Contents
- Data provision
- Data provision under the End User License Agreement
- Data provision under the End User License Agreement on the territory of the European Union, the United Kingdom, Brazil, or by California residents
- Data provision to Kaspersky Security Network
- Saving data to the application operation report
- Saving service data on application operation
- About using the application in the European Union, the United Kingdom, Brazil, or by California residents
- About Kaspersky Free
- How to install or remove the application
- What is My Kaspersky account for?
- How to protect another device
- Switching from Kaspersky Free to a different subscription
- How to configure the application interface
- Security
- Assessing computer protection status and resolving security issues
- How to fix security issues on your PC
- How to restore a deleted or disinfected file
- Scanning the computer
- Updating anti-virus databases and application modules
- Pre-Kaspersky virus removal
- Weak Settings Scan
- Scanning email messages
- Protection using hardware virtualization
- About protection using Antimalware Scan Interface
- Game mode
- Protecting personal data on the Internet
- Security news
- Data Leak Checker
- How to uninstall incompatible applications
- How to pause and resume computer protection
- How to restore the default settings of the application
- How to view the application operation report
- How to apply the application settings on another computer
- Participating in Kaspersky Security Network
- Limitations and warnings
- Other sources of information about the application
- Network settings for interaction with external services
- Glossary
- Activation code
- Anti-virus databases
- Application modules
- Blocking an object
- Compressed file
- Database of malicious web addresses
- Database of phishing web addresses
- Disk boot sector
- Exploit
- False positive
- Heuristic analyzer
- iChecker Technology
- Incompatible application
- Infected object
- Kaspersky Security Network (KSN)
- Kaspersky update servers
- License term
- Phishing
- Probably infected object
- Protection components
- Protocol
- Quarantine
- Rootkit
- Script
- Security level
- Startup objects
- Task
- Task settings
- Traces
- Traffic scanning
- Unknown virus
- Update
- Update package
- Virus
- Vulnerability
- Information about third-party code
- Trademark notices
Data provision
This section contains information on the specific data that you provide to Kaspersky. The Saving data to the application operation report subsection contains data that are stored locally on your computer and are not sent to Kaspersky.
Data provision under the End User License Agreement
This section contains information on the specific data that are provided to Kaspersky if you have installed the application version which is not intended for use in the European Union, the United Kingdom, Brazil, or by California residents.
Kaspersky protects the received information according to legal requirements and applicable rules of Kaspersky. The data is transmitted over encrypted channels.
In order to improve security awareness about new threats and their sources and in order to improve Your security protection level and the product’s operation, the Rightholder, with your consent that has been explicitly confirmed in the Kaspersky Security Network Data Collection Statement, is expressly entitled to receive such information. You can deactivate the Kaspersky Security Network service during installation. Also, You can activate and deactivate the Kaspersky Security Network service at any time in the Software settings window.
You further acknowledge and agree that any information gathered by Rightholder can be used to track and publish reports on security risk trends in the Rightholder’s sole and exclusive discretion.
If you do not wish for the information collected by the Software to be sent to the Rightholder, You should not activate and/or de-activate, the Kaspersky Security Network service.
Page top
Data provision under the End User License Agreement on the territory of the European Union, the United Kingdom, Brazil, or by California residents
This section contains information on the specific data that are provided to Kaspersky if you have installed the application version which is intended for use in the European Union, the United Kingdom, Brazil, or by California residents. The information mentioned in this section does not contain any personal data of the User and is needed for the operation of the Rightholder's Software, unless expressly stated otherwise.
To improve real-time protection, the quality of operation of the software, and timely detection and rectification of errors related to software installation, removal, and update mechanisms, as well as to keep track of the number of users, you agree to automatically provide the following data to Kaspersky while using the software:
To improve the quality of protection of the User performing payment transactions on the Internet, you agree to automatically provide the financial website with information about the name and version of the Software and the Software customization setting, the ID of the Software plug-in in the browser used to access the financial website, and the ID showing whether a safe browser or a regular browser was used.
The information received is protected by the Rightholder in the manner prescribed by the law and is required for the operation of the Software made available to use under the license.
Kaspersky may use the acquired statistical data based on the information received to monitor trends in computer security threats and publish reports on those threats.
Page top
Data provision to Kaspersky Security Network
The scope of data transmitted to Kaspersky Security Network is described in the Kaspersky Security Network Statement.
To view the Kaspersky Security Network Statement:
- Open the main application window.
- Click the
 button in the lower part of the application window.
button in the lower part of the application window.This opens the Settings window.
- Go to Security settings → Kaspersky Security Network.
The Kaspersky Security Network window opens showing the details of Kaspersky Security Network and Kaspersky Security Network participation settings.
- Click the Kaspersky Security Network Statement link to open the text of the Kaspersky Security Network Statement.
Saving data to the application operation report
Report files can contain personal data obtained during operation of protection components, such as File Anti-Virus component, Mail Anti-Virus, and Safe Browsing.
Report files can contain the following personal data:
- IP address of the user's device
- Online browsing history
- Versions of the browser and operating system
- Names of cookies and other files and paths to them
- Email address, sender, message subject
Report files are stored locally on your computer and are not transmitted to Kaspersky. Path to report files: %allusersprofile%\Kaspersky Lab\AVP21.8\Report\Database.
Reports are stored in the following files:
- reports.db
- reports.db-wal
- reports.db-shm (does not contain any personal data)
Report files are protected against unauthorized access if self-defense is enabled in Kaspersky Free. If self-defense is disabled, report files are not protected.
Page top
Saving service data on application operation
The application also processes and stores the following data, which may be needed for analyzing of operation errors:
- Data that is displayed in the application interface:
- Email address used to connect to My Kaspersky
- Website addresses that were added to the exclusions (displayed in the Network component and in the Reports window)
- License data
This data is stored locally in a non-modified form and can be viewed under any user account on the computer.
- Data on the system memory of Kaspersky Free processes at the moment when a memory dump is created.
- Data that is gathered when traces are enabled.
This data is stored locally in a modified form and can be viewed under any user account on the computer. This data is transmitted to Kaspersky only with your consent. The scope of data is described in the RDP.txt file in the following folder: %PROGRAMFILES%\Kaspersky Lab\Kaspersky 21.7\Doc\KFA\en-US.
Page top
About using the application in the European Union, the United Kingdom, Brazil, or by California residents
The versions of the application that Kaspersky and our partners distribute in the European Union, the United Kingdom, Brazil (as well as the versions intended to be used by California residents) meet the requirements of the regulations governing the collection and processing of personal data that have been established in these regions.
To install the application, you must accept the End User License Agreement and the terms of the Privacy Policy.
In addition, the Setup Wizard prompts you to accept the following agreements regarding how your personal data is processed:
- Kaspersky Security Network Statement. This statement allows Kaspersky experts to promptly receive information about threats detected on your computer, about applications being run and signed applications being downloaded, as well as operating system information to improve your protection.
- Statement regarding data processing for marketing purposes. This statement allows us to create more valuable offers for you.
You can accept or decline the Kaspersky Security Network Statement and Statement regarding data processing for marketing purposes at any time from the Settings → Security settings → Kaspersky Security Network window.
Page top
About Kaspersky Free
Kaspersky Free is an upgrade of the free version of protection. Switching to this upgrade gives you high-quality protection supplemented by advanced features and a user interface fully reworked for ease of use.
Moreover, you can always switch to a paid Kaspersky subscription without downloading and installing any additional software.
File Anti-Virus
File Anti-Virus prevents infection of the computer's file system. The component starts upon startup of the operating system, continuously remains in the computer's RAM, and scans all files that are opened, saved, or launched on your computer and all connected drives. Kaspersky Free intercepts each attempt to access a file and scans the file for known viruses and other malware. Further access to the file is allowed only if the file is not infected or is successfully disinfected. If a file cannot be disinfected for any reason, it is deleted. A copy of the file is moved to Quarantine when that happens. If an infected file is placed in the same location where the deleted file with the same name used to be, Quarantine saves only a copy of the last file. A copy of the previous file with the same name is not saved.
Mail Anti-Virus
Mail Anti-Virus scans incoming and outgoing email messages on your computer. An email message is available to the recipient only if it does not contain dangerous objects.
Safe Browsing
Safe Browsing intercepts and blocks the execution of scripts on websites if they pose a threat. Safe Browsing also monitors all web traffic and blocks access to dangerous websites.
Anti-Phishing
Anti-Phishing allows checking URLs to find out if they are included in the list of phishing URLs. This component is built into Safe Browsing.
System Watcher
The System Watcher component rolls back the changes made to the operating system by malicious or other activity of applications.
The component protects against malware, including:
- Exploits
- Screen lockers
- Encryptors that encrypt data
- Ransomware that encrypts data or blocks access to files or the system and extorts ransom for restoring the files or access to them
Disabling this component is not recommended.
Network Attack Blocker
Network Attack Blocker loads at operating system startup and tracks incoming network traffic for activities characteristic of network attacks. When an attempt to attack your computer is detected, Kaspersky Free blocks all network activity from the attacking computer that is aimed at your computer.
On-Screen Keyboard
On-Screen Keyboard prevents interception of data entered on the hardware keyboard and protects personal data against interception attempts that use screen shots.
Antimalware Scan Interface (AMSI)
Antimalware Scan Interface (AMSI) allows a third-party application that supports AMSI to send objects (for example, PowerShell scripts) to Kaspersky Free for additional scanning and to receive scan results for these objects.
What's new in the latest version of the application
The following new features and improvements are introduced in Kaspersky Free:
- Updated licensing terminology. Introducing easy-to-understand terms dealing with the subscription-based licensing model.
- A new window that lets you download other applications offered by Kaspersky and our partners (not available in some regions).
- You can now switch the application to a dark design theme or the design theme that is currently used by the operating system.
- Improved computer security statuses. In particular, we resolved the issue with the red status (for example, databases out of date) being displayed alongside an amber or green icon for a completed scan task.
- Improved animation in chat when the application runs for the first time.
- Improved scenario for region selection on application startup.
- Now you can install the Atom browser during Kaspersky Free installation (not available in some regions).
Hardware and software requirements
General requirements
- 1500 MB free disk space on the hard drive
- Processor that supports the SSE2 instruction set (except ARM).
- Internet access (for the application installation and activation, for the use of Kaspersky Security Network, and for updating databases and application modules)
- Microsoft Windows Installer 4.5 or later
- Microsoft .NET Framework 4 or later
- Microsoft .NET Desktop Runtime 5.x (5.0.10 or higher).
Operating system requirements
Operating system |
CPU |
Free RAM |
Restrictions |
|---|---|---|---|
Microsoft Windows 11 Home (21H2, 22H2) |
1 GHz or higher |
4 GB (for a 64-bit operating system) |
Windows Subsystem for Linux 2 (WSL2) is not supported.
|
Microsoft Windows 11 Enterprise (21H2, 22H2) |
|||
Microsoft Windows 11 Pro (21H2, 22H2) |
|||
Microsoft Windows 10 Home (versions: 1507, 1511, 1607, 1703, 1709, 1803, 1809, 1903, 1909, 2004, 20H2, 21H1, 21H2, 22H2) |
1 GHz or higher |
1 GB (for 32-bit operating systems) or 2 GB (for 64-bit operating systems) |
|
Microsoft Windows 10 Enterprise (versions: 1507, 1511, 1607, 1703, 1709, 1803, 1809, 1903, 1909, 2004, 20H2, 21H1, 21H2, 22H2) |
|||
Microsoft Windows 10 Pro (versions: 1507, 1511, 1607, 1703, 1709, 1803, 1809, 1903, 1909, 2004, 20H2, 21H1, 21H2, 22H2) |
|||
Microsoft Windows 8.1 (Service Pack 0 or later, Windows 8.1 Update) |
1 GHz or higher |
1 GB (for 32-bit operating systems) or 2 GB (for 64-bit operating systems) |
|
Microsoft Windows 8.1 Pro (Service Pack 0 or later, Windows 8.1 Update) |
|||
Microsoft Windows 8.1 Enterprise (Service Pack 0 or later, Windows 8.1 Update) |
|||
Microsoft Windows 8 (Service Pack 0 or later) |
1 GHz or higher |
1 GB (for 32-bit operating systems) or 2 GB (for 64-bit operating systems) |
|
Microsoft Windows 8 Pro (Service Pack 0 or later) |
|||
Microsoft Windows 8 Enterprise (Service Pack 0 or later) |
|||
Microsoft Windows 7 Starter (Service Pack 0 or later) |
1 GHz or higher
|
1 GB (for 32-bit operating systems) or 2 GB (for 64-bit operating systems)
|
|
Microsoft Windows 7 Home Basic (Service Pack 0 or later) |
|||
Microsoft Windows 7 Home Premium (Service Pack 0 or later) |
|||
Microsoft Windows 7 Professional (Service Pack 0 or later) |
|||
Microsoft Windows 7 Ultimate (Service Pack 0 or later) |
For Safe Browsing to work, the Base Filtering Engine service must be running in the operating system.
Browser support
The following browsers fully support the application:
- Chromium-based Microsoft Edge 77.x – 104.x;
- Mozilla Firefox versions 52.x – 105.x;
- Mozilla Firefox ESR 52.x, 60.x, 68.x, 78.x, 91.x, 102.x;
- Google Chrome versions 48.x – 105.x;
- Yandex Browser 18.3.1 – 22.9.1 (with limitations).
The following browsers support installing the Kaspersky Protection extension:
- Chromium-based Microsoft Edge 77.x – 104.x;
- Mozilla Firefox versions 52.x – 105.x;
- Mozilla Firefox ESR 52.x, 60.x, 68.x, 78.x, 91.x, 102.x;
- Google Chrome versions 48.x – 105.x.
The following browsers support On-Screen Keyboard and scanning of encrypted connections:
- Chromium-based Microsoft Edge 77.x – 104.x;
- Mozilla Firefox versions 52.x – 105.x;
- Mozilla Firefox ESR 52.x, 60.x, 68.x, 78.x, 91.x; 102.x;
- Google Chrome 48.x – 105.x.
Newer versions of browsers can be supported if the browser supports the corresponding technology.
Kaspersky Free supports Google Chrome and Mozilla Firefox in 32-bit and in 64-bit operating systems.
Requirements for tablet computers
- Microsoft Windows 8, Microsoft Windows 8.1, Microsoft Windows 10, Microsoft Windows 11;
- Intel Celeron processor with a clock speed of 1.66 GHz or faster;
- 1000 MB free RAM.
Requirements for netbooks
- Intel Atom CPU 1.60 GHz or faster;
- 1024 MB free RAM;
- 10.1-inch display with 1024x768 screen resolution;
- Intel GMA 950 graphics core or later.
About your subscription
The subscription determines your application usage settings (subscription expiration date and the number of protected devices). Your subscription is provided in accordance with the End User License Agreement.
Subscription entitles you to the following kinds of services:
- The right to use the application on one or several devices.
The number of devices on which you may use the application is specified in the End User License Agreement.
- Updating databases and providing new versions of the application.
- Notifications upon releases of new versions of Kaspersky applications, as well as notifications about new viruses and virus outbreaks.
The Kaspersky Free subscription is renewed without your intervention.
Page top
Compatibility with other Kaspersky applications
Kaspersky Free is compatible with the following Kaspersky applications:
- Kaspersky Safe Kids 1.5
- Kaspersky Password Manager 10
- Kaspersky Software Updater 2.1
- Kaspersky Virus Removal Tool 2015, 2020
- Kaspersky VPN Secure Connection 4.0, 5.0, 5.1, 5.2, 5.3, 5.4, 5.5, 5.6, 5.7, 5.8.
How to install the application
The application is installed to your computer in interactive mode using the Setup Wizard.
The Wizard consists of a series of windows (steps). The number and sequence of steps in the Wizard depend on the region where you install the application. In some regions, the Wizard prompts you to accept additional agreements regarding how your personal data is processed and to confirm that you are over the age of 16. To stop the Wizard's activity at any step of installation, close the Wizard window.
To install the application on your computer,
run the executable file of the Setup and Uninstall Wizard downloaded from the Internet.
You can also install the application from the command prompt.
The Setup Wizard goes through the following steps:
- Starting installation
During this step, the Wizard prompts you to install the application.
Depending on the installation type and the localization language, during this step the Wizard may prompt you to view the End User License Agreement concluded between you and Kaspersky, and ask whether you want to participate in Kaspersky Security Network.
- Installing the application
Installation of the application can take some time. Wait for it to finish. Upon installation completion, the Setup Wizard automatically proceeds to the next step.
- Completing the installation
During this step, the Wizard informs you of the completion of application installation.
All necessary application components will be automatically started immediately after installation is complete.
In some cases, you may need to restart your operating system to complete installation.
Along with the application, plug-ins for browsers are installed to ensure safe Internet browsing.
To continue using the application, you must connect to My Kaspersky and complete the activation.
Page top
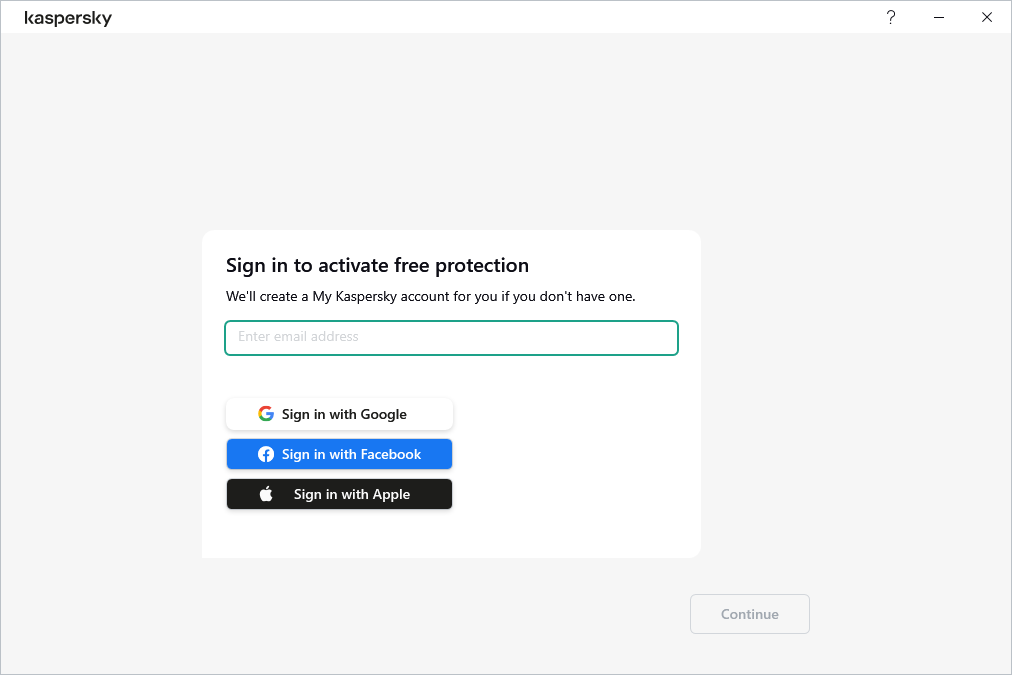
How to activate the application
You can activate the application by logging into your My Kaspersky account from the device on which you are installing the application. Kaspersky Free does not work if your device is not connected to your account. You can create an account in the account connection window during application activation or on My Kaspersky website. You can also use credentials from other Kaspersky resources to sign in to your account.
You can sign in to your My Kaspersky account using your email address and password, or with your Google, Facebook, or Apple account. If you already have an account, you can configure quick sign-in with your Google, Facebook, or Apple account in the window used for connecting your device to your My Kaspersky account. This is possible if, when creating your My Kaspersky account, you used the email address from your Google, Facebook, or Apple account.
Signing in with Facebook and Google is not available in some regions.
The application automatically connects to My Kaspersky if you downloaded the application from your account or previously entered your account credentials in a different Kaspersky application on the same device.
An Internet connection is required for activation of the application.
To activate the application:
In the account connection window, select the connection method that you find the most convenient:
- Sign in with an email address. Enter your email address in the text box. A message with a password creation link is sent to the specified email address.
If you have configured two-step verification in your My Kaspersky account, a text message containing the verification code is sent to your phone. In the entry field, enter the verification code and click Continue.
- Sign in with Google, Facebook, or Apple account.
- Click Sign in with Google, Sign in with Facebook, or Sign in with Apple.
This opens a browser window; in that window, sign in to your Google, Facebook, or Apple account and allow the application to gain access to your email address.
If you do not have a Google, Facebook, or Apple account, you can create one and proceed with configuring quick sign-in to My Kaspersky.
If two-step verification is configured for your My Kaspersky account, configure quick sign-in in your account on the My Kaspersky website then go back to the application and sign in with Google, Facebook, or Apple.
If you are using the Microsoft Edge browser, to configure the sign-in to My Kaspersky, you will need a version of Microsoft Edge based on Chromium 77.x or later. In case of a connection error, select a different browser as your default browser, install the latest version of the Microsoft Edge browser, or update the Microsoft Windows operating system.
- Go back to the application and proceed with creating the account by clicking Continue. Follow subsequent on-screen instructions.
Your device will be connected to your My Kaspersky account. In addition, you can set up a password for your account on the My Kaspersky website.
- Click Sign in with Google, Sign in with Facebook, or Sign in with Apple.
In some regions, the application prompts you to read and accept the Statement regarding data processing for purpose of using Web-Portal. If you accept the terms of the statement, click Accept.
Page top
Kaspersky Protection browser extension
In order for Kaspersky Free to fully support browsers, the Kaspersky Protection extension must be installed and enabled in the browsers. Kaspersky Free uses the Kaspersky Protection extension to inject a script into traffic. The application uses this script to interact with the web page. The application protects data transmitted by the script using a digital signature. The application can embed the script without using the Kaspersky Protection extension.
The application signs data transmitted by the script using the installed anti-virus databases and requests to Kaspersky Security Network. The application sends requests to Kaspersky Security Network regardless of whether or not you accepted the terms of the Kaspersky Security Network Statement.
When working with your browser, the Kaspersky Protection extension allows you to:
Inform about suspected phishing.
Installing the Kaspersky Protection extension in Chromium-based Microsoft Edge, Mozilla Firefox, and Google Chrome
In Google Chrome and Mozilla Firefox browsers, the Kaspersky Protection extension is installed automatically. Kaspersky Free prompts you to activate the extension. In the Chromium-based Microsoft Edge browser, the Kaspersky Protection extension is also installed automatically, but the application does not prompt you to activate the extension. You must take steps to activate the extension on your own.
Yandex Browser support
When using Yandex Browser, the following application components are operating:
- URL Advisor
- Safe Browsing;
- Anti-Phishing.
Internet Explorer support
Starting with Kaspersky Free 2021, the Kaspersky Protection extension will no longer support the browser Internet Explorer. If you want to continue using the Kaspersky Protection extension in Internet Explorer, you can go back to the previous version of the application.
Page top
How to uninstall the application
After removing the application, your computer and personal data will be unprotected.
The application is removed using the Setup Wizard.
How to uninstall the application in Windows 7
How to uninstall the application in Windows 8 or later
Removal involves the following steps:
- To remove the application, you must enter the password for accessing the application settings. If you cannot specify the password for any reason, application removal will be prohibited.
This step is available only if a password has been set for application removal.
- Saving data for future use
During this step you can specify which of the data used by the application you want to keep for further use during the next installation of the application (for example, when installing a newer version of the application).
You can save the following data:
- Quarantine files are files scanned by the application and moved to Quarantine.
After the application is removed from the computer, quarantined files become unavailable. To perform operations with these files, Kaspersky Free must be installed.
- Operational settings of the application are values of application settings selected when configuring the application.
You can also export the protection settings at the command prompt, by using the following command:
avp.com EXPORT <file_name>.- iChecker data are files that contain information about objects that have already been scanned using .
- Quarantine files are files scanned by the application and moved to Quarantine.
- Confirming removal
Since removing the application threatens the security of your computer and personal data, you will be asked to confirm your intention to remove the application. To do this, click the Remove button.
- Completing removal
During this step, the Wizard removes the application from your computer. Wait until removal is complete.
This functionality may be unavailable in some regions.
During removal of the application, you must restart your operating system. If you cancel an immediate restart, completion of the removal procedure is postponed until the operating system is restarted or the computer is turned off and then started up.
Page top
How to update the application
The application is updated automatically if you select the Automatically update mode in the update settings window (Security → Anti-Virus Database Update → Databases update schedule).
The application is automatically updated if you install a new version of the application over the previous one.
While downloading the update, the application compares the previous and new versions of the End User License Agreement, Kaspersky Security Network Statement, and Statement regarding data processing for marketing purposes. If the texts of agreements and/or statements are not identical, the application prompts you to read and accept them again.
Limitations on upgrades from a previous version of the application
Upgrading from Kaspersky Free entails the following limitations:
- When a previous version of Kaspersky Free is upgraded, the following application settings are replaced with default settings:
- Kaspersky Free display settings;
- Scan schedule;
- Participation in Kaspersky Security Network;
- File Anti-Virus protection level;
- Mail Anti-Virus protection level;
- Update sources;
- List of trusted web addresses;
- URL Advisor settings.
- After an upgrade from a previous version, Kaspersky Free starts automatically even if automatic startup of the application is disabled in the settings that have been saved. When the operating system restarts afterwards, Kaspersky Free does not start automatically if automatic startup of the application is disabled in the settings that have been saved.
What is My Kaspersky account for?
My Kaspersky is a Kaspersky website designed for centralized information storage and management of Kaspersky applications that you use.
To access My Kaspersky features, you need an account.
On My Kaspersky, you can:
- View information about subscriptions and their expiration dates.
- Securely store and synchronize your passwords and other personal information if you use Kaspersky Password Manager.
- Download purchased applications.
- Learn about new applications and special offers from Kaspersky.
Detailed information on using My Kaspersky is available in My Kaspersky help.
Page top
How to protect another device
You can share free protection with your other Windows, Android, iOS or macOS device.
You can always check how many devices you are already protecting and how many more you can protect in the Profile section of the application and in your My Kaspersky account. There you will also find easy-to-use tools for sharing your protection with another device.
To share protection from your application:
- Open the main application window.
- Go to the Profile section.
- Click the button
 . In some subscription, the text on the button reads Protect device.
. In some subscription, the text on the button reads Protect device. - In the Protect more devices window, select one of following options:
- Scan a QR code
On the QR code tab, point your phone's camera to the QR code.
On your mobile device, this opens the Google Play store, App Store, or Huawei AppGallery at the application download page. After you download and install the app, it automatically connects to My Kaspersky and starts protecting your device.
By using a QR code on an Android device, you agree to provide a one-time password to Google Play to activate the application on your smartphone.
- Send a link by email
- Go to the By email tab.
- Click the link.
This opens My Kaspersky sign-in window in your default browser.
- In the Send by email window, enter the email address in the text box and click Send.
- Download the application by following the link in the email.
After downloading and installation, the application automatically connects to your My Kaspersky account.
- Scan a QR code
In some subscription plans, only the general information about the total number of devices that you can protect may be displayed.
To learn more about remote management of device protection, revoking the subscription from a user, or revoking the subscription from a device, see My Kaspersky Help.
Page top
Switching from Kaspersky Free to a different subscription
Kaspersky Free allows you to switch to a paid subscription plan without downloading or installing any additional software.
You can temporarily switch to a trial Kaspersky Standard or Kaspersky Plus subscription to learn about the benefits of the paid subscription, or purchase a subscription and begin using the application with the paid subscription on a permanent basis.
Switching to Kaspersky Standard
Kaspersky Standard is a subscription plan designed to ensure comprehensive protection of your computer.
Compared to Kaspersky Free, Kaspersky Standard provides a range of additional advanced functionality as part of the following components and features:
- Intrusion Prevention
- Firewall
- Safe Money
- Application Manager
- Network Monitor
- Webcam Protection
- Private Browsing
- Anti-Spam
- Anti-Banner
Switching to Kaspersky Plus
Kaspersky Plus helps you improve your privacy protection and optimize the performance of your computer. This subscription plan offers the same functionality as Kaspersky Standard and a range of additional features:
- Data Leak Checker (checking an unlimited number of accounts).
- Wi-Fi network security.
- Backup and Restore
- Secret Vault
How to switch to trial subscription
You can temporarily switch to the free trial subscription for Kaspersky Standard or Kaspersky Plus to evaluate the functionality. When the trial subscription expires, you will automatically go back to using Kaspersky Free. To continue using advanced functionality of the application, you must purchase the a Kaspersky Standard or Kaspersky Plus subscription.
The trial period is not available if you have already used a trial subscription on your device.
To set up a trial subscription:
- Open the main application window.
- Go to the Profile section.
- In subscription information, click Upgrade.
- On the Upgrade page, click Try for free.
If the application is not connected to a My Kaspersky account, you must sign in to the account. If you do not have an account, you can create one in the connection window. On the territory of the European Union, you must accept the Statement regarding data processing for purpose of using Web-Portal or the Statement regarding data processing for purpose of using Web-Portal and regulating license limitations.
- The Migration Wizard starts.
When switching to Kaspersky Standard or Kaspersky Plus in the European Union, the application offers you to read and accept the End User License Agreement, Kaspersky Security Network Statement, and Statement regarding data processing for marketing purposes. You may also need to accept the Statement regarding data processing for purpose of using Web-Portal or the Statement regarding data processing for purpose of using Web-Portal and regulating license limitations.
The application may take some time to set up and start. After the completion of the process, the application is automatically activated using the trial subscription.
During the activation process, you may be prompted to install extra applications that are offered as part of the subscription.
- Click Close to finish with the Wizard, then click Start to begin using the application with the trial subscription.
How to switch to paid subscription
You can purchase a Kaspersky Standard or Kaspersky Plus subscription in the user interface of the application.
To buy a subscription:
- Open the main application window.
- Go to the Profile section.
- In subscription information, click Upgrade.
- On the Upgrade page, click Buy now.
The website of Kaspersky or one of our partners opens in the default browser. Follow the instructions on the website.
After the successful purchase, the subscription is added to your My Kaspersky account.
If the application is not connected to a My Kaspersky account, you must sign in to the account. On the territory of the European Union, you must also accept the Statement regarding data processing for purpose of using Web-Portal or the Statement regarding data processing for purpose of using Web-Portal and regulating license limitations.
- The Migration Wizard starts. To proceed with the wizard, click the Continue button.
When switching to Kaspersky Standard or Kaspersky Plus in the European Union, the application offers you to read and accept the End User License Agreement, Kaspersky Security Network Statement, and Statement regarding data processing for marketing purposes. You may also need to accept the Statement regarding data processing for purpose of using Web-Portal or the Statement regarding data processing for purpose of using Web-Portal and regulating license limitations.
The application may take some time to set up and start. After the completion of the process, the application is automatically activated using the new subscription.
During the activation process, you may be prompted to install extra applications that are offered as part of the subscription.
- Click Close to finish with the Wizard, then click Start to begin using the application with the new subscription.
How to configure the application interface
This section contains information on how to configure the interface of the application.
How to configure application notifications
Notifications that appear in the taskbar notification area inform you of application events that require your attention. Depending on how critical the event is, you may receive the following types of notifications:
- Critical notifications inform you of events that have critical importance for the computer's security, such as detection of a malicious object or dangerous activity in the operating system. Windows used for critical notifications and pop-up messages are red.
- Important notifications inform you of events that are potentially important for the computer's security, such as detection of a probably infected object or suspicious activity in the operating system. Windows used for important notifications and pop-up messages are yellow.
- Information notifications inform you of events that do not have critical importance for the computer's security. Windows used for information notifications and pop-up messages are green.
If a notification is displayed on the screen, you should select one of the options that are suggested in the notification. The optimal option is the one recommended as the default by Kaspersky experts.
A notification can be closed automatically when the computer is restarted, when Kaspersky Free is quit, or in Connected Standby mode in Windows 8. When a notification is closed automatically, Kaspersky Free performs the default recommended action.
Click the links below to learn how to configure the application notifications.
How to configure delivery of notifications
How to configure delivery of notifications containing news and special offers from Kaspersky
How to enable notification sounds
How to configure notifications when a child is using the application
Page top
How to change the application design theme
The capability to change the application design theme is not available in some regions.
To change the application design theme:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Interface settings section.
- In the Design theme block, choose one of the following options:
- Same as the operating system. The current operating system design theme is used.
- Light. The light application design theme is used.
- Dark. The dark application design theme is used.
- Use a custom design theme, if you want to use a custom design theme. Click Select and enter the path to the ZIP archive or folder containing the files with the custom design theme.
The design theme is applied after application restart.
Page top
How to configure the application icon
In this section, you will learn about configuring the application icon on your desktop and in the notification area.
How to change the application icon
How to change the icon in the notification area depending on the protection status
Page top
How to password-protect access to the application management functions
A single computer may be shared by several users with various levels of experience and computer literacy. Unrestricted access of different users to the application and its settings may compromise the level of computer security.
To restrict access to the application, you can define an administrator password for the KLAdmin account. This user has unlimited rights to manage and modify the settings of the application, and to assign application access permissions to other users. After you create a password for KLAdmin, you can assign application access permissions to various users or groups of users.
To create a KLAdmin administrator password:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Interface settings section.
- Switch the Password protection toggle to On.
- In the opened window, fill in the User name (KLAdmin is recommended), Enter password and Confirm password fields.
Tips on creating a strong password:
- The password must contain at least eight and no more than 128 characters.
- The password contains at least one number.
- The password contains both lowercase and uppercase letters.
- The password must contain at least one special character (for example: ! @ # $ % ^ & *).
- Click Save.
A forgotten password cannot be recovered. If you have forgotten your password, read the article on the Technical Support website that provides recommendations on how to recover access to Kaspersky Free.
The user KLAdmin can assign permissions to the following users and user groups:
Everyoneuser group. This group includes all users of the operating system. If you grant this group permission to perform a particular action, then group users will always be allowed to perform this action, even if a specific user or a user group belonging to theEveryoneuser group does not have individual permission to perform the action. By default, members of theEveryonegroup are not allowed to perform any actions.<system user>. By default, the selected user is not allowed to perform any actions. This means that when you try to perform a prohibited action, you will be prompted to enter yourKLAdminaccount password.
How to add a user or user group
How to edit permissions for a user or user group
How to allow an action for an individual user or user group
How to forbid an action for an individual user or user group
When you try to perform any action from the list in the Add permissions for a user or a group window, the application will ask you to enter a password. In the password window, enter the username and password for the current user account. The action will be executed if the specified account has permission to perform this action. In the password window, you can specify the time interval during which the user will not have to reenter the password.
In the password window, you can switch the input language only by pressing ALT+SHIFT. Any other shortcuts will not switch the input language, even if that shortcut is configured in the operating system.
Page top
Security
Today's hackers are getting smarter in their target to break into your devices. New ransomware, phishing and other malware types call out for new cybersecurity solutions to get you a step ahead the growing threats. We created the new Kaspersky Free application to help you stay on top of today's threats. Find out what you can do to feel secured.
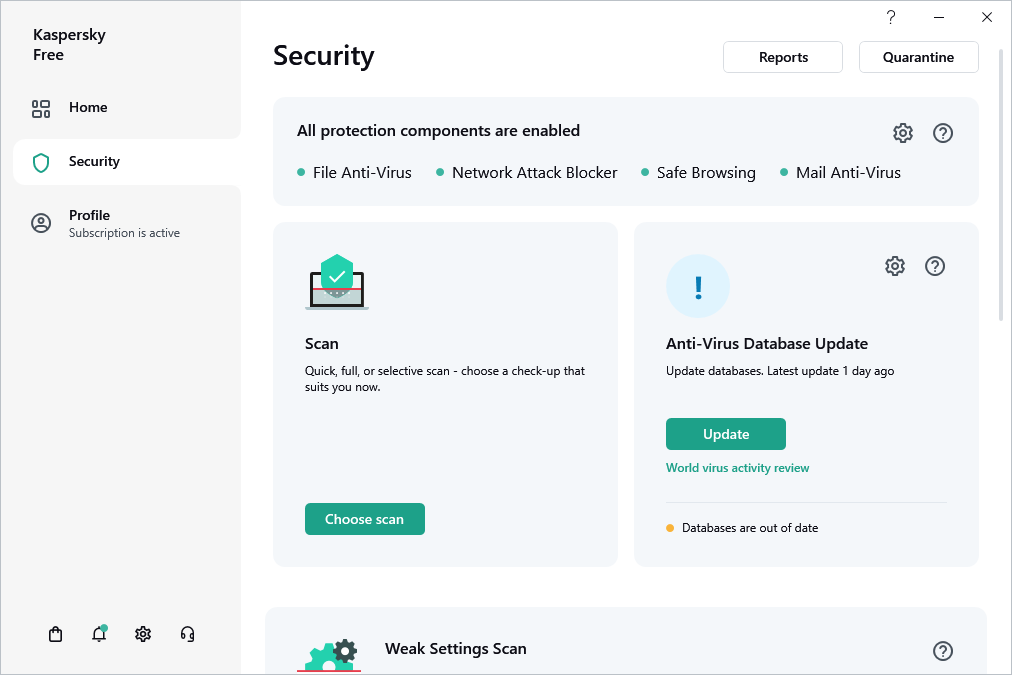
Assessing computer protection status and resolving security issues
Problems with computer protection are symbolized by an indicator located in the upper part of the main application window. Green indicates that your computer is protected. Yellow indicates that there are protection problems and red indicates that your computer's security is at serious risk. You are advised to fix problems and security threats immediately.
You can open the Notification Center window by clicking the Details button in the main application window. This window provides detailed information about the protection status of the computer and suggests possible actions for rectifying problems and threats.
Problems with protection are grouped by categories. For each problem, a list is displayed of actions that you can take to solve the problem.
The Status section displays information about the computer protection status and subscription status. If problems are detected that must be fixed, a Fix button is displayed next to the notification; you can fix security problems by clicking this button.
The Recommendations section lists actions that should be performed to optimize operation of the application and use it more effectively.
The News section displays cybersecurity news.
Clicking the Show N ignored notifications button displays notifications to which the Ignore action has been applied. Ignored notifications do not affect the color of the protection indicator in the main application window.
Page top
How to fix security issues on your PC
To fix security issues on your PC:
- Open the main application window.
- Click on the Details link in the upper part of the main application window to go to the Notification Center window.
- Go to the Status section. This section displays security issues on your PC.
- Select an issue from the list and click an action button, e.g. Fix.
- Select Ignore from the drop-down list if you do not want to fix this issue now. You can view the list of ignored notifications later by clicking the Show N ignored notifications button.
- Go to the Recommendations section. This section displays recommendations that are not mandatory but will help you optimize your usage of the application and better protect your PC.
- Select a suggestion from the list.
- Click the button next to a suggested action; for example, click the Enable button next to the Want to get rid of noisy pop-up ads? suggestion.
- Go to the News section. In this section, you will find cybersecurity news. Use the navigation buttons to read the next news item or to go back to the previous news.
How to restore a deleted or disinfected file
Backup copies of deleted or disinfected files are placed in a special folder on your computer, named Quarantine. Backup copies of files are stored in a special format that is not dangerous to your computer. You can restore deleted or disinfected file from the backup copy stored in Quarantine.
We recommend that you avoid restoring deleted or disinfected files since they may pose a threat to your computer!
The application does not disinfect Windows Store apps. If scanning results indicate that such an app is dangerous, it is deleted from your computer. When a Windows Store app is deleted, Kaspersky Free does not create a backup copy of it. To restore such objects, you must use the recovery tools included with the operating system (for detailed information, see the documentation for the operating system that is installed on your computer) or update apps via the Windows Store.
To restore deleted or disinfected file:
- Open the main application window.
- Go to the Security section.
- In the upper-right corner of the application window, click the Quarantine button.
This opens the Quarantine window.
- In the Quarantine window that opens, select the required file from the list and click the Restore button.
Scanning the computer
During scanning, the application searches for infected files and malware. There are several types of scans that vary in their search duration and scope.
- Full Scan. Scans all areas of the computer. This scan requires a lot of time to complete.
- Quick Scan. Scans objects that are loaded when the operating system starts as well as system memory and boot files. This scan does not require a lot of time to complete.
- Selective Scan. Scans the selected file or folder.
- Removable drives scan. Scan of removable drives, such as hard drives and USB sticks connected to the computer.
- Instant File Scan. This option scans files from the context menu.
- Background Scan. Scan of system memory, the system partition, boot sectors, and startup objects, as well as rootkits search.
- Application Vulnerability Scan. Scan the computer for vulnerabilities in applications that malware can exploit to infect your system.
After you install the application, we recommend that you perform a full scan of your computer.
How to run a Quick Scan
During a quick scan, the application scans the following objects by default:
- Objects loaded at the startup of the operating system;
- System memory
- Disk boot sectors.
To run a Quick Scan:
- Open the main window of the application and perform the following actions:
- Go to Home section, and click the Quick Scan button.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
- This opens the Scan window.
- In the Scan window select the Quick Scan section.
- In the Quick Scan section, click the Run scan button.
The application starts a quick scan of your computer.
Page top
How to run a Full Scan
During a full scan, the application scans the following objects by default:
- System memory
- Objects loaded on operating system startup;
- System backup storage;
- Hard drives and removable drives.
We recommend running a full scan immediately after installing the application to your computer.
To run a Full Scan:
- Open the main window of the application and go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Full Scan section.
- In the drop-down list next to the Run scan button, select the action to perform when the scan is complete.
- Click Run scan.
The application starts a full scan of your computer.
Page top
How to run a Custom Scan
A Selective Scan lets you scan a file, folder, or drive for viruses and other threats.
To run a Custom Scan:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Selective Scan section.
- Click the Select button and specify an object in the file or folder selection window that opens.
- Click Run scan.
How to run a removable drive scan
Removable drives that you connect to the computer may contain viruses or other applications that present a threat. Kaspersky Free scans removable drives to prevent your computer from becoming infected. You can configure a removable drive scan to be started manually or automatically when a removable drive is connected to the computer. Automatic scanning of removable drives is enabled by default.
To run a removable drive scan manually:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window select the Removable Drive Scan section.
- In the drop-down list, select the drive letter of the external device and click on the Run scan button.
The application will start scanning the connected device.
Page top
How to run a Context Menu File or Folder Scan
To run a Context Menu File or Folder Scan:
- Right-click on the file or folder that needs to be scanned.
- In the context menu that opens, select Scan for viruses.
The application will start scanning the selected file or folder.
In Microsoft Windows 11, you must expand the context menu of an object to see the application commands.
Page top
How to enable or disable a background scan
A Background scan is an automatic scan mode that does not display notifications. This scan requires fewer computer resources than other types of scans (for example, Full Scan). When in this mode, the application scans the system memory, system volumes, boot sectors and startup objects, and searches for rootkits.
A background scan is started in the following cases:
- After the databases and application modules are updated
- 30 minutes after application launch
- Every six hours.
- If the computer remains idle for five or more minutes (after the screen saver is started).
A background scan is interrupted when any of the following conditions is met:
- The computer becomes active again.
- The computer (laptop) switches to battery mode.
If a background scan has not been performed for over ten days, the scan is not stopped. When running a background scan, the application does not scan files whose contents are located in OneDrive cloud storage.
To enable or disable a background scan:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- Click the
 icon in the Background scan block.
icon in the Background scan block.This opens the Background scan settings window.
- In the Background scan settings window, switch the toggle to On or Off.
How to create a scan schedule
To create a scan schedule:
- Open the main application window.
- Go to the Security section.
- In the Scan block, click the Choose scan button.
This opens the Scan window.
- In the Scan window, select the type of scan and click the
 icon.
icon. - In the opened window, click the Scan schedule link to proceed to the Scan schedule window.
- In the Scan schedule window, in the Run scan list, select a period, such as Every day, and specify the time to start the scan.
A scan schedule cannot be created for the Scan from Context Menu or Background Scan.
Page top
About scanning files in OneDrive cloud storage
In Windows 10 RS3 or later, Kaspersky Free does not scan files in OneDrive cloud storage. If the application detects such files during a scan, it shows a notification stating that the files in cloud storage were not scanned.
The following components do not scan files in OneDrive cloud storage:
- Full Scan
- Selective Scan
- Quick Scan
- Background Scan.
The report on the operation of Kaspersky Free contains a list of files in OneDrive cloud storage that were skipped during scan.
Files downloaded from OneDrive cloud storage to a local computer are scanned by real-time protection components. If a file scan was postponed and the file has been uploaded back to OneDrive cloud storage before the scan is started, this file may be skipped during a scan.
In order to make sure that OneDrive files are displayed in Explorer, turn on the Files on demand in the OneDrive client application feature. If you are connected to the Internet, you can use them just like any other files on your computer.
Page top
Updating anti-virus databases and application modules
This section contains information about database and application module updates.
About updating databases and application modules
The installation package of the application includes databases and application modules. Using these databases:
- The application detects the majority of threats using Kaspersky Security Network, which requires an Internet connection.
- The application detects adware, auto dialers, and other legitimate software that can be used by intruders to damage your computer or personal data.
To get full protection, we recommend updating the anti-virus databases and application modules as soon as the application has been installed.
Databases and application modules are updated in stages:
- The application starts updating databases and application modules according to the specified settings: automatically, on schedule, or on demand. The application contacts an update source that stores a anti-virus databases and application modules update package.
- The application compares the existing databases with the databases available at the update source. If the databases are different, the application downloads the missing parts of the databases.
The application then uses the updated databases and application modules to scan the computer for viruses and other threats.
Update sources
You can use the following update sources:
- Kaspersky update servers
- HTTP or FTP server
- Network folder
Special considerations involved in updating anti-virus databases and application modules
Updates of anti-virus databases and application modules are subject to the following restrictions and specifics:
- Anti-virus databases are considered out of date after one day and extremely out of date after seven days.
- To download an update package from Kaspersky servers, an Internet connection is required.
- Updates of anti-virus databases and application modules are unavailable in the following cases:
- The subscription has expired, and the grace period or limited functionality mode is not available.
- A metered mobile Internet connection is used. This limitation applies on computers running under Microsoft Windows 8 or more recent versions of this operating system if automatic updates or scheduled updates are enabled and a traffic limit has been set for a metered mobile connection. If you want the application to update anti-virus databases and application modules in this case, clear the Limit traffic on metered connections check box in Settings → Security settings → Advanced settings → Network settings.
- The application is used under subscription from a service provider, and you have suspended your subscription on the website of the service provider.
Installing an update package
When an update package (patch) is received, the application installs it automatically. To complete the installation of an update package, you must restart the computer. Until the computer is restarted, the application icon in the notification area is red, and the application Notification Center window displays a prompt to restart the computer.
Page top
How to start an update of databases and application modules
By default, databases and application modules are updated automatically. You do not need to take any action. If automatic updates are disabled, you can update application databases and modules manually.
To start an update of databases and application modules:
- Open the main application window.
- Go to the Security section.
- In the Anti-Virus Database Update block, click the Update button.
Anti-Virus Database Update
Pre-Kaspersky virus removal
This section contains information on restoring the operating system after it has been infected with malware.
Recovering the operating system after infection
If you suspect that the operating system of your computer has been corrupted or modified due to malware activity or a system failure, use the Microsoft Windows Troubleshooting Wizard, which clears the system of any traces of malicious objects. Kaspersky recommends that you run the Wizard after the computer has been disinfected to make sure that all threats and damage caused by infections have been fixed.
The Wizard checks whether there are any changes to the system, which can include access to the network being blocked, file name extensions for known formats being changed, Control Panel being blocked, etc. There are different reasons for these different kinds of damage. These reasons may include malware activity, incorrect system configuration, system failures, or malfunctioning applications for system optimization.
After the review is complete, the Wizard analyzes the information to evaluate whether there is system damage that requires immediate attention. Based on the review, the Wizard generates a list of actions that are necessary to eliminate the damage. The Wizard groups these actions by category based on the severity of the problems detected.
Troubleshooting the operating system by using the Microsoft Windows Troubleshooting Wizard
To run the Microsoft Windows Troubleshooting Wizard:
- Open the main application window.
- Go to Security → Microsoft Windows Troubleshooting.
- Click Find damage.
The Microsoft Windows Troubleshooting Wizard window opens.
The Wizard consists of a series of pages (steps), which you can navigate through by clicking the Back and Next buttons. To close the Wizard after it finishes, click the Done button. To stop the Wizard at any stage, click the Cancel button.
Let us review the steps of the Wizard in more detail.
Start recovery of the operating system
- Select one of the two options for Wizard operation:
- Search for damage caused by malware activity. The Wizard will search for problems and possible damages.
- Roll back changes. The Wizard will roll back the fixes applied to previously identified problems and damages.
- Click Next.
Search for problems
If you selected the Search for damage caused by malware activity option, the Wizard searches for problems and possible damages that should be fixed. When the search is complete, the Wizard proceeds automatically to the next step.
Select actions to fix damage
All damage found at the previous step is grouped based on the type of danger that it poses. For each damage group, Kaspersky recommends a set of actions to repair the damage.
There are three groups:
- Strongly recommended actions eliminate problems that pose a serious security threat. You are advised to repair all damage in this group.
- Recommended actions are aimed at repairing damage that may pose a threat. You are also advised to repair damage in this group.
- Additional actions repair operating system damage that is not dangerous now, but may pose a threat to the computer's security in the future.
Expand the list of the selected group to view damage within the group.
To get the Wizard to fix a specific type of damage, select the check box next to the damage description. By default, the Wizard fixes damage belonging to the groups of recommended and strongly recommended actions. If you do not want to fix a specific type of damage, clear the check box next to it.
It is strongly recommended that you not clear the check boxes selected by default, as doing so will leave your computer vulnerable to threats.
After you define the set of actions for the Wizard to perform, click the Next button.
Fix damage
The Wizard performs the actions selected during the previous step. It may take a while to fix damage. After fixing damage, the Wizard automatically proceeds to the next step.
Wizard completion
Click the Done button to exit the Wizard.
Page top
Operating system emergency recovery
Kaspersky Rescue Disk is intended for emergency recovery of the operating system. You can use Kaspersky Rescue Disk for scanning and disinfecting infected computer that cannot be disinfected using other methods (for example, with anti-virus applications).
More details on using Kaspersky Rescue Disk are available on the Technical Support website.
Page top
Weak Settings Scan
In this section, you will learn about weak operating system settings, and how to search for and fix weak settings in the operating system.
About weak settings of the operating system
When you are working with a computer, operating system settings can be changed as a result of your actions or the actions of applications that you run. Changing the operating system settings can pose a risk to the security of your computer. For example, if automatic sign-in with the current user name and password is enabled in the browser, a third-party website can intercept your password.
Weak settings in the operating system can be divided into two types:
- Critical settings. Such settings are equated with vulnerabilities of the operating system.
- Recommended settings. You are advised to fix these settings to improve the security of the operating system.
By default, the application scans for weak settings of the operating system at least once a day. If the application detects weak settings in the operating system, it prompts you to fix them to restore the security of the operating system. For details about each weak setting, click the link next to the relevant setting in the application window.
You can click the link in the notification window to go to the Weak Settings Scan window that displays the weak settings detected in the operating system. Information about weak settings is also displayed in the Notification Center. You can proceed to view and fix the weak settings from the Notification Center.
In the Weak Settings Scan window, you can perform the following actions:
- Fix weak settings in the operating system.
- Ignore: Leave weak settings of the operating system unchanged.
- Cancel: Restore previously fixed weak settings of the operating system to their original state.
The application identifies weak settings of the operating system for all user accounts on your computer. You can fix weak settings for other user accounts on the computer only if you have logged in to the operating system under an administrator account.
If you are not an administrator of the computer, you can ignore weak settings only for your own user account. Only a computer administrator can ignore weak settings of all user accounts.
You can manually start a scan for weak settings or disable the scan for weak settings.
You can remotely manage the protection of your computer and send a command to fix weak settings from My Kaspersky.
Page top
How to find and fix weak settings in the operating system
To find and fix weak settings of the operating system:
- Open the main application window.
- Select the Security section.
- Under Security, select Weak Settings Scan.
- Click Scan.
This runs a Weak Settings Scan. After the scan is complete, you will see scan results in the Weak Settings Scan section.
- Click View to go to the Weak Settings Scan window.
- In the Weak Settings Scan window, select an action to take on weak settings:
- Detected weak settings. Do one of the following:
- Click the Fix all button to fix all weak settings.
- Click the Fix button to fix a weak setting.
- If open applications are interfering with fixing a weak setting, click the View button to view the list of interfering applications.
To close applications that prevent the setting from getting fixed, do one of the following:
- Click the
 button to the right of the name of the interfering application to shut it down normally. If the application detects any unsaved changes, it will prompt you to save them.
button to the right of the name of the interfering application to shut it down normally. If the application detects any unsaved changes, it will prompt you to save them. - Click the Force close link to close all interfering applications without saving data.
- Click the
- In the drop-down list next to the Fix button, select Ignore to leave a weak setting unchanged.
- In the drop-down list next to the Fix button, select Read more to view information about a weak setting on the Kaspersky Technical Support website.
- Previously fixed weak settings.
- Click the Roll back button to restore the fixed setting to its original state.
- In the drop-down list next to the Roll back button, select Read more to view information about a weak setting on the Kaspersky Technical Support website.
- Ignored settings. Click the Show all link next to the N ignored settings message to open the list of weak settings that you left unchanged, and click the Fix button.
- Detected weak settings. Do one of the following:
How to enable Weak Settings Scan
To disable the Weak Settings Scan:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to the Performance settings section.
- Click PC resource consumption.
- Clear the Scan for weak operating system settings check box.
The application will not scan for weak settings of the operating system or show alerts about them.
Page top
Scanning email messages
Kaspersky Free allows scanning email messages for dangerous objects by using Mail Anti-Virus. Mail Anti-Virus starts when the operating system is started and remains constantly in the RAM of the computer, scanning all email messages that are sent or received over the POP3, SMTP, IMAP, and NNTP protocols, as well as via encrypted connections (SSL) over the POP3, SMTP, and IMAP protocols.
By default, Mail Anti-Virus scans both incoming and outgoing messages.
If no threats are detected in an email message, or if all infected objects have been successfully disinfected, the message becomes available for further access. If the component fails to disinfect an infected object, Mail Anti-Virus renames or deletes the object from the message and adds a notification to the message subject line, stating that the message has been processed by Kaspersky Free. Before deleting an object, Kaspersky Free creates a backup copy of it and places a copy in Quarantine.
If Kaspersky Free detects the password for the archive in the message text during scanning, the password is used to scan the contents of that archive for malware. The password is not saved. The archive is unpacked before scanning. If the application crashes while unpacking the archive, you can manually delete the files that are unpacked at the following path: %systemroot%\temp. The files have the PR prefix.
Page top
Protection using hardware virtualization
In this section, you will learn how you can protect your computer using hardware virtualization.
About protection using hardware virtualization
When Kaspersky Free is installed in 64-bit Microsoft Windows 8, Microsoft Windows 8.1 or Microsoft Windows 10, it uses
technology for additional protection against complex malware that could intercept your personal data by using the clipboard or phishing.Protection using hardware virtualization is enabled by default. If protection has been disabled manually, you can enable it in the application settings window.
On computers running 64-bit Microsoft Windows 8, Microsoft Windows 8.1 or Microsoft Windows 10, the protection provided by Kaspersky Free hardware virtualization (hypervisor) has the following limitations:
- This feature is not available when a third-party hypervisor is running, such as the hypervisor used by the VMware virtualization software. After you close the third-party hypervisor, protection against screenshots becomes available again.
- The feature is not available if the CPU of your computer does not support hardware virtualization technology. For more details on whether your CPU supports hardware virtualization, please refer to the documentation shipped with your computer or to the website of the CPU manufacturer.
- The feature is not available if a third-party hypervisor (such as the VMware hypervisor) is running when you start Protected Browser.
- The feature is not available if hardware virtualization is disabled on your computer. For details on how to enable hardware virtualization on your computer, please refer to your computer's technical documentation or visit the website of your processor's manufacturer.
- The feature is not available if Device Guard is enabled in the Microsoft Windows 10 operating system.
- The feature is not available if Virtualization Based Security (VBS) is enabled in the Microsoft Windows 10 operating system.
How to enable protection using hardware virtualization
To enable protection using hardware virtualization:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → Privacy settings → Secure Data Input.
- Select the Use hardware virtualization if available check box. This check box is displayed when the application is installed on a 64-bit version of Windows 8, Windows 8.1 and Windows 10.
- Select the Use advanced features of hardware virtualization check box if you want to turn hardware virtualization on when the operating system starts.
If hardware virtualization is disabled on your computer, protection using hardware virtualization will be disabled.
Page top
About protection using Antimalware Scan Interface
Antimalware Scan Interface (AMSI) allows a third-party application that supports AMSI to send objects (for example, PowerShell scripts) to Kaspersky Free for additional scanning and to receive scan results for these objects. For example, Microsoft Office applications can be such third-party applications. For more information about the AMSI interface, refer to Microsoft documentation.
Antimalware Scan Interface allows only to detect a threat and notify a third-party application about the detected threat. After receiving the threat notification, the third-party application prevents malicious actions (for example, shuts down).
Kaspersky Free may decline a request from a third-party application if, for example, this application exceeds the maximum number of requests allowed for a period. In this case, Kaspersky Free displays a notification about the declined request. If you receive such a notification, you do not have to perform any actions.
Protection using Antimalware Scan Interface is available on Windows 10 Home / Pro / Education / Enterprise and Windows 11 Home / Pro / Enterprise operating systems.
Page top
How to exclude a script from scanning using Antimalware Scan Interface
To exclude a script from scanning using Antimalware Scan Interface:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → AMSI Protection.
- In the Script scanner section, select the Scan scripts using Antimalware Scan Interface (AMSI) check box.
- Click the Manage exclusions link to go to the Exclusions window.
- In the Exclusions window, click the Add button.
The Add new exclusion window opens.
- In the File or folder field, specify the folder with the script.
- In the Object field, specify the name of the script.
You can also add several files of the same type to the exclusions by using a mask.
- In the Protection components section, select the check box next to the File Anti-Virus component.
- Select the Active status.
The specified object will not be scanned using Antimalware Scan Interface.
Page top
How to enable protection using Antimalware Scan Interface
To enable protection using Antimalware Scan Interface:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → AMSI Protection.
- In the Script scanner section, select the Scan scripts using Antimalware Scan Interface (AMSI) check box.
Game mode
When Kaspersky Free runs in full-screen mode together with some other applications (particularly computer games), the following issues may occur:
- Application or game performance decreases due to lack of system resources;
- Notification windows of Kaspersky Free distract the user from the gaming process.
To avoid changing the settings of Kaspersky Free manually every time you switch to full-screen mode, you can use Game mode. If Game mode is being used and you are playing or working with applications in full-screen mode, Kaspersky Free does not run scan and update tasks and does not display notifications.
To enable Game mode:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Performance settings → PC resource consumption.
- Select the Game Mode check box.
Protecting personal data on the Internet
This section provides information about how to make your Internet browsing safe and protect your data against theft.
About protection of personal data on the Internet
Kaspersky Free helps you to protect your personal data against theft:
- Passwords, user names, and other registration data
- Account numbers and bank card numbers
Kaspersky Free includes components and tools that allow you to protect your personal data against theft by criminals who use methods such as
and interception of data entered on the keyboard.Protection against phishing is provided by Anti-Phishing, which is implemented in the Safe Browsing component. Enable these components to ensure comprehensive protection against phishing.
Protection against interception of data entered on the keyboard is provided by On-Screen Keyboard.
Page top
About On-Screen Keyboard
When using the Internet, you frequently need to enter your personal data or your user name and password. This happens, for example, during account registration on websites, online shopping, and Internet banking.
There is a risk that personal data can be intercepted by hardware keyboard interceptors or keyloggers, which are programs that record keystrokes. The On-Screen Keyboard tool prevents the interception of data entered via the keyboard.
Many programs classified as spyware can take screenshots, which then are automatically transmitted to an intruder for further analysis to steal the user's personal data. On-Screen Keyboard protects entered personal data from attempts to intercept it by means of screenshots.
On-Screen Keyboard has the following features:
- You can click the On-Screen Keyboard buttons with the mouse.
- Unlike hardware keyboards, it is impossible to press several keys simultaneously on On-Screen Keyboard. This is why key combinations (such as ALT+F4) require that you click the first key (for example, ALT), then the second key (for example, F4), and then the first key again. The second click of the key acts in the same way as releasing the key on a hardware keyboard.
- The On-Screen Keyboard language can be switched by using the same shortcut that is specified by the operating system settings for the hardware keyboard. To do so, right-click the other key (for example, if the LEFT ALT+SHIFT shortcut is configured in the operating system settings for switching the keyboard language, left-click the LEFT ALT key and then right-click the SHIFT key).
To ensure protection of data entered via On-Screen Keyboard, restart your computer after installing Kaspersky Free.
The use of On-Screen Keyboard has the following limitations:
- On-Screen Keyboard prevents interception of personal data only when used with the Chromium-based Microsoft Edge, Mozilla Firefox, or Google Chrome browsers. When used with other browsers, On-Screen Keyboard does not protect entered personal data against interception.
- On-Screen Keyboard cannot protect your personal data if the website requiring the entry of such data is hacked, because in this case the information is obtained directly by the intruders from the website.
- On-Screen Keyboard does not prevent screenshots that are made by using the Print Screen key and other combinations of keys specified in the operating system settings.
- Kaspersky Free does not provide protection against unauthorized screenshots in Microsoft Windows 8 and 8.1 (64-bit only) if the On-Screen Keyboard window is open but the Protected Browser process is not started.
How to open On-Screen Keyboard
You can open On-Screen Keyboard in the following ways:
- From the toolbar of Chromium-based Microsoft Edge, Mozilla Firefox, or Google Chrome
- By pressing a combination of keyboard keys
Starting On-Screen Keyboard from the browser toolbar
Starting On-Screen Keyboard by using the hardware keyboard
Page top
Checking a website for safety
Kaspersky Free allows checking the safety of a website before you click a link to open it. Websites are checked using URL Advisor.
The URL Advisor component checks links on a web page opened in Chromium-based Microsoft Edge, Google Chrome, or Mozilla Firefox. Kaspersky Free displays one of the following icons next to the checked link:
 – if the linked web page is safe according to Kaspersky
– if the linked web page is safe according to Kaspersky
 – if there is no information about the safety status of the linked web page
– if there is no information about the safety status of the linked web page
 – if according to Kaspersky, hackers can cause harm to your computer or your data by using the web page that the link leads to;
– if according to Kaspersky, hackers can cause harm to your computer or your data by using the web page that the link leads to;
 – if according to Kaspersky, the web page that the link leads to can be infected or hacked;
– if according to Kaspersky, the web page that the link leads to can be infected or hacked;
 – if the linked web page is dangerous according to Kaspersky
– if the linked web page is dangerous according to Kaspersky
To view a pop-up window with more details on the link, move the mouse pointer to the corresponding icon.
By default, Kaspersky Free checks links in search results only.
Page top
How to change encrypted connections settings
Encrypted connections are established over the SSL and TLS protocols. By default, Kaspersky Free scans such connections upon request from URL Advisor.
To change encrypted connections settings:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to the Security settings section.
- In the Advanced settings block, click the Network settings button.
- In the Network settings window, go to the Encrypted connections scan section.
- Select an action to perform when connecting to websites over an encrypted connection:
- Do not scan encrypted connections. Kaspersky Free does not scan encrypted connections.
- Scan encrypted connections upon request from protection components. Kaspersky Free only scans encrypted connections upon request from URL Advisor. This action is selected by default.
- Always scan encrypted connections. Kaspersky Free always scans encrypted connections.
Clicking the Show certificates link opens a window with a list of trusted certificates that are used by popular websites. Certificates are added to this list if you click Add to trusted certificates and continue in a Kaspersky Free warning when visiting a website. After you add a certificate to the list, the website is considered trusted. You can add or remove certificates in the Trusted root certificates window using the Add and Delete buttons.
If you have multiple user accounts on your computer, and one of the users accepts the new certificate, this certificate is also added to the trusted certificate list for all other users.
- Select an action to perform if there are errors when scanning encrypted connections:
- Ignore. If this action is selected, Kaspersky Free terminates the connection with the website on which the scan error occurred.
- Ask. If there is an error when scanning encrypted connection with a website, Kaspersky Free shows a notification where you can select an action:
- Ignore. Kaspersky Free terminates the connection with the website on which the scan error occurred.
- Add domain to exclusions. Kaspersky Free adds the website address to the list of trusted addresses. Kaspersky Free does not scan encrypted connections on websites from the list of trusted addresses. You can view such websites by clicking the Trusted addresses link.
This option is selected by default.
- Add domain to exclusions. Kaspersky Free adds the website to the list of trusted addresses. Kaspersky Free does not scan encrypted connections on websites from the list of trusted addresses. These websites are displayed in the Trusted addresses window, which can be opened by clicking the Trusted addresses link.
- Click the Trusted addresses link to open the Trusted addresses window and perform the following actions:
- Click the Add button to add the website to the list of exclusions for encrypted connections scan.
- Enter the domain name of the website in the Domain name field.
Click Add. The application will not scan encrypted connections with this website. Please note that adding a website to the list of exclusions may limit the functionality of scanning the website by URL Advisor.
How to access files stored in a secret vault
To access files stored in a secret vault:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Under Privacy settings, select Secret Vault.
- In the Secret Vault block, click the I already have a secret vault button.
This opens the Secret Vault window.
- Click Unlock next to your secret vault.
- Enter the password and click the Open in Windows Explorer button.
Files stored in the secret vault appear in the Explorer window.
Page top
About security news
Every day, the world is seeing more and more mass theft of passwords, hacking of databases, and online banking fraud. Kaspersky security news provides fresh information about such crimes and helps you prevent situations in which you could become a victim of hackers. To make sure that the security news you receive is specifically relevant for you, the application analyzes information about the resources you visit and the apps that you run. This information is used only for the purpose of selecting news that may be important or interesting to you.
Security news is displayed in the Notification Center together with other news from Kaspersky. Security news notifications appear in the taskbar notification area. Notification windows contain the news header and a brief recommendation on resolving the problem described in the news.
Depending on the severity level, news can be of the following types:
- Important news – news about events that pose a potential threat to your security (for example, news about mass theft of Facebook passwords). Windows containing important news are yellow.
- General news – news that is for information purposes (for example, news about more and more frequent cases of data breaches in online banking caused by Trojan malware). Windows containing general news are green.
If a notification about security news appears on the screen, you can proceed to the full text of the news by clicking the Details button in the pop-up window, or you can close the pop-up window. You can view the full text of news at any time by selecting the relevant news in the Notification Center news list.
If you do not want to receive security news on a specific device, you can disable the display of news. If you do not want to receive news on any of your devices, you can disable the receipt of news on My Kaspersky.
Security news is not displayed during the first hour of operation of the application after it is installed.
Page top
How to enable or disable security news
To enable or disable security news:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Interface settings section.
This opens the Interface settings window.
- In the Promotional materials section, perform one of the following:
- If you want to receive security news, select the Receive informational messages and advertisements from Kaspersky check box.
- If you do not want to receive security news, clear the Receive informational messages and advertisements from Kaspersky check box.
How to enable or disable the receipt of security news on My Kaspersky
To enable or disable the receipt of security news on My Kaspersky:
- Open the main page of My Kaspersky.
- Click the Sign in button and enter your email address that you specified when creating the account and your password.
- Click the button
 .
.This opens the window for viewing notifications.
- Click the Settings link to go to the Notification settings window.
- Do one of the following:
- If you want to enable the receipt of security news, select the Security news check box.
- If you want to disable the receipt of security news, clear the Security news check box.
Data Leak Checker
This section explains how to check if your user account data can be accessed publicly.
About Data Leak Checker
Data Leak Checker on the Kaspersky Free subscription plan lets you manually check only the My Kaspersky account. Automatic checks of My Kaspersky account and other accounts are available only in Kaspersky Plus package.
Most users create accounts on various websites for work, shopping, and communication purposes. There is always the risk that attackers could hack the site and gain access to user data. If you use the same email address and password for different sites, it is more likely that your data will be leaked.
With Kaspersky Free, you can check your user accounts for potential leaks. If the check reveals that your data may be publicly accessible, the application will notify you about it and display a list of sites from which a data leak could have occurred, the date of possible leakage, and the category of data that may be publicly accessible.
Kaspersky Free also checks your accounts for data leaks to Darknet. If a leak is found, the application warns you about it.
When checking user accounts, Kaspersky does not retrieve data in plaintext form, and uses it only for the specified check without storing it. On detecting a leak, Kaspersky Free does not gain access to the user data itself, but only provides information about categories of data that may be publicly accessible.
Kaspersky Free can notify you of a possible leak of the following categories of data:
- Personal data: for example, passport data, biometric data, data about age.
- Banking data: for example, numbers of credit cards and bank accounts, information about funds available on credit cards and bank accounts.
- Activity history: for example, authentication tokens, password history.
By default, Kaspersky Free tries to check your user accounts when you are authorized on a particular website. During authorization, your email address used to sign in to the website is encrypted and forwarded to the KSN cloud. If the check reveals that your data may be publicly accessible, you will receive an appropriate notification. You can disable Data Leak Checker.
You can add up to 50 accounts for automatic checking. Lists of accounts in Kaspersky Free are not synchronized between devices. Added accounts are checked once a day.
Adding accounts to the list for automatic checking may be unavailable in your region.
Kaspersky Free periodically checks the email address linked to your My Kaspersky account. The first such check is performed 48 hours after installation of Kaspersky Free. Further checks are made every 24 hours.
Data Leak Checker for My Kaspersky account does not work if Kaspersky Free is not connected to My Kaspersky or the My Kaspersky account password is not entered in the application.
Page top
How to enable or disable Data Leak Checker
To enable or disable Account Check:
- Open the main window of Kaspersky Free.
- Select the Privacy section.
- In the Data Leak Checker block, click the Search leaks button.
This opens the Data Leak Checker window.
- Use the toggle switch to enable or disable the Data Leak Checker component.
How to check if your data may become publicly accessible
To check if your data may become publicly accessible:
- Open the main window of Kaspersky Free.
- Select the Privacy section.
- In the Data Leak Checker block, click the Search leaks button.
This opens the Data Leak Checker window.
- Specify your email address in the input field and click the Check button.
Kaspersky Free starts checking the specified address. If the check reveals that your data may be publicly accessible, the application will notify you about it and display a list of sites from which a data leak could have occurred, the date of possible leakage, and the category of data that may be publicly accessible. Clicking a data category link will provide recommendations on how to minimize the consequences of a possible leak of this data.
Kaspersky Free lets you check for possible leaks of not only your own data, but from other user accounts that belong to your friends and family, for example.
How to uninstall incompatible applications
Kaspersky Free regularly checks if there are any
on your computer. Such applications are added to the list of incompatible applications. You can look through the list and decide what to do with the incompatible applications.It is recommended that you delete incompatible applications from your computer. Otherwise, Kaspersky Free will not be able to fully protect your computer.
The following are some of the reasons why a third-party application might not be compatible with Kaspersky Free:
- The application conflicts with File Anti-Virus.
- The application conflicts with Firewall.
- The application conflicts with Anti-Spam.
- The application interferes with protecting network traffic.
- The application conflicts with Secret Vault.
- The application conflicts with Kaspersky Password Manager.
How to uninstall incompatible applications
Page top
How to pause and resume computer protection
Pausing protection means temporarily disabling all protection components for some time.
To pause computer protection:
- In the context menu of Kaspersky Free icon located in the taskbar notification area, select the Pause protection item.
The Pause protection window opens.
- In the Pause protection window, select the time interval after which protection will be resumed:
- Pause for – protection is enabled after expiration of the time interval selected from the drop-down list.
- Pause until application restart – protection is enabled after the application is started again or the operating system is restarted (if the application automatically starts on startup).
- Pause – protection will be resumed when you decide to resume it.
- Click the Pause protection button and confirm your choice in the window that opens.
How to resume computer protection
Page top
How to restore the default settings of the application
You can restore the application settings recommended by Kaspersky experts at any time. When the settings are restored, the Optimal security level is set for all protection components.
To restore the default settings of the application:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Select the Manage settings section.
- Click the Restore link to run the Settings Restore Wizard.
- Click Next.
The window of the Wizard shows the progress of restoring the application settings back to the default settings configured by Kaspersky experts.
- After the default application settings restoration process is finished, click Done.
How to view the application operation report
The application maintains operation reports for each of the protection components. Using a report, you can obtain statistical information about the application's operation (for example, how many malicious objects have been detected and neutralized during a specified time period, how many times application databases and modules have been updated during the same period, and much more).
To view the application operation report:
- Open the main application window.
- Go to the Security section.
- Click the Reports button in the upper part of the window.
The Reports window displays data in the form of a table. For convenient viewing of reports, you can select various filtering options.
How to apply the application settings on another computer
Having configured Kaspersky Free in a particular way, you can then apply the settings on another computer. As a result, Kaspersky Free will be configured identically on both computers.
Kaspersky Free settings are saved in a configuration file that you can move from one computer to another.
The settings of Kaspersky Free are moved from one computer to another in three steps:
- Save Kaspersky Free settings to configuration file.
- Move the configuration file to the other computer (for example, by email or on a removable drive).
- Import the settings from the configuration file to Kaspersky Free that is installed on the other computer.
Participating in Kaspersky Security Network
Kaspersky Free uses cloud protection to make protection of your computer more effective. Cloud protection is implemented using the Kaspersky Security Network infrastructure that uses data received from users all over the world.
Kaspersky Security Network (KSN) is the cloud-based knowledge base of Kaspersky containing information about the reputation of applications and websites. The use of data from Kaspersky Security Network ensures faster responses by Kaspersky Free to new threats, improves the performance of some protection components, and reduces the likelihood of false positives.
Users' participation in Kaspersky Security Network allows Kaspersky to promptly receive information about types and sources of new threats, develop solutions for neutralizing them, and minimize the number of false positives. Participation in Kaspersky Security Network lets you access reputation statistics for applications and websites.
If you participate in Kaspersky Security Network, you automatically send information about the configuration of your operating system and the start and completion time of processes in Kaspersky Free to Kaspersky.
How to enable or disable participation in Kaspersky Security Network
Participation in Kaspersky Security Network is voluntary. You can enable or disable the use of Kaspersky Security Network (KSN) when installing Kaspersky Free and/or at any moment after the application is installed.
To enable or disable participation in Kaspersky Security Network:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
- Go to Security settings → Kaspersky Security Network.
The Kaspersky Security Network window opens showing the details of Kaspersky Security Network and Kaspersky Security Network participation settings.
- Enable or disable participation in Kaspersky Security Network by using the toggle in the upper part of the window:
- If you want to participate in Kaspersky Security Network, set the toggle to On.
A window with the text of the Kaspersky Security Network Statement opens. If you accept the terms of the statement, click I agree.
- If you do not want to participate in Kaspersky Security Network, set the toggle to Off.
- If you want to participate in Kaspersky Security Network, set the toggle to On.
In some versions of Kaspersky Free, the Kaspersky Security Network window shows the Kaspersky Security Network Statement instead of information about Kaspersky Security Network.
To accept Kaspersky Security Network Statement:
- Click the Accept button in the Kaspersky Security Network Statement section.
Kaspersky Security Network Statement opens. This statement allows Kaspersky experts to promptly receive information about threats detected on your computer, about applications being run and signed applications being downloaded, as well as operating system information to improve your protection.
- If you accept the terms of the statement, click the Accept button.
To decline the Kaspersky Security Network Statement,
click the Decline button in the Kaspersky Security Network Statement section.
Page top
How to check the connection to Kaspersky Security Network
Your connection to Kaspersky Security Network may be lost for the following reasons:
- You do not participate in Kaspersky Security Network.
- Your computer is not connected to the Internet.
- Current key status does not allow connecting to Kaspersky Security Network. For example, a connection to KSN may be unavailable due to the following reasons:
- The application is not activated.
- License or subscription has expired.
License key issues have been identified (for example, the key has been added to denylist).
To check the connection to Kaspersky Security Network:
- Open the main application window.
- Click
 in the lower part of the main window.
in the lower part of the main window.This opens the Settings window.
Go to Security settings → Kaspersky Security Network.
The Kaspersky Security Network window shows the status of your connection to Kaspersky Security Network.
In some cases, Kaspersky may temporarily restrict requests to Kaspersky Security Network concerning the reputation of files. When temporary restrictions are imposed on requests for information from Kaspersky Security Network, the corresponding notification is displayed.
Page top
Limitations and warnings
Kaspersky Free has a number of limitations that are not critical to operation of the application.
Limitations on configuring protection components
When Kaspersky Free starts for the first time, its protection components are configured automatically according to rules created by Kaspersky specialists. You cannot configure protection components.
Limitations on the operation of certain components and automatic processing of files
Infected files are processed automatically according to rules created by Kaspersky experts. You cannot modify these rules manually. Rules can be updated following an update of databases and application modules.
Limitations of System Watcher functionality
Protection against cryptors (malware that encrypts user files) has the following limitations:
- The Temp system folder is used to support this functionality. If the system drive with the Temp folder has insufficient disk space to create temporary files, protection against cryptors is not provided. In this case, the application does not display a notification that files are not backed up (protection is not provided).
- Temporary files are deleted automatically when you close Kaspersky Free or disable the System Watcher component.
- In case of an emergency termination of Kaspersky Free, temporary files are not deleted automatically. To delete temporary files, clear the Temp folder manually. To do so, open the Run window and in the Open field type
%TEMP%. Click OK. - Protection against encryptors is provided only for files that are located on data drives that have been formatted with the NTFS file system.
- The number of files that can be restored cannot exceed 50 per one encryption process.
- The total volume of modifications to files cannot exceed 100 MB. Files with modifications that exceed this limit cannot be restored.
- File modifications initiated via network interface are not monitored.
- Files encrypted with EFS are not supported.
- You must restart the computer to enable protection against encryptors after Kaspersky Free is installed.
Website certificate check and file scan limitations
When scanning files, the application may query Kaspersky Security Network for information. If data from Kaspersky Security Network could not be retrieved, the application makes decisions on whether or not the file is infected based on local anti-virus databases.
Encrypted connections scan limitations
Due to technical limitations of the implementation of scanning algorithms, scanning of encrypted connections does not support certain extensions of the TLS 1.0 protocol and later versions (particularly NPN and ALPN). Connections via these protocols may be limited. Browsers with SPDY protocol support use the HTTP over TLS protocol instead of SPDY even if the server to which the connection is established supports SPDY. This does not affect the level of connection security. If the server supports only the SPDY protocol and it is impossible to establish the connection via the HTTPS protocol, the application does not monitor the connection established.
The application does not process traffic transmitted via extensions of the HTTP/2 protocol.
Kaspersky Free prevents data exchange over the QUIC protocol. Browsers use a standard transport protocol (TLS or SSL) regardless of whether or not support for the QUIC protocol is enabled in the browser.
Kaspersky Free monitors only those protected connections which it is able to decrypt. The application does not monitor connections added to the list of exclusions (Websites link in the Network settings window).
The following components perform decryption and scanning of encrypted traffic by default:
- Safe Browsing;
- URL Advisor.
Kaspersky Free does not monitor traffic if the browser loads a web page or its elements from a local cache instead of from the Internet.
Limitations on scanning The Bat client encrypted connections
Since The Bat mail client uses its own certificate store, Kaspersky Free identifies the certificate used to establish an HTTPS connection between this client and the server as untrusted. To prevent this from happening, configure The Bat mail client to work with the local Windows Certificate Store.
Limitations on encrypted connections scan exclusions
When scanning encrypted connections with websites that have been added to exclusions, URL Advisor may continue to scan encrypted connections. Safe Browsing does not scan websites that have been added to exclusions.
Specifics of infected file processing by application components
By default, Kaspersky Free can delete infected files that cannot be disinfected. Removal by default can be performed during file processing by such components as Mail Anti-Virus and File Anti-Virus, and during scan tasks.
Specifics of the autorun process operation
The autorun process logs the results of its operation. Data is logged in text files named “kl-autorun-<date><time>.log”. To view data, open the Run window (Run command under Windows XP) and in the Open field type %TEMP% and click OK.
All trace files are saved at the path to setup files that were downloaded during operation of the autorun process. Data is stored for the duration of operation of the autorun process and deleted permanently when this process is terminated. Data is not sent anywhere.
Kaspersky Free limitations under Microsoft Windows 10 RS4 with the Device Guard mode enabled:
Operation of the following functionality is partly limited:
- Clipboard protection
- Browser protection from keyboard and mouse input emulators (input spoofing)
- Protection from remote management applications
- Browser protection (management through API, protection from attacks that use dangerous messages to browser windows, protection from message queue management)
- Heuristic Analysis (emulation of the startup of malicious applications)
If UMCI mode is enabled in Windows, Kaspersky Free does not detect screen lockers.
About logging of events in the Windows event log that are related to the End User License Agreement and Kaspersky Security Network
Events involving accepting and declining the terms of the End User License Agreement, and also accepting and declining participation in Kaspersky Security Network, are recorded in the Windows event log.
Limitations on local address reputation checks in Kaspersky Security Network
Links to local resources are not scanned in Kaspersky Security Network.
Warning about applications that collect information
If an application that collects information and sends it to be processed is installed on your computer, Kaspersky Free may classify this application as malware. To avoid this, you can exclude the application from scanning by configuring Kaspersky Free as described in this document.
Warning about the creation of an application installation report
An installation report file is created when the application is installed to a computer. If application installation completed with an error, an installation report file is saved and you can send it to Kaspersky Technical Support. You can view the contents of the installation report file by clicking the link in the application window. If the application is successfully installed, the installation report file is immediately deleted from your computer.
Limitations when the application is started for the first time after upgrading from Microsoft Windows 7 to Microsoft Windows 10
If you have upgraded Microsoft Windows 7 to Microsoft Windows 8 / 8.1 or Microsoft Windows 10 / RS1 / RS2 / RS3, Kaspersky Free operates with the following limitations when started for the first time:
- Only File Anti-Virus (real-time protection) is running. Other application components are not running.
- Self-Defense of files and the system registry is running. Self-Defense of processes is not running.
- The application interface is not available until you restart the computer. The application displays a notification stating that some application components are not running and that the computer must be restarted after completion of adaptation to the new operating system.
- Only the Exit option is available in the context menu of the application icon in the notification area.
- The application does not display notifications, and automatically chooses the recommended action.
Warning about error adapting application drivers when upgrading the operating system from Windows 7 to Windows 10
Upgrading Windows 7 to Windows 10 may result in an error adapting the drivers of Kaspersky Free. Drivers are adapted in the background, which means that you do not receive notifications about its progress.
If there is an error adapting the drivers, you will not be able to use the following features of the application:
- Threat detection while the operating system is loading
- Protection of application processes by using the Protected Process Light (PPL) technology of Microsoft Corporation
You can use the following methods to fix the error:
- Restart the computer and restart application adaptation from the notification in the Notification Center.
- Uninstall the application and re-install it.
Limitations on scanning traffic sent over HTTPS in the Mozilla Firefox browser
In Mozilla Firefox 58.x and later versions, the application does not scan traffic transmitted over the HTTPS protocol if browser settings modification is protected by a Primary password. When a Primary password is detected in the browser, the application shows a notification containing a link to an article in the Knowledge Base. The article contains instructions on resolving this problem.
If HTTPS traffic is not monitored, the operation of the following components is limited:
- Safe Browsing;
- Anti-Phishing;
- Secure Data Input.
Limitations of the Kaspersky Protection extension in Google Chrome and Mozilla Firefox
The Kaspersky Protection extension does not operate in Google Chrome and Mozilla Firefox if there is Malwarebytes for Windows installed on your computer.
Special considerations when installing the application in Microsoft Windows 7 Service Pack 0 and Service Pack 1
When installing the application in an operating system that does not support certificates with an SHA256 digital signature, the application installs its own trusted certificate.
About automatic testing of functionality of Kaspersky applications
Kaspersky applications including Kaspersky Free, have a special API (application programming interface) for automatic testing of application functionality. This API is intended to be used only by Kaspersky developers.
Page top
Other sources of information about the application
Kaspersky Free page in the Knowledge Base
Knowledge Base is a section on the Technical Support website.
On Kaspersky Free page in the Knowledge Base, you can read articles that provide useful information, recommendations, and answers to frequently asked questions on how to purchase, install, and use the application.
Articles in the Knowledge Base may provide answers to questions that relate both to Kaspersky Free as well as to other Kaspersky applications. Articles in the Knowledge Base may also contain news from Technical Support.
Support for Kaspersky applications in our Forum
You can receive support from users and Kaspersky experts in our Forum.
In the Forum, you can view existing topics, post your comments, and create new topics for discussion and getting help.
Page top
List of services to which the password is sent when a QR code is scanned
When you scan a QR code on Android, a single-use password for activating the application on your smartphone is sent to Google Play and AppsFlyer.
Page top
Network settings for interaction with external services
Kaspersky Free uses the following network settings for interacting with external services.
Network settings
Address |
Description |
|---|---|
Protocol: Port: |
Activating the application. |
Protocol: Port: |
Updating databases and application software modules. |
Protocol: Port: |
Requests sent by the application may contain addresses of domains and the public IP address of the user because the application establishes a TCP/UDP connection with the DNS server. This information is needed, for example, to validate the certificate of a web resource when using HTTPS. If Kaspersky Free is using a public DNS server, data processing is governed by the privacy policy of the relevant service. If you want to prevent Kaspersky Free from using a public DNS server, contact Technical Support for a private patch. |
Protocol: |
|
Protocol: Port: |
Updating databases and application software modules. |
Protocol: Port: |
Using Kaspersky Security Network. |
Protocol: Port: |
Using Kaspersky Security Network. |
Protocol: |
Follow links from the interface. |
Restoring data from a backup copy using Kaspersky Restore Utility
Kaspersky Restore Utility lets you manage backup storage data on a computer where a Kaspersky application is corrupted or has been removed. By default, after installation of the application the utility is located in the Kaspersky Restore Utility folder located in the application setup folder. To use the utility on a computer where a Kaspersky application is not installed or is corrupted, copy the utility to a removable drive.
To start Kaspersky Restore Utility, you need local administrator rights.
How to start the Restore Utility
How to open a storage using the Restore Utility
How to restore data from a backup copy
Page topGlossary
Activation code
A code that you receive when purchasing a license for Kaspersky Free. This code is required for activation of the application.
The activation code is a unique sequence of twenty alphanumeric characters in the format xxxxx-xxxxx-xxxxx-xxxxx.
Anti-virus databases
Databases that contain information about computer security threats known to Kaspersky as of when the anti-virus databases are released. Entries in anti-virus databases allow detecting malicious code in scanned objects. Anti-virus databases are created by Kaspersky specialists and updated hourly.
Application modules
Files included in the Kaspersky installation package that are responsible for performing the main tasks of the corresponding application. A particular application module corresponds to each type of task performed by the application (protection, scan, updates of anti-virus databases and application modules).
Blocking an object
Denying access to an object from third-party applications. A blocked object cannot be read, executed, modified, or deleted.
Compressed file
A compressed executable file that contains a decompression program and instructions for the operating system to execute it.
Database of malicious web addresses
A list of web addresses whose content may be considered to be dangerous. Created by Kaspersky specialists, the list is regularly updated and is included in the Kaspersky application package.
Database of phishing web addresses
List of web addresses which have been defined as phishing web addresses by Kaspersky specialists. The databases are regularly updated and are part of the Kaspersky application package.
Disk boot sector
A boot sector is a special area on a computer's hard drive, floppy disk, or other data storage device. It contains information on the disk's file system and a boot loader program, which is responsible for starting the operating system.
There exist a number of viruses that infect boot sectors, which are thus called boot viruses. The Kaspersky application allows scanning boot sectors for viruses and disinfecting them if an infection is found.
Exploit
A software code that uses a vulnerability in the system or software. Exploits are often used to install malware on the computer without user's knowledge.
False positive
A situation when a Kaspersky application considers a non-infected object to be infected because the object's code is similar to that of a virus.
Heuristic analyzer
A technology for detecting threats about which information has not yet been added to Kaspersky databases. The heuristic analyzer detects objects whose behavior in the operating system may pose a security threat. Objects detected by the heuristic analyzer are considered to be probably infected. For example, an object may be considered probably infected if it contains sequences of commands that are typical of malicious objects (open file, write to file).
iChecker Technology
A technology that allows increasing the speed of anti-virus scanning by excluding objects that have remained unchanged since their last scan, provided that the scan parameters (the databases and the settings) have not been altered. The information for each file is stored in a special database. This technology is used in both real-time protection and on-demand scan modes.
For example, you have an archive file that was scanned by a Kaspersky application and assigned not infected status. Next time, the application will skip this archive unless the archive has been altered or the scan settings have been changed. If you have changed the archive content by adding a new object to it, modified the scan settings, or updated the application databases, the archive will be re-scanned.
Limitations of iChecker technology:
- This technology does not work with large files, since it is faster to scan a file than to check whether the file has been modified since it was last scanned.
- The technology supports a limited number of formats.
Incompatible application
An anti-virus application from a third-party developer or a Kaspersky Lab application that does not support management through Kaspersky Free.
Infected object
An object a portion of whose code completely matches part of the code of known malware. Kaspersky does not recommend accessing such objects.
Kaspersky Security Network (KSN)
The cloud-based knowledge base of Kaspersky containing information about the reputation of applications and websites. Use of data from Kaspersky Security Network ensures faster responses by Kaspersky applications to threats, improves the performance of some protection components, and reduces the likelihood of false positives.
Kaspersky update servers
Kaspersky HTTP servers from which updates of databases and software modules are downloaded.
License term
A time period during which you have access to the application features and rights to use additional services.
Phishing
A type of Internet fraud aimed at obtaining unauthorized access to users' confidential data.
Probably infected object
An object whose code contains portions of modified code from a known threat, or an object whose behavior is similar to that of a threat.
Protection components
Integral parts of Kaspersky Free intended for protection against specific types of threats (for example, Anti-Phishing). Each of the components is relatively independent of the other ones and can be disabled or configured individually.
Protocol
A clearly defined and standardized set of rules governing the interaction between a client and a server. Well-known protocols and the services associated with them include HTTP, FTP, and NNTP.
Quarantine
A dedicated storage in which the application places backup copies of files that have been modified or deleted during disinfection. Copies of files are stored in a special format that is not dangerous for the computer.
Rootkit
A program or a set of programs for hiding traces of an intruder or malware in the operating system.
On Windows-based operating systems, a rootkit usually refers to a program that penetrates the operating system and intercepts system functions (Windows APIs). Interception and modification of low-level API functions are the main methods that allow these programs to make their presence in the operating system quite stealthy. A rootkit can usually also mask the presence of any processes, folders, and files that are stored on a disk drive, in addition to registry keys, if they are described in the configuration of the rootkit. Many rootkits install their own drivers and services on the operating system (these also are "invisible").
Script
A small computer program or an independent part of a program (function) which, as a rule, has been developed to execute a specific task. It is most often used with programs that are embedded in hypertext. Scripts are run, for example, when you open some websites.
If real-time protection is enabled, the application tracks the execution of scripts, intercepts them, and scans them for viruses. Depending on the results of scanning, you may block or allow the execution of a script.
Security level
The security level is defined as a predefined collection of settings for an application component.
Startup objects
The set of programs needed to start and correctly operate the operating system and software installed on your computer. These objects are executed every time the operating system is started. There are viruses capable of infecting autorun objects specifically, which may lead, for example, to blocking of operating system startup.
Task
The functions of the Kaspersky application are implemented in the form of tasks, such as: Full Scan task or Update task.
Task settings
Application settings that are specific for each task type.
Traces
Running the application in debugging mode; after each command is executed, the application is stopped, and the result of this step is displayed.
Traffic scanning
Real-time scanning that uses information from the current (latest) version of the databases for objects transferred over all protocols (for example, HTTP, FTP, and other protocols).
Unknown virus
A new virus about which there is no information in the databases. Generally, unknown viruses are detected by the application in objects by using the heuristic analyzer. These objects are classified as probably infected.
Update
The procedure of replacing / adding new files (databases or application modules) retrieved from the Kaspersky update servers.
Update package
A file package designed for updating databases and application modules. The Kaspersky application copies update packages from Kaspersky update servers and automatically installs and applies them.
Virus
A program that infects other programs, by adding its code to them in order to gain control when infected files are run. This simple definition allows identifying the main action performed by any virus: infection.
Vulnerability
A flaw in an operating system or an application that may be exploited by malware makers to penetrate the operating system or application and corrupt its integrity. Presence of a large number of vulnerabilities in an operating system makes it unreliable, because viruses that penetrate the operating system may cause disruptions in the operating system itself and in installed applications.
Page top
Information about third-party code
Information about third-party code is contained in the file legal_notices.txt, in the application installation folder.
Page top
Trademark notices
Registered trademarks and service marks are the property of their respective owners.
Adobe, Acrobat, Reader are either registered trademarks or trademarks of Adobe in the United States and/or other countries.
Apple and Safari are trademarks of Apple Inc., registered in the United States and other countries and regions.
Google, Google Play, Google Chrome, Chromium, Android, SPDY are trademarks of Google LLC.
Intel, Celeron, and Atom are trademarks of Intel Corporation in the U.S. and/or other countries.
Linux is a trademark of Linus Torvalds, registered in the U.S. and other countries.
LogMeIn Pro and Remotely Anywhere are trademarks of LogMeIn, Inc.
Mail.ru is a Trademark of Mail.ru LLC.
Microsoft, Windows, Windows Mail, PowerShell, Internet Explorer, Outlook are trademarks of the Microsoft group of companies.
Mozilla, Thunderbird, and Firefox are trademarks of the Mozilla Foundation.
VMware is a registered trademark of VMware, Inc. in the United States and/or other jurisdictions.
Java is a registered trademark of Oracle Corporation and/or its affiliates.
Page top
Enter activation code window
Fields for entering an application activation code
Restore subscription from your account
Where can I find an activation code?
Page top
Activation code corresponds to another application
This window opens if the activation code entered is intended for another application. You can start using this application now or after your subscription for Kaspersky Free expires.
Page top
Information about the current license is found window
No, continue the wizard and enter a new activation code
Page top
Registration window
In this window, specify the registration data required to contact Technical Support.
Page top
Internet connection is not available
This window is displayed if you fail to activate the application due to problems with your Internet connection.
Page top
Activation error
Application activation failed. To view information about the issue in the Knowledge Base, click the Reasons and possible solutions link.
Reasons and possible solutions
Page top
Switching to other application
To run the Migration Wizard, click the Continue button. The Migration Wizard will help you migrate to the new subscription.
To cancel the migration to the new subscription, click Decline.
Page top
About the use of the application by a child
If Kaspersky Safe Kids is installed and used on your computer, the child can use Kaspersky Free to disable Kaspersky Safe Kids. To avoid this, we recommend that you protect access to Kaspersky Free settings with a password.
If you signed in to the operating system under an account that is linked to a child profile in Kaspersky Safe Kids, Kaspersky Free stops showing the following notifications:
- Notifications about security news
- Notifications about the detection of weak settings in the operating system
- Notifications about the current device connecting to a Wi-Fi network
- Notifications about a device connecting to a home Wi-Fi network
- Browser notifications about an insufficiently strong password being entered on a website
- Notifications warning you that the password you are entering on a website has already been previously entered by you on a different website
You can enable notifications by selecting the Show notifications in children's accounts check box in the Settings → Interface window.
Page top
Permissions
A password protects the following application settings from being changed by a user or group. If a check box next to an action is selected, it means that the user or user group is allowed to perform the selected action.
Configure application settings |
Change application settings in the main window, the Settings window, Notification Center and notifications. |
Exit the application |
Exit the application. |
Remove / modify / restore the application |
Remove, modify and restore the application. |
View reports |
Go to the Reports window. |
Disable protection components |
Pause scanning from the context menu of the application icon in the taskbar notification area. |
Subscription details window
This window displays the following application subscription information:
- Subscription status
- Number of days remaining until subscription expires
- Number of devices covered by the subscription
- Activation date
- Subscription expiration date
End User License Agreement window
The window contains the text of the End User License Agreement. Use the scroll bar to view the End User License Agreement.
Page top
Licensing window
License information is displayed in the section located in the upper part of the window:
- License key
- Key status
- Number of hosts covered by the license
- Activation date
- License expiration date
- Number of days before expiration of the license
About your license/About your subscription
Depending on the presence of a license and on the properties of your version of the application, the window may display various buttons for initiating actions related to your license. Default buttons are described below.
Reasons and possible solutions
Page top
Certificate Installation
This window displays the progress of automatic installation of the certificate. Task completion may take some time.
Kaspersky Free searches for web browsers installed on the user's computer and then automatically installs certificates to the Microsoft Windows certificate storage.
While installing the certificate, a Microsoft Windows security notification may appear on the screen, prompting you to confirm installation of the certificate.
Page top
Special considerations when adding a rule for a network adapter
When you create an allow rule for a network adapter and/or a rule with a specified TTL, this rule may conflict with a deny rule for applications. For example, if an application is in the High Restricted group, it will be denied network access even if you created an allow packet rule for the network adapter (and for TTL).
To configure an allow rule to work for all applications that attempt to connect to the network via this network adapter, you must create the following rules in order of priority from the highest priority to the lowest priority (in the general list of packet rules, the priority is determined from top to bottom, going from the highest priority to the lowest priority).
- Allow rule for the selected network adapter.
- Deny rules for all other network adapters.
- Allow rule without specifying a network adapter.
To configure an allow rule to work for a network adapter using TTL, you must create the following rules in order of priority from the highest priority to the lowest priority:
- Allow rule for a specific TTL value.
- Deny rule for a TTL value equal to 255.
- Allow rule without specifying a TTL value.
Network connections termination
If the computer is shut down or protection is paused when the application is monitoring active network connections, notification about termination of those connections is displayed. This is necessary for properly quitting the application. Termination occurs automatically after 10 seconds or after you click the Yes button. Most terminated connections are recovered after a short time.
If the connection is terminated when you are downloading a file without a download manager, data transmission is interrupted. To download the file, you must start the download process again.
You can cancel termination of connections. To do this, in the notification dialog box, click the No button. The application continues to run.
Page top
Kaspersky Free notification windows
Notifications that appear in the taskbar notification area inform you of application events that require your attention.
If a notification is displayed on the screen, you should select one of the options that are suggested in the notification. The optimal option is the one recommended as the default by Kaspersky experts.
Page top
Registration
When you sign in to an existing My Kaspersky account, the window displays the following:
During My Kaspersky account creation, the window displays the following:
I agree to provide Kaspersky with my email address to receive personalized marketing offers
More about My Kaspersky account
Page top
Quarantine window
Kaspersky Free does not disinfect Windows Store apps. If scanning results indicate that such an app is dangerous, it is deleted from your computer. When a Windows Store app is deleted, Kaspersky Free does not create a backup copy of it. To restore such objects, you must use the recovery tools included with the operating system (for detailed information, see the documentation for the operating system that is installed on your computer) or update apps via the Windows Store.
Updates search mode / Schedule
The table describes the settings that control the schedule for the App Updater and Application Manager components.
Settings |
Description |
|---|---|
Updates search mode (App Updater) Run analysis (Application Manager) |
Automatically. Kaspersky Free runs the task once every 24 hours according to the internal settings. Every minute / Every hour / Every day / Weekly / Monthly / At a specified time. Kaspersky Free runs the task according to your defined schedule, which can be specified up to the exact minute. When one of these options is selected, the Postpone running after application startup for N minutes list is available. After application startup. After Kaspersky Free starts, it runs the task after waiting the amount of minutes indicated in the Start in N minutes field. After every update. Kaspersky Free runs the task after downloading and installing a new update package. |
Search for updates on the next day if computer is turned off (App Updater) Run object analysis on the next day if computer is turned off (Application Manager) |
If a scheduled search for application updates or object analysis was skipped because the computer was turned off, Kaspersky Free runs the task after the computer is turned on. This check box is displayed if one of the following run modes is selected: Every day / Weekly / Monthly / At a specified time. |
Search for application updates only when screensaver is active or computer is locked (App Updater) Run object analysis only when screensaver is active or computer is locked (Application Manager) |
Kaspersky Free runs the task when you are finished working with the computer. This means that the task will not use system resources while you work. This check box is displayed if the After every update run mode is selected. |
Update settings
Settings |
Description |
|---|---|
Databases update schedule |
Clicking this link opens the Databases update schedule window in which you can select one of the database update run modes: Automatically. Update task run mode, under which Kaspersky Free scans for the update package in the update source at a particular frequency. The scanning frequency can be increased during virus outbreaks and decreased when there are none. After detecting a fresh update package, Kaspersky Free downloads it and installs the updates on the computer. Manually. This task run mode allows you to run the update task manually. Every minute / Every hour / Every day / Weekly / Monthly / At a specified time / After application startup. Update task run mode in which Kaspersky Free runs the update task according to the schedule you have created. If you select this update task run mode, you can also run the Kaspersky Free update task manually. |
Select update sources |
Clicking this link opens a window with the list of update sources. An update source is a public HTTP or FTP server or a shared folder (local or network) from where the application can download update databases and modules. By default, the list of update sources contains Kaspersky update servers. You can add other update sources to the list. If several update sources are selected from the list, Kaspersky Free will query them one after the other until it reaches the first available update source from which it is able to download the update package. |
Run database updates as |
Clicking the link opens a window in which you can choose to run the database update with a particular user’s rights. By default, the Kaspersky Free update task is run in the name of the user with whose rights you are registered in the operating system. However, Kaspersky Free can be updated from an update source to which the user does not have access rights (for example, from a shared folder containing the update package) or for which there is no configured authentication on the proxy server. You can specify a user that possesses the required rights in the application settings and run Kaspersky Free update task in the name of this user. |
Recommended setting window
Turn on protection against ads to install only desired software and block additional installations
Page top
Reports window
You can use the following capabilities for convenient management of reports:
- Filter by date;
- Filter by value in any cell;
- Search by event record text;
- Sort the list by each report column;
- Change the order and arrangement of columns that are displayed in the report.
The following event importance levels are used in reports:
![]() Informational messages. Informational events that generally do not contain important information.
Informational messages. Informational events that generally do not contain important information.
![]() Warnings. Events that you need to pay attention to, since they contain information about important situations that Kaspersky Free encounters when running.
Warnings. Events that you need to pay attention to, since they contain information about important situations that Kaspersky Free encounters when running.
![]() Critical events. Critically important events that indicate that Kaspersky Free has encountered problems affecting its ability to run or vulnerabilities affecting the protection level of the user’s computer.
Critical events. Critically important events that indicate that Kaspersky Free has encountered problems affecting its ability to run or vulnerabilities affecting the protection level of the user’s computer.
When you click the Save report button, you can save the report as either a TXT or CSV format file.
Select a ZIP file or folder
Custom design themes are not available in some regions.
When choosing a theme, consider the following limitations:
- Kaspersky Free will not be able to use the selected theme in the following cases:
- The files within the archive have a name or path within the folder structure that is different than in the default theme.
- The archived files responsible for the texts in the application windows are corrupted.
- Themes are designed for a specific version of Kaspersky Free and are not applicable to other versions or other applications. When upgrading the application to a new version or installing another application over it, the theme is changed to the default theme.
If you encounter problems when selecting an alternative theme and you cannot install the default theme using the prescribed method (for example, you cannot clear the Use a custom design theme check box in the Interface settings window because the font merges with the background and the necessary management elements are indistinguishable), you are advised to reinstall Kaspersky Free.
Page top
Reports and Quarantine settings
In the Reports section, you can configure the settings for report creation and storage.
Limit the size of report file to
In the Quarantine section, you can modify Quarantine settings.
Limit the size of Quarantine to
Page top
Proxy server settings
Automatically detect proxy server settings
Use specified proxy server settings
Use proxy server authentication
Bypass proxy server for local addresses
Page top
Password protection window
The Change or remove password link is available if a password has been set earlier to protect access to Kaspersky Free functions.
In the Password scope section, you can specify which parts of application administration you want to protect with a password.
Configure application settings
Scan settings
The table describes the settings that control the following types of scans: Full Scan, Quick Scan, Selective Scan, and Instant File Scan.
Settings |
Description |
|---|---|
Security level |
Kaspersky Free uses various sets of settings for scanning. The sets of settings that are stored in the application are called security levels:
|
Action on threat detection |
Before attempting to disinfect or delete an infected file, the application creates a backup copy in case you subsequently need to restore the file or it becomes possible to disinfect it later. |
Edit scan scope (not available in the Context Menu Scan settings) |
Clicking the link opens a window with a list of objects that Kaspersky Free can scan. Depending on the type of scan (Full Scan, Quick Scan or Selective Scan), various objects will be included by default in the list. You can add objects to the list or delete the objects that you add. To remove an object from the scan, you do not have to delete the object from the list. All you need to do is clear the check box next to the object name. |
Scan schedule (not available in the Context Menu Scan settings) |
Manually. Run mode in which you can start scan manually at a time when it is convenient for you. By schedule. Scan run mode in which the application runs the scan task according to the schedule you have created. If you select this scan run mode, you can also run the scan task manually. |
Run scan as |
Clicking the link opens a window in which you can choose to run the scan with a particular user’s rights. By default the scan task is run in the name of the user with whose rights you are registered in the operating system. The protection scope may include network drives or other objects that require special rights to access. You can specify a user that possesses the required rights in the application settings and run the scan task on behalf of this user. |
File types |
Kaspersky Free treats files without extensions as executables. The application always scans them, regardless of the file types you have selected for scanning. All files. If this setting is enabled, Kaspersky Free scans all files without exception (all formats and extensions). Files scanned by format. If you select this setting, the application will scan only . Before searching for malicious code in a file, its internal header is analyzed to determine the file format (for example, TXT, DOC, EXE). The scan also looks for files with particular file extensions.Files scanned by extension. If you select this setting, the application will scan only potentially infected files. The file format is determined based on the extension of a file. |
Scan only new and changed files |
Scans only new files and those files that have been modified since the last time they were scanned. This will allow you to save time performing the scan. This scan mode applies both to simple and compound files. |
Skip objects scanned longer than N seconds |
Limits the duration for scanning a single object. After the specified amount of time has run out, the application will stop the file scan. This will allow you to save time performing the scan. |
Scan archives |
Scan ZIP, GZIP, BZIP, RAR, TAR, ARJ, CAB, LHA, JAR, ICE and other archives. The application scans archives not only by their extension, but by their format as well. |
Scan distribution packages |
The check box enables/disables the scanning of third-party distribution packages. |
Scan files in Microsoft Office formats |
Scans Microsoft Office files (DOC, DOCX, XLS, PPT and other Microsoft extensions). Office format files also include OLE objects. |
Scan email formats |
This check box enables / disables the option for Kaspersky Free to scan files in email formats and mail databases. The application fully scans only Microsoft Outlook, Windows Mail/Microsoft Outlook Express and EML mail file formats, and only if the computer has the Microsoft Outlook x86 mail client. If this check box is selected, Kaspersky Free parses the email format file and analyzes each component (body, attachments) for viruses. If this check box is cleared, Kaspersky Free scans the email format file as a single object. |
Scan password-protected archives |
If the check box is selected, the application scans password-protected archives. Before files contained in the archive can be scanned, a request for password will be displayed on the screen. If the check box is not selected, the application skips scanning password-protected archives. |
Do not unpack large compound files Maximum file size |
If the check box is selected, the application does not scan compound files that are larger than the specified value. If this check box is cleared, the application scans compound files of all sizes. The application scans large files that are extracted from archives regardless of whether the check box is selected or not. |
Heuristic Analysis |
A technique for detecting threats that cannot be identified using the current version of the Kaspersky application databases. It allows you to find files that may contain unknown malware or a new modification of a known malware program. When scanning files for malicious code, the heuristic analyzer executes instructions in the executable files. The number of instructions that are executed by the heuristic analyzer depends on the level that is specified for the heuristic analyzer. The heuristic analysis level sets the balance between the thoroughness of searches for new threats, the load on the operating system resources, and the time required for heuristic analysis. |
iSwift Technology |
This technology is a development of the iChecker technology for computers using the NTFS file system. There are limitations to iSwift Technology: it is bound to a specific file's location in the file system and works only with objects in the NTFS file system. When you upgrade Kaspersky Free to a new version, the iSwift technology is enabled for all scan types, even if it was previously disabled. |
iChecker Technology |
This technology allows increasing scan speed by excluding certain files from scanning. Files are excluded from the scan using a special algorithm that takes into account the release date of Kaspersky Free databases, the date when the file was scanned last, and any changes made to the scan settings. There are limitations to iChecker Technology: it does not work with large files and applies only to files with a structure that the application recognizes (for example, EXE, DLL, LNK, TTF, INF, SYS, COM, CHM, ZIP, and RAR). |
Removable drives scan settings
Settings |
Description |
|---|---|
Action when a removable drive is connected |
|
Maximum removable drive size |
If this check box is selected, Kaspersky Free will scan all external devices that do not exceed the specified maximum size. If this check box is cleared, Kaspersky Free scans external devices of all sizes. |
Show scan progress |
If this check box is selected, Kaspersky Free shows the progress of external device scans in a separate window and in the running scan window. |
Block the stopping of the scan task |
If this check box is selected, the Stop button is unavailable for external device scans in the running scan window. |
Background scan settings
If background scan is enabled, Kaspersky Free will perform a background scan. A Background scan is an automatic scan mode that does not display notifications. This scan requires fewer computer resources than other types of scans (for example, Full Scan). When in this mode, Kaspersky Free scans the system memory, system volumes, boot sectors and startup objects, and searches for rootkits.
If the computer is running on battery power, Kaspersky Free will not perform background scans when the computer is idle.
Page top
Application Vulnerability Scan settings
Settings |
Description |
|---|---|
Edit search scope |
Clicking the link opens the Application Vulnerability Scan scope window with a list of objects that are scanned for vulnerabilities in applications. You can add objects to the list or delete the objects that you add. To remove an object from the scan, you do not have to delete the object from the list. All you need to do is clear the check box next to the object name. |
Search schedule |
Manually. Run mode in which you can start the Application Vulnerability Scan manually at a convenient time. By schedule. Scan run mode in which the application runs the scan task according to the schedule you have created. If you select this scan run mode, you can also run the scan task manually. |
Network Attack Blocker settings
Network Attack Blocker loads at operating system startup and tracks incoming network traffic for activities characteristic of network attacks. When Kaspersky Free detects a network attack attempt on a user's computer, it blocks the network connection with the attacking computer. Descriptions of currently known types of network attacks and methods of neutralizing them are specified in Kaspersky Free databases. The list of network attacks that are detectable by the Network Attack Blocker is updated when the application databases and modules are updated.
Network Attack Blocker settings
Settings |
Description |
|---|---|
Treat port scanning and network flooding as attacks |
Network Flooding is an attack on organization's network resources (for example, web servers). This attack consists in sending a massive amount of traffic to exhaust the traffic capacity of a network. As a result, users can't access organization's network resources. Port scanning attack consists in scanning UDP- and TCP ports, as well as network services on the computer. This attack allows to determine computer’s vulnerability level before even more dangerous types of network attacks. Port scanning also allows hackers to determine computer's OS and choose OS-specific attacks for it. If the toggle is on, the Network Attack Blocker component blocks port scanning and network flooding. |
Add an attacking computer to the list of blocked computers for N min |
If the toggle is on, the Network Attack Blocker component adds the attacking computer to the blocked list. This means that the Network Attack Blocker will block the network connection with the attacking computer after the first network attack attempt during the specified period of time in order to automatically protect the user’s computer against any possible future network attacks from the same address. The attacking computer can be added to the block list for a minimum time of one minute. The maximum duration is 32 768 minutes. |
Manage exclusions |
The list contains IP addresses from which the Network Attack Blocker does not block network attacks. The application does not report information about network attacks from IP addresses included in the exception list. |
System Watcher settings
In the Exploit Prevention section, you can configure the actions that the application performs when executable files are run by vulnerable applications.
Monitor attempts to perform unauthorized operations
Action on detection of malicious or other activity
Action to perform if malicious or other activity can be rolled back
In the Protection against screen lockers section, you can configure the actions that are performed if screen locker activity is detected. Screen lockers are malicious programs that limit the user's operations on a computer, by locking the screen and the keyboard, or by blocking access to the taskbar and shortcuts. Screen lockers may attempt to extort ransom for recovery of access to the operating system. By using protection against screen lockers, you can close any screen locker by pressing a specified combination of keys.
Detect and close screen lockers
Use the following key combination to close a screen locker manually
Page top
PC resource consumption
Settings |
Description |
|---|---|
Perform recommended actions automatically |
If the check box is cleared, main components of Kaspersky Free work in interactive mode. This means that Kaspersky Free asks you to decide which action to take on detected objects and threats if the Ask user option is selected in the settings of File Anti-Virus, Safe Browsing, Mail Anti-Virus, System Watcher, and Intrusion Prevention. If the check box is selected, Kaspersky Free automatically chooses the action based on rules defined by Kaspersky experts. |
Delete malicious tools, adware, auto-dialers and suspicious packers |
If the check box is selected, Kaspersky Free deletes malicious tools, adware, auto-dialers and suspicious packers in automatic protection mode. The function is available if the Perform recommended actions automatically check box is selected. |
Battery Saver |
If the check box is selected, energy conservation mode is enabled. Kaspersky Free postpones scheduled tasks. You can start scan and update tasks manually, if necessary. |
Game Mode |
If the check box is selected, the application does not run scan or update tasks and does not display notifications when you play games or run applications in full-screen mode. |
Do not Disturb Mode |
If the check box is selected, Kaspersky Free does not display event notifications during video calls and when watching videos. |
Postpone computer scan tasks when the CPU and disk systems are at high load |
When Kaspersky Free runs schedule tasks, this may result in increased workload on the CPU and disk subsystems, which affects the performance of other applications. When the check box is selected, Kaspersky Free suspends scheduled tasks when it detects an increased load and frees up operating system resources for user applications. |
Scan for weak operating system settings |
If this check box is selected, Kaspersky Free searches for weak settings of the operating system automatically. |
Launch <PRODUCT> at computer startup (recommended) |
When the check box is selected, Kaspersky Free is started after the operating system loads, protecting the computer during the entire session. When the check box is cleared, Kaspersky Free is not started after the operating system loads, until the user starts it manually. Computer protection is disabled and user data may be exposed to threats. |
Use Advanced Disinfection technology (requires considerable computer resources) |
If the check box is selected, a pop-up notification appears on the screen when malicious activity is detected in the operating system. In its notification, Kaspersky Free offers the user to perform Advanced Disinfection of the computer. After the user approves this procedure, Kaspersky Free neutralizes the threat. After completing the advanced disinfection procedure, Kaspersky Free restarts the computer. The advanced disinfection technology uses considerable computing resources, which may slow down other applications. While the application is detecting an active infection, some operating system functionality may not be available. Availability of the operating system is restored after Advanced Disinfection is complete and the computer is restarted.
|
Automatically search for ways to speed up your PC |
If the check box is selected, automatic search for opportunities to speed up the computer is performed. |
Enable Self-Defense |
When this check box is selected, Kaspersky Free prevents alteration or deletion of application files on the hard drive, memory processes, and entries in the system registry. |
Allow managing <PRODUCT> settings via remote control applications |
If this check box is selected, trusted remote administration applications (such as TeamViewer, LogMeIn Pro and Remotely Anywhere) can change Kaspersky Free settings. Untrusted remote control applications will not be allowed to change Kaspersky Free settings, even when the check box is selected. |
Enable external management of system services |
If the check box is selected, Kaspersky Free allows management of application services from a remote computer. When an attempt is made to manage application services remotely, a notification is displayed in the Microsoft Windows taskbar, above the application icon (unless the notification service has been disabled by the user). |
Enable dump writing |
If the check box is selected, Kaspersky Free writes dumps when it crashes. If the check box is cleared, Kaspersky Free does not write dumps. The application also deletes existing dump files from the computer hard drive. |
Enable dump and trace files protection |
If the check box is selected, access to dump files is granted to the system administrator and local administrator as well as to the user who enabled dump writing. Only system and local administrators can access trace files. If the check box is cleared, any user can access dump files and trace files. |
Threats and Exclusions
Settings |
Description |
|---|---|
Types of detected objects |
The application detects various types of objects, such as viruses and worms, Trojans, and adware. For details, please refer to the Kaspersky Encyclopedia. You can disable detection of the following types of objects:
|
Manage exclusions |
Clicking this link opens the Exclusions window containing a list of scan exclusions. A scan exclusion is a set of conditions that, when fulfilled, cause the application to not scan a particular object for viruses and other threats. You can add, edit, or delete exclusions from the list. In the window for adding or editing an exclusion, you can define specific conditions that, when fulfilled, will prevent objects from being scanned (the application will not scan them):
Instead of deleting an exclusion from the list, you can change the status of an en exclusion to Inactive (in the window for adding or editing an exclusion). When inactive, the exclusion will not be applied. |
Specify trusted applications |
Clicking this link opens a window with the list of trusted applications. Kaspersky Free does not monitor file activity and network activity of trusted applications (including malicious ones), and does not monitor these applications' queries to the system registry. You can add, edit, or delete trusted applications from the list. Even if an application is on the trusted list, Kaspersky Free continues to scan the executable file and process of this application for viruses and other threats. If you do not want to scan the executable file and process of a trusted application, add the application to the list of exclusions. When adding or editing a trusted application, in the Exclusions for application window you can specify rules that will be used by Kaspersky Free to monitor the activity of the trusted application. In the Exclusions for application window, the following rules are available:
If you change the status of an application to Inactive in the Exclusions for application window, Kaspersky Free does not treat the application as a trusted application. This way, you can temporarily exclude an application from the trusted list without actually deleting it from the list. |
Trusted system certificate store |
If one of the trusted system certificate stores is selected, Kaspersky Free excludes applications signed with a trusted digital signature from scans. Kaspersky Free automatically assigns such applications to the Trusted group. If Do not use is selected, Kaspersky Free scans applications regardless of whether or not they have a digital signature. Kaspersky Free places an application in a trust group depending on the level of danger that this application may pose to the computer. |
Network settings
Settings |
Description |
|---|---|
Limit traffic on metered connections |
If this check box is selected, the application limits its own network traffic when the Internet connection is limited. Kaspersky Free identifies a high-speed mobile Internet connection as a limited connection and identifies a Wi-Fi connection as an unlimited connection. Cost-Aware Networking works on computers running Windows 8 or higher. |
Inject script into web traffic to interact with web pages |
If the check box is selected, Kaspersky Free injects a web page interaction script into web traffic. This script ensures the operation of such components as URL Advisor. |
Support DNS over HTTPS (DoH) |
If the check box is selected, the application correctly processes DNS data transmitted over HTTPS. We do not recommend clearing this check box. |
Manage DoH servers |
The link opens a window where you can manually add a DoH server through which DNS data will be transferred in a browser. Here you can read about DNS over HTTPS (DoH) and how to add a DoH server. |
Monitored ports |
Monitor all network ports. In this port monitoring mode, Mail Anti-Virus and Safe Browsing monitor all open ports of your computer. Monitor selected network ports only. In this port monitoring mode, Mail Anti-Virus and Safe Browsing monitor the selected ports of your computer. You can specify the monitored network ports in the Network ports window, which can be opened by clicking the Select link. You can also specify the particular applications where monitoring of all the network ports used by these applications should be enabled:
|
Network ports |
A list of ports that are normally used for transferring email and web traffic is included in Kaspersky Free distribution kit. By default, Kaspersky Free monitors traffic passing through all ports from this list. You can add ports to the list or delete them from the list. If the Active value is set in the port line in the Status column, Kaspersky Free monitors the traffic passing through this port. If the Inactive value is set in the port line in the Status column, Kaspersky Free excludes this port from scans, but does not remove it from the list of ports. You can change the status and other port settings in the window by clicking the Edit button. |
Encrypted connections scan |
You can select one of the following modes for scanning encrypted connections over SSL:
|
When encrypted connections scan errors occur |
In the drop-down list, you can select the action that the application will perform if a secure connections scan error occurs on a website.
|
Domains with scan errors |
List of domains that could not be scanned due to errors when connecting to them. The addresses of the domains were checked against the database of malicious objects. |
Trusted addresses |
Click this link to open the Trusted addresses window, which contains a list of websites that you added as an exclusion for the Safe Browsing and URL Advisor components. |
Trusted applications |
List of applications whose activity is not monitored by Kaspersky Free during its operation. You can select the types of application activity that Kaspersky Free will not monitor (for example, do not scan network traffic). Kaspersky Free supports environment variables, and the |
Block SSL 2.0 connections (recommended) |
If the check box is selected, the application blocks network connections established over the SSL 2.0 protocol. If the check box is cleared, the application does not block network connections established over the SSL 2.0 protocol and does not monitor network traffic transmitted over these connections. |
Decrypt an encrypted connection with the website that uses EV certificate |
EV certificates (Extended Validation Certificates) confirm the authenticity of websites and enhance the security of the connection. Browsers use a lock icon in their address bar to indicate that a website has an EV certificate. Browsers may also fully or partially color the address bar in green. If the check box is selected, the application decrypts and monitors encrypted connections with websites that use an EV certificate. If the check box is cleared, the application does not have access to the contents of HTTPS traffic. For this reason, the application monitors HTTPS traffic only based on the website address, for example, If you are opening a website with an EV certificate for the first time, the encrypted connection will be decrypted regardless of whether or not the check box is selected. |
Proxy server settings |
Settings of the proxy server used for Internet access of users of client computers. Kaspersky Free uses these settings for certain protection components, including for updating databases and application modules. For automatic configuration of a proxy server, Kaspersky Free uses the WPAD protocol (Web Proxy Auto-Discovery Protocol). If the IP address of the proxy server cannot be determined by using this protocol, the application uses the proxy server address that is specified in the Microsoft Internet Explorer browser settings. |
Use the selected certificate store to scan encrypted connections in Mozilla applications |
If this check box is selected, the application scans encrypted traffic in the Mozilla Firefox browser and Thunderbird mail client. Access to some websites via the HTTPS protocol may be blocked. To scan traffic in Mozilla Firefox and Thunderbird, you must enable Encrypted Connections Scan. If Encrypted Connections Scan is disabled, the application does not scan encrypted traffic in Mozilla Firefox and Thunderbird. The application uses Kaspersky root certificate to decrypt and analyze encrypted traffic. You can select the certificate store that will contain the Kaspersky root certificate.
|
Managing application settings
Settings |
Description |
|---|---|
|
Import |
Extract application settings from a file in CFG format and apply them. |
|
Export |
Save the current application settings to a file in CFG format. |
|
Restore |
You can restore the application settings recommended by Kaspersky experts at any time. When the settings are restored, the Optimal security level is set for all protection components. |
Secure Data Input settings
Settings |
Description |
|---|---|
Use hardware virtualization if available |
If the check box is selected, hardware virtualization (hypervisor) is used for the operation of Protected Browser. The application uses hypervisor technology for additional protection against complex malware that could intercept your personal data by using the clipboard or phishing. This check box is displayed when the application is installed on a 64-bit version of Windows 8, Windows 8.1 and Windows 10. For more details about hardware virtualization and how it works, click the link. |
Protection using hardware virtualization
|
Secure Keyboard Input helps you prevent cybercriminals from intercepting the data that you enter from the keyboard when visiting websites (for more details, please refer to the About Secure Keyboard Input section). Select the check boxes for categories of websites on which you want to protect data that is entered via the keyboard. Click the Manage exclusions link to create lists of websites on which you want to enable or disable Secure Keyboard Input irrespective of the selected website categories. You can use masks when adding exclusions. |
On-Screen Keyboard |
Many programs classified as spyware can take screenshots, which then are automatically transmitted to an intruder for further analysis to steal the user's personal data. On-Screen Keyboard protects entered personal data from attempts to intercept it by means of screenshots. (For more details, please refer to About On-Screen Keyboard). To make sure that On-Screen Keyboard is enabled, you must restart your computer after installing Kaspersky Free. You can choose how you will be able to open On-Screen Keyboard:
Click the Manage exclusions link in the Exclusions for On-Screen Keyboard window to create lists of websites on which you want to enable or disable display of the On-Screen Keyboard quick launch icon irrespective of the selected website categories. You can use masks when adding exclusions. |
Show hints for creating strong passwords |
If the check box is selected, Kaspersky Free checks the strength of a password that you are entering in the browser for the first time, and notifies you about it. |
Protection against using the same passwords
|
When you enter a password on a website where password security is especially important (such as on a social network), Kaspersky Free prompts you to enable protection against the use of the same passwords. If the Warn about using the same passwords on websites check box is selected, protection against using the same passwords is enabled. You can select the categories of websites that should be protected from using the same passwords. These categories include banks and payment system websites, social networking websites, and mail service websites. You can click the Delete saved data link to delete all previously saved passwords. |
|
|
Support window
The Kaspersky Technical Support section contains information required for contacting Kaspersky Technical Support: version number of Kaspersky Free, release date and time of the databases and application modules, operating system version, and key.
Answers to frequently asked questions
Application configuration tips
Page top
About phishing
Phishing is a type of Internet fraud involving the theft of personal data; phishing is propagated via email and other channels.
Emails can be fake notifications from banks, ISPs, online stores, electronic payment systems, or other entities. The emails attempt to trick the recipient into visiting the scammers' website under false pretenses, such as an invitation to update login information or to find out more about a product or service.
Unsuspecting recipients of a phishing email may follow the link to find themselves on a phishing website that looks exactly like the company's website it purports to be.
Internet users can get to a phishing site in other ways, for example, by clicking on a link in a search engine.
Scammers can generally pursue a range of different goals. One of them is to trick users into disclosing their confidential data, such as various credentials, bank account numbers and banking card details. Users would enter this information into a web form on the fraudulent website giving the scammers access to their money. Infecting computers with viruses and malware is another trap a user might step into after clicking on a phishing link.
Recognizing fraudulent emails and websites
Fraudulent (phishing) emails and websites may look unsuspicious at first glance. Inclusion of company logos that look like the authentic ones or actual contact phone numbers may lull users into a false sense of security. The email may also contain links to the company's actual website, except for the main phishing link that would take the user to the criminals’ website.
The following telltale signs of phishing may alert the user:
- Though phishing website domains may look like actual legitimate companies' web domains, on closer inspection the user may notice extra words in the domain name (for example, a company's official domain www.example.com could be changed to www.login-example.com), or dots and dashes replacing slashes (www.example.com/personal/login could be changed to www.example.com.personal.login or www.example.com-personal.login). Please note that the email body may contain the company's actual domain address, but when the user clicks on the link, the browser's address bar will show a different domain.
- The email is using an impersonal form of address, such as "Dear user," or "Hello".
- Graphics in the email or on he website look unprofessional, the text contains typos or bad grammar.
- The email recipient is being asked to immediately verify their confidential data by following a link, or sometimes to enter their data in a form in the email body. The email may explain such urgency with alleged account suspension or hacking, or a threat of losing one's data.
Phishing check
Kaspersky Free checks email and website contents for phishing links. Links are checked against a database of phishing web addresses, which is regularly updated.
For additional protection, Kaspersky uses heuristic analysis and sends queries to the Kaspersky Security Network (KSN) cloud services during the check. Kaspersky Security Network contains the most up-to-date information about recently emerged threats, including phishing websites which have not yet been added to Kaspersky databases. The data received by the KSN is analyzed by Virus Lab employees in real time.
If you have clicked through to a phishing website, you can report it to Kaspersky Security Network using the Kaspersky Protection extension.
Page top
Profile
Connecting a device to My Kaspersky
You need a My Kaspersky account to manage subscription, activate the subscription on different devices and remotely manage the protection of such devices. Your My Kaspersky account lets you view the status of all devices connected to the account, which have the application installed; you can also manage subscriptions and store activation codes in a secure location.
More about My Kaspersky account
Subscription details
Here you can find general information about the subscription used by your application.
To reveal other actions that you can perform with your subscription, click  . Depending on your subscription and its status, the list of available actions may be different.
. Depending on your subscription and its status, the list of available actions may be different.
Protect more devices
Here you can see how many devices you can protect with your subscription, how many devices you are currently protecting; also you can start protecting new devices. If you have connected a device to your My Kaspersky account, the information is refreshed when you run the application.
The number of devices on which you may use your subscription depends on the subscription plan and the terms and conditions stipulated by the End User License Agreement.
Clicking the  button lets you choose one of the following actions:
button lets you choose one of the following actions:
Depending on your subscription, only the general information about the total number of devices that you can protect may be displayed.
Page top
Solutions for you
On this page, we will offer Kaspersky solutions and solutions provided by our partners that you might find interesting. Here you will be able to buy a solution that is tailored to your needs, browse previously bought applications and services, keep an eye on your subscription status, proceed to install an application, or read an instruction manual.
Clicking Buy takes you to the online store where you can learn more about your chosen solution and check out your purchase. You will receive an email with information about your purchase and activation instructions.
You can manage the subscriptions that you bought in your My Kaspersky account.
Page top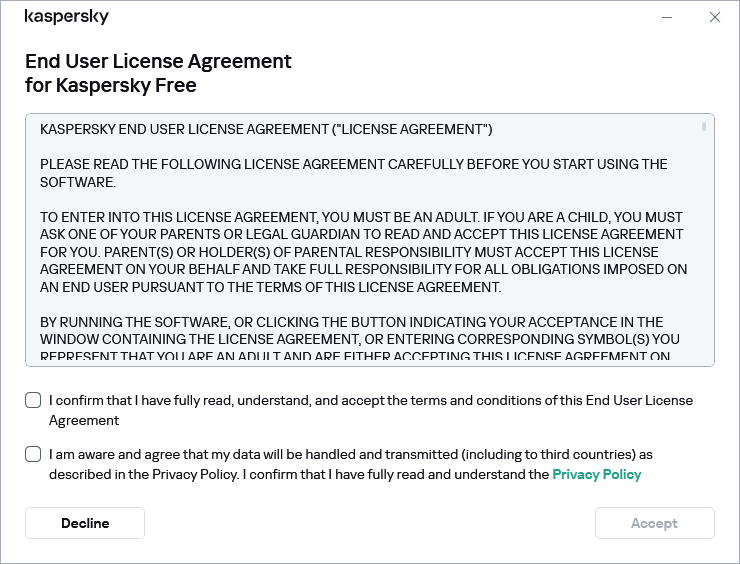
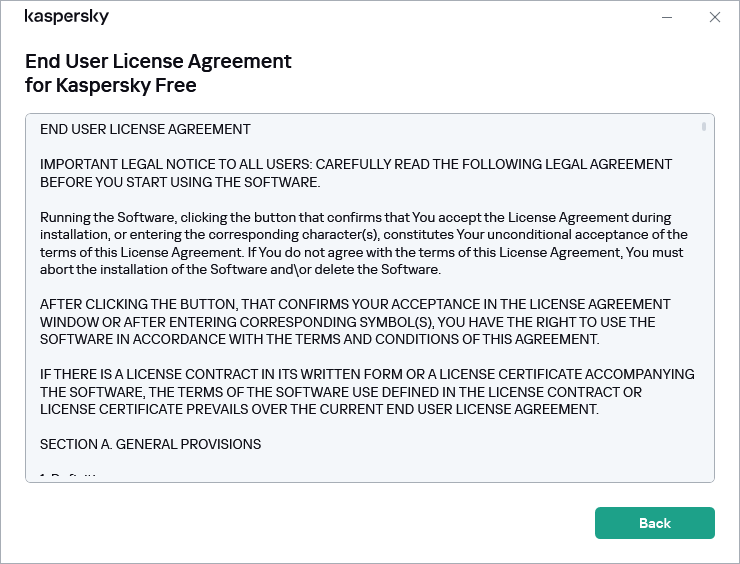
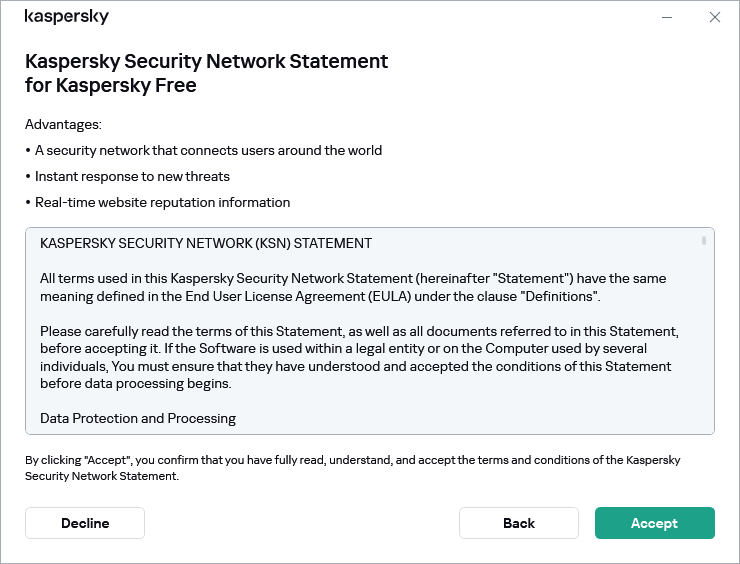
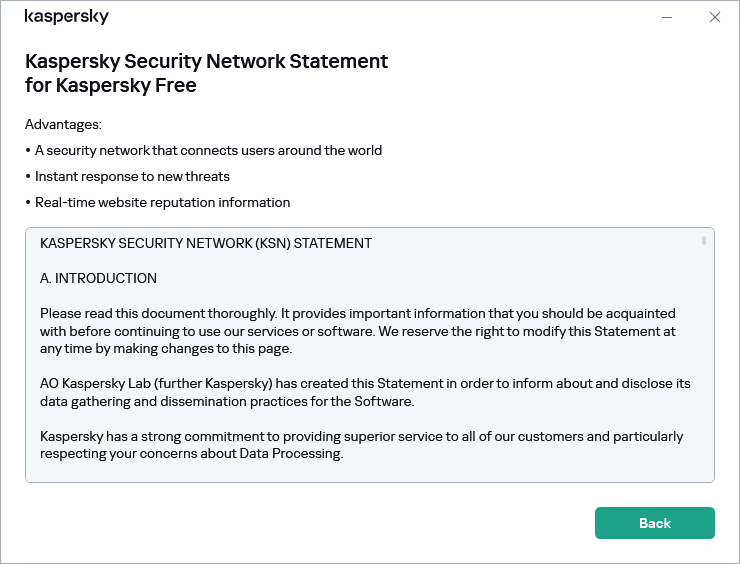
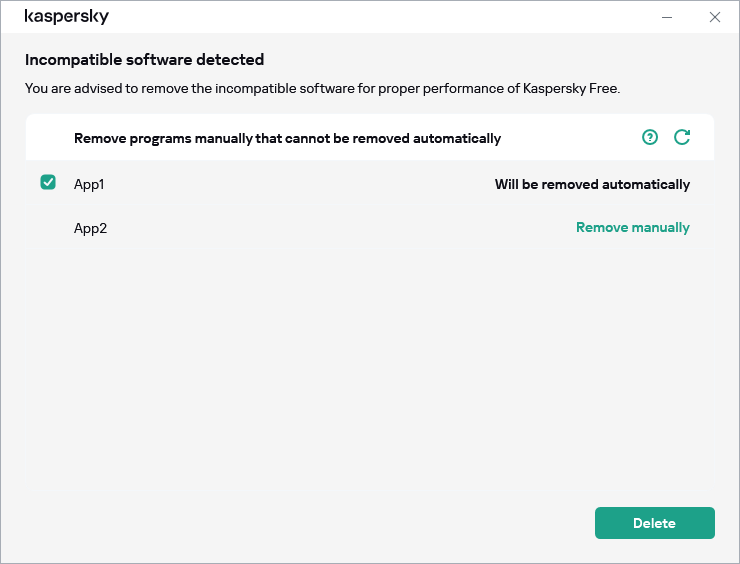

 button opens a menu from which you can select an additional action:
button opens a menu from which you can select an additional action:


