB] KSC normalizer is selected.
- At the Routing step, make sure that the following destinations are added to the collector resource set:
- Storage. To send processed events to the storage.
- Correlator. To send processed events to the correlator.
If the Storage and Correlator destinations were not added, create them.
- At the Setup validation tab, click Create and save service.
- Copy the command for installing the KUMA collector that appears.
Installing KUMA collector for collecting Kaspersky Security Center events
After configuring the collector for collecting Kaspersky Security Center events in the CEF format, install the KUMA collector on the network infrastructure server intended for receiving events.
For details on installing the KUMA collector, refer to the Installing collector in the network infrastructure section.
Page topConfiguring receiving Kaspersky Security Center event from MS SQL
KUMA allows you to receive information about Kaspersky Security Center events from an MS SQL database.
Before configuring, make sure that you have created the KUMA collector for Kaspersky Security Center events from MS SQL.
When creating the collector in the KUMA web interface, at the Transport step, select the [OOTB] KSC SQL connector.
To receive Kaspersky Security Center events from the MS SQL database, at the Event parsing step, select the [OOTB] KSC from SQL normalizer.
Configuring event receiving consists of the following steps:
- Creating an account in the MS SQL.
- Configuring the SQL Server Browser service.
- Creating a secret.
- Configuring a connector.
- Installation of collector in the network infrastructure.
- Verifying receipt of events from MS SQL in the KUMA collector.
You can verify that the receipt of events from MS SQL is configured correctly by searching for related events in the KUMA web interface.
Creating an account in the MS SQL database
To receive Kaspersky Security Center events from MS SQL, a user account is required that has the rights necessary to connect and work with the database.
To create an account for working with MS SQL:
- Log in to the server with MS SQL for Kaspersky Security Center installed.
- Using SQL Server Management Studio, connect to MS SQL using an account with administrator rights.
- In the Object Explorer pane, expand the Security section.
- Right-click the Logins folder and select New Login from the context menu.
The Login - New window opens.
- On the General tab, click the Search button next to the Login name field.
The Select User or Group window opens.
- In the Enter the object name to select (examples) field, specify the object name and click OK.
The Select User or Group window closes.
- In the Login - New window, on the General tab, select the Windows authentication option.
- In the Default database field, select the Kaspersky Security Center database.
The default Kaspersky Security Center database name is KAV.
- On the User Mapping tab, configure the account permissions:
- In the Users mapped to this login section, select the Kaspersky Security Center database.
- In the Database role membership for section, select the check boxes next to the db_datareader and public permissions.
- On the Status tab, configure the permissions for connecting the account to the database:
- In the Permission to connect to database engine section, select Grant.
- In the Login section, select Enabled.
- Click OK.
The Login - New window closes.
To check the account permissions:
- Run SQL Server Management Studio using the created account.
- Go to any MS SQL database table and make a selection based on the table.
Configuring the SQL Server Browser service
After creating an account in MS SQL, you must configure the SQL Server Browser service.
To configure the SQL Server Browser service:
- Open SQL Server Configuration Manager.
- In the left pane, select SQL Server Services.
A list of services opens.
- Open the SQL Server Browser service properties in one of the following ways:
- Double-click the name of the SQL Server Browser service.
- Right-click the name of the SQL Server Browser service and select Properties from the context menu.
- In the SQL Server Browser Properties window that opens, select the Service tab.
- In the Start Mode field, select Automatic.
- Select the Log On tab and click the Start button.
Automatic startup of the SQL Server Browser service is enabled.
- Enable and configure the TCP/IP protocol by doing the following:
- In the left pane, expand the SQL Server Network Configuration section and select the Protocols for <SQL Server name> subsection.
- Right-click the TCP/IP protocol and select Enable from the context menu.
- In the Warning window that opens, click OK.
- Open the TCP/IP protocol properties in one of the following ways:
- Double-click the TCP/IP protocol.
- Right-click the TCP/IP protocol and select Properties from the context menu.
- Select the IP Addresses tab, and then in the IPALL section, specify port 1433 in the TCP Port field.
- Click Apply to save the changes.
- Click OK to close the window.
- Restart the SQL Server (<SQL Server name>) service by doing the following:
- In the left pane, select SQL Server Services.
- In the service list on the right, right-click the SQL Server (<SQL Server name>) service and select Restart from the context menu.
- In Windows Defender Firewall with Advanced Security, allow inbound connections on the server on the TCP port 1433.
Creating a secret in KUMA
After creating and configuring an account in MS SQL, you must add a secret in the KUMA web interface. This resource is used to store credentials for connecting to MS SQL.
To create a KUMA secret:
- In the KUMA web interface, open Resources → Secrets.
The list of available secrets will be displayed.
- Click the Add secret button to create a new secret.
The secret window is displayed.
- Enter information about the secret:
- In the Name field, choose a name for the added secret.
- In the Tenant drop-down list, select the tenant that will own the created resource.
- In the Type drop-down list, select urls.
- In the URL field, specify a string of the form:
sqlserver://[<domain>%5C]<username>:<password>@<server>:1433/<database_name>where:
domainis a domain name.%5Cis the domain/user separator. Represents the "\" character in URL format.usernameis the name of the created MS SQL account.passwordis the password of the created MS SQL account.serveris the name or IP address of the server where the MS SQL database for Kaspersky Security Center is installed.database_nameis the name of the Kaspersky Security Center database. The default name is KAV.
Example:
sqlserver://test.local%5Cuser:password123@10.0.0.1:1433/KAVIf the MS SQL database account password contains special characters (@ # $ % & * ! + = [ ] : ' , ? / \ ` ( ) ;), convert them to URL format.
- Click Save.
For security reasons, the string specified in the URL field is hidden after the secret is saved.
Configuring a connector
To connect KUMA to an MS SQL database, you must configure the connector.
To configure a connector:
- In the KUMA web interface, select Resources → Connectors.
- In the list of connectors, find the [OOTB] KSC SQL connector and open it for editing.
If a connector is not available for editing, copy it and open the connector copy for editing.
If the [OOTB] KSC SQL connector is not available, contact your system administrator.
- On the Basic settings tab, in the URL drop-down lists, select the secret created for connecting to the MS SQL database.
- Click Save.
Configuring the KUMA Collector for receiving Kaspersky Security Center events from an MS SQL database
After configuring the event export settings, you must create a collector in the KUMA web interface for Kaspersky Security Center events received from MS SQL.
For details on creating a KUMA collector, refer to Creating a collector.
When creating the collector in the KUMA web interface, at the Transport step, select the [OOTB] KSC SQL connector.
To receive Kaspersky Security Center events from MS SQL, at the Event parsing step, select the [OOTB] KSC from SQL normalizer.
Page topInstalling the KUMA Collector for receiving Kaspersky Security Center events from the MS SQL database
After configuring the collector for receiving Kaspersky Security Center events from MS SQL, install the KUMA collector on the network infrastructure server where you intend to receive events.
For details on installing the KUMA collector, refer to the Installing collector in the network infrastructure section.
Page topConfiguring receipt of events from Windows devices using KUMA Agent (WEC)
KUMA allows you to receive information about events from Windows devices using the WEC KUMA Agent.
Configuring event receiving consists of the following steps:
- Configuring policies for receiving events from Windows devices.
- Configuring centralized receipt of events using the Windows Event Collector service.
- Granting permissions to view events.
- Granting permissions to log on as a service.
- Configuring the KUMA Collector.
- Installing KUMA collector.
- Forwarding events from Windows devices to KUMA.
Configuring audit of events from Windows devices
You can configure event audit on Windows devices for an individual device or for all devices in a domain.
This section describes how to configure an audit on an individual device and how to use a domain group policy to configure an audit.
Configuring an audit policy on a Windows device
To configure audit policies on a device:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
secpol.mscand click OK.The Local security policy window opens.
- Select Security Settings → Local policies → Audit policy.
- In the pane on the right, double-click to open the properties of the policy for which you want to enable an audit of successful and unsuccessful attempts.
- In the <Policy name> properties window, on the Local security setting tab, select the Success and Failure check boxes to track successful and interrupted attempts.
It is recommended to enable an audit of successful and unsuccessful attempts for the following policies:
- Audit Logon
- Audit Policy Change
- Audit System Events
- Audit Logon Events
- Audit Account Management
Configuration of an audit policy on the device is complete.
Page topConfiguring an audit using a group policy
In addition to configuring an audit policy on an individual device, you can also configure an audit by using a domain group policy.
To configure an audit using a group policy:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
gpedit.mscand click OK.The Local Group Policy Editor window opens.
- Select Computer configuration → Windows configuration → Security settings → Local policies → Audit policy.
- In the pane on the right, double-click to open the properties of the policy for which you want to enable an audit of successful and unsuccessful attempts.
- In the <Policy name> properties window, on the Local security setting tab, select the Success and Failure check boxes to track successful and interrupted attempts.
It is recommended to enable an audit of successful and unsuccessful attempts for the following policies:
- Audit Logon
- Audit Policy Change
- Audit System Events
- Audit Logon Events
- Audit Account Management
If you want to receive Windows logs from a large number of servers or if installation of KUMA agents on domain controllers is not allowed, it is recommended to configure Windows log redirection to individual servers that have the Windows Event Collector service configured.
The audit policy is now configured on the server or workstation.
Page topConfiguring centralized receipt of events from Windows devices using the Windows Event Collector service
The Windows Event Collector service allows you to centrally receive data about events on servers and workstations running Windows. You can use the Windows Event Collector service to subscribe to events that are registered on remote devices.
You can configure the following types of event subscriptions:
- Source-initiated subscriptions. Remote devices send event data to the Windows Event Collector server whose address is specified in the group policy. For details on the subscription configuration procedure, please refer to the Configuring data transfer from the event source server section.
- Collector-initiated subscriptions. The Windows Event Collector server connects to remote devices and independently gathers events from local logs. For details on the subscription configuration procedure, please refer to the Configuring the Windows Event Collector service section.
Configuring data transfer from the event source server
You can receive information about events on servers and workstations by configuring data transfer from remote devices to the Windows Event Collector server.
Preliminary steps
- Verify that the Windows Remote Management service is configured on the event source server by running the following command in the PowerShell console:
winrm get winrm/configIf the Windows Remote Management service is not configured, initialize it by running the following command:
winrm quickconfig - If the event source server is a domain controller, make the Windows logs available over the network by running the following command in PowerShell as an administrator:
wevtutil set-log security /ca:’O:BAG:SYD:(A;;0xf0005;;;SY)(A;;0x5;;;BA)(A;;0x1;;;S-1-5-32-573)(A;;0x1;;;S-1-5-20)Verify access by running the following command:
wevtutil get-log security
Configuring the firewall on the event source server
To enable the Windows Event Collector server to receive Windows log entries, inbound connection ports must be opened on the event source server.
To open ports for inbound connections:
- On the event source server, open the Run window by pressing the key combination Win+R.
- In the opened window, type
wf.mscand click OK.The Windows Defender Firewall with Advanced Security window opens.
- Go to the Inbound Rules section and click New Rule in the Actions pane.
The New Inbound Rule Wizard opens.
- At the Rule type step, select Port.
- At the Protocols and ports step, select TCP as the protocol. In the Specific local ports field, indicate the relevant port numbers:
5985(for HTTP access)5986(for HTTPS access)
You can indicate one of the ports, or both.
- At the Action step, select Allow connection (selected by default).
- At the Profile step, clear the Private and Public check boxes.
- At the Name step, specify a name for the new inbound connection rule and click Done.
Configuration of data transfer from the event source server is complete.
The Windows Event Collector server must have the permissions to read Windows logs on the event source server. These permissions can be assigned to both the Windows Event Collector server account and to a special user account. For details on granting permissions, please refer to the Granting user permissions to view the Windows Event Log.
Page topConfiguring the Windows Event Collector service
The Windows Event Collector server can independently connect to devices and gather data on events of any severity.
To configure the receipt of event data by the Windows Event Collector server:
- On the event source server, open the Run window by pressing Win+R.
- In the opened window, type
services.mscand click OK.The Services window opens.
- In the list of services, find and start the Windows Event Collector service.
- Open the Event Viewer snap-in by doing the following:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
eventvwrand click OK.
- Go to the Subscriptions section and click Create Subscription in the Actions pane.
- In the opened Subscription Properties window, specify the name and description of the subscription, and define the following settings:
- In the Destination log field, select Forwarded events from the list.
- In the Subscription type and source computers section, click the Select computers button.
- In the opened Computers window, click the Add domain computer button.
The Select computer window opens.
- In the Enter the object names to select (examples) field, list the names of the devices from which you want to receive event information. Click OK.
- In the Computers window, check the list of devices from which the Windows Event Collector server will gather event data and click OK.
- In the Subscription properties window, in the Collected events field, click the Select events button.
- In the opened Request filter window, specify how often and which data about events on devices you want to receive.
- If necessary, in the <All event codes> field, list the codes of the events whose information you want to receive or do not want to receive. Click OK.
- If you want to use a special account to view event data, do the following:
- In the Subscription properties window, click the Advanced button.
- In the opened Advanced subscription settings window, in the user account settings, select Specific user.
- Click the User and password button and enter the account credentials of the selected user.
Configuration of the Event Collector Service is complete.
To verify that the configuration is correct and event data is being received by the Windows Event Collector server:
In the Event Viewer snap-in, go to Event Viewer (Local) → Windows logs → Forwarded events.
Page topGranting permissions to view Windows events
You can grant permissions to view Windows events for a specific device or for all devices in a domain.
To grant permissions to view events on a specific device:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
compmgmt.mscand click OK.The Computer Management window opens.
- Go to Computer Management (local) → Local users and groups → Groups.
- In the pane on the right, select the Event Log Readers group and double-click to open the policy properties.
- Click the Add button at the bottom of the Properties: Event Log Readers window.
The Select Users, Computers or Groups window opens.
- In the Enter the object names to select (examples) field, list the names of the users or devices to which you want to grant permissions to view event data. Click OK.
To grant permissions to view events for all devices in a domain:
- Log in to the domain controller with administrator privileges.
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
dsa.mscand click OK.The Active Directory Users and Computers window opens.
- Go to Active Directory Users and Computers → <Domain name> → Builtin.
- In the pane on the right, select the Event Log Readers group and double-click to open the policy properties.
In the Properties: Event Log Readers window, open the Members tab and click the Add button.
The Select Users, Computers or Groups window opens.
- In the Enter the object names to select (examples) field, list the names of the users or devices to which you want to grant permissions to view event data. Click OK.
Granting permissions to log on as a service
You can grant permission to log on as a service to a specific device or to all devices in a domain. The "Log on as a service" permission allows you to start a process using an account that has been granted this permission.
To grant the "Log on as a service" permission to a device:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
secpol.mscand click OK.The Local security policy window opens.
- Go to Security settings → Local policies → User rights assignment.
- In the pane on the right, double-click to open the properties of the Log on as a service policy.
- In the opened Properties: Log on as a Service window, click the Add User or Group button.
The Select Users or Groups window opens.
- In the Enter the object names to select (examples) field, list the names of the accounts or devices to which you want to grant the permission to log on as a service. Click OK.
Before granting the permission, make sure that the accounts or devices to which you want to grant the Log on as a service permission are not listed in the properties of the Deny log on as a service policy.
To grant the "Log on as a service" permission to devices in a domain:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
gpedit.mscand click OK.The Local Group Policy Editor window opens.
- Select Computer configuration → Windows configuration → Security settings → Local policies → User rights assignment.
- In the pane on the right, double-click to open the properties of the Log on as a service policy.
- In the opened Properties: Log on as a Service window, click the Add User or Group button.
The Select Users or Groups window opens.
- In the Enter the object names to select (examples) field, list the names of the users or devices to which you want to grant the permission to log on as a service. Click OK.
Before granting the permission, make sure that the accounts or devices to which you want to grant the Log on as a service permission are not listed in the properties of the Deny log on as a service policy.
Page topConfiguring the KUMA Collector for receiving events from Windows devices
After you finish configuring the audit policy on devices, creating subscriptions to events and granting all the necessary permissions, you need to create a collector in the KUMA web interface for events from Windows devices.
For details on creating a KUMA collector, refer to Creating a collector.
To receive events from Windows devices, define the following collector settings in the KUMA Collector Installation Wizard:
- At the Transport step, define the following settings:
- In the Connector window, select Create.
- In the Type field, select http.
- In the Delimiter field, select \0.
- On the Advanced settings tab, in the TLS mode field, select With verification.
- At the Event parsing step, click the Add event parsing button.
- In the opened Basic event parsing window, in the Normalizer field, select [OOTB] Windows Extended v.1.0 and click OK.
- At the Routing step, add the following destinations:
- Storage. To send processed events to the storage.
- Correlator. To send processed events to the correlator.
If the Storage and Correlator destinations were not added, create them.
- At the Setup validation tab, click Create and save service.
- Copy the command for installing the KUMA collector that appears.
Installing the KUMA Collector for receiving events from Windows devices
After configuring the collector for receiving Windows events, install the KUMA Collector on the server of the network infrastructure intended for receiving events.
For details on installing the KUMA collector, refer to the Installing collector in the network infrastructure section.
Page topConfiguring forwarding of events from Windows devices to KUMA using KUMA Agent (WEC)
To complete the data forwarding configuration, you must create a WEC KUMA agent and then install it on the device from which you want to receive event information.
For more details on creating and installing a WEC KUMA Agent on Windows devices, please refer to the Forwarding events from Windows devices to KUMA section.
Page topConfiguring receipt of events from Windows devices using KUMA Agent (WMI)
KUMA allows you to receive information about events from Windows devices using the WMI KUMA Agent.
Configuring event receiving consists of the following steps:
- Configuring audit settings for managing KUMA.
- Configuring data transfer from the event source server.
- Granting permissions to view events.
- Granting permissions to log on as a service.
- Creating a KUMA collector.
To receive events from Windows devices, in the KUMA Collector Installation Wizard, at the Event parsing step, in the Normalizer field, select [OOTB] Windows Extended v.1.0.
- Installing KUMA collector.
- Forwarding events from Windows devices to KUMA.
To complete the data forwarding configuration, you must create a WMI KUMA agent and then install it on the device from which you want to receive event information.
Configuring audit settings for managing KUMA
You can configure event audit on Windows devices both on a specific device using a local policy or on all devices in a domain using a group policy.
This section describes how to configure an audit on an individual device and how to use a domain group policy to configure an audit.
Configuring an audit using a local policy
To configure an audit using a local policy:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
secpol.mscand click OK.The Local security policy window opens.
- Select Security Settings → Local policies → Audit policy.
- In the pane on the right, double-click to open the properties of the policy for which you want to enable an audit of successful and unsuccessful attempts.
- In the <Policy name> properties window, on the Local security setting tab, select the Success and Failure check boxes to track successful and interrupted attempts.
It is recommended to enable an audit of successful and unsuccessful attempts for the following policies:
- Audit Logon
- Audit Policy Change
- Audit System Events
- Audit Logon Events
- Audit Account Management
Configuration of an audit policy on the device is complete.
Page topConfiguring an audit using a group policy
In addition to configuring an audit on an individual device, you can also configure an audit by using a domain group policy.
To configure an audit using a group policy:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
gpedit.mscand click OK.The Local Group Policy Editor window opens.
- Select Computer configuration → Windows configuration → Security settings → Local policies → Audit policy.
- In the pane on the right, double-click to open the properties of the policy for which you want to enable an audit of successful and unsuccessful attempts.
- In the <Policy name> properties window, on the Local security setting tab, select the Success and Failure check boxes to track successful and interrupted attempts.
It is recommended to enable an audit of successful and unsuccessful attempts for the following policies:
- Audit Logon
- Audit Policy Change
- Audit System Events
- Audit Logon Events
- Audit Account Management
The audit policy is now configured on the server or workstation.
Page topConfiguring data transfer from the event source server
Preliminary steps
- On the event source server, open the Run window by pressing the key combination Win+R.
- In the opened window, type
services.mscand click OK.The Services window opens.
- In the list of services, find the following services:
- Remote Procedure Call
- RPC Endpoint Mapper
- Check the Status column to confirm that these services have the Running status.
Configuring the firewall on the event source server
The Windows Management Instrumentation server can receive Windows log entries if ports are open for inbound connections on the event source server.
To open ports for inbound connections:
- On the event source server, open the Run window by pressing the key combination Win+R.
- In the opened window, type
wf.mscand click OK.The Windows Defender Firewall with Advanced Security window opens.
- In the Windows Defender Firewall with Advanced Security window, go to the Inbound Rules section and in the Actions pane, click New Rule.
This opens the New Inbound Rule Wizard.
- In the New Inbound Rule Wizard, at the Rule Type step, select Port.
- At the Protocols and ports step, select TCP as the protocol. In the Specific local ports field, indicate the relevant port numbers:
13544549152–65535
- At the Action step, select Allow connection (selected by default).
- At the Profile step, clear the Private and Public check boxes.
- At the Name step, specify a name for the new inbound connection rule and click Done.
Configuration of data transfer from the event source server is complete.
Page topGranting permissions to view Windows events
You can grant permissions to view Windows events for a specific device or for all devices in a domain.
To grant permissions to view events on a specific device:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
compmgmt.mscand click OK.The Computer Management window opens.
- Go to Computer Management (local) → Local users and groups → Groups.
- In the pane on the right, select the Event Log Readers group and double-click to open the policy properties.
- Click the Add button at the bottom of the Properties: Event Log Readers window.
The Select Users, Computers or Groups window opens.
- In the Enter the object names to select (examples) field, list the names of the users or devices to which you want to grant permissions to view event data. Click OK.
To grant permissions to view events for all devices in a domain:
- Log in to the domain controller with administrator privileges.
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
dsa.mscand click OK.The Active Directory Users and Computers window opens.
- In the Active Directory Users and Computers window, go to the Active Directory Users and Computers section → <Domain name> → Builtin.
- In the pane on the right, select the Event Log Readers group and double-click to open the policy properties.
In the Properties: Event Log Readers window, open the Members tab and click the Add button.
The Select Users, Computers or Groups window opens.
- In the Select User, Computer, or Group window, In the Enter the object name to select (examples) field, list the names of the users or devices to which you want to grant permissions to view event data. Click OK.
Granting permissions to log on as a service
You can grant permission to log on as a service to a specific device or to all devices in a domain. The "Log on as a service" permission allows you to start a process using an account that has been granted this permission.
Before granting the permission, make sure that the accounts or devices to which you want to grant the Log on as a service permission are not listed in the properties of the Deny log on as a service policy.
To grant the "Log on as a service" permission to a device:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
secpol.mscand click OK.The Local security policy window opens.
- In the Local Security Policy window, go to the Security Settings → Local Policies → User Rights Assignment section.
- In the pane on the right, double-click to open the properties of the Log on as a service policy.
- This opens the Properties: Log on as a Service window; in that window, click Add User or Group.
This opens the Select Users or Groups window.
- In the Enter the object names to select (examples) field, list the names of the accounts or devices to which you want to grant the permission to log on as a service. Click OK.
To grant the "Log on as a service" permission to devices in a domain:
- Open the Run window by pressing the key combination Win+R.
- In the opened window, type
gpedit.mscand click OK.The Local Group Policy Editor window opens.
- Select Computer configuration → Windows configuration → Security settings → Local policies → User rights assignment.
- In the pane on the right, double-click to open the properties of the Log on as a service policy.
- This opens the Properties: Log on as a Service window; in that window, click Add User or Group.
This opens the Select Users or Groups window.
- In the Enter the object names to select (examples) field, list the names of the users or devices to which you want to grant the permission to log on as a service. Click OK.
Configuring receipt of PostgreSQL events
KUMA lets you monitor and audit PostgreSQL events on Linux devices using rsyslog.
Events are audited using the pgAudit plugin. The plugin supports PostgreSQL 9.5 and later. For details about the pgAudit plugin, see https://github.com/pgaudit/pgaudit.
Configuring event receiving consists of the following steps:
- Installing the pdAudit plugin.
- Creating a KUMA collector for PostgreSQL events.
To receive PostgreSQL events using rsyslog, in the collector installation wizard, at the Event parsing step, select the [OOTB] PostgreSQL pgAudit syslog normalizer.
- Installing a collector in the KUMA network infrastructure.
- Configuring the event source server.
- Verifying receipt of PostgreSQL events in the KUMA collector
You can verify that the PostgreSQL event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Installing the pgAudit plugin
To install the pgAudit plugin:
- On the OS command line, run the following commands as a user with administrator rights:
sudo apt updatesudo apt -y install postgresql-<PostgreSQL version>-pgauditYou must select the plugin version to match the PostgresSQL version. For information about PostgreSQL versions and the matching plugin versions, see https://github.com/pgaudit/pgaudit#postgresql-version-compatibility.
Example:
sudo apt -y install postgresql-12-pgaudit - Find the postgres.conf configuration file. To do so, run the following command on the PostgreSQL command line:
show data_directoryThe response will indicate the location of the configuration file.
- Create a backup copy of the postgres.conf configuration file.
- Open the postgres.conf file and copy or replace the values in it with the values listed below.
```## pgAudit settingsshared_preload_libraries = 'pgaudit'## database logging settingslog_destination = 'syslog'## syslog facilitysyslog_facility = 'LOCAL0'## event identsyslog_ident = 'Postgres'## sequence numbers in syslogsyslog_sequence_numbers = on## split messages in syslogsyslog_split_messages = off## message encodinglc_messages = 'en_US.UTF-8'## min message level for loggingclient_min_messages = log## min error message level for logginglog_min_error_statement = info## log checkpoints (buffers, restarts)log_checkpoints = off## log query durationlog_duration = off## error description levellog_error_verbosity = default## user connections logginglog_connections = on## user disconnections logginglog_disconnections = on## log prefix formatlog_line_prefix = '%m|%a|%d|%p|%r|%i|%u| %e '## log_statementlog_statement = 'none'## hostname logging status. dns bane resolving affect#performance!log_hostname = off## logging collector buffer status#logging_collector = off## pg audit settingspgaudit.log_parameter = onpgaudit.log='ROLE, DDL, MISC, FUNCTION'``` - Restart the PostgreSQL service using the command:
sudo systemctl restart postgresql - To load the pgAudit plugin to PostgreSQL, run the following command on the PostgreSQL command line:
CREATE EXTENSION pgaudit
The pgAudit plugin is installed.
Page topConfiguring a Syslog server to send events
The rsyslog service is used to transmit events from the server to KUMA.
To configure the sending of events from the server where PostgreSQL is installed to the collector:
- To verify that the rsyslog service is installed on the event source server, run the following command as administrator:
sudo systemctl status rsyslog.serviceIf the rsyslog service is not installed on the server, install it by executing the following commands:
yum install rsyslogsudo systemctl enable rsyslog.servicesudo systemctl start rsyslog.service - In the /etc/rsyslog.d/ directory, create a pgsql-to-siem.conf file with the following content:
If $programname contains 'Postgres' then @<IP address of the collector>:<port of the collector>For example:If $programname contains 'Postgres' then @192.168.1.5:1514If you want to send events via TCP, the contents of the file must be as follows:
If $programname contains 'Postgres' then @@<IP address of the collector>:<port of the collector>Save changes to the pgsql-to-siem.conf configuration file.
- Add the following lines to the /etc/rsyslog.conf configuration file:
$IncludeConfig /etc/pgsql-to-siem.conf$RepeatedMsgReduction offSave changes to the /etc/rsyslog.conf configuration file.
- Restart the rsyslog service by executing the following command:
sudo systemctl restart rsyslog.service
Configuring receipt of IVK Kolchuga-K events
You can configure the receipt of events from the IVK Kolchuga-K system to the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring the sending of IVK Kolchuga-K events to KUMA.
- Creating a KUMA collector for receiving events from the IVK Kolchuga-K system.
To receive IVK Kolchuga-K events using Syslog, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] Kolchuga-K syslog normalizer.
- Installing a KUMA collector for receiving IVK Kolchuga-K events.
- Verifying receipt of IVK Kolchuga-K events in KUMA.
You can verify that the IVK Kolchuga-K event source is configured correctly in the Searching for related events section of the KUMA web interface.
Configuring export of IVK Kolchuga-K events to KUMA
To configure the export of events of the IVK Kolchuga-K firewall via syslog to the KUMA collector:
- Connect to the firewall over SSH with administrator rights.
- Create a backup copy of the /etc/services and /etc/syslog.conf files.
- In the /etc/syslog.conf configuration file, specify the FQDN or IP address of the KUMA collector. For example:
*.* @kuma.example.com
or
*.* @192.168.0.100
Save changes to the configuration file /etc/syslog.conf.
- In the /etc/services configuration file, specify the port and protocol used by the KUMA collector. For example:
syslog 10514/udp
Save changes to the /etc/services configuration file.
- Restart the syslog server of the firewall:
service syslogd restart
Configuring receipt of CryptoPro NGate events
You can configure the receipt of CryptoPro NGate events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring export of CryptoPro NGate events to KUMA.
- Creating a KUMA collector for receiving CryptoPro NGate events.
To receive CryptoPro NGate events using Syslog, in the collector installation wizard, at the Event parsing step, select the [OOTB] NGate syslog normalizer.
- Creating a KUMA collector for receiving CryptoPro NGate events.
- Verifying receipt of CryptoPro NGate events in the KUMA collector.
You can verify that the CryptoPro NGate event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of CryptoPro NGate events to KUMA
To configure the sending of events from CryptoPro NGate to KUMA:
- Connect to the web interface of the NGate management system.
- Connect remote syslog servers to the management system. To do so:
- Open the page with the list of syslog servers: External Services → Syslog Server → Add Syslog Server.
- Enter the settings of the syslog server and click
 .
.
- Assign syslog servers to the configuration for recording logs of the cluster. To do so:
- In the Clusters → Summary section, select the cluster that you want to configure.
- On the Configurations tab, click the Configuration control for the relevant cluster to go to the configuration settings page.
In the Syslog Servers field of the configured configuration, click the Assign button.
Select the check boxes for syslog servers that you want to assign and click
the icon.
icon.You can assign an unlimited number of servers.
To add new syslog servers, click
 .
.Publish the configuration to activate the new settings.
Assign syslog servers to the management system for recording Administrator activity logs. To do so:
Select the Management Center Settings menu item and on the page that is displayed, under Syslog servers, click Assign.
In the Assign Syslog Servers to Management Center window, select the check box for those syslog servers that you want to assign, then click
 .
.You can assign an unlimited number of servers.
As a result, events of CryptoPro NGate are sent to KUMA.
Page topConfiguring receipt of Ideco UTM events
You can configure the receipt of Ideco UTM application events in KUMA via the Syslog protocol.
Configuring event receiving consists of the following steps:
- Configuring export of Ideco UTM events to KUMA.
- Creating a KUMA collector for receiving Ideco UTM.
To receive Ideco UTM events, in the Collector Installation Wizard, at the Event parsing step, select the "[OOTB] Ideco UTM syslog" normalizer.
- Creating a KUMA collector for receiving Ideco UTM events.
- Verifying receipt of Ideco UTM events in KUMA.
You can verify that the Ideco UTM event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of Ideco UTM events to KUMA
To configure the sending of events from Ideco UTM to KUMA:
- Connect to the Ideco UTM web interface under a user account that has administrative privileges.
- In the System message forwarding menu, move the Syslog toggle switch to the enabled position.
- For the IP address setting, specify the IP address of the KUMA collector.
- For the Port setting, enter the port that the KUMA collector is listening on.
- Click Save to apply the changes.
The forwarding of Ideco UTM events to KUMA is configured.
Page topConfiguring receipt of KWTS events
You can configure the receipt of events from the Kaspersky Web Traffic Security (KWTS) web traffic analysis and filtering system in KUMA.
Configuring event receiving consists of the following steps:
- Configuring export of KWTS events to KUMA.
- Creating a KUMA collector for receiving KWTS events.
To receive KWTS events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] KWTS normalizer.
- Installing a KUMA collector for receiving KWTS events.
- Verifying receipt of KWTS events in the KUMA collector.
You can verify that KWTS event export is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of KWTS events to KUMA
To configure the export of KWTS events to KUMA:
- Connect to the KWTS server over SSH as root.
- Before making changes, create backup copies of the following files:
- /opt/kaspersky/kwts/share/templates/core_settings/event_logger.json.template
- /etc/rsyslog.conf
- Make sure that the settings in the /opt/kaspersky/kwts/share/templates/core_settings/event_logger.json.template configuration file have the following values, and make changes if necessary:
"siemSettings":{"enabled": true,"facility": "Local5","logLevel": "Info","formatting":{ - Save your changes.
- To send events via UDP, make the following changes to the /etc/rsyslog.conf configuration file:
$WorkDirectory /var/lib/rsyslog$ActionQueueFileName ForwardToSIEM$ActionQueueMaxDiskSpace 1g$ActionQueueSaveOnShutdown on$ActionQueueType LinkedList$ActionResumeRetryCount -1local5.* @<<IP address of the KUMA collector>:<port of the collector>>If you want to send events over TCP, the last line should be as follows:
local5.* @@<<IP address of the KUMA collector>:<port of the collector>> - Save your changes.
- Restart the rsyslog service with the following command:
sudo systemctl restart rsyslog.service - Go to the KWTS web interface, to the Settings – Syslog tab and enable the Log information about traffic profile option.
- Click Save.
Configuring receipt of KLMS events
You can configure the receipt of events from the Kaspersky Linux Mail Server (KLMS) mail traffic analysis and filtering system to the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring export of KLMS events to KUMA
- Creating a KUMA collector for receiving KLMS events
To receive KLMS events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] KLMS syslog CEF normalizer.
- Installing a KUMA collector for receiving KLMS events
- Verifying receipt of KLMS events in the KUMA collector
You can verify that the KLMS event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of KLMS events to KUMA
To configure the export of KLMS events to KUMA:
- Connect to the KLMS server over SSH and go to the Technical Support Mode menu.
- Use the klms-control utility to download the settings to the settings.xml file:
sudo /opt/kaspersky/klms/bin/klms-control --get-settings EventLogger -n -f /tmp/settings.xml - Make sure that the settings in the /tmp/settings.xml file have the following values; make changes if necessary:
<siemSettings><enabled>1</enabled><facility>Local1</facility>...</siemSettings> - Apply settings with the following command:
sudo /opt/kaspersky/klms/bin/klms-control --set-settings EventLogger -n -f /tmp/settings.xml - To send events via UDP, make the following changes to the /etc/rsyslog.conf configuration file:
$WorkDirectory /var/lib/rsyslog$ActionQueueFileName ForwardToSIEM$ActionQueueMaxDiskSpace 1g$ActionQueueSaveOnShutdown on$ActionQueueType LinkedList$ActionResumeRetryCount -1local1.* @<<IP address of the KUMA collector>:<port of the collector>>If you want to send events over TCP, the last line should be as follows:
local1.* @@<<IP address of the KUMA collector>:<port of the collector>> - Save your changes.
- Restart the rsyslog service with the following command:
sudo systemctl restart rsyslog.service
Configuring receipt of KSMG events
You can configure the receipt of events from the Kaspersky Secure Mail Gateway (KSMG) 1.1 mail traffic analysis and filtering system in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring export of KSMG events to KUMA
- Creating a KUMA collector for receiving KSMG events
To receive KSMG events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] KSMG normalizer.
- Installing a KUMA collector for receiving KSMG events
- Verifying receipt of KSMG events in the KUMA collector
You can verify that the KSMG event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of KSMG events to KUMA
To configure the export of KSMG events to KUMA:
- Connect to the KSMG server via SSH using an account with administrator rights.
- Use the ksmg-control utility to download the settings to the settings.xml file:
sudo /opt/kaspersky/ksmg/bin/ksmg-control --get-settings EventLogger -n -f /tmp/settings.xml - Make sure that the settings in the /tmp/settings.xml file have the following values; make changes if necessary:
<siemSettings><enabled>1</enabled><facility>Local1</facility> - Apply settings with the following command:
sudo /opt/kaspersky/ksmg/bin/ksmg-control --set-settings EventLogger -n -f /tmp/settings.xml - To send events via UDP, make the following changes to the /etc/rsyslog.conf configuration file:
$WorkDirectory /var/lib/rsyslog$ActionQueueFileName ForwardToSIEM$ActionQueueMaxDiskSpace 1g$ActionQueueSaveOnShutdown on$ActionQueueType LinkedList$ActionResumeRetryCount -1local1.* @<<IP address of the KUMA collector>:<port of the collector>>If you want to send events over TCP, the last line should be as follows:
local1.* @@<<IP address of the KUMA collector>:<port of the collector>> - Save your changes.
- Restart the rsyslog service with the following command:
sudo systemctl restart rsyslog.service
Configuring receipt of PT NAD events
You can configure the receipt of PT NAD events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring export of PT NAD events to KUMA.
- Creating a KUMA collector for receiving PT NAD events.
To receive PT NAD events using Syslog, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] PT NAD json normalizer.
- Installing a KUMA collector for receiving PT NAD events.
- Verifying receipt of PT NAD events in the KUMA collector.
You can verify that the PT NAD event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of PT NAD events to KUMA
Configuring the export of events from PT NAD 11 to KUMA over Syslog involves the following steps:
- Configuring the ptdpi-worker@notifier module.
- Configuring the sending of syslog messages with information about activities, attacks and indicators of compromise.
Configuring the ptdpi-worker@notifier module.
To enable the sending of information about detected information security threats, you must configure the ptdpi-worker@notifier module.
In a multi-server configuration, these instructions must be followed on the primary server.
To configure the ptdpi-worker@notifier module:
- Open the /opt/ptsecurity/etc/ptdpi.settings.yaml file:
sudo nano /opt/ptsecurity/etc/ptdpi.settings.yaml - In the General settings group of settings, uncomment the 'workers' setting and add 'notifier' to its list of values.
For example:
workers: ad alert dns es hosts notifier - To the end of the file, append a line of the form: notifier.yaml.nad_web_url: <URL of the PT NAD web interface>
For example:
notifier.yaml.nad_web_url: https://ptnad.example.comThe ptdpi-worker@notifier module uses the specified URL to generate links to session and activity cards when sending messages.
- Restart the sensor:
sudo ptdpictl restart-all
The ptdpi-worker@notifier module is configured.
Configuring the sending of syslog messages with information about activities, attacks and indicators of compromise
The settings listed in the following instructions may not be present in the configuration file. If a setting is missing, you must add it to the file.
In a multi-server PT NAD configuration, edit the settings on the primary server.
To configure the sending of syslog messages with information about activities, attacks and indicators of compromise:
- Open the /opt/ptsecurity/etc/ptdpi.settings.yaml file:
sudo nano /opt/ptsecurity/etc/ptdpi.settings.yaml - By default, PT NAD sends activity information in Russian. To receive information in English, change the value of the notifier.yaml.syslog_notifier.locale setting to "en".
For example:
notifier.yaml.syslog_notifier.locale: en - In the notifier.yaml.syslog_notifier.addresses setting, add a section with settings for sending events to KUMA.
The <Connection name> setting can only contain Latin letters, numerals, and the underscore character.
For the 'address' setting, specify the IP address of the KUMA collector.
Other settings can be omitted, in which case the default values are used.
notifier.yaml.syslog_notifier.addresses:<Connection name>:address: <For sending to a remote server, specify protocol: UDP (default) or TCP, address and port; for local connection, specify Unix domain socket>doc_types: [<Comma-separated message types ('alert' for information about attacks, 'detection' for activities, and 'reputation' for information about indicators of compromise). By default, all types of messages are sent>]facility: <Numeric value of the subject category>ident: <software tag><Connection name>:...The following is a sample configuration of sending syslog messages with information about activities, attacks, and indicators of compromise to two remote servers via TCP and UDP without writing to the local log:
notifier.yaml.syslog_notifier.addresses:remote1:address: tcp://198.51.100.1:1514remote2:address: udp://198.51.100.2:2514 - Save your changes in the /opt/ptsecurity/etc/ptdpi.settings.yaml.
- Restart the ptdpi-worker@notifier module:
sudo ptdpictl restart-worker notifier
The sending of events to KUMA via Syslog is configured.
Page topConfiguring receipt of events using the MariaDB Audit Plugin
KUMA allows auditing events using the MariaDB Audit Plugin. The plugin supports MySQL 5.7 and MariaDB. The audit plugin does not support MySQL 8. Detailed information about the plugin is available on the official MariaDB website.
We recommend using MariaDB Audit Plugin version 1.2 or later.
Configuring event receiving consists of the following steps:
- Configuring the MariaDB Audit Plugin to send MySQL events and configuring the Syslog server to send events.
- Configuring the MariaDB Audit Plugin to send MariaDB events and configuring the Syslog server to send events.
- Creating a KUMA Collector for MySQL 5.7 and MariaDB Events.
To receive MySQL 5.7 and MariaDB events using the MariaDB Audit Plugin, in the KUMA Collector Installation Wizard, at the Event parsing step, in the Normalizer field, select [OOTB] MariaDB Audit Plugin syslog.
- Installing a collector in the KUMA network infrastructure.
- Verifying receipt of MySQL and MariaDB events by the KUMA collector.
To verify that the MySQL and MariaDB event source server is configured correctly, you can search for related events.
Configuring the MariaDB Audit Plugin to send MySQL events
The MariaDB Audit Plugin is supported for MySQL 5.7 versions up to 5.7.30 and is bundled with MariaDB.
To configure MySQL 5.7 event reporting using the MariaDB Audit Plugin:
- Download the MariaDB distribution kit and extract it.
You can download the MariaDB distribution kit from the official MariaDB website. The operating system of the MariaDB distribution must be the same as the operating system on which MySQL 5.7 is running.
- Connect to MySQL 5.7 using an account with administrator rights by running the following command:
mysql -u<username>-p - To get the directory where the MySQL 5.7 plugins are located, on the MySQL 5.7 command line, run the following command:
SHOW GLOBAL VARIABLES LIKE 'plugin_dir' - In the directory obtained at step 3, copy the MariaDB Audit Plugin from
<directory to which the distribution kit was extracted>/mariadb-server-<version>/lib/plugins/server_audit.so. - On the operating system command line, run the following command:
chmod 755<directory to which the distribution kit was extracted>server_audit.soFor example:
chmod 755 /usr/lib64/mysql/plugin/server_audit.so - On the MySQL 5.7 command line, run the following command:
install plugin server_audit soname 'server_audit.so' - Create a backup copy of the /etc/mysql/mysql.conf.d/mysqld.cnf configuration file.
- In the configuration file /etc/mysql/mysql.conf.d/mysqld.cnf, in the
[mysqld]section, add the following lines:server_audit_logging=1server_audit_events=connect,table,query_ddl,query_dml,query_dclserver_audit_output_type=SYSLOGserver_audit_syslog_facility=LOG_SYSLOGIf you want to disable event export for certain audit event groups, remove some of the values from the
server_audit_eventssetting. Descriptions of settings are available on the MariaDB Audit Plugin vendor's website. - Save changes to the configuration file.
- Restart the MariaDB service by running one of the following commands:
systemctl restart mysqldfor a system with systemd initialization.service mysqld restartfor a system with init initialization.
MariaDB Audit Plugin for MySQL 5.7 is configured. If necessary, you can run the following commands on the MySQL 5.7 command line:
show pluginsto check the list of current plugins.SHOW GLOBAL VARIABLES LIKE 'server_audit%'to check the current audit settings.
Configuring the MariaDB Audit Plugin to send MariaDB Events
The MariaDB Audit Plugin is included in the MariaDB distribution kit starting with versions 5.5.37 and 10.0.10.
To configure MariaDB event export using the MariaDB Audit Plugin:
- Connect to MariaDB using an account with administrator rights by running the following command:
mysql -u<username>-p - To check if the plugin is present in the directory where operating system plugins are located, run the following command on the MariaDB command line:
SHOW GLOBAL VARIABLES LIKE 'plugin_dir' - On the operating system command line, run the following command:
ll<directory obtained by the previous command>| grep server_audit.soIf the command output is empty and the plugin is not present in the directory, you can either copy the MariaDB Audit Plugin to that directory or use a newer version of MariaDB.
- On the MariaDB command line, run the following command:
install plugin server_audit soname 'server_audit.so' - Create a backup copy of the /etc/mysql/my.cnf configuration file.
- In the /etc/mysql/my.cnf configuration file, in the
[mysqld]section, add the following lines:server_audit_logging=1server_audit_events=connect,table,query_ddl,query_dml,query_dclserver_audit_output_type=SYSLOGserver_audit_syslog_facility=LOG_SYSLOGIf you want to disable event export for certain audit event groups, remove some of the values from the
server_audit_eventssetting. Descriptions of settings are available on the MariaDB Audit Plugin vendor's website. - Save changes to the configuration file.
- Restart the MariaDB service by running one of the following commands:
systemctl restart mariadbfor a system with systemd initialization.service mariadb restartfor a system with init initialization.
MariaDB Audit Plugin for MariaDB is configured. If necessary, you can run the following commands on the MariaDB command line:
show pluginsto check the list of current plugins.SHOW GLOBAL VARIABLES LIKE 'server_audit%'to check the current audit settings.
Configuring a Syslog server to send events
The rsyslog service is used to transmit events from the server to the collector.
To configure the sending of events from the server where MySQL or MariaDB is installed to the collector:
- Before making any changes, create a backup copy of the /etc/rsyslog.conf configuration file.
- To send events via UDP, add the following line to the /etc/rsyslog.conf configuration file:
*.* @<IP address of the KUMA collector>:<port of the KUMA collector>For example:
*.* @192.168.1.5:1514If you want to send events over TCP, the line should be as follows:
*.* @@192.168.1.5:2514Save changes to the /etc/rsyslog.conf configuration file.
- Restart the rsyslog service by executing the following command:
sudo systemctl restart rsyslog.service
Configuring receipt of Apache Cassandra events
KUMA allows receiving information about Apache Cassandra events.
Configuring event receiving consists of the following steps:
- Configuring Apache Cassandra event logging in KUMA.
- Creating a KUMA collector for Apache Cassandra events.
To receive Apache Cassandra events, in the KUMA Collector Installation Wizard, at the Transport step, select a file type connector; at the Event parsing step, in the Normalizer field, select [OOTB] Apache Cassandra file.
- Installing a collector in the KUMA network infrastructure.
- Verifying receipt of Apache Cassandra events in the KUMA collector.
To verify that the Apache Cassandra event source server is configured correctly, you can search for related events.
Configuring Apache Cassandra event logging in KUMA
To configuring Apache Cassandra event logging in KUMA:
- Make sure that the server where Apache Cassandra is installed has 5 GB of free disk space.
- Connect to the Apache Cassandra server using an account with administrator rights.
- Before making changes, create backup copies of the following configuration files:
- /etc/cassandra/cassandra.yaml
- /etc/cassandra/logback.xml
- Make sure that the settings in the /etc/cassandra/cassandra.yaml configuration file have the following values; make changes if necessary:
- in the
audit_logging_optionssection, set theenabledsetting totrue. - in the
loggersection, set theclass_namesetting toFileAuditLogger.
- in the
- Add the following lines to the /etc/cassandra/logback.xml configuration file:
<!-- Audit Logging (FileAuditLogger) rolling file appender to audit.log --><appender name="AUDIT" class="ch.qos.logback.core.rolling.RollingFileAppender"><file>${cassandra.logdir}/audit/audit.log</file><rollingPolicy class="ch.qos.logback.core.rolling.SizeAndTimeBasedRollingPolicy"><!-- rollover daily --><fileNamePattern>${cassandra.logdir}/audit/audit.log.%d{yyyy-MM-dd}.%i.zip</fileNamePattern><!-- each file should be at most 50MB, keep 30 days worth of history, but at most 5GB --><maxFileSize>50MB</maxFileSize><maxHistory>30</maxHistory><totalSizeCap>5GB</totalSizeCap></rollingPolicy><encoder><pattern>%-5level [%thread] %date{ISO8601} %F:%L - %replace(%msg){'\n', ' '}%n</pattern></encoder></appender><!-- Audit Logging additivity to redirect audt logging events to audit/audit.log --><logger name="org.apache.cassandra.audit" additivity="false" level="INFO"><appender-ref ref="AUDIT"/></logger> - Save changes to the configuration file.
- Restart the Apache Cassandra service using the following commands:
sudo systemctl stop cassandra.servicesudo systemctl start cassandra.service
- After restarting, check the status of Apache Cassandra using the following command:
sudo systemctl status cassandra.serviceMake sure that the command output contains the following sequence of characters:
Active: active (running)
Apache Cassandra event export is configured. Events are located in the /var/log/cassandra/audit/ directory, in the audit.log file (${cassandra.logdir}/audit/audit.log).
Page topConfiguring receipt of FreeIPA events
You can configure the receipt of FreeIPA events in KUMA via the Syslog protocol.
Configuring event receiving consists of the following steps:
- Configuring export of FreeIPA events to KUMA.
- Creating a KUMA collector for receiving FreeIPA events.
To receive FreeIPA events, in the KUMA Collector Setup Wizard, at the Event parsing step, in the Normalizer field, select [OOTB] FreeIPA.
- Installing the KUMA collector in the network infrastructure.
- Verifying receipt of FreeIPA events by KUMA.
To verify that the FreeIPA event source server is configured correctly, you can search for related events.
Configuring export of FreeIPA events to KUMA
To configure the export of FreeIPA events to KUMA via the Syslog protocol in JSON format:
- Connect to the FreeIPA server via SSH using an account with administrator rights.
- In the /etc/rsyslog.d/ directory, create a file named freeipa-to-siem.conf.
- Add the following lines to the /etc/rsyslog.d/freeipa-to-siem.conf configuration file:
template(name="ls_json" type="list" option.json="on"){ constant(value="{")constant(value="\"@timestamp\":\"") property(name="timegenerated" dateFormat="rfc3339")constant(value="\",\"@version\":\"1")constant(value="\",\"message\":\"") property(name="msg")constant(value="\",\"host\":\"") property(name="fromhost")constant(value="\",\"host_ip\":\"") property(name="fromhost-ip")constant(value="\",\"logsource\":\"") property(name="fromhost")constant(value="\",\"severity_label\":\"") property(name="syslogseverity-text")constant(value="\",\"severity\":\"") property(name="syslogseverity")constant(value="\",\"facility_label\":\"") property(name="syslogfacility-text")constant(value="\",\"facility\":\"") property(name="syslogfacility")constant(value="\",\"program\":\"") property(name="programname")constant(value="\",\"pid\":\"") property(name="procid")constant(value="\",\"syslogtag\":\"") property(name="syslogtag")constant(value="\"}\n")}*.* @<IP address of the KUMA collector>:<port of the KUMA collector KUMA>;ls_jsonYou can fill in the last line in accordance with the selected protocol:
*.* @<192.168.1.10>:<1514>;ls_jsonfor sending events over UDP*.* @@<192.168.2.11>:<2514>;ls_jsonfor sending events over TCP - Add the following lines to the /etc/rsyslog.conf configuration file:
$IncludeConfig /etc/freeipa-to-siem.conf$RepeatedMsgReduction off - Save changes to the configuration file.
- Restart the rsyslog service by executing the following command:
sudo systemctl restart rsyslog.service
Configuring receipt of VipNet TIAS events
You can configure the receipt of ViPNet TIAS events in KUMA via the Syslog protocol.
Configuring event receiving consists of the following steps:
- Configuring export of ViPNet TIAS events to KUMA.
- Creating a KUMA collector for receiving ViPNet TIAS events.
To receive ViPNet TIAS events using Syslog, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] Syslog-CEF normalizer.
- Installing a KUMA collector for receiving ViPNet TIAS events.
- Verifying receipt of ViPNet TIAS events in KUMA.
You can verify that ViPNet TIAS event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of ViPNet TIAS events to KUMA
To configure the export of ViPNet TIAS events to KUMA via the syslog protocol:
- Connect to the ViPNet TIAS web interface under a user account with administrator rights.
- Go to the Management – Integrations section.
- On the Integration page, go to the Syslog tab.
- In the toolbar of the list of receiving servers, click New server.
- This opens the new server card; in that card:
- In the Server address field, enter the IP address or domain name of the KUMA collector.
For example, 10.1.2.3 or syslog.siem.ru
- In the Port field, specify the inbound port of the KUMA collector. The default port number is 514.
- In the Protocol list, select the transport layer protocol that the KUMA collector is listening on. UDP is selected by default.
- In the Organization list, use the check boxes to select the organizations of the ViPNet TIAS infrastructure.
Messages are sent only for incidents detected based on events received from sensors of selected organizations of the infrastructure.
- In the Status list, use check boxes to select incident statuses.
Messages are sent only when selected statuses are assigned to incidents.
- In the Severity level list, use check boxes to select the severity levels of the incidents.
Messages are sent only about incidents with the selected severity levels. By default, only the high severity level is selected in the list.
- In the UI language list, select the language in which you want to receive information about incidents in messages. Russian is selected by default.
- In the Server address field, enter the IP address or domain name of the KUMA collector.
- Click Add.
- In the toolbar of the list, set the Do not send incident information in CEF format toggle switch to enabled.
As a result, when new incidents are detected or the statuses of previously detected incidents change, depending on the statuses selected during configuration, the corresponding information is sent to the specified addresses of receiving servers via the syslog protocol in CEF format.
- Click Save changes.
Export of events to the KUMA collector is configured.
Page topConfiguring receipt of Sendmail events
You can configure the receipt of Sendmail mail agent events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring Sendmail logging.
- Configuring the event source server.
- Creating a KUMA collector.
To receive Sendmail events, use the following values in the Collector Installation Wizard:
- At the Event parsing step, select the [OOTB] Sendmail syslog normalizer.
- At the Transport step, select the tcp or udp connector type.
- Installing KUMA collector.
- Verifying receipt of Sendmail events in the KUMA collector
You can verify that the Sendmail event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring Sendmail logging
By default, events of the Sendmail system are logged to syslog.
To make sure that logging is configured correctly:
- Connect via SSH to the server on which the Sendmail system is installed.
- Run the following command:
cat /etc/rsyslog.d/50-default.confThe command should return the following string:
mail.* -/var/log/mail.log
If logging is configured correctly, you can proceed to configuring the export of Sendmail events.
Page topConfiguring export of Sendmail events
Events are sent from the Sendmail mail agent server to the KUMA collector using the rsyslog service.
To configure transmission of Sendmail events to the collector:
- Connect to the server where Sendmail is installed using an account with administrative privileges.
- In the /etc/rsyslog.d/ directory, create the Sendmail-to-siem.conf file and add the following line to it:
If $programname contains 'sendmail' then @<<IP address of the collector>:<port of the collector>>Example:
If $programname contains 'sendmail' then @192.168.1.5:1514If you want to send events via TCP, the contents of the file must be as follows:
If $programname contains 'sendmail' then @@<<IP address of the collector>:<port of the collector>> - Create a backup copy of the /etc/rsyslog.conf file.
- Add the following lines to the /etc/rsyslog.conf configuration file:
$IncludeConfig /etc/Sendmail-to-siem.conf$RepeatedMsgReduction off - Save your changes.
- Restart the rsyslog service by executing the following command:
sudo systemctl restart rsyslog.service
Configuring receipt of Nextcloud events
You can configure the receipt of Nextcloud 26.0.4 events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring audit of Nextcloud events.
- Configuring a Syslog server to send events.
The rsyslog service is used to transmit events from the server to the collector.
- Creating a KUMA collector for receiving Nextcloud events.
To receive Nextcloud events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] Nextcloud syslog normalizer, and at the Transport step select the tcp or udp connector type.
- Installing KUMA collector for receiving Nextcloud events
- Verifying receipt of Nextcloud events in the KUMA collector
You can verify that the Nextcloud event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring audit of Nextcloud events
To configure the export of Nextcloud events to KUMA:
- On the server where Nextcloud is installed, create a backup copy of the /home/localuser/www/nextcloud/config/config.php configuration file.
- Edit the /home/localuser/www/nextcloud/config/config.php Nextcloud configuration file.
- Edit the settings as follows:
'log_type' => 'syslog','syslog_tag' => 'Nextcloud','logfile' => '','loglevel' => 0,'log.condition' => ['apps' => ['admin_audit'],], - Restart the Nextcloud service:
sudo service restart nextcloud
Export of events to the KUMA collector is configured.
Page topConfiguring a Syslog server to send Nextcloud events
To configure the sending of events from the server where Nextcloud is installed to the collector:
- In the /etc/rsyslog.d/ directory, create a Nextcloud-to-siem.conf file with the following content:
If $programname contains 'Nextcloud' then @<IP address of the collector>:<port of the collector>Example:
If $programname contains 'Nextcloud' then @192.168.1.5:1514If you want to send events via TCP, the contents of the file must be as follows:
If $programname contains 'Nextcloud' then @<IP address of the collector>:<port of the collector> - Save changes to the Nextcloud-to-siem.conf configuration file.
- Create a backup copy of the /etc/rsyslog.conf file.
- Add the following lines to the /etc/rsyslog.conf configuration file:
$IncludeConfig /etc/Nextcloud-to-siem.conf$RepeatedMsgReduction off - Save your changes.
- Restart the rsyslog service by executing the following command:
sudo systemctl restart rsyslog.service
The export of Nextcloud events to the collector is configured.
Page topConfiguring receipt of Snort events
You can configure the receipt of Snort 3 events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring logging of Snort events.
- Creating a KUMA collector for receiving Snort events.
To receive Snort events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] Snort 3 json file normalizer, and at the Transport step, select the file connector type.
- Installing a KUMA collector for receiving Snort events
- Verifying receipt of Snort events in the KUMA collector
You can verify that the Snort event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring logging of Snort events
Make sure that the server running Snort has at least 500 MB of free disk space for storing a single Snort event log.
When the log reaches 500 MB, Snort automatically creates a new file with a name that includes the current time in unixtime format.
We recommend monitoring disk space usage.
To configure Snort event logging:
- Connect to the server where Snort is installed using an account with administrative privileges.
- Edit the Snort configuration file. To do so, run the following command on the command line:
sudo vi /usr/local/etc/snort/snort.lua - In the configuration file, edit the alert_json block:
alert_json ={file = true,limit = 500,fields = 'seconds action class b64_data dir dst_addr dst_ap dst_port eth_dst eth_len \eth_src eth_type gid icmp_code icmp_id icmp_seq icmp_type iface ip_id ip_len msg mpls \pkt_gen pkt_len pkt_num priority proto rev rule service sid src_addr src_ap src_port \target tcp_ack tcp_flags tcp_len tcp_seq tcp_win tos ttl udp_len vlan timestamp',} - To complete the configuration, run the following command:
sudo /usr/local/bin/snort -c /usr/local/etc/snort/snort.lua -s 65535 -k none -l /var/log/snort -i<name of the interface that Snort is listening on>-m 0x1b
As a result, Snort events are logged to /var/log/snort/alert_json.txt.
Page topConfiguring receipt of Suricata events
You can configure the receipt of Suricata 7.0.1 events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring export of Suricata events to KUMA
- Creating a KUMA collector for receiving Suricata events.
To receive Suricata events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] Suricata json file normalizer, and at the Transport step, select the file connector type.
- Installing KUMA collector for receiving Suricata events
- Verifying receipt of Suricata events in the KUMA collector
You can verify that the Suricata event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring audit of Suricata events
To configure Suricata event logging:
- Connect via SSH to the server that has administrative accounts.
- Create a backup copy of the /etc/suricata/suricata.yaml file.
- Set the following values in the eve-log section of the /etc/suricata/suricata.yaml configuration file:
- eve-log:enabled: yesfiletype: regular #regular|syslog|unix_dgram|unix_stream|redisfilename: eve.json - Save your changes to the /etc/suricata/suricata.yaml configuration file.
As a result, Suricata events are logged to the /usr/local/var/log/suricata/eve.json file.
Suricata does not support limiting the size of the eve.json event file. If necessary, you can manage the log size by using rotation. For example, to configure hourly log rotation, add the following lines to the configuration file:
outputs:
- eve-log:
filename: eve-%Y-%m-%d-%H:%M.json
rotate-interval: hour
Configuring receipt of FreeRADIUS events
You can configure the receipt of FreeRADIUS 3.0.26 events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring audit of FreeRADIUS events
- Configuring a Syslog server to send FreeRADIUS events.
- Creating a KUMA collector for receiving FreeRADIUS events.
To receive FreeRADIUS events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] FreeRADIUS syslog normalizer, and at the Transport step, select the tcp or udp connector type.
- Installing KUMA collector for receiving FreeRADIUS events.
- Verifying receipt of FreeRADIUS events in the KUMA collector.
You can verify that the FreeRADIUS event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring audit of FreeRADIUS events
To configure event audit in the FreeRADIUS system:
- Connect to the server where the FreeRADIUS system is installed using an account with administrative privileges.
- Create a backup copy of the FreeRADIUS configuration file:
sudo cp /etc/freeradius/3.0/radiusd.conf /etc/freeradius /3.0/radiusd.conf.bak - Open the FreeRADIUS configuration file for editing:
sudo nano /etc/freeradius/3.0/radiusd.conf - In the 'log' section, edit the settings as follows:
destination = syslogsyslog_facility = daemonstripped_names = noauth = yesauth_badpass = yesauth_goodpass = yes - Save the configuration file.
FreeRADIUS event audit is configured.
Page topConfiguring a Syslog server to send FreeRADIUS events
The rsyslog service is used to transmit events from the FreeRADIUS server to the KUMA collector.
To configure the sending of events from the server where FreeRADIUS is installed to the collector:
- In the /etc/rsyslog.d/ directory, create the FreeRADIUS-to-siem.conf file and add the following line to it:
If $programname contains 'radiusd' then @<IP address of the collector>:<port of the collector>If you want to send events via TCP, the contents of the file must be as follows:
If $programname contains 'radiusd' then @<IP address of the collector>:<port of the collector> - Create a backup copy of the /etc/rsyslog.conf file.
- Add the following lines to the /etc/rsyslog.conf configuration file:
$IncludeConfig /etc/FreeRADIUS-to-siem.conf$RepeatedMsgReduction off - Save your changes.
- Restart the rsyslog service:
sudo systemctl restart rsyslog.service
The export of events from the FreeRADIUS server to the KUMA collector is configured.
Page topConfiguring receipt of zVirt events
You can configure the receipt of zVirt 3.1 events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Configuring export of zVirt events to KUMA.
- Creating a KUMA collector for receiving zVirt events.
To receive zVirt events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] OrionSoft zVirt syslog normalizer, and at the Transport step, select the tcp or udp connector type.
- Installing KUMA collector for receiving zVirt events
- Verifying receipt of zVirt events in the KUMA collector
You can verify that the zVirt event source server is correctly configured in the Searching for related events section of the KUMA web interface.
Configuring export of zVirt events
ZVirt can send events to external systems in Hosted Engine installation mode.
To configure the export of zVirt events to KUMA:
- In the zVirt web interface, under Resources, select Virtual machines.
- Select the machine that is running the HostedEngine virtual machine and click Edit.
- In the Edit virtual machine window, go to the Logging section.
- Select the Determine Syslog server address check box.
- In the text box, enter the collector information in the following format:
<IP address or FQDN of the KUMA collector>:<port of the KUMA collector>. - If you want to use TCP instead of UDP for sending logs, select the Use TCP connection check box.
Event export is configured.
Page topConfiguring receipt of Zeek IDS events
You can configure the receipt of Zeek IDS 1.8 events in the KUMA SIEM system.
Configuring event receiving consists of the following steps:
- Conversion of the Zeek IDS event log format.
The KUMA normalizer supports Zeek IDS logs in the JSON format. To send events to the KUMA normalizer, log files must be converted to the JSON format.
- Creating a KUMA collector for receiving Zeek IDS events.
To receive Zeek IDS events, in the Collector Installation Wizard, at the Event parsing step, select the [OOTB] ZEEK IDS json file normalizer, and at the Transport step, select the file connector type.
- Installing KUMA collector for receiving Zeek IDS events
- Verifying receipt of Zeek IDS events in the KUMA collector
You can verify that the Zeek IDS event source server is correctly configured in the Searching for related events section of the KUMA web interface.
New Topic (202)
By default, Zeek IDS events are logged in files in the /opt/zeek/logs/current directory.
The "[OOTB] ZEEK IDS json file" normalizer supports Zeek IDS logs in the JSON format. To send events to the KUMA normalizer, log files must be converted to the JSON format.
This procedure must be repeated every time before receiving Zeek IDS events.
To convert the Zeek IDS event log format:
- Connect to the server where Zeek IDS is installed using an account with administrative privileges.
- Create the directory where JSON event logs must be stored:
sudo mkdir /opt/zeek/logs/zeek-json - Change to this directory:
sudo cd /opt/zeek/logs/zeek-json - Run the command that uses the jq utility to convert the original event log format to the target format:
jq . -c<path to the log file to be converted to a different format>>><new file name>.logExample:
jq . -c /opt/zeek/logs/current/conn.log >> conn.log
As a result of running the command, a new file is created in the /opt/zeek/logs/zeek-json directory if this file did not exist before. If the file was already present in the current directory, new information is appended to the end of the file.
Page top