Contents
- Management of mobile device settings
- Configuring connection to a Wi-Fi network
- Configuring email
- Configuring protection levels in Kaspersky Security Center
- Managing app configurations
- Managing app permissions
- Creating a report on installed mobile apps
- Installing root certificates on Android devices
- Configuring notifications for Kaspersky Endpoint Security for Android
- Selecting the download manager for Android devices
- Connecting iOS MDM devices to AirPlay
- Connecting iOS MDM devices to AirPrint
- Configuring the Access Point Name (APN)
- Corporate container
- Adding an LDAP account
- Adding a contacts account
- Adding a calendar account
- Configuring a calendar subscription
- Configuring SSO
- Managing Web Clips
- Setting a wallpaper
- Adding fonts
Management of mobile device settings
This section contains information about how to remotely manage the settings of mobile devices in Kaspersky Security Center Web Console.
Configuring connection to a Wi-Fi network
This section provides instructions on how to configure automatic connection to a corporate Wi-Fi network on Android and iOS MDM devices.
Connecting Android devices to a Wi-Fi network
For an Android device to automatically connect to an available Wi-Fi network and protect data during the connection, you must configure the connection settings.
To connect a mobile device to a Wi-Fi network:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Device configuration section.
- On the Wi-Fi card, click Settings.
The Wi-Fi window opens.
- Enable the settings using the Wi-Fi toggle switch.
- Click Add.
The Add Wi-Fi network window opens.
- In the Service set identifier (SSID) field, enter the name of the Wi-Fi network that includes the access point (SSID).
- Select the Connect automatically check box if you want Android devices to automatically connect to the Wi-Fi network.
- Select the Hidden network check box if you want the Wi-Fi network to be hidden in the list of available networks on the device.
In this case, to connect to the network the user needs to manually enter the service set identifier (SSID) specified in the settings of the Wi-Fi router on the mobile device.
- In the Protection section, select the type of Wi-Fi network security (open network or secure network protected with the WEP, WPA2 PSK, or 802.1.x EAP protocol).
The 802.1.x EAP security protocol is supported only in Kaspersky Endpoint Security for Android 10.48.1.1 or later. The WEP protocol is supported only on Android 9 or earlier.
- If you selected the 802.1.x EAP security protocol, specify the following network protection settings:
- In the Password field, set a network access password if you selected a secure network at step 9.
- On the Additional tab, select the Use a proxy server check box if you want to use a proxy server to connect to the Wi-Fi network.
- If you selected Use a proxy server, in the Proxy server address and Proxy server port fields, enter the IP address or DNS name of the proxy server and port number, if necessary.
On devices running Android 8 or later, proxy server settings for Wi-Fi cannot be redefined with a policy. However, you can manually configure the proxy server settings for a Wi-Fi network on the mobile device.
If you are not using a proxy server to connect to a Wi-Fi network, there are no limitations on using policies to manage a Wi-Fi network connection.
- In the Do not use proxy server for the specified addresses field, add web addresses that can be accessed without the use of the proxy server.
For example, you can enter the address
example.com. In this case, the proxy server will not be used for the addressespictures.example.com,example.com/movies, etc. The protocol (for example,http://) can be omitted.On devices running Android 8 or later, excluding web addresses from the proxy server does not work.
- Click Add.
The added Wi-Fi network is displayed in the list of Wi-Fi networks.
This list contains the names of suggested wireless networks.
On personal devices running Android 10 or later, the operating system prompts the user to connect to such networks. Suggested networks don't appear in the saved networks list on these devices.
On corporate devices and personal devices running Android 9 or earlier, after synchronizing the device with the Administration Server, the device user can select a suggested wireless network in the saved networks list and connect to it without having to specify any network settings.
You can modify or delete Wi-Fi networks in the list of networks using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
On devices running Android 10 or later, if a user refuses to connect to the suggested Wi-Fi network, the app's permission to change Wi-Fi state is revoked. The user must grant this permission manually.
Page topConnecting iOS MDM devices to a Wi-Fi network
For an iOS MDM device to automatically connect to an available Wi-Fi network and protect data during the connection, you must configure the connection settings.
To configure the connection of an iOS MDM device to a Wi-Fi network:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Wi-Fi card, click Settings.
The Wi-Fi window opens.
- Enable the settings using the Wi-Fi toggle switch.
- Click Add.
The Add Wi-Fi network window opens.
- In the Service set identifier (SSID) field, enter the name of the Wi-Fi network that includes the access point (SSID).
- If you want iOS MDM devices to automatically connect to the Wi-Fi network, select the Connect automatically check box.
If you disable automatic connection to an existing Wi-Fi network in the policy settings, you will not be able to enable automatic connection to this network again. This is due to an issue known to Apple.
- If you don't want iOS MDM devices to connect to Wi-Fi networks requiring preliminary authentication (captive networks), select the Disable captive network detection check box.
To use a captive network, you must subscribe, accept an agreement, or make a payment. Captive networks may be deployed in cafes and hotels, for example.
- If you want the Wi-Fi network to be hidden in the list of available networks on the iOS MDM device, select the Hidden network check box.
In this case, to connect to the network the user needs to manually enter the service set identifier (SSID) specified in the settings of the Wi-Fi router on the mobile device.
- If you want iOS MDM devices to use static MAC addresses when they connect to the Wi-Fi network, select the Disable MAC address randomization check box.
- In the Protection section, select the type of Wi-Fi network security (open network or secure network protected with the WEP, WPA, WPA2, or WPA3 protocol).
On devices running iOS 15 or earlier, selecting WPA, WPA2, or WPA3 is identical and lets you connect to any network protected using WPA.
- Open network. User authentication is not required.
- WEP. The network is protected using Wireless Encryption Protocol (WEP).
WEP protection is available on devices running iOS 5 or later.
- WPA. The network is protected using the WPA (Wi-Fi Protected Access) or WPA2 protocol.
- WPA2. The network is protected using the WPA2 or WPA3 protocol.
- WPA3. The network is protected using the WPA3 protocol.
- Personal network (any). The network is protected using the WEP, WPA, WPA2, or WPA3 encryption protocol depending on the type of Wi-Fi router. An encryption key unique to each user is used for authentication.
- WEP (corporate network). The network is protected using the WEP protocol with the use of a dynamic key.
- WPA (corporate network). The network is protected using the WPA or WPA2 encryption protocol with the use of the 802.1X protocol.
- WPA2 (corporate network). The network is protected using the WPA2 or WPA3 encryption protocol with the use of one key shared by all users (802.1X).
- WPA3 (corporate network). The network is protected using the WPA3 encryption protocol with the use of one key shared by all users (802.1X).
- Corporate network (any). The network is protected using the WEP, WPA, WPA2, or WPA3 protocol depending on the type of Wi-Fi router. Authentication is performed using a single encryption key shared by all users.
If you have selected any of the corporate network options, in the EAP protocol section you can select the types of EAP protocols (Extensible Authentication Protocol) for user identification on the Wi-Fi network.
In the Trusted certificates section, you can also create a list of trusted certificates for authentication of the iOS MDM device user on trusted servers.
- In the Authentication section, configure the settings of the account for user authentication upon connection of the iOS MDM device to the Wi-Fi network:
- In the User name field, enter the account name for user authentication upon connection to the Wi-Fi network.
- In the User ID field, enter the user ID displayed during data transmission upon authentication instead of the user's real name.
The user ID is designed to make the authentication process more secure, since the user name is not displayed openly, but rather transmitted via an encrypted TLS tunnel.
- In the Password field, enter the password of the account for authentication on the Wi-Fi network.
- If you want the user to enter the password manually upon every connection to the Wi-Fi network, select the Prompt for password at each connection check box.
- In the Authentication certificate drop-down list, select a certificate for user authentication on the Wi-Fi network.
- In the Minimum TLS version drop-down list, select the minimum allowed TLS version.
- In the Maximum TLS version drop-down list, select the maximum allowed TLS version.
- If necessary, on the Additional tab, configure the settings for connecting to the Wi-Fi network via a proxy server:
- Select the Use a proxy server check box.
- Configure a connection to a proxy server:
- If you want to configure the connection automatically:
- Select Automatic.
- In the PAC file URL field, specify the URL of the proxy PAC file.
- To allow the user to connect the mobile device to a wireless network without using a proxy server when the PAC file cannot be accessed, select the Allow direct connection if PAC file cannot be accessed check box.
- If you want to configure the connection manually:
- Select Manual.
- In the Proxy server address and Proxy server port fields, enter the IP address or DNS name of the proxy server and port number.
- In the User name field, select a macro that will be used as a user name for the connection to the proxy server.
- In the Password field, specify the password for the connection to the proxy server.
- If you want to configure the connection automatically:
- Click Add.
The new Wi-Fi network is displayed in the list.
- Click OK.
- Click Save to save the changes you have made.
As a result, a Wi-Fi network connection will be configured on the user's iOS MDM device once the policy is applied. The user's mobile device will automatically connect to available Wi-Fi networks. Data security during a Wi-Fi network connection is ensured by the selected authentication method.
Page topConfiguring email
This section contains information on configuring mailboxes on mobile devices.
Configuring a mailbox on iOS MDM devices
These settings apply to supervised devices and devices operating in basic control mode.
To enable an iOS MDM device user to work with email, add the user's email account to the list of accounts on the iOS MDM device.
By default, the email account is added with the following settings:
- Email protocol – IMAP.
- The user can move email messages between the user's accounts and synchronize account addresses.
- The user can use any email client (other than Mail) to use email.
- The SSL connection is not used during transmission of messages.
You can edit the specified settings when adding an account.
To add an email account of the iOS MDM device user:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Email card, click Settings.
The Email window opens.
- Enable the settings using the Email toggle switch.
- Click Add.
The Add email account window opens.
- Specify the email account settings:
- On the General tab, configure the following settings:
- In the User name field, specify the name of the iOS MDM device user. You can either enter a value or select a macro by clicking the
 button.
button. - In the Email address field, specify the email address of the iOS MDM device user. You can either enter a value or select a macro by clicking the
 button.
button. - In the Account description field, enter a description of the user's email account.
- In the Email protocol field, select one of the following protocols:
- POP
- IMAP
- If you selected IMAP, specify the IMAP path prefix in the IMAP path prefix field.
The IMAP path prefix must be entered using uppercase letters (for example: GMAIL for Google Mail).
- In the Incoming mail server settings and Outgoing mail server settings sections, configure the server connection settings:
- In the Server address field, specify names of hosts or IP addresses of incoming and outgoing mail servers.
- In the Server port fields, specify the port numbers of incoming and outgoing mail servers.
To configure optional settings for the incoming and outgoing mail servers, click More settings and do the following:
- In the User name field, specify the name of the user's account for authorization on the incoming and outgoing mail servers. You can either enter a value or select a macro by clicking the
 button.
button. - In the Authentication type field, select the type of authentication of the user's email account on the incoming and outgoing mail servers.
- In the Password field, specify the account password for authenticating on incoming and outgoing mail servers protected using the selected authentication method.
- If you want to use the SSL (Secure Sockets Layer) data transport protocol, select the Use SSL connection check box.
- If you want to use the same password for user authentication on the incoming and outgoing mail servers, select the Use the same password for incoming and outgoing mail servers check box.
- In the User name field, specify the name of the iOS MDM device user. You can either enter a value or select a macro by clicking the
- On the Advanced tab, configure the additional settings of the email account:
- In the Restrictions section, select or clear the following check boxes, if necessary:
- In the Signature and Encryption sections, configure the settings for signing and encrypting outgoing mail using the S/MIME protocol in the Mail app.
S/MIME is a protocol for transmitting digitally signed encrypted messages. S/MIME provides cryptographic security capabilities such as authentication, message integrity control, and non-repudiation of origin (using digital signatures). The protocol also helps improve the confidentiality and security of data in email messages by using encryption.
- If necessary, in the Per App VPN section, configure Per App VPN.
- On the General tab, configure the following settings:
- Click Save.
The new email account appears in the list.
You can modify or delete email accounts in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, email accounts from the list are added on the user's mobile device.
We recommend closing and opening the Settings app on the iOS MDM device after you configure a mailbox.
Page topConfiguring an Exchange mailbox on iOS MDM devices
These settings apply to supervised devices and devices operating in basic control mode.
To allow an iOS MDM device user to use corporate email, calendar, contacts, notes, and tasks, add the user's Exchange ActiveSync account on the Microsoft Exchange server.
By default, an account with the following settings is added on the Microsoft Exchange server:
- Email is synchronized once per week.
- The user can move messages between the user's accounts and synchronize account addresses.
- The user can use any email clients (other than Mail) to use email.
- The SSL connection is not used during transmission of messages.
You can edit the specified settings when adding the Exchange ActiveSync account.
To add an Exchange ActiveSync account of an iOS MDM device user:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Exchange ActiveSync card, click Settings.
The Exchange ActiveSync window opens.
- Enable the settings using the Exchange ActiveSync toggle switch.
- Click Add.
The Add Exchange ActiveSync account window opens.
- Specify the Exchange ActiveSync settings:
- On the General tab, specify the user's data:
- In the Account name field, enter the account name for authorization on the Microsoft Exchange server. You can either enter a value or select a macro by clicking the
 button.
button. - In the Exchange ActiveSync server address field, enter the DNS name or IP address of the Microsoft Exchange server.
- Settings in the User credentials section:
- In the User domain field, enter the name of the iOS MDM device user's domain. You can either enter a value or select a macro by clicking the
 button.
button. - In the User name field, enter the name of the iOS MDM device user. You can either enter a value or select a macro by clicking the
 button.
button.If you leave this field blank, Kaspersky Mobile Devices Protection and Management prompts the user to enter the user name when applying the policy on the iOS MDM device.
- In the Email address field, specify the email address of the iOS MDM device user. You can either enter a value or select a macro by clicking the
 button.
button.
- In the User domain field, enter the name of the iOS MDM device user's domain. You can either enter a value or select a macro by clicking the
- Settings in the Authentication section:
- In the Password field, enter the password of the Exchange ActiveSync account for authorization on the Microsoft Exchange server.
- In the Authentication certificate drop-down list, select the certificate used for authenticating the iOS MDM device user on the Microsoft Exchange server. You can add certificates in the Certificate management settings of the policy or in the Certificates section of Web Console.
- In the Account name field, enter the account name for authorization on the Microsoft Exchange server. You can either enter a value or select a macro by clicking the
- On the Additional tab, configure the additional settings of the Exchange ActiveSync account:
- In the Email synchronization section, in the Synchronization period drop-down list, select the time interval for which email is automatically synchronized and stored on the iOS MDM device. The longer the email synchronization period, the more free space required in the memory of the mobile device. Messages that have not been synchronized are not available without an internet connection. The default value is 1 week.
- In the Restrictions section, select or clear the following check boxes, if necessary:
- In the Signature and encryption section, configure the settings for signing and encrypting outgoing mail using the S/MIME protocol in the Mail app. S/MIME is a protocol for transmitting digitally signed encrypted messages. S/MIME provides cryptographic security capabilities such as authentication, message integrity control, and non-repudiation of origin (using digital signatures). The protocol also uses encryption to help improve the level of confidentiality and security of data in email messages.
- On the General tab, specify the user's data:
- Click Add.
The new Exchange ActiveSync account appears in the list.
You can modify or delete Exchange ActiveSync accounts in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, Exchange ActiveSync accounts from the compiled list are added on the user's mobile device.
Page topConfiguring an Exchange mailbox on Android devices
To work with corporate mail, contacts, and the calendar on the mobile device, you can configure the Exchange mailbox settings for the standard Samsung Email app.
An Exchange mailbox can be configured only for Samsung devices running Android 9 or earlier.
To configure an Exchange mailbox on a user's mobile device:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Samsung Knox settings section.
- On the Exchange ActiveSync card, click Settings.
The Exchange ActiveSync window opens.
- Enable the settings using the Exchange ActiveSync toggle switch.
- In the Server address field, enter the IP address or DNS name of the server hosting the mail server.
- In the Domain name field, enter the name of the mobile device user's domain on the corporate network.
- In the Synchronization interval drop-down list, select the interval for mobile device synchronization with the Microsoft Exchange server.
- To use the SSL (Secure Sockets Layer) data transport protocol, select the Use SSL connection check box. The SSL protocol uses encryption and certificate-based authentication for secure data transfer. This check box is selected by default.
- To use digital certificates to protect data transfer between the user's mobile device and the Microsoft Exchange server, select the Verify server certificate check box. The server certificate is verified to have been issued from the trusted root certificate. This check box is selected by default.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
Page topConfiguring protection levels in Kaspersky Security Center
These settings apply to Android devices.
To configure rules for assigning protection levels in Kaspersky Security Center:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the KES for Android settings section.
- On the Severity settings for device protection level card, click Settings.
The Severity settings for device protection level window opens.
- Enable the settings using the Severity settings for device protection level toggle switch.
- Select the OK, Warning, or Critical protection level for each of the following conditions:
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
For more information about default values, reasons, and conditions for assigning protection levels, please refer to the Mobile device protection levels section.
Page topManaging app configurations
This section provides instructions on how to manage settings and edit configurations of the apps installed on your users' devices.
Managing Google Chrome settings
These settings apply to corporate devices and devices with a corporate container.
To configure Google Chrome settings:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the App configuration section.
- On the Google Chrome settings card, click Settings.
The Google Chrome settings window opens.
- Enable the settings using the Google Chrome settings toggle switch.
The toggle switch in this card does not enable or disable the corresponding functionality on devices. Enabling the toggle switch lets you configure custom settings. Disabling the toggle switch lets you use default settings.
- Configure the required settings.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
Manage content settings
On the Content tab, you can manage the following settings:
- In the Cookies section:
- In the JavaScript section:
- In the Pop-ups section:
- In the Location tracking section:
Manage proxy settings
On the Proxy tab, you can manage the following settings:
Manage search settings
On the Search tab, you can manage the following settings:
- In the Touch to Search section:
- In the Search provider section:
Manage security settings
On the Security tab, you can manage the following settings:
- In the Google Safe Browsing and SafeSearch section:
- In the Blocked websites section:
- In the Passwords and autofill section:
- In the Network section:
Manage additional settings
On the Additional settings tab, you can manage the following settings:
- In the Bookmarks section:
- In the History and Incognito mode section:
- In the Other section:
Managing Exchange ActiveSync for Gmail
These settings apply to corporate devices and devices with a corporate container.
The Exchange ActiveSync settings let you manage Exchange ActiveSync for the Gmail app.
To configure Exchange ActiveSync settings:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the App configuration section.
- On the Exchange ActiveSync card, click Settings.
The Exchange ActiveSync window opens.
- Enable the settings using the Exchange ActiveSync toggle switch.
- Specify the Exchange ActiveSync settings:
- On the General tab, specify the following settings:
- Exchange ActiveSync server address
- Settings in the User credentials section:
- Settings in the Authentication section:
- On the Additional tab, specify the following settings:
- Settings in the Email synchronization section:
- Settings in the Restrictions section:
- Settings in the Signature section:
- On the General tab, specify the following settings:
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
Page topConfiguring other apps
These settings apply to corporate devices and devices with a corporate container.
The Configure other apps settings let you configure installed apps that support configurations.
To add app configurations:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the App configuration section.
- On the Configure other apps card, click Settings.
The Configure other apps window opens.
- Enable the settings using the Configure other apps toggle switch.
- Click Add.
The Add app configuration window opens.
- In the Method for adding configuration drop-down list, select how to add configuration:
- In the Configuration data section, specify the following settings:
An example of configured basic parameters for the Microsoft Outlook app.
- Click the Add setting button to add a block of the app configuration settings. You can add several blocks of settings.
Specify the following parameters for each block of settings of the configuration:
For some types of settings, additional parameters can be configured. For example:
- You can add macros for a String.
- You can add a field to a Bundle.
- You can add a Bundle to a BundleArray.
It is also possible to edit a setting to be added to a BundleArray by clicking the Configure Bundle button and configuring the setting's parameters.
For information about configuring rules, please refer to the official documentation for the app to be configured.
- Click Add.
The configuration appears in the list of app configurations.
You can modify or delete app configurations in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
The app configuration is applied.
Some apps may not notify Kaspersky Endpoint Security for Android that the app configuration has been applied.
When configuring some apps, certificates installed on devices via Kaspersky Security Center can be used. In this case, you must specify a certificate alias in the app configuration:
VpnCertfor VPN certificates.MailCertfor mail certificates.SCEP_profile_namefor certificates received using SCEP.
Managing app permissions
These settings apply to corporate devices and devices with a corporate container.
App permission management settings let you configure rules for granting runtime permissions to installed apps.
To add app permissions:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the App configuration section.
- On the App permission management card, click Settings.
The App permission management window opens.
- Enable the settings using the App permission management toggle switch.
- Click Add.
The Add app with permission granting rules window opens.
- In the Method for adding configuration section, select how to add a configuration with permission granting rules:
- In the App data section, specify the following settings:
- Click the Add rule button to add and configure a new rule. You can add several permissions.
Select one of the following permissions.
To configure granting rules for app runtime permissions, you need to select one of the following actions for each permission:
You can save only one granting rule for each app permission.
- Click Add.
The configuration appears in the Apps with configured permission granting rules list.
You can modify or delete configurations in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
The configuration with permission granting rules is applied. Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
Permission granting rules configured for specific apps have precedence over the general policy for granting permissions. For example, if you first select the Deny permissions automatically option in the Corporate container on devices section, and then select the Grant permissions automatically option for a specific app in the App permission management section, the permission for this app will be granted automatically.
Page topCreating a report on installed mobile apps
The Report on installed mobile apps lets you get detailed information about the apps installed on users' Android devices.
To allow the report to display information, the Send data on installed apps check box must be selected in App Control settings and the An app was installed or removed (list of installed apps) informational event type must be stored in the Administration Server database.
To enable sending data:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Security controls section.
- On the App Control card, click Settings.
The App Control window opens.
- In the Report on installed apps section, select the Send data on installed apps check box.
- If you want to receive data about system apps, select the Send data on built-in apps check box.
- If you want to receive data about service apps, which do not have an interface and cannot be opened by the user, select the Send data on service apps check box.
- Click OK.
- Click Save to save the changes you have made.
- Click the name of the policy and select Event configuration.
- Go to the Info section.
- Click the An app was installed or removed (list of installed apps) event to open its properties.
- In the event properties window, turn on the Store in the Administration Server database for (days) toggle switch and set the storage period. By default, the storage period is 30 days.
After the storage period expires, the Administration Server deletes outdated information from the database. For more information about events, please refer to the Kaspersky Security Center Help.
- Click OK.
- Click Save to save the changes you have made.
Sending data is enabled.
To configure a report on installed mobile apps:
- In the main window of Kaspersky Security Center Web Console, select Monitoring & reporting → Reports.
- Click the Report on installed mobile apps report template to open its properties.
- In the window that opens, click Edit.
- Edit the report template properties:
- On the General tab, specify the following parameters:
- On the Fields tab, select the fields that will be displayed in the report and the order of these fields, and configure whether the report must be sorted and filtered by each of the fields.
- Click Save to save the changes you have made.
The updated report template appears in the list of report templates.
To create and view a report on installed mobile apps:
- In the main window of Kaspersky Security Center Web Console, select Monitoring & reporting → Reports.
- Click a report with the Report on installed mobile apps type.
A report using the selected template is generated and displayed.
For more information about using reports, managing custom report templates, using report templates to generate new reports, and creating report delivery tasks, please refer to the Kaspersky Security Center Help.
Page topInstalling root certificates on Android devices
A root certificate is a public key certificate issued by a trusted certificate authority (CA). Root certificates are used to verify custom certificates and guarantee their identity.
Kaspersky Security Center Web Console lets you add root certificates to be installed to a trusted certificate store on Android devices.
These certificates are installed on user devices as follows:
- On corporate devices, the certificates are installed automatically.
If you delete a root certificate in the policy settings, it will also be automatically deleted on the device during the next synchronization with the Administration Server.
- On personal devices:
- If a corporate container was not created, the device user is prompted to install each certificate manually in a personal space by following the instructions in the notification.
- If a corporate container was created, the certificates are installed automatically to the container. If the Duplicate installation of root certificates in user's personal space check box is selected in the corporate container settings, the certificates can also be installed in a personal space. The device user is prompted to do this manually by following the instructions in the notification.
If you delete a root certificate in the policy settings, it will also be automatically deleted on the device during the next synchronization with the Administration Server.
For instructions on how to install certificates in a personal space, please refer to Installing root certificates on the device.
To add a root certificate:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Device configuration section.
- On the Root certificates card, click Settings.
The Root certificates window opens.
- Enable the settings using the Root certificates toggle switch.
- Click Add.
The file explorer opens.
- Select a certificate file (a CER, PEM, KEY, or CRT file) and click Open.
The certificate file must be no larger than 10 MB.
The certificate will appear in the list of root certificates.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are configured after the next device synchronization with Kaspersky Security Center.
Page topConfiguring notifications for Kaspersky Endpoint Security for Android
If you don't want the mobile device user to be distracted by Kaspersky Endpoint Security for Android notifications, you can disable certain notifications.
Kaspersky Endpoint Security for Android uses the following tools to display the status of device protection:
- Protection status notification. This notification is pinned to the notification bar. A protection status notification cannot be removed. The notification displays the device protection status (for example,
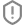 ) and the number of issues, if any. You can tap the device protection status and see security issues in the app.
) and the number of issues, if any. You can tap the device protection status and see security issues in the app. - App notifications. These notifications inform the device user about the application (for example, the detection of a threat).
- Pop-up messages. Pop-up messages require action from the device user (for example, action to take when a threat is detected).
All Kaspersky Endpoint Security for Android notifications are enabled by default.
On Android 13, the device user must grant the permission to send notifications during or after the Initial Configuration Wizard.
The user can disable all notifications from Kaspersky Endpoint Security for Android in the settings on the notification bar. If notifications are disabled, the user is not monitoring operation of the app and may ignore important information (for example, information about failures during device synchronization with Kaspersky Security Center). In this case, to find out the app operating status, the user must open Kaspersky Endpoint Security for Android.
To configure displaying notifications about the operation of Kaspersky Endpoint Security for Android:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the KES for Android settings section.
- On the Notifications card, click Settings.
The Notifications window opens.
- Enable the settings using the Notifications toggle switch.
- If you want to hide all notifications and pop-up messages, in the Background notifications section, select the Disable notifications when Kaspersky Endpoint Security is in the background check box.
Kaspersky Endpoint Security for Android will display only the protection status notification. The notification displays the device protection status (for example,
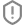 ) and the number of issues.
) and the number of issues.In-app notifications (for example, when the user updates anti-malware databases manually) will still be displayed.
We recommend that you enable notifications and pop-up messages. If you disable notifications and pop-up messages when the app is in the background, the app will not warn users about threats in real time. In this case, mobile device users will not see the device protection status unless they open the app.
- In the Notifications about device security issues section, select the Kaspersky Endpoint Security for Android issues that you want to display on the user's mobile device.
Displaying certain Kaspersky Endpoint Security for Android issues is mandatory. These issues are always displayed on the device (for example, issues about license expiration).
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center. The notifications that you disable will not be displayed on the user's mobile device.
Page topSelecting the download manager for Android devices
If you use a Web Server with a self-signed certificate instead of a certificate signed by a certification authority (CA), the standard Android download manager lets you download files, apps, and Kaspersky Endpoint Security for Android installation packages from your Web Server to devices only via HTTP.
To securely download files from a Web Server with a self-signed certificate to devices, you can use the built-in Kaspersky Endpoint Security for Android download manager that always downloads files via HTTPS.
The built-in Kaspersky Endpoint Security for Android download manager is enabled by default.
To change the download manager used by Kaspersky Endpoint Security for Android:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the KES for Android settings section.
- Do one of the following:
- To use the Kaspersky Endpoint Security for Android download manager, turn on the Built-in download manager toggle switch.
- To use the standard Android download manager, turn off the Built-in download manager toggle switch.
The download manager used on devices is configured.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
Page topConnecting iOS MDM devices to AirPlay
Configure the connection to AirPlay devices to stream music, photos, and videos from an iOS MDM device to AirPlay devices. To be able to use AirPlay, the mobile device and AirPlay devices must be connected to the same wireless network. AirPlay devices include Apple TV devices (second generation or later), AirPort Express devices, speakers, TVs, and radios with AirPlay support.
Automatic connection to AirPlay devices is available for devices operating in basic control mode and for supervised devices.
To configure the connection of an iOS MDM device to AirPlay devices:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the AirPlay card, click Settings.
The AirPlay window opens.
- Enable the settings using the AirPlay toggle switch.
- In the Passwords section, click Add password.
- In the Device field, enter the name of the AirPlay device on the wireless network.
- In the Password field, enter the password to the AirPlay device.
- If you want iOS MDM devices to connect only to specific AirPlay devices, create a list of allowed devices in the Allowed devices section. To do this, click Add device and specify the MAC addresses of AirPlay devices.
Both the Wi-Fi and Ethernet address for each device must be added.
Access to AirPlay devices that are not in the list of allowed devices is blocked. If the list of allowed devices is empty, Kaspersky Mobile Devices Protection and Management allows access to all AirPlay devices.
- Click OK.
- Click Save to save the changes you have made.
As a result, once the policy is applied, the user's mobile device will automatically connect to AirPlay devices to stream media.
Page topConnecting iOS MDM devices to AirPrint
To enable printing documents from an iOS MDM device wirelessly using AirPrint, configure automatic connection to AirPrint printers. The mobile device and printer must be connected to the same wireless network. Shared access for all users must be configured on the AirPrint printer.
To configure the connection of an iOS MDM device to an AirPrint printer:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the AirPrint card, click Settings.
The AirPrint window opens.
- Enable the settings using the AirPrint toggle switch.
- Click Add.
The Add printer window opens.
- In the IP address or FQDN field, enter the IP address or a fully qualified domain name (FQDN) of the AirPrint printer.
- In the Port field, enter the listening port of the AirPrint destination.
- In the Resource path field, enter the path to the AirPrint printer.
The path to the printer corresponds to the rp (resource path) key of the Bonjour protocol. For example:
- printers/Canon_MG5300_series
- ipp/print
- Epson_IPP_Printer
- If you want to protect the connection to the AirPrint printer using the TLS protocol, select the Use TLS check box.
- Click Add.
The newly added AirPrint printer appears in the list.
- Click OK.
- Click Save to save the changes you have made.
As a result, once the policy is applied, the mobile device user can wirelessly print documents on the AirPrint printer.
Page topConfiguring the Access Point Name (APN)
This section provides instructions on how to connect a mobile device to cellular data services on a mobile network.
Configuring APN on Android devices (only Samsung)
APN can be configured only for Samsung devices.
A SIM card must be inserted to be able to use an access point on the user's mobile device. Access point settings are provided by the mobile operator. Incorrect access point settings may result in additional mobile charges.
To configure the Access Point Name (APN) settings on a user's mobile device:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Samsung Knox settings section.
- On the APN settings card, click Settings.
The APN settings window opens.
- Enable the settings using the APN settings toggle switch.
The toggle switch in this card does not enable or disable the corresponding functionality on devices. Enabling the toggle switch lets you configure custom settings. Disabling the toggle switch lets you use default settings.
- Specify the following access point settings for connecting the user to the data service:
- In the APN type drop-down list, select the type of access point (APN) for data transmission on a GPRS/3G/4G mobile network:
- Internet. Connection of the user's mobile device to the internet.
- MMS. Exchange of MMS multimedia messages.
- Internet and MMS. Connection to the internet and exchange of multimedia messages. This is the default value.
- In the APN name field, specify the name of the access point.
- In the MCC field, enter the mobile country code (MCC).
- In the MNC field, enter the mobile network code (MNC).
- In the APN type drop-down list, select the type of access point (APN) for data transmission on a GPRS/3G/4G mobile network:
- If you have selected MMS or Internet and MMS as the type of access point, specify the following additional MMS server settings in the MMS server section:
- In the MMS server name field, specify the full domain name of the mobile carrier's server used for MMS exchange (for example,
mms.mobile.com). - In the MMS proxy server address field, specify the network name or IP address of the proxy server.
- In the MMS proxy server port field, specify the port number of the mobile carrier's server used for MMS exchange.
- In the MMS server name field, specify the full domain name of the mobile carrier's server used for MMS exchange (for example,
- In the Authentication section, specify the authentication settings:
- In the Authentication type drop-down list, select the type of authentication of the mobile device user that will be used on the mobile carrier's server for network access. By default, user authentication is not required. The following types are available:
- None. User authentication is not required to access the mobile network.
- PAP (Password Authentication Protocol). An authentication protocol that uses passwords as plain non-encrypted text.
- CHAP (Challenge Handshake Authentication Protocol). A request-response authentication protocol that uses standard MD5 hashing to encrypt the response.
- Concurrently. Combined use of CHAP and PAP protocols.
- In the User name field, enter the user name for authorization on the mobile network.
- In the Password field, enter the password for user authorization on the mobile network.
- In the Authentication type drop-down list, select the type of authentication of the mobile device user that will be used on the mobile carrier's server for network access. By default, user authentication is not required. The following types are available:
- In the Network section, specify the following network settings:
- In the Network name field, enter the name of the network.
- In the Server address field, specify the network name of the mobile carrier's server through which data transmission services are accessed.
- In the Proxy server section, specify the following proxy server settings:
- Select the Use a proxy server check box to enable the use of a proxy server. This check box is cleared by default.
- In the Proxy server address field, specify the network name or IP address of the mobile carrier's proxy server for network access. This field is available only if the Use a proxy server check box is selected.
- In the Proxy server port field, specify the port number of the mobile carrier's proxy server for network access. This field is available only if the Use a proxy server check box is selected.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center.
Page topConfiguring APN on iOS MDM devices
The Access Point Name (APN) has to be configured in order to enable the mobile network data transmission service on the user's iOS MDM device.
To configure an access point on a user's iOS MDM device:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the APN settings card, click Settings.
The APN settings window opens.
- Enable the settings using the APN settings toggle switch.
The toggle switch in this card does not enable or disable the corresponding functionality on devices. Enabling the toggle switch lets you configure custom settings. Disabling the toggle switch lets you use default settings.
- In the APN type drop-down list, select the type of access point for data transfer on a GPRS/3G/4G mobile network:
- Built-in APN. Configure cellular communication settings for data transfer via a mobile network operator that supports operation with a built-in Apple SIM. For more details about devices with a built-in Apple SIM, visit the Apple Support website.
- APN. Configure cellular communication settings for data transfer via the mobile network operator of the inserted SIM card.
- Built-in APN and APN. Configure cellular communication settings for data transfer via the mobile network operators of the inserted SIM card and the built-in Apple SIM. For more details about devices with a built-in Apple SIM and a SIM card slot, visit the Apple Support website.
- If you selected APN, in the APN section click Add.
The Add APN window opens.
- Configure the following settings:
- In the APN name field, specify the name of the access point.
- In the Authentication type drop-down list, select the type of user authentication on the mobile operator's server for network access (internet and MMS).
- In the User name field, enter the user name for authorization on the mobile network.
- In the Password field, enter the password for user authorization on the mobile network.
- In the Proxy server address field, enter the name of the host or the IP address of the proxy server.
- In the Proxy server port field, enter the number of the proxy server port.
- In the Allowed protocol drop-down list, select the internet protocol.
- In the Allowed protocol for roaming drop-down list, select the internet protocol that will be used during international roaming.
- In the Allowed protocol for domestic roaming drop-down list, select the internet protocol that will be used during domestic roaming.
- If you want devices on IPv6-only networks to be able to access IPv4-only internet services, select the Use the 464XLAT technology check box.
- Click OK.
- If you selected Built-in APN, configure the following settings:
- In the Built-in APN name field, specify the name of the access point.
- In the Authentication type drop-down list, select the type of user authentication on the mobile operator's server for network access (internet and MMS).
- In the User name field, enter the user name for authorization on the mobile network.
- In the Password field, enter the password for user authorization on the mobile network.
- In the Allowed protocol drop-down list, select the internet protocol.
- Click OK.
- Click Save to save the changes you have made.
As a result, the access point name (APN) is configured on the user's mobile device after the policy is applied.
Page topCorporate container
This section contains information about working with a corporate container.
About corporate containers
Android Enterprise is a platform for managing the corporate mobile infrastructure and provides company employees with a safe work environment in which they can use mobile devices. For details on using Android Enterprise, see the Google support website.
You can create a corporate container that uses an Android Work Profile on a user's personal mobile device. A corporate container is a safe environment in which the administrator can manage apps and user accounts without restricting the user's use of their own data. When a corporate container is created on the user's mobile device, the following corporate apps are automatically installed in it: Google Play, Google Chrome, Downloads, Kaspersky Endpoint Security for Android, and others. Apps installed in the corporate container as well as notifications from these apps are marked with a briefcase icon. You have to create a separate Google corporate account for the Google Play app. Apps installed in a corporate container appear in the common list of apps.
Page topConfiguring a corporate container
To configure the settings of a corporate container:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Corporate container section.
- On the Corporate container on devices card, click Settings.
The Corporate container on devices window opens.
- Enable the settings using the Corporate container on devices toggle switch.
- Specify the corporate container settings:
- On the General tab, you can specify the settings for data sharing, contacts, and more.
- Settings in the Data access and sharing section:
- Prohibit personal apps from sharing data with corporate container apps
- Prohibit corporate container apps from sharing data with personal apps
- Prohibit corporate container apps from accessing personal files
- Prohibit personal apps from accessing files in corporate container
- Prohibit use of clipboard between personal apps and corporate container
- Prohibit activation of USB debugging
- Prohibit users from adding and removing accounts in corporate container
- Prohibit screen sharing, recording, and screenshots in corporate container apps
- Settings in the File sharing section:
- Settings in the Contacts section:
- Settings in the Data access and sharing section:
- On the Apps tab, specify the following settings:
- Settings in the General section:
- Enable App Control in corporate container only
- Enable Web Protection and Web Control in corporate container only
- Prohibit installation of apps from unknown sources in corporate container
- Prohibit removing apps from corporate container
- Prohibit displaying notifications from corporate container apps when screen is locked
- Prohibit use of camera for corporate container apps
- In the Granting runtime permissions for corporate container apps section you can select an action to be performed when corporate container apps are running and request additional permissions. This does not apply to permissions granted in the device settings (for example, Access All Files).
- In the Adding widgets of corporate container apps to device home screen section you can choose whether the device user is allowed to add widgets of corporate container apps to the device home screen.
- Settings in the General section:
- On the Certificates tab, you can configure the following settings:
- On the Password tab, specify the corporate container password settings:
- Require setting a password for corporate container
- Minimum password length
- Minimum password complexity requirements
- Maximum number of failed password attempts before corporate container is deleted
- Maximum password lifetime (days)
- Number of days to send a notification before a required password change
- Number of recent passwords that cannot be set as a new password
- Period of inactivity before corporate container is locked (sec)
- Period after biometric unlock before password must be entered (min)
- Allow biometric unlock methods
- Allow fingerprint unlock
- Allow face unlock
- Allow iris scanning
- On the Passcode tab, specify the one-time passcode settings. The user will be prompted to enter the one-time passcode to unlock their corporate container if it is locked.
- On the General tab, you can specify the settings for data sharing, contacts, and more.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with Kaspersky Security Center. The user's mobile device is divided into a corporate container and a personal space.
Page topUnlocking the corporate container
The corporate container can be locked if the device does not meet the Compliance Control security requirements.
To unlock the corporate container, the user of the mobile device must enter a one-time corporate container passcode on the locked screen. The passcode is generated by Kaspersky Security Center and is unique for each mobile device. When the corporate container is unlocked, the corporate container password is set to the default value (1234).
As an administrator, you can view the passcode in the policy settings that are applied to the mobile device. The length of the passcode can be changed (4, 8, 12, or 16 digits) in the Corporate container on devices settings of the policy.
To unlock a corporate container using a one-time passcode:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Mobile → Devices.
- Click the mobile device for which you want to get a one-time passcode.
- Select Applications → Kaspersky Mobile Devices Protection and Management.
The Kaspersky Mobile Devices Protection and Management properties window opens.
- Select the Application settings tab.
The unique passcode for the selected device is shown in the One-time code field of the One-time corporate container passcode section.
- Use any available method (such as email) to communicate the one-time passcode to the user.
The user then must enter the received one-time passcode on their device.
The corporate container of the user's mobile device is unlocked.
After the corporate container on a device is locked, the history of corporate container passwords is cleared. This means that the user can specify a recent password, regardless of the corporate container password settings.
Page topAdding an LDAP account
These settings apply to supervised devices and devices operating in basic control mode.
To enable an iOS MDM device user to access corporate contacts on the LDAP server, add an LDAP account.
To add an LDAP account of an iOS MDM device user:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the LDAP card, click Settings.
The LDAP window opens.
- Enable the settings using the LDAP toggle switch.
- Click Add.
The Add LDAP account window opens.
- On the General tab. specify the following LDAP settings:
- In the Server section, specify the server settings:
- In the Description field, enter a description of the user's LDAP account. You can either enter a value or select a macro by clicking the
 button.
button. - In the Server address field, enter the name of the LDAP server domain.
- In the Description field, enter a description of the user's LDAP account. You can either enter a value or select a macro by clicking the
- In the Authentication section, specify the user's credentials:
- In the Account name field, enter the account name for authorization on the LDAP server. You can either enter a value or select a macro by clicking the
 button.
button. - In the Password field, enter the password of the LDAP account for authorization on the LDAP server.
- To use the SSL (Secure Sockets Layer) data transport protocol to secure the transmission of messages, select the Use SSL connection check box.
- In the Account name field, enter the account name for authorization on the LDAP server. You can either enter a value or select a macro by clicking the
- If necessary, in the Per App VPN section, configure Per App VPN.
- In the Server section, specify the server settings:
- On the Search tab, compile a list of search queries for the iOS MDM device user to access corporate data on the LDAP server:
- Click the Add setting button to add a block of the search query settings.
- In the Name field, enter the name of a search query.
- In the Search scope drop-down list, select the nesting level of the folder for searching corporate data on the LDAP server:
- Root folder of the LDAP server. Search in the base folder of the LDAP server.
- First level subfolders. Search in folders in the first nesting level, counting from the base folder.
- All subfolders. Search in folders in all nesting levels, counting from the base folder.
- In the Search base field, enter the path to the folder on the LDAP server where the search begins (for example: "ou=people", "o=example corp").
- Repeat steps a-d for all search queries that you want to add to the iOS MDM device.
- Click Add.
The new LDAP account appears in the list.
You can modify or delete LDAP accounts in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, LDAP accounts from the compiled list is added on the user's mobile device. The user can access corporate contacts in the standard iOS apps: Contacts, Messages, and Mail.
Page topAdding a contacts account
These settings apply to supervised devices and devices operating in basic control mode.
To let the iOS MDM device user synchronize data with the CardDAV server, add a CardDAV account. Synchronization with the CardDAV server lets the user access the contact details from any device.
To add a CardDAV account of an iOS MDM device user:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Contacts card, click Settings.
The Contacts window opens.
- Enable the settings using the Contacts toggle switch.
- Click Add.
The Add CardDAV account window opens.
- In the Server section, in the Description field, enter a description of the user's CardDAV account.
- In the Server address and Server port fields, enter the host name or the IP address of the CardDAV server and the number of the CardDAV server port.
- In the Contact URL field, specify the URL of the CardDAV account of the iOS MDM device user on the CardDAV server (for example:
http://example.com/carddav/users/mycompany/user).The URL must begin with
http://orhttps://. - In the Authentication section, in the Account name field, enter the account name for authorization on the CardDAV server.
- In the Password field, enter the CardDAV account password for authorization on the CardDAV server.
- If you want to use the SSL (Secure Sockets Layer) data transport protocol to secure the transmission of data between the CardDAV server and the mobile device, select the Use SSL connection check box.
- If necessary, in the Per App VPN section, configure Per App VPN.
- Click Add.
The new CardDAV account appears in the list.
You can modify or delete CardDAV accounts in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, CardDAV accounts from the compiled list will be added on the user's mobile device.
If you experience problems when adding or updating accounts, check whether the settings you configured are correct.
Page topAdding a calendar account
To let an iOS MDM device user access their calendar events on a CalDAV server, add a CalDAV account. Synchronization with the CalDAV server lets the user create and receive invitations, receive event updates, and synchronize tasks with the Reminders app.
To add an iOS MDM device user's CalDAV account:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Calendar card, click Settings.
The Calendar window opens.
- Enable the settings using the Calendar toggle switch.
- Click Add.
The Add CalDAV account window opens.
- In the Server section, in the Description field, enter a description of the user's CalDAV account.
- In the Server address and Server port fields, enter the host name or the IP address of a CalDAV server and the number of the CalDAV server port.
- In the Calendar URL field, specify the URL of the CalDAV account of the iOS MDM device user on the CalDAV server (for example, http://example.com/caldav/users/mycompany/user).
The URL must begin with
http://orhttps://. - In the Authentication section, in the Account name field, enter the account name for authorization on the CalDAV server.
- In the Password field, set the CalDAV account password for authorization on the CalDAV server.
- If you want to use the SSL (Secure Sockets Layer) data transport protocol to secure transmission of event data between the CalDAV server and the mobile device, select the Use SSL connection check box.
- If necessary, in the Per App VPN section, configure Per App VPN.
- Click Add.
The new CalDAV account appears in the list.
You can modify or delete CalDAV accounts in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, CalDAV accounts from the compiled list is added on the user's mobile device.
If you experience problems when adding or updating accounts, check whether the settings you configured are correct.
Page topConfiguring a calendar subscription
These settings apply to supervised devices and devices operating in basic control mode.
To let the iOS MDM device user add events of shared calendars (such as a corporate calendar) to the user's calendar, add a subscription to these calendars. Shared calendars are calendars of other users who have a CalDAV account, iCal calendars, and other published calendars.
To add a calendar subscription:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Calendar subscriptions card, click Settings.
The Calendar subscriptions window opens.
- Enable the settings using the Calendar subscriptions toggle switch.
- Click Add.
The Add calendar subscription window opens.
- In the Description field, enter a description of the calendar subscription.
- In the Server address field, specify the URL of a third-party calendar.
In this field, you can enter the mail URL of the CalDAV account of a user whose calendar you are subscribing to. You can also specify the URL of an iCal calendar or a different published calendar.
- In the User name field, enter the user account name for authentication on the server of the third-party calendar.
- In the Password field, enter the calendar subscription password for authentication on the server of the third-party calendar.
- If you want to use the SSL (Secure Sockets Layer) data transport protocol to secure the transmission of event data between the CalDAV server and the mobile device, select the Use SSL connection check box.
- If necessary, in the Per App VPN section, configure Per App VPN.
- Click Add.
The new calendar subscription appears in the list.
You can modify or delete calendar subscriptions in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, events from the shared calendar in the list will be added to the calendar on the user's mobile device.
Page topConfiguring SSO
These settings apply to supervised devices and devices operating in basic control mode.
The SSO settings let you configure account settings for using Single Sign-On technology. Single Sign-On (SSO) is an authentication method that allows a user to sign in to multiple services with a single ID. The Kerberos protocol is used for user authentication.
To configure the use of SSO on iOS MDM devices:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the SSO card, click Settings.
The SSO window opens.
- Enable the settings using the SSO toggle switch.
- Specify the following settings:
- In the Account name field, specify the name of the user's Single Sign-On account for Kerberos server authorization. You can either enter a value or select a macro by clicking the
 button.
button. - In the Authentication section, specify the authentication settings:
- In the URL prefixes section, specify the addresses of websites on which Kaspersky Mobile Devices Protection and Management allows using SSO:
- In the Bundle IDs section, specify the IDs of apps in which Kaspersky Mobile Devices Protection and Management allows using SSO:
- In the Account name field, specify the name of the user's Single Sign-On account for Kerberos server authorization. You can either enter a value or select a macro by clicking the
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, SSO is configured on the iOS MDM device.
Page topManaging Web Clips
A Web Clip is an app that opens a website from the home screen of a mobile device. By clicking Web Clip icons on the home screen of the device, the user can quickly open websites (such as the corporate website). Web Clips may also pop-up if the user taps and holds the Kaspersky Endpoint Security for Android app icon.
You can add or delete Web Clips on user devices and specify icons displayed on the screen. Web Clips can be added on both Android and iOS MDM devices.
Managing Web Clips on Android devices
To manage Web Clips on a user's Android device:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Device configuration section.
- On the Web Clips card, click Settings.
The Web Clips window opens.
- Enable the settings using the Web Clips toggle switch.
- Click Add.
The Add Web Clip window opens.
- In the Web Clip name field, enter the name of the Web Clip to be displayed on the home screen of the Android device.
- In the Website URL field, enter the web address of the website that will open when the user taps the Web Clip icon. The address should begin with
http://orhttps://.If the entered website is forbidden or is not on the list of allowed websites in the Web Control settings of the policy, users will not be able to access this website via the Web Clip.
- Click Select to specify the image for the Web Clip icon. The PNG, JPEG, and ICO file formats are supported. If you do not select an image for the Web Clip, a blank square is displayed as the icon.
- Click Add.
The new Web Clip appears in the list.
You can modify or delete Web Clips in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Once the policy is applied to a device, the Kaspersky Endpoint Security for Android app shows notifications to prompt the user to install the Web Clips you created. After the user installs these Web Clips, the corresponding icons are added on the home screen of the device.
If there is no in-app notifications prompting the user to install Web Clips, make sure the Device has not been synchronized with the Administration Server for a long time check box is selected in the Notifications settings of the KES for Android settings section.
The deleted Web Clips are disabled on the home screen of the Android device. If the user taps the corresponding icon, a notification appears that the Web Clip is no longer available. The user should delete the Web Clip from the home screen by following a vendor-specific procedure.
Managing Web Clips on iOS MDM devices
By default, the following restrictions apply to Web Clips:
- The user cannot manually remove Web Clips from the mobile device.
- The corner rounding, shadow, and gloss visual effects are applied to the Web Clip icon on the screen.
- Websites that open when the user taps a Web Clip icon do not open in full-screen mode.
To manage Web Clips on a user's iOS MDM device:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Web Clips card, click Settings.
The Web Clips window opens.
- Enable the settings using the Web Clips toggle switch.
- Click Add.
The Add Web Clip window opens.
- In the Web Clip name field, enter the name of the Web Clip to be displayed on the home screen of the iOS MDM device.
- In the Website URL field, enter the web address of the website that will open when the user taps the Web Clip icon. The address should begin with
http://orhttps://.If the entered website is forbidden or is not on the list of allowed websites in the Web Control settings of the policy, users will not be able to access this website via the Web Clip.
- Click Select to specify the image for the Web Clip icon.
The image must meet the following requirements:
- Image size no greater than 400 х 400 pixels.
- File format: PNG, JPEG, or ICO.
- File size no larger than 1 MB.
If you do not select an image for the Web Clip, a blank square is displayed as the icon.
If the selected image has a transparent background, the background will be black on the device.
- In the Options section, specify the following additional settings:
- If you want to allow the user to remove the Web Clip from the iOS MDM device, select the Allow removal of Web Clip check box.
- If you want the Web Clip icon to be displayed without special visual effects (rounding of icon corners and gloss effect), select the Precomposed icon check box.
- If you want the website to open in full-screen mode on the iOS MDM device when the user taps the icon, select the Full screen Web Clip check box.
In full-screen mode, the Safari toolbar is hidden and only the website is shown on the device screen.
- Click Add.
The new Web Clip appears in the list.
You can modify or delete Web Clips in the list using the Edit and Delete buttons at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Once the policy is applied, the Web Clip icons in the list you have created are added on the home screen of the user's mobile device.
The deleted Web Clips are removed from the home screen of the iOS MDM device.
Page topSetting a wallpaper
You can set an image as the home screen wallpaper and lock screen wallpaper on users' devices that fall under the same policy.
To set a wallpaper on users' Android devices:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select Android and go to the Device configuration section.
- On the Custom wallpapers card, click Settings.
The Custom wallpapers window opens.
- Enable the settings using the Custom wallpapers toggle switch.
- In the Home screen wallpaper section, in the How to set wallpaper drop-down list, select the method for specifying the wallpaper:
- Add an image to be used as a wallpaper:
- If you selected the Upload file option, click Select to upload an image. When the upload is finished, an image preview will be displayed.
- If you selected the Download image from the internet option, specify the link to the image in the Link to image field. You can click Open preview to view the image in a new browser tab.
- If you want to use the same image as the lock screen wallpaper, in the Lock screen wallpaper section, select the Use home screen wallpaper for lock screen check box.
- Click OK.
- Click Save to save the changes you have made.
The imported image is set as a wallpaper on users' devices.
Page topAdding fonts
These settings apply to supervised devices and devices operating in basic control mode.
To add a font on a user's iOS MDM device:
- In the main window of Kaspersky Security Center Web Console, select Assets (Devices) → Policies & profiles. In the list of group policies that opens, click the name of the policy that you want to configure.
- In the policy properties window, select Application settings.
- Select iOS and go to the Device configuration section.
- On the Custom fonts card, click Settings.
The Custom fonts window opens.
- Enable the settings using the Custom fonts toggle switch.
- Click Add.
- Select the font file saved on your computer. The file must have the .TTF or .OTF extension.
Fonts with the .TTC or .OTC extension are not supported.
Fonts are identified using the PostScript name. Do not install fonts with the same PostScript name even if their content is different. Installing fonts with the same PostScript name will result in an error.
- Click Open.
The new font appears in the list.
You can delete fonts in the list using the Delete button at the top of the list.
- Click OK.
- Click Save to save the changes you have made.
Mobile device settings are changed after the next device synchronization with the iOS MDM Server.
As a result, once the policy is applied, the user will be prompted to install fonts from the list that has been created.
Page top icon in the Mail app in the
icon in the Mail app in the