Contents
- Kaspersky Container Security 1.2 Help
- About the Kaspersky Container Security platform
- Solution architecture
- Standard deployment schemes
- Preparing to install the solution
- Solution installation
- Removing the solution
- Updating the solution
- Solution interface
- Licensing the solution
- Data provisioning
- Working with clusters
- View the list of clusters
- Namespaces in the cluster
- Pods in the cluster
- Visualization of cluster resources
- Setting up integration with external image registries
- Working with images from registers
- Integration with CI/CD
- Image scanning in CI/CD processes
- Configuring integration with GitLab CI/CD
- Configuring integration with Jenkins CI/CD
- Configuring integration with TeamCity CI/CD
- Defining the path to container images
- Monitoring the integrity and origin of images
- Running the scanner in SBOM mode
- Getting scan results in JSON or HTML format
- Running the scanner in lite SBOM mode
- Risk handling
- Compliance check
- Configuring and generating reports
- Security policies configuration
- Managing container runtime profiles
- File Threat Protection
- Configuring integration with image signature validators
- Setting up integration with notification outputs
- Configuring LDAP server integration
- Users, roles, and scopes
- Managing users
- About user roles
- Working with system roles
- Displaying list of roles
- About scopes
- Scopes and enforcement of security policies
- Switching between scopes
- Adding users, roles, and scopes
- Resetting password for user accounts
- Changing settings for users, roles, and scopes
- Removing users, roles, and scopes
- Using Kaspersky Container Security OpenAPI
- Security event log
- Exporting events to SIEM systems
- Information about the status of solution components
- Ensuring safety and reliability of components
- Managing the dynamics of data accumulation
- Backing up and restoring data
- Contacting Technical Support
- Sources of information about the application
- Limitations and warnings
- Glossary
- Third party code information
- Trademark notices
Kaspersky Container Security 1.2 Help
|
Learn about the new functional capabilities of Kaspersky Container Security. |
|
Hardware and software requirements Check the supported orchestration platforms, CI systems, available image registries, and user workstation requirements. |
|
Licensing Kaspersky Container Security Learn more about license types provided for Kaspersky Container Security. |
|
Installing Kaspersky Container Security Prepare for installation and install Kaspersky Container Security in a private or public corporate network. |
|
Scan objects and receive information about detected vulnerabilities, malware, misconfigurations, and sensitive data. |
|
Accepting risks identified by Kaspersky Container Security (vulnerabilities, malware, sensitive data, and misconfigurations) to change the security status of images. |
|
Security policies configuration Configure scanner policies, assurance policies, response policies, and runtime policies to conduct scans in accordance with your requirements. |
|
Image scanning from registries and integration with CI/CD During the project build in the CI system, run the Kaspersky Container Security scanner to check the objects in the repository for compliance with the enabled security policies. |
|
Configure integrations with Telegram and email addresses to receive notifications about security events. |
|
Integration with Active Directory Configure user roles using data on groups from Active Directory |
Process control within containers Use container runtime profiles to control processes and applications inside containers. |
|
Learn more about registration of user activity and storage of scan results. |
About the Kaspersky Container Security platform
Kaspersky Container Security (hereinafter referred to as the solution) allows you to discover security problems and ensures protection throughout the container application lifecycle, from development and deployment control to runtime.
Solution functionalities:
- Integration with image registries (Docker Hub, JFrog Artifactory, Sonatype Nexus Repository OSS, GitLab Registry, Harbor) to scan images in the registry for known vulnerabilities published by the NVD and VDB (DSTD), secrets (passwords, access keys, tokens), misconfigurations, and malware.
- Integration into the continuous integration / continuous delivery (CI/CD) process as a pipeline stage, as well as scanning IaC for misconfigurations and container images for vulnerabilities, malware, and sensitive data (secrets).
- Checking of cluster nodes for compliance with industry information security benchmarks.
- Monitoring compliance with the configured security policies while building and operating the applications, including monitoring container runs in the runtime.
- Monitoring of resources used by the controlled clusters.
You can configure and access the functionalities of Kaspersky Container Security through the Management Console. The console is implemented as a web interface which can be accessed through the Chromium (Google Chrome, Microsoft Edge, Apple Safari) or Mozilla Firefox browsers.
What's new
Kaspersky Container Security 1.2 offers the following new features and improvements:
- Built-in tools to check components' state (the Health Check mechanism), and specifically:
- Automation of maintenance processes, ensuring the safety and reliability of components by means of Auto Care tools, including automatic cleaning of the following:
- Security event log
- Scan history
- Visualization of monitored clusters, network communications, and cluster resource security issues.
- Search and analysis of potential file threats to protect containerized files from malware.
- Support for integration with the following CI systems:
- Generation of reports on the results of checking cluster nodes for compliance with the Kubernetes benchmarks:
- Summary report
- Detailed report
- Integration of Kaspersky Container Security with the Harbor registry to serve as an additional scanner. This functionality allows to start image scanning from the Harbor Registry interface. Scan results are saved in the solution and are available for further use.
- Documenting API requests by using Swagger.
- Ensuring continuous monitoring of infrastructures containing up to 1000 network nodes.
- Support for simplified Chinese.
- Solution functioning in the following cloud environments:
- AWS EKS.
- Microsoft Azure
Kaspersky Security for Containers 1.2.1 has the following updates:
- LDAP-based authentication method was improved.
- Operations for working in Telegram (sending messages, chat searching) were improved.
- Application of filters for results of checking for compliance with the Kubernetes standard was corrected.
- The Vendor Fix field in the Risk acceptance report was amended.
- Capability to work with vulnerabilities in Java dependencies for the CI agent was added.
- Performance of the following controls in runtime policies was improved: Block non-compliant images and Block unregistered images.
- Logic of deleting scopes with policies assigned to them was improved.
- Work with image signature validators was optimized.
- Procedure for authentication of Kaspersky Container Security users was improved.
- API token reissue functionality was corrected.
- Display of a large number of tags when adding images for analysis was corrected.
- Adding a new registry using API was improved (the logic of saving information about tags was fixed).
- Image report templates were amended (links to vulnerabilities in images are displayed).
- Work with email servers when using CRAM-MD5 authentication was ijmproved.
- Capability to configure the frequency of accessing an image registry was added.
- Web interface was improved.
Kaspersky Security for Containers 1.2.2 has the following updates:
- Yandex Registry support was implemented.
- General way to support image registries using the Docker V2 API was added.
- Work with the JFrog Artifactory image registry to support accounts with reduced privileges was improved.
- Mechanism for saving artifacts in CI/CD was improved.
- Agent operation errors in older versions of Kubernetes (version 4.18) were fixed.
- Scheduled scanning of image registries in case of errors with codes 4XX and 5XX was corrected.
- Logic of operation during an integration with a subdomain (using names other than standard names) in the JFrog Artifactory was improved.
Distribution kit
For information about purchasing the application, please visit https://www.kaspersky.com or contact our partners.
The distribution kit includes a Helm Chart package with the containerized resources necessary for deploying and installing Kaspersky Container Security components. The containerized components from the distribution kit are listed in the table below.
Containerized components from the Kaspersky Container Security distribution kit
Component |
Image |
Pod |
|---|---|---|
ClickHouse DBMS |
clickhouse |
kcs-clickhouse |
PostgreSQL DBMS |
postgresql |
kcs-postgres |
PGBouncer connection pooler |
pgbouncer |
kcs-pgbouncer |
Middleware |
middleware |
kcs-middleware |
Event Broker |
event-broker |
kcs-eb |
Image Handler, client scanner |
image-handler |
kcs-ih |
Scanner |
scanner-server |
kcs-scanner |
Licenses |
licenses |
kcs-licenses |
File storage (Minio) |
minio |
kcs-s3 |
Message Broker |
nats |
kcs-nats |
Update file server for private corporate networks (Updates) |
updates |
kcs-updates |
Solution interface (Panel) |
nginx |
kcs-panel |
Agents |
node-agent |
node-agent |
The Helm package also includes a values.yaml configuration file that contains the values of settings for installing and updating the solution.
After downloading and saving the Helm package in a selected directory, the orchestrator downloads the images from the source specified in the Helm package directly to the orchestration platform nodes.
The information required to activate the application is sent to you by email.
Page top
Hardware and software requirements
To install and operate Kaspersky Container Security, the following infrastructure requirements must be met:
- One of the following orchestration platforms:
- Kubernetes (version 1.21 or later)
- OpenShift (version 4.11 or later)
- DeckHouse (versions 1.52, 1.53. CNI: Flannel)
- Availability of a CI system to scan container images within the development process (for example, GitLab CI).
- Installed package manager Helm v3.10.0 or later.
To implement runtime monitoring with container runtime profiles, orchestrator nodes must meet the following requirements:
- Linux kernel 4.18 or later.
- Container runtimes (CRI): containerd, CRI-O.
- Container Network Interface (CNI) plug-ins: Flannel, Calico, Cilium.
Minimum supported versions of Linux distributions and Linux kernels to implementing runtime monitoring using container runtime profiles:
- CentOS 8.2.2004 or later + kernel 4.18.0-193 or later.
- Ubuntu 18.04.2 or later + kernel 4.18.0 or later
- Debian 10 or later + kernel 4.19.0 or later
- Astra Linux SE 1.7. * + Kernel 6.1.50-1-generic.
If your infrastructure contains host servers running other Linux distributions, we recommend contacting Technical Support. Technical Support will check the compatibility of the solution with your distributions. If such compatibility is not available, the distributions may be supported by future versions of Kaspersky Container Security.
Kaspersky Container Security ensures correct operation when used in the Istio service mesh infrastructure.
When using external database management systems, Kaspersky Container Security supports PostgreSQL 11.*, 13.*, 14.*.
Kaspersky Container Security supports integration with the following image registries:
- GitLab 14.2 or later
- Docker Hub V2 API or later
- JFrog Artifactory 7.55 or later
- Sonatype Nexus Repository OSS 3.43 or later
- Harbor 2.х.
Image requirements (OS, version, scanned packages):
- AlmaLinux, versions 8, 9. Packages installed via dnf/yum/rpm are scanned.
- Alpine Linux, versions 2.2 - 2.7, 3.0 - 3.20, Edge. Packages installed via apk are scanned.
- Amazon Linux, versions 1, 2, 2023. Packages installed via dnf/yum/rpm are scanned.
- Astra Linux SE, versions 1.6.x, 1.7.x. Packages installed via apt/dpkg are scanned.
- CBL-Mariner, versions 1.0, 2.0. Packages installed via dnf/yum/rpm are scanned.
- CentOS, versions 6, 7, 8. Packages installed via dnf/yum/rpm are scanned.
- Chainguard, all versions. Packages installed via apk are scanned.
- Debian GNU/Linux, versions 7, 8, 9, 10, 11, 12. Packages installed via apt/dpkg are scanned.
- openSUSE Leap, versions 42, 15. Packages installed via zypper/rpm are scanned.
- Oracle Linux, versions 5, 6, 7, 8. Packages installed via dnf/yum/rpm are scanned.
- Photon OS, versions 1.0, 2.0, 3.0, 4.0. Packages installed via tdnf/yum/rpm are scanned.
- Red Hat Enterprise Linux, versions 6, 7, 8. Packages installed via dnf/yum/rpm are scanned.
- RedOS, versions 7.1, 7.2, 7.3.x, 8.0. Packages installed via dnf/yum/rpm are scanned.
- Rocky Linux, versions 8, 9. Packages installed via dnf/yum/rpm are scanned.
- SUSE Enterprise Linux, versions 11, 12, 15. Packages installed via zypper/rpm are scanned.
- Ubuntu, all versions supported by Canonical. Packages installed via apt/dpkg are scanned.
- Wolfi Linux, all versions. Packages installed via apk are scanned.
- OS with the Conda command line tool installed. Packages installed via conda are scanned.
When configuring Kaspersky Container Security in a cluster with three worker nodes, three scanner pods (kcs-ih) and a maximum image scan size of 10 GB, the cluster working node must meet the following requirements:
- At least 10 processor cores
- At least 18 GB of RAM
- 40 GB of free disk space
- At least 1 Gbps of communication channel bandwidth between cluster components
For agents operation in the cluster, each working node must be provided with the following additional computational resources:
- 2 processor cores
- 3 GB of RAM
- 15 GB of free disk space
You must allocate 1 GB of free disk space for ClickHouse Persistent Volume for each monitored node in the cluster where the solution is installed.
The above requirements apply to Kaspersky Container Security deployment only; they do not take into account other loads on the client's resources.
Kaspersky Container Security user workstation requirements:
- Permanent Internet connection when deployed in a public corporate network.
- Access to the Management Console page of Kaspersky Container Security (address within customer's corporate network, specified during installation).
- Communication channels with at least 10 Mbit/s bandwidth.
- One of the following browsers:
- Google Chrome version 73 or later.
- Microsoft Edge version 79 or later.
- Mozilla Firefox version 63 or later.
- Apple Safari version 12.1 or later.
- Opera version 60 or later.
Scaling
Kaspersky Container Security supports scaling for the number of scanning pods to ensure that the incoming image volume can be scanned. You can scale the number of scanning pods up or down at any time while the solution is operating.
When a scanning pod is added, the system resources increase as follows:
- The number of node processors—by 2.
- The amount of RAM on the nodes—by 4 GB.
- The amount of free disk space on a node hard drive—by 15 GB.
To scan images larger than 10 GB, the kcs-ih service resources must be increased as follows per scanning pod and for each additional GB.
- The amount of RAM on the nodes—by 300 MB.
- The amount of free disk space on a node hard drive—by 1 GB.
If the images are not scanned for configuration file errors during standard operation mode, it is not necessary to increase the RAM of the scanning pods.
To process the results of scanning many large objects faster, you can allocate more resources to the job handler service by updating variables in the Helm package.
To add more scan job handling resources:
- Open the Helm package and specify the required number of handlers for the
kcs-middlewareparameter in thescanWorkersvariable in thedefaultsection. - In the
requestsandlimitsvariables, specify the size of RAM as determined according to the following formula:memory = X * scanWorkers / 2, wherememoryis the size of RAM allocated to the image handler service.Xis the original value of the variable that denotes the size of RAM.scanWorkersis the number of handlers specified in step 1.The result of
scanWorkers/2can't be zero. - In the
requestsandlimitsvariables, specify the CPU resources as calculated according to the following formula:cpu = X*scanWorkers, wherecpuis the CPU resources allocated to the image handler service.Xis the original value of the variable that denotes the CPU resources.scanWorkersis the number of handlers.
Example of adding more scan job handling resources
Page top
System packages of base images
The following operating system images are used as base images by Kaspersky Container Security:
- Alpine 3.18.4.
- Ubuntu 23.10.
- Oracle Linux 9.2.
Package management systems ("package managers") are used to manage the installation, removal, configuration, and updating of various software components. Kaspersky Container Security uses the following package managers for its base operating systems:
- For Alpine, apk.
- For Ubuntu, apt.
- For Oracle Linux, rpm.
To get information about installed system packages,
use the standard orchestrator tools for accessing a running container and (depending on the package manager used) enter the following bash command:
- For apk:
apk -q list | grep "installed". - For apt:
apt list --installed. - For rpm:
yum list installed.
Scanned application software packages
Kaspersky Container Security supports the following scanned application software packages in the specified programming languages:
- Ruby:
- gemspec (image is scanned).
- Gemfile.lock (repository in CI/CD is scanned).
- Python:
- egg package, wheel package, conda package (image is scanned).
- Pipfile.lock, poetry.lock, requirements.txt (repository in CI/CD is scanned).
- PHP:
- installed.json (image is scanned).
- composer.lock (repository in CI/CD is scanned).
- Node.js:
- package.json (image is scanned).
- package-lock.json, yarn.lock, pnpm-lock.yaml (repository in CI/CD is scanned).
- .NET: packages.lock.json, packages.config, .deps.json, Packages.props (image and repository in CI/CD are scanned).
- Java:
- * .jar, * .war, * .par and * .ear (image is scanned).
- pom.xml, * gradle.lockfile, * .sbt.lock (repository in CI/CD is scanned).
- Go:
- Binary files (image is scanned).
- go.mod (repository in CI/CD is scanned).
- Rust:
- Binaries checked by Cargo (image is scanned).
- Cargo.lock (image and repository in CI/CD are scanned).
- C/C++: conan.lock (repository in CI/CD is scanned).
- Elixir: mix.lock (repository in CI/CD is scanned).
- Dart: pubspec.lock (repository in CI/CD is scanned).
- Swift: Podfile.lock, Package.resolved (repository in CI/CD is scanned).
- Julia: Manifest.toml (image and repository in CI/CD are scanned).
Working in cloud-based environments
Kaspersky Container Security can operate in various cloud environments. For more information on launching the solution in cloud environments, contact your Presales Manager.
Page top
Solution architecture
Kaspersky Container Security components are deployed based on the images included in the distribution kit. The table below shows which images correspond to which solution components.
Kaspersky Container Security components
Component |
Image |
Component function |
|---|---|---|
ClickHouse DBMS |
clickhouse |
Managing ClickHouse databases for storing and processing informational messages from agents. |
PostgreSQL DBMS |
postgresql |
Managing databases using tools for analyzing and optimizing query parsing and query engines. |
PGBouncer connection pooler |
pgbouncer |
PostgreSQL connection pool management. |
Middleware |
middleware |
Implementation of the data processing business logic of the solution server component and providing REST API for the graphical user interface of Kaspersky Container Security. |
Event Broker |
event-broker |
Ensuring communication between various elements of the distributed solution system. |
Image Handler, client scanner |
image-handler |
Processing scan jobs using vulnerability and malware scanners: starting scan jobs, scanning objects, aggregating and publishing scan results. |
Scanner server |
scanner-server |
Managing the scanner server, which is used to store the vulnerabilities database and the image layer cache, as well as to support the image handler. |
Licensing module |
licenses |
Manage functionalities provided under the license. |
File storage |
minio |
Managing the storage for storing and distributing to users the files that the solution generates. |
Message Broker |
nats |
Determining the order of communication requests in the form of messages. |
File server with updates for private corporate networks |
updates |
Delivery of updates when the solution is deployed. |
Solution interface |
nginx |
Functioning of the Kaspersky Container Security graphical user interface. |
Agents |
node-agent kube-agent |
Maintaining security on the nodes in accordance with configured security policies and integration with the orchestrator. |
The solution includes the following main components:
- Kaspersky Container Security Middleware
- Kaspersky Container Security Agents
- Kaspersky Container Security Scanner
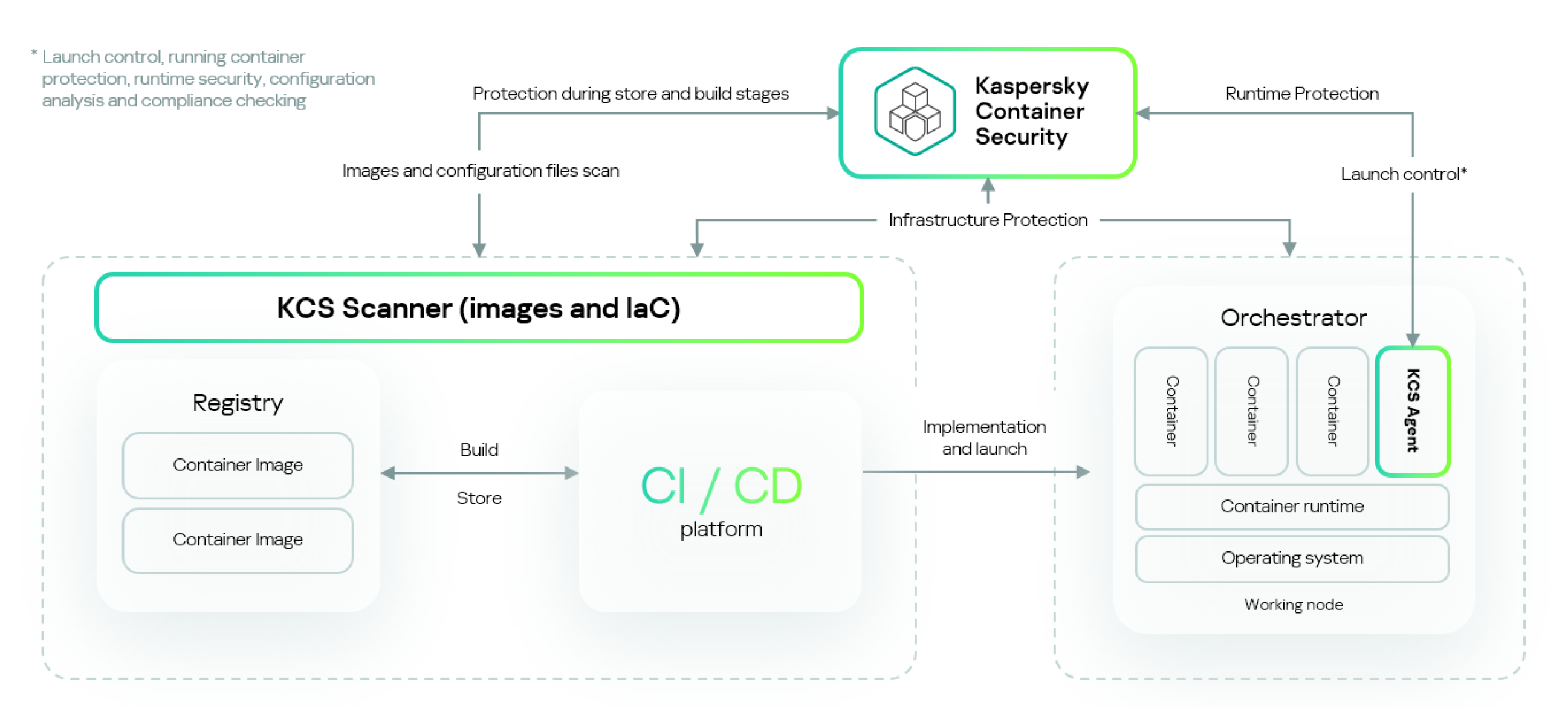
Overall architecture scheme of Kaspersky Container Security
Kaspersky Container Security can be deployed in a public or private corporate network.
Middleware
The Kaspersky Container Security middleware has the following functions:
- Provides an interface for interactive management of the solution (Management Console).
- Ensures integration with external software components (SIEM, CI, image registries, LDAP, Telegram, email) and the receipt of information from them.
- Coordinates the operation of other solution components.
- Ensures the creation and management of security policies.
- Displays the results of solution operations.
Agents
Kaspersky Container Security Agents (hereinafter also referred to as "agents") are a solution component that runs as a containerized application and provides security on nodes in accordance with configured security policies, in particular:
- Runtime security of containers running on the nodes.
- Network interaction between pods and applications inside containers.
- Integration with the orchestration platform and flow of data necessary for analysis of the orchestrator configuration and its components.
- Startup of containers from trusted images to prevent unverified images from running.
Agents are installed on all nodes of clusters and all clusters that need protection. Kaspersky Container Security works with two types of agents: cluster protection agents (csp-kube-agent) and node protection agents (csp-node-agent). Together they form groups of agents. A separate group of agents is created for each cluster. Multiple groups of agents can be created for one installation of the solution.
If the cluster contains no agents, some of the solution functionality is unavailable (for example, runtime policies, resource monitoring).
Scanner
Scanner is a Kaspersky Container Security software component that scans objects in real time to assess their security and detect known vulnerabilities, malware, signs of sensitive data, and misconfigurations. The scanner lets you conduct security checks based on active security policies.
Kaspersky Container Security employs the following types of scanners:
- Vulnerability scanner based on the Common Vulnerabilities and Exposures (CVE) database
- File threat scanner within the File Threat Protection component
- Configuration file scanner
- Sensitive data (secrets) scanner
About object scanning
Kaspersky Container Security checks objects deployed in the solution during the scanning process.
The scanning process searches for and analyzes threats and security risks associated with objects in the solution. Object scans must be performed regularly to keep track of emerging security threats.
When scanning, Kaspersky Container Security identifies the following security threats:
- Vulnerabilities
- Malware.
- Misconfigurations
- Sensitive data
- Non-compliance with security policy requirements
Scanning process
The scanner receives scan jobs through the image handler. The image handler is a module deployed in the Kaspersky Container Security infrastructure that forwards scan jobs to the scanner and receives the scan results from the scanner.
When scan jobs are forwarded, the current status of the scanner is determined as one of the following:
- Free — the scanner is not processing objects and can accept a job from the image handler application if requested.
- Busy — the scanner is currently processing a scan job. A new job from the image handler application is put in the queue.
The scan job queue includes all forwarded scan jobs and is generated in the following cases:
- An image registry scan is manually started.
- An image registry scan is automatically started.
- A bulk scan of cluster objects is started.
Jobs in the scan queue receive the following statuses:
- Pending — status assigned by default when a job is created.
- In progress — the job is being processed by the image handler.
- Parsing results — the solution processes the job scanning results to display them in the interface.
- Error— scan job failed.
- Finished — the results of the scan job are available.
Scan jobs from the queue are submitted to the image handler in the order of their receipt. A job then goes to a scanner with Free status and is scanned for security issues. The scan results are sent back to the image handler. The job is considered completed and finished if scanning results are received. If a scan job was performed three or more times but received no results, the job is given the Error status.
When scanning many large objects, the solution may be slower to display scan results in the user interface. You may have to wait up to several minutes for the results to appear. During this time, the scan jobs are displayed in the Scanners section with the Parsing results status.
If you want to speed up the processing of scan results, you can allocate more resources to the job handler service by updating the variables in Helm Chart (for more details, see Scaling).
When an error occurs, the solution displays an error message that consists of a code and a text message (for example, HNDL-004: scan time out).
Error messages are displayed in English. Examples of messages and their meanings are listed in the table below.
Examples of possible error messages when running scan jobs
After scanning, the solution displays the scan results. If security threats are detected in an object, Kaspersky Container Security prompts you to perform one of the following actions:
- Delete the security threat.
- Accept the risk.
Standard deployment schemes
Kaspersky Container Security supports the following deployment scenarios:
- Deployment in a public corporate network (Internet access from the Kubernetes cluster is allowed):
- Images from which the Kaspersky Container Security components are deployed are located in a public repository.
- After installation, the solution components refer to the vulnerability databases on the Internet.
- Databases are updated using the Kaspersky update server, available on the Internet.
A private corporate network with access to servers in the allowed servers list may be considered a public corporate network.
- Deployment in a private corporate network (Internet access from the Kubernetes cluster is prohibited):
- An internal repository is used to host the images from which the Kaspersky Container Security components are deployed.
- Additionally, the component kcs-updates is installed, which is a special image containing the vulnerability databases and security benchmarks that the solution requires.
- After installation, the solution components refer to the vulnerability databases and security standards located in the special image kcs-updates inside the corporate network.
- The Update server providing threat database updates is deployed as a separate component in the corporate network.
A private corporate network also allows for deployment with a proxy server.
We do not recommend deploying the solution with a clustered infrastructure configuration in which network interaction between host servers (nodes) is conducted in the public Internet. If this configuration is used, network interaction in the cluster may be exposed to critical network security risks.
Deployment in a public corporate network
When deployed in a public corporate network, Kaspersky Container Security is allowed to access the Internet from a cluster. The solution databases are updated from external databases containing updates for the vulnerabilities and malware databases.
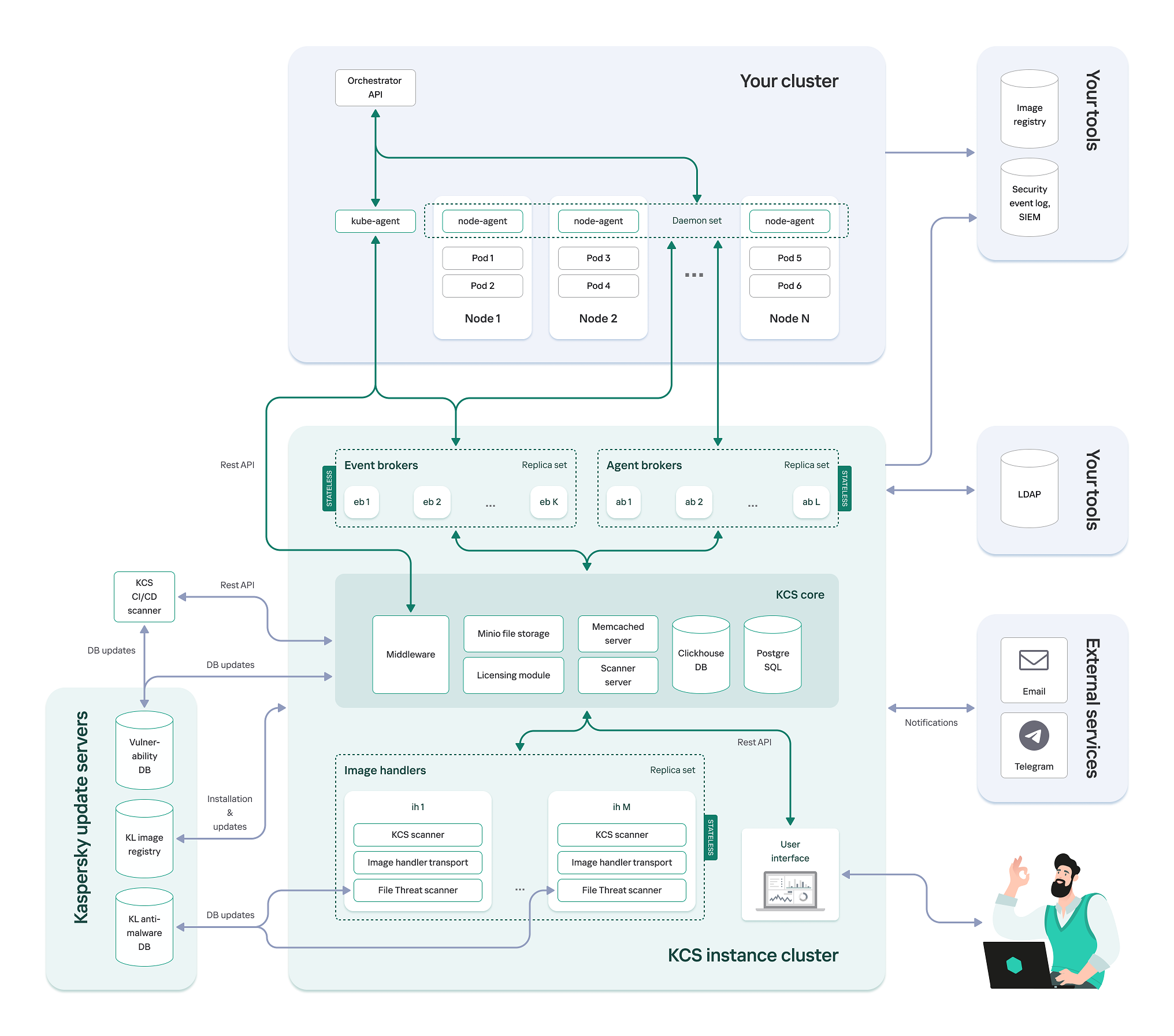
Solution architecture when deployed in a public corporate network
Page top
Deployment in a private corporate network
When deployed in a private corporate network, Kaspersky Container Security is prohibited from accessing the Internet from a cluster. The solution databases are updated by updating the images of the scanner that is run from the CI / CD and the image scanner.
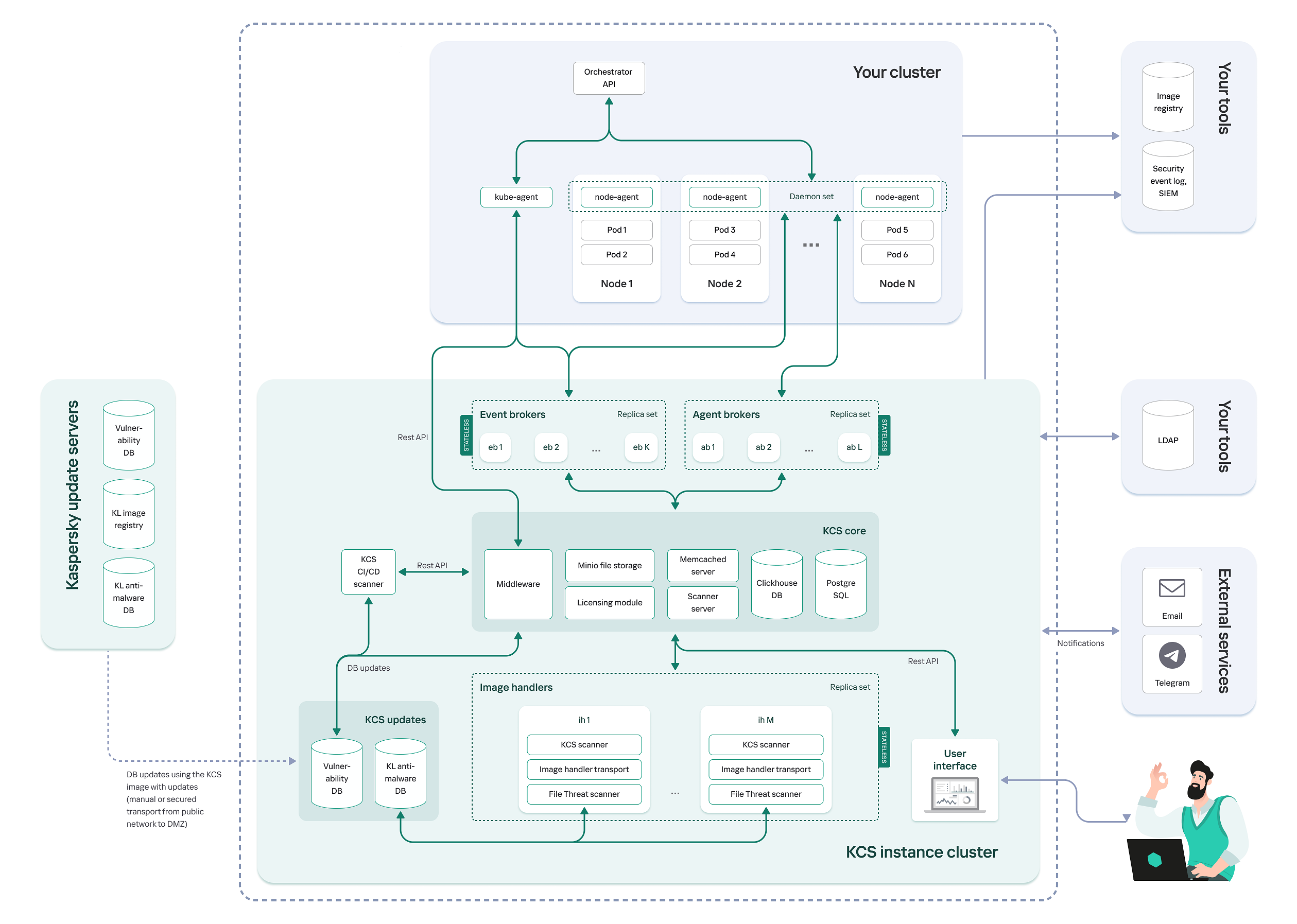
Solution architecture when deployed in a private corporate network
Page top
Preparing to install the solution
Prior to installing Kaspersky Container Security, you must install all certificates required for the corporate network and configure the proxy servers.
The solution can be deployed in a private or public corporate network.
Before installing Kaspersky Container Security, make sure that you have the following components and accesses:
- Virtual or physical machine with access to the Internet and the cluster.
- Helm package manager for packaging, configuring, and deploying applications and services in clusters.
Kaspersky Container Security supports Helm v3.10.0 or later.
- Internet access to download Helm Chart packages.
- Orchestrator management tool, for example, kubectl for Kubernetes or oc for Openshift.
- Access to a cluster using the kubeconfig file.
To install the solution in a private corporate network, configure a repository for container images. This repository accesses the Kaspersky Container Security vendor repository with the credentials provided by the solution vendor.
To prepare to install the solution in a private corporate network:
- Connect the vendor's Helm repository containing the Helm Chart package.
export CHART_URL="xxxxxx"export CHART_USERNAME="xxxxxx"export CHART_PASSWORD="xxxxxx"export VERSION="xxxxxx"The
CHART_URL, CHART_USERNAME, CHART_PASSWORD, and VERSIONvalues are provided by the vendor. - Fill in the file with the installation settings (values.yaml) included in the solution distribution kit according to the comments in the file.
We do not recommend specifying account data in the values.yaml file to be used when launching the Helm Chart package.
The following main installation settings must be specified in the values.yaml file:
- Namespace name.
helm upgrade --install kcs . \--create-namespace \--namespace kcs \--values values.yaml \ - The domain name of Kaspersky Container Security for Inbound connections.
--set default.domain="kcs.example.domain.ru" \When network policies are enabled, you must specify at least one namespace for the cluster ingress controller.
--set default.networkPolicies.ingressControllerNamespaces="{ingress-nginx}" \By default, network policies are enabled.
- Secrets of the solution components.
--set secret.infracreds.envs.POSTGRES_USER="user" \--set-string secret.infracreds.envs.POSTGRES_PASSWORD="pass" \--set secret.infracreds.envs.MINIO_ROOT_USER="user" \--set-string secret.infracreds.envs.MINIO_ROOT_PASSWORD="pass" \--set-string secret.infracreds.envs.CLICKHOUSE_ADMIN_PASSWORD="pass" \--set secret.infracreds.envs.NATS_USER="user" \--set-string secret.infracreds.envs.NATS_PASSWORD="pass" \ - Secrets related to access to the solution installation repository.
--set pullSecret.kcs-pullsecret.username="user" \--set pullSecret.kcs-pullsecret.password="pass"
We recommend not to change the composition of the basic installation settings.
- Namespace name.
- Save the file with the installation settings and proceed to install the solution.
Solution installation
Kaspersky Container Security components are supplied as images in the Kaspersky Container Security manufacturer registry and deployed as containers.
Installation of the Kaspersky Container Security platform consists of the following steps:
- Installation of the Basic business logic module and the Scanner components.
- First launch of the Management Console.
- Configuration of the agent groups and agent deployment on the controlled cluster nodes.
After installation, you should prepare the solution for operation:
- Configure integration with image registries.
- Configure integration with outputs.
- Configure security policies.
- Add container runtime profiles.
- Configure the File Threat Protection parameters.
- Configure integration with image signature validators.
- Configure integration with CI/CD.
- Configure user accounts, roles, and scopes.
- Configure integration with LDAP server.
Installing the basic business logic module and scanner
Before the solution installation, you must check the data integrity in the prepared Helm Chart package.
To check the data integrity:
- Download the archive with the prepared Helm Chart package and the hash file into the same directory.
- From this directory, execute the following command:
sha256sum -c kcs-1.2.0.tgz.shaThe data integrity is confirmed if the following message is displayed:
kcs-1.2.0.tgz: OK
Before starting the installation (including on AWS EKS or Microsoft Azure), pay attention to the storageClass and ingressClass settings in the default and ingress.kcs blocks in the values.yaml configuration file. These settings are cluster relevant and, if necessary, are to be changed according to your infrastructure. Below is the example of the default settings option for Azure:
default: storageClass: azurefile networkPolicies: ingressControllerNamespaces: - app-routing-system
ingress: kcs: ingressClass: webapprouting.kubernetes.azure.com
To install the basic business logic module and the scanner of Kaspersky Container Security,
After preparing the configuration file, run the solution installation:
cd kcs/
helm upgrade --install kcs . \
--create-namespace \
--namespace kcs \
--values values.yaml \
--set default.domain="kcs.example.domain.ru" \
--set default.networkPolicies.ingressControllerNamespaces="{ingress-nginx}" \
--set secret.infracreds.envs.POSTGRES_USER="user" \
--set secret.infracreds.envs.POSTGRES_PASSWORD="pass" \
--set secret.infracreds.envs.MINIO_ROOT_USER="user" \
--set secret.infracreds.envs.MINIO_ROOT_PASSWORD="pass" \
--set secret.infracreds.envs.CLICKHOUSE_ADMIN_PASSWORD="pass" \
--set secret.infracreds.envs.NATS_USER="user" \
--set secret.infracreds.envs.NATS_PASSWORD="pass" \
--set pullSecret.kcs-pullsecret.username="user" \
--set pullSecret.kcs-pullsecret.password="pass"
After installation, the solution components are deployed.
After installation is complete, a record about the execution of the solution installation command remains in the command shell. You can open the command history file and delete this record, or prevent the command history from being logged in the command shell before installation.
The control panel will be available at the address specified in the envs subsection of the environment variables section. This allows you to create the ConfigMap object for the API_URL parameter:
http://${DOMAIN}
First launch of the Management console
To start the Kaspersky Container Security Management Console:
- In your browser, navigate to the address specified for the Management Console during the Server installation.
The authorization page opens.
- Enter your user name and password and click the Login button.
During the installation of the solution, the user name and password have the same value assigned—admin. You can change the user name and password after launching the Management Console.
After 3 unsuccessful password entry attempts, the user is temporarily blocked. The default block duration is 1 minute.
- Following the request, change the current password for the user account: enter a new password, confirm it, and click the Change button.
Passwords have the following requirements:
- The password must contain numerals, special characters, and uppercase and lowercase letters.
- The minimum password length is 6 characters, and the maximum password length is 72 characters.
The main page of the Management Console opens.
By default, the logged-in user session in the Management Console is 9 hours. In the Settings → Authentication section, you can set your own session duration from the minimum of 1 hour to the maximum of 168 hours. After this time expires, the session ends.
You can change the connection settings in the Settings → Authentication section.
Page top
Viewing and accepting the End User License Agreement
When you launch the Management Console in a browser for the first time, Kaspersky Container Security prompts you to read the End User License Agreement between you and Kaspersky. To continue working with the solution, confirm that you have fully read and accept the terms of the End User License Agreement for Kaspersky Container Security.
To confirm acceptance of the terms of the End User License Agreement,
at the bottom of the End User License Agreement window, click the Accept button.
The authorization page opens for launching the Management Console.
After installing a new version of the solution, accept the End User License Agreement again.
Page top
Checking solution functionality
After installing Kaspersky Container Security and starting the administration console, you can make sure that the solution is detecting security problems and protecting containerized objects.
To check the functionality of Kaspersky Container Security:
- Activate the solution using an activation code or key file.
- Configure integration with image registries. Integration with a single registry is sufficient to check the functionality.
- If necessary, configure the settings of the scanner policy that is created by default after installation of the solution.
- Add an image for scanning and make sure that the scan task is sent for processing.
- After the scan is complete, go to the page with detailed information about the image scan results.
Scanning an image and receiving valid results confirms that Kaspersky Container Security is operating correctly. After this, you can further configure the solution settings.
Agent deployment
You should install Agents on all nodes of the cluster that you want to protect.
A separate group of agents is installed on each cluster.
To deploy agents in the cluster:
- In the main menu, go to the Components → Agents section.
- In the work pane, click the Add agent group button.
- Fill in the fields in the form.
- Enter the group name. For convenient agent management, we recommend naming the group after cluster whose nodes the agents will be deployed on.
- If required, enter a description of the agent group.
- Select the type of agent.
- Select the type of target node operating system.
- Select the orchestrator to use.
- In the KCS registry section, enter the web address of the registry where the images used to install agents are located. To access the registry, you must specify the correct user name and password.
- Under Node monitoring, use the Disable/Enable toggle to start monitoring and analyzing the status of the network, processes inside containers, and file threat protection for the following settings:
- Network connections monitoring. The status of network connections is monitored with traffic capture devices (network monitors) and eBPF modules. This process considers applicable runtime policies and container runtime profiles.
- Container processes monitoring. Container processes are monitored using eBPF programs based on applicable runtime policy rules and container runtime profile rules.
- File threat protection. To track malware database updates, specify one of the following values:
- Malware DB update URL: the web address of the Kaspersky Container Security update service.
- Malware DB update proxy: the HTTP proxy for a cloud or local update server.
If the
kcs-updatescontainer is used to update malware databases, the URL of the database update tool must be specified as follows:<domain>/kuu/updates(for example,https://kcs.company.com/kuu/updates).By default, File Threat Protection databases are updated from Kaspersky cloud servers.
Monitoring steps that are not needed can be disabled to avoid unnecessary load on the nodes.
- Under Deployment data, specify the name of the cluster namespace.
- Click Save.
The work pane below the completed form will display data required to continue deploying agents to the cluster.
- To copy an automatically generated deployment token, click Copy. Deployment token: the identifier that the agent uses to connect to the server.
- Use the instruction from the Configuration field to deploy agents in the cluster. For example:
kubectl apply -f <file> -n <namespace>You can copy the instruction or download it in the .YAML format. Following the application of the instruction, the agent is deployed on all worker nodes of the cluster.
If you change the following settings:
- TLS certificates of the solution,
- URL, user name and password for downloading the kube-agent and node-agent images,
- settings in the Node status monitoring section,
the solution automatically updates the agent deployment instruction.
You must copy or download the updated instruction in a .YAML file again, and then apply it by using the kubectl apply -f file > -n namespace > command. Otherwise, changes to the agent deployment settings are not applied.
Viewing and editing agent groups
The table under Components → Agents displays the created and deployed agent groups. The following information is provided for each of these groups:
- Agent group name
- Number of connected agents in the group
- Type of connected agents
- Orchestrator
- Enabled node monitoring activities
You can filter agent groups by connection status (All, Connected, Disconnected, Pending) using the buttons above the table.
By clicking on the deployment icon ( ), you can expand each agent group in the table to view the following agent details:
), you can expand each agent group in the table to view the following agent details:
- The name of the agent and its connection status.
- Version of the node where the agent is deployed (primary or worker)
- The name of the pod with which the agent is associated.
- Node monitoring activities (Container processes, Network connections, and File Threat Protection).
- Date and time when the agent last connected
By clicking the agent name link, you can expand the sidebar to view agent status information.
To edit the agent group settings:
- Under Components → Agents, in the table with the list of agent groups, click the link in the agent group name.
- In the window that opens, edit the group settings.
- Click Save.
Configuring a proxy server
In version 1.2, Kaspersky Container Security can proxy requests from private corporate networks to the external environment. The settings for connection through a proxy server are configured using the following environment variables in the Helm Chart package, which is included in the solution distribution kit:
HTTP_PROXY– proxy server for HTTP requests.HTTPS_PROXY– proxy server for HTTPS requests.NO_PROXY– a variable that specifies domains or domain masks to be excluded from proxying.If
HTTP_PROXYorHTTPS_PROXY is used,the NO_PROXYvariable is automatically generated in the Helm Chart package, and all the components used by Kaspersky Container Security are indicated in this variable.You can change
the NO_PROXYvariable if you need to specify domains and masks for operation of Kaspersky Container Security in order to exclude them from proxying.SCANNER_PROXY– a specialized variable that specifies which proxy server receives requests from the scanner of the File Threat Protection component. These requests are used by Kaspersky servers to update databases.LICENSE_PROXY– a specialized variable that specifies the proxy server through which kcs-licenses module sends requests to Kaspersky servers to check and update information about the current license.
To specify Kaspersky servers in the permission lists of proxy servers, you must use a *.kaspersky.com or .kaspersky.com mask (depending on the domain name masks supported by your proxy server).
The table below lists the Kaspersky Container Security components that can use environment variables, and also indicates the purpose of these environment variables.
Environment variables used by Kaspersky Container Security components
Component |
Environment variable |
Purpose |
|---|---|---|
kcs-ih |
|
Getting access to external image registries that are not available from the Kaspersky Container Security namespace. |
kcs-ih |
|
Update of the databases of the File Threat Protection scanner using Kaspersky update servers. |
kcs-middleware |
|
Getting access to external image registries that are not available from the Kaspersky namespace. |
kcs-scanner |
|
Update of the vulnerability scanner databases using Kaspersky update servers. |
kcs-licenses |
|
Check and update of information about the current license using Kaspersky license servers. |
Removing the solution
To uninstall the basic business logic module of Kaspersky Container Security, do one of the following:
- On a workstation with the Helm package manager installed, access to the target cluster and the namespace with Kaspersky Container Security installed, run the following command:
helm uninstall kcs-releaseThe Helm package manager does not delete PVC objects, PV objects or secrets. You should delete these manually using the following commands:
kubectl delete pvc<PVC name>kubectl delete secret<secret name>kubectl delete pv<PV name> - If Kaspersky Container Security is installed in a separate namespace, run the following command:
kubectl delete ns<namespace>
To delete a Kaspersky Container Security agent:
Run the following command on the cluster node with the agent deployed:
kubectl delete -f <file> -n kcs
where <file> is the name of the YAML configuration file used to deploy the agent.
If you delete all agents on the nodes of a cluster, we recommend that you remove the group that included these agents.
To delete a group of agents:
- In the main menu of Kaspersky Container Security, go to the Components → Agents section.
- In the line containing the name of the agents group that you want to delete, click the delete icon (
 ).
). - In the window that opens, confirm the action.
Updating the solution
You can find information about the latest versions of the application on the Kaspersky website at https://www.kaspersky.com or contact our partners.
The upgrade process is identical to the installation process. As part of the update process, the current version of the application is indicated.
Page top
Solution interface
The Management Console is implemented through the web interface and consists of the following elements:
- Main menu — sections and subsections of the main menu give access to the key functionalities of the solution.
- Work pane — information and controls in the work pane depend on the section or subsection that you select in the main menu.
Main menu
In the web interface, the main menu of Kaspersky Container Security in the left pane consists of sections that correspond to the basic functions of the solution.
Resources
This section contains the monitoring results of all available Kaspersky Container Security resources: clusters, registries integrated with the solution, and CI/CD processes.
Components
This section contains information about the state of solution components, that is, agents, scanners, and the kernel.
Compliance
This section contains the results of checks on cluster nodes for compliance with the Kubernetes benchmarks.
Policies
This section allows you to configure security policies when operating Kaspersky Container Security.
The Risk acceptance subsection contains a list of all detected threats and vulnerabilities, the risk of which is accepted by the user. In this subsection, you can cancel a risk acceptance or set the period during which a risk is considered accepted.
Administration
This section allows you to perform the following tasks:
- Under Access management, you can manage user access rights, define roles and access rights, and restrict access to resources and functional capabilities within specific scopes.
- Under Reports, you can view a list of generated reports on images, and download and delete reports.
- The Integrations subsection allows configuring integrations with public image registries, image signature validators, outputs, and the LDAP server, as well as getting integration status information.
- Under Events, you can view a list of application-generated events that may be useful when tracking processes and analyzing potential security threats.
Settings
This section allows you to perform the following tasks:
- Under Authentication, you can configure the settings for starting the Management Console for Kaspersky Container Security and manage the connection settings.
- The Licensing subsection allows you to manage licensing settings and view license functionality.
- The About subsection contains information about the version of the application and the latest update of the malware and vulnerabilities database. You can also view the terms and conditions of the Kaspersky Container Security License Agreement, Third party code information, and API reference as well as open the Kaspersky Container Security Help for a detailed description of the solution and its operation.
Block with the name of the current user
This block displays information about the user that logged in to the Kaspersky Container Security Management Console. Using the commands of the pop-up menu, you can go to the user profile page and exit the console.
Page top
Dashboard
On the main Kaspersky Container Security page, you can configure the dashboard to receive up-to-date analytical data on objects that are processed by the solution. This configuration is performed using filters that let you sort information by object and period.
Analytical data is displayed using widgets or specialized tools that show analytic information.
The Kaspersky Container Security dashboard opens when logging in to an account or when clicking the area containing the logo and name of the solution above the main menu.
Applying filters
Kaspersky Container Security provides the capability to configure the dashboard using the following filters:
- Filter by period:
- For the entire period
- For the year
- For the quarter
- For the month
- For the week
- For the past 24 hours
- For a customized period
For any period you select, the time count begins from the current day. By default, information is displayed for the week.
- Filter by resource:
- All images
- All images outside of clusters
- All images in clusters
- Images of a specific cluster
- CI/CD images
By default, information is displayed for all images.
Widgets on the dashboard
Kaspersky Container Security provides analytical data on the dashboard by using widgets that are organized into groups based on data type. The following widget groups and widgets are available in Kaspersky Container Security:
- Image compliance with security policy requirements. The solution displays the following information:
- Total number of images.
- Number of images with Compliant status.
- Number of images with Non-compliant status.
- Image risk assessment. The widget provides the following information on the statuses of objects:
- Total number of images.
- Number of images with the Critical status.
- Number of images with the High status.
- Number of images with the Medium status.
- Number of images with the Low status.
- Number of images with the Negligible status.
- Number of images with the Ok status.
- Top 10 object benchmarks that most frequently result in failure of cluster nodes to comply with the Kubernetes benchmarks:
- 10 cluster node benchmarks that most frequently result in non-compliance.
- Number of cluster nodes that failed the compliance check for the specified benchmark.
- Top 10 registries by number of images with the highest risk rating.
- Vulnerabilities
- Top 10 detected vulnerabilities with Critical, High or Medium severity status, and the number of images containing the specified vulnerability.
If a vulnerability contains an exploit, an exploit icon (
 ) is displayed next to the severity level. You can use the Show only Exploit toggle switch above the list of vulnerabilities to display all matching vulnerabilities or only vulnerabilities with exploits.
) is displayed next to the severity level. You can use the Show only Exploit toggle switch above the list of vulnerabilities to display all matching vulnerabilities or only vulnerabilities with exploits. - Top 10 images containing the maximum number of identified vulnerabilities with Critical and High severity status.
- Top 10 detected vulnerabilities with Critical, High or Medium severity status, and the number of images containing the specified vulnerability.
- Malware
- Top 10 most frequently detected types of malware and number of images containing this malware.
- Top 10 images with the maximum number of detected types of malware.
- Sensitive data:
- Top 10 detected types of sensitive data with Critical, High or Medium severity status and the number of images containing this sensitive data.
- Top 10 images containing the maximum amount of detected sensitive data with Critical and High severity status.
- Misconfigurations
- Top 10 detected misconfigurations with Critical, High or Medium severity status, and the number of images containing such sensitive data.
- Top 10 images with the maximum number of detected misconfigurations with Critical and High severity status.
Object lists that specify the severity level are sorted in descending order of severity (first items on the list are objects with the highest severity status).
User profile
To go to the user profile page:
- In the main menu, click on the block with the current user name.
- Select My Profile.
On the My Profile page, Kaspersky Container Security displays key information about the active user account. This information is divided into the following sections:
- General information—shows the user's name and their displayed user name, a contact email address, and a list of the roles assigned to the user.
In this section, you can also change the password to enter the Management Console by clicking the Change password button.
- API token—information about the token for connecting to and accessing the solution using API. The value of the valid API token is hidden by a mask and can be viewed by clicking the unmask icon (
 ) located to the right of the token. You can hide the token value with a mask by clicking the mask icon (
) located to the right of the token. You can hide the token value with a mask by clicking the mask icon ( ).
).In this section, you can also copy the value of the active token by using the Copy button. If necessary, you can also generate a new API token by clicking the Reissue token button.
- Permissions - all rights and permissions assigned to the user are displayed.
Specific ways to set up data display
Kaspersky Container Security interface provides the following ways to set up data displaying:
- Filtering: The filter fields are located above the data tables. Filter fields and ways to manage the filter depend on the specifics of the data to be displayed.
In some sections, you must click the filter icon to open the filter fields (
 ).
). - Sorting in ascending or descending order. In some sections, you can sort the list of data by the selected column by using the sort icon (
 ) in the column header.
) in the column header. - Search: You can search the displayed data by using the Search field, located above the table and designated by the search icon (
 ).
). - Menu. In some tables, you can perform actions on the objects using the menu commands in the table rows. To open the menu for the selected object, click the menu icon (
 ) in the object row.
) in the object row. - Select. In some tables, you can select items by clicking the check box (
 ). To unselect a check box, click the checkbox again.
). To unselect a check box, click the checkbox again. - Delete. You can delete objects in the solution by using the delete icon (
 ) or the Delete link that appears when selecting objects.
) or the Delete link that appears when selecting objects. - Expand or collapse lists. In some tables, you can click the expand icon (
 ) to expand an object row and view its contents. To collapse table elements, click the collapse icon (
) to expand an object row and view its contents. To collapse table elements, click the collapse icon ( ).
).
Licensing the solution
This section provides information about the general terms related to the licensing of Kaspersky Container Security.
About the End User License Agreement
The End User License Agreement is a binding agreement between you and AO Kaspersky Lab stipulating the terms on which you may use the application.
Please carefully read the terms of the End User License Agreement before you start using the application.
You can read the terms of the End User License Agreement during the Kaspersky Container Security installation.
By confirming that you agree with the text of the End User License Agreement during installation of the application, you signify your acceptance of the terms of the End User License Agreement. If you do not accept the terms of the End User License Agreement, you must cancel installation of the application and must not use the application.
Updates functionality (including providing anti-virus signature updates and codebase updates) might not be available in the software in the U.S. territory.
Page top
About the license
A license is a time-limited right to use Kaspersky Container Security as granted under the End User License Agreement.
A license includes the right to use the application in accordance with the terms of the End User License Agreement, and to receive technical support. The available functionality and application usage period depend on the type of license that was used to activate the application.
Kaspersky Container Security supports the following types of licenses:
- NFR (not for resale) is a free license for a specific period intended to familiarize the user with the application and to conduct test deployments.
- A Commercial license is a paid license that is provided when you purchase the solution.
Solution functionality depends on the type of license held. Kaspersky Container Security supports the following licenses:
- Standard license — allows for integration with image registries and platforms, security threat detection scans, risk assessment, and monitoring of object status.
- Enterprise license — in addition to the functionality of the standard license, this license also provides access to components used for the monitoring, control, and analysis of objects, misconfiguration detection and security threat protection.
When the license expires, the application continues to work but with limited functionality. For full Kaspersky Container Security functionality, you must purchase a commercial license or renew your commercial license.
Page top
About the license certificate
A license certificate is a document that you receive together with a key file or activation code.
The license certificate contains the following license information:
- License number or order number
- Information about the user who is granted the license
- Information about the application that can be activated under the provided license
- Restrictions on the number of licensing units (for example, devices on which the application can be used under the provided license)
- Start date of the license term
- License expiration date or license term
- License type
About the license key
A license key is a sequence of bits that you can use to activate and then use the application in accordance with the terms of the End User License Agreement. The license key is generated by Kaspersky experts.
You can add a license key to the application by either applying a key file or entering an activation code.
Kaspersky can block a license key over violations of the End User License Agreement. If the license key has been blocked, you have to add a different license key to continue using the application.
Page top
About the key file
A key file is a file with the KEY extension that you receive from Kaspersky. The purpose of a key file is to add a license key that activates the application.
You receive a key file at the email address that you provided when you purchased Kaspersky Container Security.
You do not need to connect to Kaspersky activation servers to activate the solution with a key file.
You can restore a key file if it has been accidentally deleted.
To restore a key file, do one of the following:
- Contact the license vendor.
- Get a key file from the Kaspersky website based on an available activation code.
About the activation code
An activation code is a unique sequence of 20 English letters and numbers. You must enter an activation code to add a license key that activates Kaspersky Container Security. Your activation code will be sent to the email address that you provided when you purchased Kaspersky Container Security.
To activate the application with an activation code, Internet access is required to connect to Kaspersky activation servers.
If you lose your activation code after activating the application, please contact the Kaspersky partner that you purchased the license from.
Page top
Application activation procedure
Application activation is the process of activating a license that grants the right to use Kaspersky Container Security until expiry.
You can activate the application by using the activation code or key file provided to you when you purchased the solution.
An activation code is used for activation when you install the solution in a public corporate network with Internet access. A key file is used for activation when you install Kaspersky Container Security in a public corporate network or private corporate network without Internet connectivity.
To activate the application with an activation code:
- In the Settings → Licensing section, click the Add license key button.
- In the window prompting you to select how you want to add the license key, select Enter activation code.
- In the Activation code field, enter the activation code and click Add.
The application is activated, and the license info page opens.
To activate the application with a key file:
- In the Settings → Licensing section, click the Add license key button.
- In the window prompting you to select how to add the license key, select Upload key file and click the Upload and add button.
- In the window that opens, select a file with the KEY extension and click Open.
The application is activated, and the license info page opens.
When activating the application, the new activation code or key file will replace the previously entered activation code or key file.
Page top
Viewing license information
You can view information about the active license in the Kaspersky Container Security web interface, in the Settings → Licensing section.
The license details page displays the following parameters:
- Licensing information. Kaspersky Container Security displays the following:
- Name of the Kaspersky partner that you purchased the license from.
- License term.
The term begins from the moment you purchase the license, not from the moment you activate the application.
- Customer information. This subsection provides data on the company that purchased the license:
- Company name
- Country where the company is located
- Email address of the customer representative
- Time period remaining until license expiration The solution displays the exact date and time of license expiration.
- Node count—maximum number of nodes and number of active nodes allowed by the license.
- Image scans per month—maximum number of image scans and completed scans allowed by the license. A month is considered to be the last 30 days (30 days from the current day).
- Functionality provided by the license. The solution displays a list of the available functionality under the license you purchased.
Renewing the license
When the license is approaching its expiration date, Kaspersky Container Security displays the following notifications:
- Notification that the license is expiring soon, indicating the time remaining until expiration. You receive this notification 30, 14, and 7 days before the license expires.
- Notification that the license is expiring and the solution will switch to limited functionality mode. This notification is sent on the day of license expiration.
In limited functionality mode, the functionality of Kaspersky Container Security is limited as follows:
- No new object scans are performed.
- The web interface does not display the new nodes added to the previously created clusters after the license expired.
- New clusters cannot be added for monitoring purposes.
- Vulnerabilities databases are not updated.
You can renew a license by applying a new activation code or by adding a new key file. To renew a license, contact the Kaspersky partner you purchased the license from.
Page top
Removing the license key
To remove the license key:
- In the Settings → Licensing section, click the Delete license key button.
- Confirm the removal by clicking the Delete button.
Data provisioning
This section contains information about the data that Kaspersky Container Security can save on the device and forward to Kaspersky during its operation.
If you use an activation code to activate Kaspersky Container Security, you agree to automatically provide information to Kaspersky as part of the regular license key status confirmation process. To confirm the license key status, Kaspersky Container Security periodically contacts Kaspersky activation servers and forwards the following information to Kaspersky:
- regional activation center identifier;
- title of the license to use the solution;
- checksum type and checksum of the license key;
- date and time when the license key was created;
- date and time when the solution license expires;
- solution license identifier;
- identifier of the information model applied when providing a license to use the solution;
- current license key status;
- license type used to activate the solution;
- unique device identifier;
- family name of the device operating system;
- solution installation identifier (PCID);
- identifier, localization, and full version of the solution;
- solution identifier obtained from the license;
- set of compatible software identifiers;
- solution rebrand identifier;
- list of legal agreements shown to the solution user;
- type and version of the legal agreement accepted by the user while using the solution.
In addition, by using the activation code, you agree to forward the following information to Kaspersky:
- activation code entered by the user to activate the solution;
- date and time on the user device;
- version, build number, update number, and revision of the device operating system;
- flag indicating that the user accepted the terms of the legal agreement while using the solution.
By using the activation code, you agree to automatically forward the data listed above to Kaspersky. If you do not agree to provide this information, use a key file to activate Kaspersky Container Security.
If you use Kaspersky update servers to download updates, you agree to automatically provide the following information:
- Identifier of the Kaspersky Container Security solution obtained from the license;
- full version of the solution;
- solution license identifier;
- type of valid license;
- solution installation identifier (PCID);
- Identifier of the solution update launch;
- processed web address.
Kaspersky can use all the obtained data to generate statistical information about the distribution and use of Kaspersky software.
Any received information is protected in accordance with legally established requirements and applicable Kaspersky regulations. Data is transmitted over encrypted communication channels.
More detailed information about the processing, storage, and destruction of information obtained during the use of the solution and transferred to Kaspersky is provided in the End User License Agreement and the Privacy Policy on the Kaspersky website.
Page top
Working with clusters
Kaspersky Container Security provides a tool for displaying and analyzing the connections between various objects within namespaces in clusters.
A cluster is a set of
that run applications placed in containers.By using clusters, you can perform bulk scans of images within those clusters. When doing so, the registries found in a cluster during a scan are automatically created. Kaspersky Container Security automatically reads and records the identification data used for accessing registries in a cluster (user name, password, token), and generates a link to this object. Registries are also assigned a name in the following format: <cluster name>_<registry name>. When working with cluster objects, the received identification data is used to access the registries.
Kaspersky Container Security displays a list of available clusters as a table under Resources → Assets → Clusters.
View the list of clusters
The Resources → Assets → Clusters section displays a table of clusters available in Kaspersky Container Security. The following data is provided for each cluster:
- Cluster name. Clicking the cluster name in the Cluster name column takes you to the page where you can view the namespaces in that cluster
- Number of namespaces included in the cluster
- Name of the orchestrator where the cluster is deployed
- Maximum risk rating. The maximum risk rating assigned to the cluster is based on the risk ratings for the images in that cluster
You can use sorting to rearrange the data in the table as follows:
- By cluster name: you can arrange clusters alphabetically in the Cluster name column in ascending (A to Z) or descending (Z to A) order.
- By number of namespaces - You can sort clusters in descending or ascending order of the number of namespaces in the Namespaces column.
- By orchestrator name: by sorting on the Orchestrator column, you can group clusters by the orchestrator where they are deployed.
- By maximum risk rating: you can arrange clusters in descending or ascending order of the maximum risk rating, displayed in the Max risk rating column.
You can view the namespaces in the cluster and the links between these by clicking View in the View on graph column. Kaspersky Container Security opens the namespace graph for the selected cluster.
Cluster resources can be scanned and visually represented only if deployed agents are available.
Namespaces in the cluster
To view the namespaces included in the cluster:
- Go to the Table tab under Resources → Assets → Clusters.
- In the Cluster name column of the table with the list of clusters, click the cluster name.
Kaspersky Container Security opens a page displaying a table with a list of namespaces in the selected cluster.
The following information is indicated for each namespace in the cluster:
- Namespace name. Clicking the link in the name of the namespace in the Namespace column takes you to the page where you can view the pods in that namespace.
- The number of containers in all pods in the selected namespace.
- Number of scanned images. The Scanned images column displays this information in X/Y format, for example: 1/8. The first value (X) represents the number of images scanned, and the second value (Y) represents the total number of images in the namespace.
- Number of images with the Queued status. The Scans in queue column displays the number of images in the jobs that are queued and waiting to be scanned.
- Number of images with the Error status. The Failed scans column displays the number of images whose scanning completed with an error.
- The maximum risk rating assigned to images in the namespace.
You can use sorting to rearrange the data in the table as follows:
- By namespace name: you can arrange objects alphabetically in the Namespace column in ascending (A to Z) or descending (from Z to A) order.
- In the ascending or descending order of the number of containers in the pods in the selected namespace.
- In the ascending or descending order of the number of images with the Queued status.
- In the ascending or descending order of the number of images with the Error status.
- By maximum risk rating: you can arrange namespaces in descending or ascending order of the maximum risk rating, displayed in the Max risk rating column.
You can view the objects in the namespace by clicking View in the View on graph column. Kaspersky Container Security opens the application graph of the selected namespace.
To view the namespaces in a cluster and the relationships between them,
go to the Graph tab under Resources → Assets → Clusters.
Page top
Pods in the cluster
To view a list of pods in a namespace:
- Under Resources → Assets → Clusters, open the table with a list of namespaces in the cluster.
- In the Namespace column, click namespace name.
Kaspersky Container Security opens a page that displays a table with a list of pods in the selected cluster.
The following is displayed for each pod in the selected namespace:
- Pod name.
- List of container names associated with the pod
- Name of the image the container was deployed from. By clicking the link in the image name, you can go to the page with the results of this image scanning under Resources → Assets → Registries.
- Status of compliance with security policy requirements
- Risk rating. Kaspersky Container Security displays the risk rating for the image specified in the Image column
- Number of security issues (vulnerabilities, malware, sensitive data, and misconfigurations) detected For vulnerabilities, the solution separately lists the number of security issues broken down by severity.
- Date and time of the last object scan
You can use sorting to rearrange the data in the table as follows:
- By pod name, container name, or image name: you can arrange objects in the Pod, Container and Image columns in ascending or descending alphabetical order.
- For compliance or non-compliance with security policies. Kaspersky Container Security can group objects in line with the Compliant and Non-compliant statuses.
- By risk rating: you can arrange objects according to the severity level.
- By date and time: Kaspersky Container Security can display objects starting with the earliest or latest by scan date and time.
Visualization of cluster resources
Kaspersky Container Security visualizes objects within one or more clusters, as well as the links between objects in a cluster and resources out of cluster or scope. Depending on the level of the cluster resources visualization, it displays the following:
- Namespace graph: represents the cluster and the namespaces in it.
- Application graph of the selected cluster: shows the cluster, its namespaces, and the applications of the expanded namespaces. The application graph can shown in maximum detail by expanding objects to the lowest level.
When working with cluster resource graphs, one must take into account the following specifics of object display:
- The number on the upper right of the object icon shows the number of lower-level objects within the specified object (child objects).
- Objects on the graph may be highlighted in color. The object is identified if it meets the parameters established regarding risk assessment and compliance with security policies.
- Objects on the graph are grouped according to the following rules:
- Highlighted objects are grouped together if their number is more than five.
- Unhighlighted objects are grouped together if their number is more than two.
- Objects on the graph can be hidden if needed.
A visual representation of cluster resources is generated if active agents exist for this cluster.
Page top
Cluster resources on a graph
Kaspersky Container Security scans and displays the resources of the cluster and the links between them. This scan is performed for all clusters with active agents.
Cluster resources are entities or objects that are stored in the orchestrator and used to represent the status of the cluster. With their help, you can get information about running containerized applications, where they are started (nodes), and the resources available to them. Cluster objects also define strategies for managing running applications (for example, restarting or updating).
In the interface of Kaspersky Container Security, the highest-level object (parent object) is the cluster. It includes namespaces in which applications are started. Applications, in turn, include pods and other objects.
A cluster is a set of physical or virtual machines (nodes) that run containerized applications. The following types of nodes are distinguished in Kubernetes:
- A master node implements API objects and is used to manage the cluster and its resources.
- A worker node is used to run the workload. A cluster includes one or more worker nodes.
Kaspersky Container Security displays the cluster as a graph using the cluster icon ( ).
).
Depending on the level of detail you want for the cluster resource display, Kaspersky Container Security displays the graph as a graph of namespaces or a graph of applications. The table below shows all objects that may be included in the cluster and are displayed on the graph.
Objects within the cluster
Object |
Icon |
Description |
|---|---|---|
Namespace |
|
A mechanism for isolating resources within a cluster. A namespace includes various objects necessary for an individual workspace (for example, Deployment, Service). Kaspersky Container Security can group namespaces on the graph and display such a group of objects with the number of entities in it indicated (for example, |
Pod |
|
An entity that includes one or more containers with shared network resources, as well as a set of rules for running containers included in the pod. |
Application |
|
A group of objects in the cluster that is conventionally considered as a single entity in Kaspersky Container Security. The application is formed from the following objects:
Individual pods do not form an application. They continue to function as part of a namespace and are displayed individually on the graph. |
Deployment |
|
An object that includes a set of rules that describe pods and the running of applications in them, the number of pod replicas, and the order in which they are replaced if their characteristics change. |
DaemonSet |
|
An object responsible for creating and running pods from the same image on all nodes of the cluster. In Kaspersky Container Security, a DaemonSet is used to deploy an agent (node-agent) on each node of the cluster to receive information and manage processes in pods. |
Ingress |
|
An object that provides external access to services in the cluster, usually over HTTP and HTTPS. |
ReplicaSet |
|
An object that manages pod replication. ReplicaSet maintains a certain number of identical pods. |
Secret |
|
An object for storing sensitive data (for example, a password, token, or key). Secret helps avoid storing such data in the application code. The Secret is created separately from the pods that use such objects to store sensitive data. This reduces the risk of secrets being revealed when creating, viewing, or editing pods. |
Service |
|
An object describing the network capabilities of applications in pods. Service combines pods into logical groups, forwards traffic to them, and balances the load among them. |
Endpoints |
|
A list of network endpoints that the Service object queries to determine which pods to direct traffic to. |
StatefulSet |
|
A workload object used for managing applications by keeping track of and saving their state. StatefulSet is used in applications that need:
|
ConfigMap |
|
An object for storing non-sensitive data in key-value pairs. ConfigMap is used in pods as an environment variable, command line argument, or configuration file within a volume. Using ConfigMap lets you separate environment-specific configuration settings from images in a container for better portability of your applications. |
Persistent volume (PV) |
|
A dedicated persistent resource (volume) for storing pod data in the cluster. PV is independent of pods, stores information contained in it and, when implementing multiple access, allows other pods to use this information. |
Persistent volume claim (PVC) |
|
A user-generated request to store data with persistent volume (PV) requirements. For example, a PVC can specify the size of the persistent volume required and the mode of access to data in it (for example, single read access or multiple read/write access). |
Namespace graph
To view the namespace graph for the selected cluster,
in the table with the list of clusters, click View.
Kaspersky Container Security displays the cluster with its namespaces.
Kaspersky Container Security can display information about the cluster and namespaces on the namespace graph in the sidebar or in a table. The sidebar provides a brief summary of the object. The table shows a more detailed security scan status for objects in the cluster. The data is partially duplicated between the sidebar and the table.
Page top
Viewing details about graph objects in the sidebar
To view cluster information in the sidebar:
- Click the cluster (
 ) or namespace (
) or namespace ( ) icon on the namespace graph.
) icon on the namespace graph. - In the menu that opens, select Details.
The details sidebar displays the following object-specific data:
- For a cluster:
- Cluster name.
- Number of namespaces in the cluster
- Cluster orchestration platform
- Maximum risk rating assigned to the objects in the cluster
- The security policy compliance status is Compliant or Not Compliant.
- For a namespace:
- Namespace name
- Number of containers and applications in the namespace
- Number of scanned images in the namespace
- Number of processed and failed scan tasks
- Maximum risk rating assigned to the objects in the cluster
- The security policy compliance status is Compliant or Not Compliant.
- Number of security issues across all risk types. For vulnerabilities, the number of security issues is specified, broken down by risk severity.
- For a cluster:
Viewing details about graph objects in the table
To view information about the objects on a graph in a table:
- Click one of the following icons in the namespace graph:
- Cluster (
 )
) - Namespace group (
 )
) - Namespace (
 )
)
- Cluster (
- In the menu that opens, select Open in table.
Kaspersky Container Security opens a table with information about the selected object or group of objects at the bottom of the work pane under the graph. Depending on the object, Kaspersky Container Security displays the following container details in the table that opens:
- For a cluster or a namespace group:
- List of namespaces in the cluster
- Number of containers in each namespace
- Number of scanned images, scan jobs in queue, and failed scan jobs for each namespace
- Maximum risk rating assigned to the objects in the cluster
- The security policy compliance status is Compliant or Not Compliant.
- For the selected namespace:
- List of applications in this namespace and their types.
- Number of pods and containers in each application.
- Maximum risk rating assigned to the objects in the namespace.
- The security policy compliance status is Compliant or Not Compliant.
- For a cluster or a namespace group:
You can also use the table to configure the way objects are displayed on the graph to hide or show namespaces.
Page top
Application graph
To view the application graph for the selected cluster:
- Go to Resources → Assets → Clusters.
- Do one of the following:
- On the Table view tab, open the table with the list of namespaces and click View.
- On the Graph view tab, open the namespace graph and do one of the following:
- Double-click to expand the namespace to applications.
- Click the namespace icon (
 ) to open a menu and select Expand on graph.
) to open a menu and select Expand on graph.
Kaspersky Container Security displays all applications in the selected namespace.
Each application can be expanded down to the pod level. You can view detailed information about the following objects on the application graph of the selected cluster:
Viewing information about application
To open information about an application in the application graph,
Click the application icon ( ) to open a menu and select Details.
) to open a menu and select Details.
Kaspersky Container Security opens a side panel with detailed information about the application.
The solution displays the following information about the application:
- The object type and application type (for example, Application: Deployment).
- Application name.
- Maximum risk rating. The solution assigns a risk rating to the application according to the highest severity level of all the objects within that application.
- The security policy compliance status is Compliant or Not Compliant.
- The Containers tab contains the following information about the containers in the selected pod:
- Name of the container.
- Name of the image the container was deployed from.
- The security policy compliance status is Compliant or Not Compliant.
- Maximum risk rating assigned to containers in the pod.
- Number of security issues across all risk types. For vulnerabilities, the number of security issues is specified, broken down by risk severity.
- Date and time of the last scan of the image from which the container was deployed.
- The Policies tab displays information about assurance policies and runtime policies that are applied to the application.
The following information is provided in the Assurance policies section:
- Policy application status (Passed/Failed).
- Policy name.
- Indication of existing security threats. In terms of the applied policy, the scan results can be displayed as follows:
- Scan was performed, security threats were identified (
 ).
). - Scan was performed, no security threats were detected (
 ).
). - No scan was performed for this type of security threat (
 ).
).
- Scan was performed, security threats were identified (
The Runtime policies section contains the following information:
- Policy name.
- Policy application mode (Audit/Enforce).
By clicking the link on the name of a policy in the Policies tab, you can view its detailed description. The sidebar displays the following information:
- Policy type and name.
- Description of the policy (if any).
- Author of the policy.
- Mode (for runtime policy).
- List of predefined scopes.
- Actions that are performed when the policy is applied (for an assurance policy).
- Set benchmarks and their parameters.
You can edit the settings of an assurance policy by clicking the Edit policy button.
To view the detailed description of policies, you must have rights to view them. Policy management rights are required to make changes to policy settings.
Viewing information about objects in the application
To open information about objects on the applications graph:
- On the applications graph, select the application about whose objects you want to obtain information and do one of the following:
- Double-click the application to expand it to its constituent objects.
- Click the application icon (
 ) to open a menu and select Expand on graph.
) to open a menu and select Expand on graph.
- Select the object of interest and double-click to expand its information in the side panel.
Kaspersky Container Security opens a side panel with detailed information about the selected object.
Depending on the type of the object, additional information about the selected entity is displayed. The table below describes the set of information that the solution displays for various objects in the application.
Information about objects in the application
Object |
Displayed object data |
|---|---|
Deployment |
|
DaemonSet |
|
Ingress |
|
Secret |
|
ReplicaSet |
|
Service |
|
Endpoint |
|
StatefulSet |
|
ConfigMap |
|
Persistent volume |
|
Persistent volume claim |
|
You can generate and download a file with the description of the object current state in the .YAML format for all objects by using the Download .yaml button.
Page top
Viewing information about pod
To open the pod information,
on the graph, select the pod about which you want to receive information, and double-click to expand its information in the side panel.
Kaspersky Container Security displays pods on all types of graphs: namespace graphs and application graphs.
The solution opens a side panel with detailed information about the pod.
Kaspersky Container Security displays the following information about the pod:
- Object type.
- Maximum risk score among pod images.
- The security policy compliance status is Compliant or Not Compliant.
- Pod name.
- The General tab contains the following information about the object:
- Date and time of creation.
- Labels.
- Pod running status.
- Pod lifetime—the period between the date and time of viewing the pod information and the date and time of its creation.
- List of ports used by pod containers in the following format: <
"port name" port protocol>. For example,"dns" UDP 53. - Available system functions of the pod.
- The name of the PV used by the pod.
- The name of the PVC used.
- The name of the application, namespace and cluster within which the pod is located.
Also in this tab, you can click Download *.yaml to generate and download a file with a description of the pod.
- The Containers tab contains the following information on containers within the pod:
- Name of the container.
- Name of the image the container was deployed from.
- Compliance status of the deployed image: Compliant or Non-compliant.
- Maximum risk rating of the deployed image.
- Number of security issues across all risk types. For vulnerabilities, the number of security issues is specified, broken down by risk severity.
- Date and time of the last scan of the image from which the container was deployed.
- List of ports used by pod containers in the following format: <
"port name" port protocol>. - Additional properties of the container—it is an .
- The Policies tab displays information about assurance policies and runtime policies applied to the pod. Information about policies applied to the pod is presented in two sections (Assurance policies and Runtime policies), similarly to the information displayed about the applicable policies when viewing information about the application on the graph.
To view the detailed description of policies, you must have rights to view them. Policy management rights are required to make changes to policy settings.
Viewing details about application graph objects in the table
To view information about the objects on the application graph as a table:
- Do one of the following:
- Click the namespace icon (
 ) that indicates the number of applications within the namespace on the graph.
) that indicates the number of applications within the namespace on the graph. - Click the icon of the application group within the namespace (
 ).
).
- Click the namespace icon (
- In the menu that opens, select Open in table.
The solution opens a table with information about applications in the lower part of the workspace below the graph. Kaspersky Container Security displays the following information:
- The list of applications in this namespace and their types (types of parent objects).
- Number of pods and containers in each application.
- Maximum risk rating assigned to the objects in the namespace.
- The security policy compliance status is Compliant or Not Compliant.
Highlighting objects on the graph
To highlight objects on the graph:
- Click the Highlight objects button above the graph.
Kaspersky Container Security opens a sidebar where you can configure the settings for highlighting objects.
- Select the check boxes to specify values for the following settings:
- Risk rating. You can select one or several risk severity levels (Critical, High, or Medium). If the check boxes are not selected, objects on the graph are not highlighted.
The check boxes for the Critical and High values are selected by default.
- Compliance If the Non-compliant check box is selected, Kaspersky Container Security highlights objects that do not comply with applicable security policies. If this check box is not selected, objects on the graph will not be highlighted, regardless of their compliance or non-compliance with standards.
Non-compliant is specified by default.
- Risk rating. You can select one or several risk severity levels (Critical, High, or Medium). If the check boxes are not selected, objects on the graph are not highlighted.
- Click Apply.
Kaspersky Container Security updates the graph and displays the objects according to your settings.
For each user, the solution saves the highlighting settings that the user has specified and applies them when displaying cluster objects that this user opens later.
Configuring visibility of objects on the graph
By default, Kaspersky Container Security displays all namespaces in the cluster on the graph. If necessary, you can hide namespaces if these namespaces and objects in them are not relevant to you for a specific analytical task.
You can configure graph object visibility:
- On the graph
- In the table with information about the child object
To hide a namespace with the help of the graph:
- Click the object icon on the graph.
- In the menu that opens, select Hide.
Kaspersky Container Security updates the graph and hides the object.
You can restore object visibility with the help of the table with detailed information about the parent object or group of objects.
To configure namespace visibility with the help of the table:
- In the table with namespaces as part of the column, select one or more objects for which you want to change the visibility settings.
- Use the buttons above the table to do one of the following:
- To display the object on the graph, click Show on graph.
- To hide the object on the graph, click Hide on graph.
Kaspersky Container Security updates the graph and displays the objects according to your settings. The Data display column indicates whether the object is shown or hidden on the graph.
Network processes on the graph
Kaspersky Container Security displays network interactions between objects on the graph, and also provides information about network activity between cluster resources.
To view network activity in the cluster:
- In the Resources → Assets → Clusters section, go to the Graph view tab.
- Click Show network activity above the graph area.
The solution opens the sidebar with the types of network activity available for display.
- By selecting check boxes, select one or more network activity display options. You can select the following display options:
- Show audited activity. This displays network connections that were detected in accordance with the applied runtime policies in Audit mode.
- Show blocked activity. This displays network connection attempts that were blocked in accordance with the applied runtime policies in Enforce mode.
- Show other activity. This displays network connections that were not covered by the applied runtime policies in Audit and Enforce modes.
- Click Apply.
The graph is reloaded and the selected network activity is displayed.
Principles of displaying network processes
The following principles apply to the display of network connections on the graph in Kaspersky Container Security:
- The solution displays processes as edges between two objects (groups of objects within a cluster), or between an object (group of objects) and resources outside the cluster. An arrow on the graph points from the sender object to the recipient object. If the same types of network activity (for example, audited activity) occurs between a pair of objects that are linked by a network connection and the traffic between the object goes both ways, the solution represents this activity with a bidirectional arrow.
- If the recipient object is outside the relevant cluster, infrastructure or the scope assigned to the user, the solution indicates it as Resources out of cluster or scope.
- The graph displays network connections to a group of namespaces or applications if inbound or outbound traffic is detected involving at least one object inside such a group. When you expand a group to its constituent objects, the connection is displayed to the specific resource.
- If multiple network processes go from one object to another, the solution takes the priority of network activity when displaying them. Blocked activity has the maximum priority, and other activity has the minimum priority.
The solution displays different types of network activity as follows:
- Blocked activity on the graph is represented by a dotted red line (
 ).
). - Audited activity on the graph is represented by a solid red line with an arrow (
 ).
). - Other activity on the graph is represented by a solid black line with an arrow (
 ).
). - Two-way network activity is represented on the graph as a line corresponding to one of the activity types, with arrows on both ends (
 ).
). - If you hover over a network connection line on the graph, it is highlighted and changes color (
 ).
).
Viewing information about network processes
Kaspersky Container Security can provide brief and detailed information about network activity.
To view brief information about network activity:
Hover over the network connection of interest.
A tooltip is displayed with the number of non-unique connections for each type of network activity (blocked, audited, and other).
To view detailed information about network activity:
Click the connection of interest.
This opens the sidebar with information about network activity for the selected connection.
The sidebar displays information about network activity for the 15 minutes before the sidebar was called up. Network activity information is presented in tables on the Audited activities, Blocked activities, and Other activities tabs. The number of connections is indicated next to tab captions.
The tables have the same structure and contain the following information:
- The Source column contains the name of the pod that is the sender of the network traffic and the IP address of the pod in the
<pod IP address:outbound traffic port>format. You can click the link in the pod name to open a detailed description of the pod. - The Protocol column indicates the pod interaction protocol.
- The Destination column contains the name of the pod that is the recipient of the network traffic and the IP address of the pod in the
<pod IP address:inbound traffic port>format. You can click the link in the pod name to open a detailed description of the pod. - The Number of connections column displays the total number of non-unique connections between the sender and the recipient of the traffic.
- The Last connection column displays the date and time of the last non-unique connection between the sender and the recipient of the traffic.
If the sender object or the recipient object is outside the relevant cluster, the Source or Destination columns display the domain name and IP address of such an object respectively (if the solution can obtain this information).
Displaying the graph subject to applicable scope
When displaying cluster resources on the graph, the scope assigned to the user role is taken into account. In this case, the following must be considered:
- If the global scope is assigned to the user role, the graph displays all cluster resources.
- If a scope with access to a specific image within the namespace is assigned to the user role, the graph displays the entire namespace (all entities in the namespace are displayed).
- If a scope that does not have access to specific namespaces is assigned to the user role, such namespaces are not displayed on the graph.
If there are no namespaces to display for the selected cluster in view of the assigned scope, the solution informs you that is no data to display.
Setting up integration with external image registries
Kaspersky Container Security can scan images from the following external image registries:
- Harbor
- GitLab Registry
- JFrog Artifactory
- Sonatype Nexus Repository OSS
- Yandex Registry
- Docker Hub
- Docker Registry
You should integrate Kaspersky Container Security with external registries containing images to be scanned. Images from registries integrated with Kaspersky Container Security can be scanned automatically or manually, depending on the configured image pulling and scanning settings for each registry.
Minimum sufficient rights for integration with registries
To integrate with external image registries, a Kaspersky Container Security account must have a certain set of rights, which differs depending on the registry type. The list of the minimum account rights required for integration is given below for each registry type.
GitLab
To integrate the solution with a GitLab user's registry, you should define the parameter values as follows:
- User role in the project or group: Reporter.
- Level of access to the project: Reporter.
- Rights assigned to the user token: read_api, read_registry.
JFrog
To integrate the solution with a JFrog user's registry, you need to define the parameter values as follows:
- User role in the project or group: Manage Reports.
- Project access: Can Update Profile.
- User rights: the right to read any repository (ANY repository).
Harbor
To integrate the solution with a Harbor user's registry, you should define the parameter values as follows:
- Member type: user. To do this, specify User in the Member Type column of the table in the Projects → Members section.
- User role in the project or group: user with limited rights. To do this, you must specify Limited Guest in the Role column of the table in the Projects → Members section.
- User rights: user without administrator rights. To do this, in the Administrator column of the table in the Users section, select No.
Nexus
To integrate the solution with a Nexus user's registry, you should define the parameter values as follows:
- User role in the project or group: user.
- Rights assigned to the user role in the project or group: nx-apikey-all, nx-repository-view-docker-*-browse, nx-repository-view-docker-*-read.
Docker Hub
The solution integrates with a Docker Hub user's registry after authorization using the user name and password.
This Docker Hub registry integration option only applies to a personal namespace.
Working with public registries without authorization
Kaspersky Container Security 1.2 does not work with public registries without authorization. For example, you cannot use the solution to scan images when Docker Hub is accessed anonymously.
If you do not authorize in public registries, you can use such image registries in a cluster, add them to Kaspersky Container Security and manually assign them to a specific scope. If the scope includes only one or several public registries for which you are not authorized, and you try to add an image in the Resources → Assets → Registries section, the solution displays an error indicating that it is impossible to add images as the solution is not integrated with image registries.
Page top
Adding integrations with external image registries
Integrated registries support only local image repositories that directly contain the images. In version 1.2, Kaspersky Container Security does not support working with remote or virtual repositories.
To add an integration with an external registry:
- In the Administration → Integrations → Image registries section, click the Add registry button.
The integration settings window opens.
- On the Registry details tab, specify the settings for connection to the registry:
- Enter the name of the registry.
- If required, enter a description of the registry.
- Select the registry type from the drop-down list. Kaspersky Container Security supports the following types of registries:
- Harbor (integration using the Harbor V2 API).
- GitLab Registry (integration using the GitLab Container Registry API).
- JFrog Artifactory (integration using the JFrog API).
- Sonatype Nexus Repository OSS (integration using the Nexus API).
- Yandex Registry (integration using the Yandex Container Registry API).
- Docker Hub (integration using the Docker Hub API).
- Docker Registry (integration using the Docker V2 API).
The Docker Registry can be accessed using the Docker V2 API if you are configuring integration with the Sonatype Nexus Repository OSS, Harbor, JFrog Artifactory (using a port or a subdomain), or Yandex Registry. Integrations with GitLab Registry, Docker Hub, and JFrog Artifactory (via Repository Path) are not supported.
- If you set up a JFrog Artifactory registry integration, select one of the following methods in the Repository Path method drop-down list to access Docker:
- Repository path.
- Subdomain.
- Port.
- If you configure an integration with such registry as JFrog Artifactory, Harbor, GitLab Registry, Sonatype Nexus Repository OSS, or Docker Registry, enter the full registry web address (URL) that directly leads to the container registry. We recommend that you use HTTPS connection (HTTP connection is also supported).
If you use HTTP or HTTPS with a self-signed or invalid certificate, you should check the insecure-registry box for the Docker engine on the nodes where the server and scanner are installed.
- If you configure an integration with such registry as JFrog Artifactory, Harbor, GitLab Registry, and Sonatype Nexus Repository OSS, enter the full web address (URL) that leads to the registry API.
- Select an authentication method and specify the necessary data for it as follows:
- If you configure an integration with such registry as GitLab Registry, select authentication using an account or an access token.
- If you configure an integration with such a registry as Yandex Registry, select authentication using an API key (Yandex OAuth token) or using a user name and token. Specify oauth for the user name when using the Yandex OAuth token, or iam when using the Yandex IAM token.
- For such registries as Sonatype Nexus Repository OSS and Docker Hub, authentication is performed only with an account.
- For such a registry as Harbor, authentication is only permitted with an account of a user or a robot.
- For such a registry as Docker Registry, authentication is only conducted using a user name and password, which are provided by the Docker V2 API.
- Go to the Image scan details tab and specify the scan timeout for scanning images from this registry (in minutes).
If image scanning lasts longer than the specified time, the scanning stops and the image is returned to the scanning queue. The solution will requeue the image up to 3 times. This means that the time required to scan an image from the registry may be tripled.
- Configure the image pull and scan settings for the registry. By default, the Manual option is selected in Pull and scan images: images are not automatically pulled from the registry, but the user can manually add images to the list of images for scanning. New images are automatically queued for scanning.
If you want images to be pulled from the registry and queued for scanning automatically, select Automatic in Pull and scan images and configure the settings for image pulling and scanning. The following options are available:
- Scan timeout—a block of settings that determine the frequency at which images are pulled from the registry for scanning. The time is specified in accordance with the time of the node on which the Kaspersky Container Security Server is deployed.
- Rescan images—if you check this box, images that were previously pulled from the registry are rescanned each time new images are scanned.
- Name/tag criteria—you can use name criterion and/or image tag pattern to specify which images to pull and scan. If you check the box, Kaspersky Container Security will only pull those images that match the specified patterns for scanning.
You can use criteria in the following patterns:
- by image name and tag – <name><:tag>
- by image name only – <name>
- by image tag only – <:tag>
For example:
- for the
alpinepattern, all images with the name "alpine" are pulled, regardless of the tag; - for the
4pattern, all images with tag 4 are pulled, regardless of the image name; - for the
alpine:4pattern, all images with the name "alpine" and tag 4 are pulled.
When generating criteria, you can use the * character, which replaces any number of characters.
To add a criterion, enter it in the field and click the Add button. You can add one or more criteria.
- Additional conditions for image pulling.
- If no additional conditions are required, select No additional conditions.
- Images created within – select this option if you want to only pull images created within a specific period (for a specified number of days, months, or years). Specify the duration of the period and the unit of measurement in the fields on the right. By default, the period is 60 days long.
- Latest - select this option if you want to only pull images with the latest tags (from the date of the image creation). In the field on the right, specify the number of latest tags to consider.
- Never pull images with the name/tag pattern - using image name/tag patterns you can specify, which images are excluded from pulling and scanning.
- Always pull images with the name/tag pattern—using image name/tag patterns you can specify, which images are always pulled and scanned, regardless of other conditions set above.
- Click Test connection to see if a connection with the registry can be established.
- Click the Save button in the top of the window to save the registry integration settings.
Viewing information about integrations with registries
You can view a table with the list of all registries integrated with Kaspersky Container Security in the Administration → Integrations → Image registries section.
The table displays the following information about integrated registries:
- Name of the image registry integration
- Description, if one was specified when creating the integration with the image registry
- The type of the connected registry: Docker, Harbor, GitLab, JFrog, or Nexus
- Registry URL
- Status of the last connection with the image registry: Success or Error. If Error is displayed, the solution also displays a brief description of the connection error.
In the table, you can:
- Add new registry integrations. Click Add registry above the table to open the integration settings window.
- View and modify registry integration settings, including image pull and scan settings. You can open the editing window by clicking the registry name link.
In this window, you can also click Test connection to see if a connection with the registry can be established.
- Delete integrations with registries.
Deleting integration with external registry
To delete an integration with an external registry:
- In the Administration → Integrations → Image registries section, select the integration you want to delete by selecting the check box in the row with the registry name. You can select one or more integrations.
- Click Delete above the table.
The Delete button becomes enabled after you select one or more integrations.
- In the window that opens, confirm the deletion.
Kaspersky Container Security does not scan images from a registry it is no longer integrated with.
Page top
Harbor integration
Integration of Kaspersky Container Security with the external Harbor registry can be performed in two ways:
- In the same way as integration with other external registries
- Upon the request of the external Harbor registry
Harbor views the solution as an additional external scanner to scan objects for vulnerabilities. Integration with Kaspersky Container Security is configured using the Harbor scanner plugin. The solution names this automatically created image registry as Harbor External Integration and marks the repository in which it is located with the Harbor icon ( ).
).
This integration remains the only automatically created integration with Harbor, and the name assigned to the image registry cannot be changed.
To start the Harbor scan process, you need to know the endpoint of the Kaspersky Container Security API.
To create an integration by Harbor request it is required to have rights to view and configure scanning in CI/CD. If these rights are absent, Harbor will not be able to connect the solution as a scanner and scan objects as part of the CI/CD process.
Page top
Creating an integration upon Harbor request
To create registry integration by Harbor request, you must have a Harbor account with administrator rights, as well as rights to view and configure scanning in CI/CD in Kaspersky Container Security. If these rights are not available, Harbor will not be able to connect the solution as a scanner.
To create a Harbor integration upon Harbor request:
- From the main menu in the left pane of the Harbor web interface, select Administration → Interrogation Services.
- Click the New Scanner button.
- Enter the following information:
- The unique name of the solution integration to be displayed in the Harbor interface.
- If necessary, a description of the external scanner that is being added.
- The address of the Kaspersky Container Security API endpoint displayed by Harbor.
- In the Authorization drop-down list, select APIKey as the authorization method when connecting the registry to the solution.
- In the APIKey field, enter the value of the API token.
If the API token changes, you must specify its new value before starting the Harbor scan. If a new API token is not added to the external scanner settings in Harbor, the scan fails.
- Select the Skip certificate verification check box to skip certificate verification.
- If necessary, click Test Connection to verify that Harbor can connect to the solution.
- Click Add to create the integration.
In the list of available scanners under Administration → Interrogation Services → Scanners, Harbor shows the name assigned to the solution in the Harbor.
The new scanner is used for scanning objects if it is specified as the default scanner in Harbor or assigned to the project. Both options require additional configuration in Harbor.
After scanning is started, an integration with the solution upon Harbor request is created in the external registry. Kaspersky Container Security displays the created Harbor External Integration registry in the list of image registries in the Administration → Integrations → Image registries section. The repository containing images from the external registry is marked with the Harbor icon ( ). Harbor External Integration is updated after starting and running another scan in the external registry.
). Harbor External Integration is updated after starting and running another scan in the external registry.
You cannot add an image to an automatically created registry of images from Harbor by using the Add images button in the management console.
Harbor External Integration scans can be manually initiated or automatically started from the external registry. You cannot start scanning or rescanning images from the Harbor automatically created image registry in Kaspersky Container Security.
The Harbor External Integration registry (as well as the registry created as part of the standard integration with Harbor) is scanned in line with the applicable scanner policy.
At the end of the scan, the solution generates a report on vulnerabilities found during scanning of selected objects and sends it to Harbor. If sending a report takes more than five seconds (for example, because of the quality of the network connection), an error in receiving scan results is displayed in the external registry interface.
Page top
Viewing and editing the Harbor External Integration settings
The Harbor External Integration image registry is displayed in the list of registries integrated with Kaspersky Container Security in the Administration → Integrations → Image registries section.
To change the Harbor External Integration settings:
- Select the Harbor External Integration registry in the list of image registries in the Administration → Integrations → Image registries section.
- Specify the values of the following configurable settings:
- Description on the Registry details tab.
- Scan timeout on the Image scan details tab.
You cannot change other Harbor External Integration registry details.
- Click Save.
Rescanning
After receiving the scan results, objects from the Harbor External Integration registry cannot be sent for rescanning from Kaspersky Container Security. Rescanning can only be initiated from Harbor.
If you create an integration with Harbor from Kaspersky Container Security and the created image registry is similar to Harbor External Integration, the following rules are applied to rescanning:
- Scanning objects in the registry created in the solution does not trigger a rescan in Harbor External Integration.
- Scanning objects in Harbor External Integration does not trigger a rescan in the registry created in the solution.
Working with images from registers
The Resources → Assets → Registries section contains a list of images scanned by Kaspersky Container Security and the image scan results. The list includes images from registries integrated with Kaspersky Container Security. You can add images to the list automatically or manually.
The list of images is empty until you configure integration with registries and settings for pulling and scanning images for the registry in the Administration section.
The list of images is displayed as a table, the images are grouped by repositories.
You can perform the following actions in the Resources → Assets → Registries section:
- Search for images by name or checksum.
A search is conducted only in the selected active image registry. If the sought image is absent from the selected registry but is part of a different registry, the search gives no results.
- Filter the list to display images that match the specified criteria:
- Images only from the specified registries;
- Images that comply with or fail to comply with benchmarks;
- Images scanned during a specified period of time;
- Images for which the specified risks are identified.
- Start rescanning of the specified images (the Rescan button is displayed above the table after you select one or more images).
- Generate reports on selected images (the Create report button is displayed above the table after you select one or more images).
- Add images to the list and remove images from the list.
- View detailed information about the image scanning results.
Adding and removing images
Images from the registries integrated with Kaspersky Container Security can be added to the list of images automatically, in line with the configured settings for pulling and scanning images for each registry. You can also add images to the list of images from registries manually. New images are queued for scanning.
To manually add images to the list:
- In the Resources → Assets → Registries section, do one of the following:
- Select a repository from the list, open the action menu located to the right of the repository name, and select Add images.
- Click the Add images button above the table.
You cannot add images to an image registry that is created at the request of the external Harbor registry.
- Do one of the following:
- If you add images from the selected repository, select the required image tags in the window that opens and click the Add images button.
- If you add images using the Add images button above the table, in the window that opens, select a registry, a repository, one or more images and click the Add images button.
To optimize the load on image registries, a list of images in the connected registries is generated every 10 minutes. After a new image appears in the registry, its appearance in the Kaspersky Container Security interface may be delayed by the specified period.
To remove images from the list:
- In the Resources → Assets → Registries section, do one of the following:
- Select one or more images that you want to remove from the list and start removal using the Delete link located above the table.
- In the list, select the repository of images you want to delete, open the action menu on the row with the repository name, and select Delete repository.
- In the window that opens, confirm the deletion.
Viewing image scanning results from registries
Summary information about the scan results of all images in the repository and each specific image is displayed in the list of images in the Resources → Assets → Registries section.
Click the image name link to open a page with detailed information on image scanning results.
The tabs at the top of the window contain the following information:
- The Risk tab provides a summary of the scanning results. If threats are detected during scanning, recommended actions to protect the image are available at the bottom of the page. Click the Rescan image button to repeat scanning of the image.
- The Vulnerabilities tab shows the vulnerabilities detected in the image. Clicking the link in the name of the vulnerability can open a detailed description of the vulnerability and find out if it has an .
Kaspersky Container Security receives a description of vulnerabilities from the connected vulnerabilities database. The description is provided in the language of the vulnerabilities database. For example, a description of vulnerabilities from the NVD is displayed in English.
The classification of vulnerabilities in the solution matches the classification used in the connected vulnerabilities database. - The Layers tab displays layers used in the image with the specification of identified vulnerabilities. Click the layer name link to open a detailed description of the identified vulnerabilities.
- The Resources tab demonstrates resources (components) with the specification of identified vulnerabilities. Click the resource name link to open a detailed description of the identified vulnerabilities.
- The Malware tab lists malware detected in the image. Click the malware name link to open a detailed description.
- The Sensitive data tab shows sensitive data (secrets) found in the image such as passwords, access keys, or tokens.
- The Misconfigurations tab displays detected image misconfigurations that constitute a threat. Click the misconfiguration name link to open a detailed description.
- The Information tab provides the basic information about the image and image history.
- The Scan history presents the latest scan results for each version of the image. The results are updated if the same version of an image is scanned, or they are added in a separate row of the table if a different version of the image is scanned.
The following information is displayed for each image:
- Status of compliance with security policy requirements
- Risk rating with an indication of the risk severity level.
- Date and time of the last scan.
The number of objects containing vulnerabilities, malware, sensitive data, and misconfigurations in the image. For vulnerabilities, the number of objects is indicated separately for each identified risk severity level.
- The results of image scanning using the appropriate security policies within the current scopes.
If an image is included in the registry of images created during integration with the solution by Harbor request, the solution indicates this and marks the image with the Harbor icon ( ).
).
By clicking the Create report button, you can generate a detailed report on images. You can also initiate a rescanning of the image by clicking the Rescan button.
Rescanning is not available for images received by Kaspersky Container Security from the image registry created during integration with the solution by Harbor request.
You can accept each identified risk.
Page top
About risk rating
A scan conducted by Kaspersky Container Security results in rating a risk of the scanned object. While scanning, the solution may detect all or some of the following security issues in objects:
- Vulnerabilities
- Malware.
- Sensitive data.
- Misconfigurations
Each risk detected is assigned one of the following risk ratings, based on the severity of the security threats:
- Negligible.
- Low.
- Medium.
- High.
- Critical.
If no security issues are detected during scanning, such an image is considered secure and is marked as Ok.
Risk ratings of the detected vulnerabilities, malware, sensitive data, or misconfigurations correspond to the ratings specified in the security threat databases, which are used for scanning (for example, NVD, VDB). These vulnerability and threat databases use special scoring scales to assess the severity of security threats. For example, the Common Vulnerability Scoring System (CVSS) is applied in the NVD.
The object is assigned the highest severity level of all the detected with an appropriate risk rating.
For example, the following security threats were detected during an object scan:
- vulnerabilities with the low level of severity;
- sensitive data with the high and critical levels of severity;
- configuration errors with the medium severity level;
- malware with the low severity level.
Here, the risk rating is critical in accordance with the highest severity level of the detected threats.
Page top
Detailed information about detected vulnerabilities
To view detailed information about vulnerabilities detected in an image:
In the window with image scan results, select the Vulnerabilities tab.
The list of vulnerabilities detected during image scanning is presented as a table with the following information provided for each vulnerability:
- The Vulnerability column contains the ID of the vulnerability entry. The identifier is given in the CVE-YYYY-X... format, where:
- CVE is a prefix that indicates that the vulnerability is included in the database of known vulnerabilities and security defects.
- YYYY is the year when the vulnerability was reported.
- X... is the number assigned to the vulnerability by authorized bodies.
- The Severity column specifies the severity level of a vulnerability based on its risk rating.
If a vulnerability contains an exploit, an exploit icon (
 ) is displayed next to the severity level.
) is displayed next to the severity level. - The Resource column indicates the installed containerized resource in which the vulnerability was detected.
You can accept the risk of the vulnerability by clicking the Accept button in the Risk acceptance column.
To view detailed information about a vulnerability detected in an image:
- Do one of the following:
- In the window with the image scan results, go to the Vulnerabilities tab and click the link with the vulnerability entry ID in the Vulnerabilities column of the table.
- In the Vulnerabilities section on the dashboard, click the link with the vulnerability record ID.
- This opens the sidebar with the following information about the detected vulnerability:
- Vulnerability entry identifier
- Description of the vulnerability from the vulnerability database. The description is provided in the language of the vulnerabilities database. For example, descriptions of vulnerabilities from the NVD are displayed in English.
- The General information tab displays the following:
- Vulnerability severity level
- Installed resource in which the vulnerability was detected.
- Vulnerability severity score based on the open standard in the , , and vulnerability databases, as well as the final consolidated vulnerability severity score.
On this tab, you can accept the risk of the vulnerability by clicking Accept.
The Accept button is not displayed and risk acceptance is not possible when the sidebar is open on the dashboard.
- The Scan details tab displays the following:
- Image in which the vulnerability was detected
- Operating system that was scanned
- Date and time when the vulnerability was first detected
- Date and time of the last time the image was scanned
- The Workloads tab displays a list of detected workloads and the number of workloads.
Detailed information about detected malware
If image scanning detects malware, the solution displays this on the page with information about the image scan results. To view detailed information about a detected malicious object, in the window with image scan results, select the Malware tab.
For each object, the solution generates the MD5 or SHA256 hash and indicates the path to the location where it was detected.
You can view detailed information about detected malicious objects in the cyberthreat databases created in
and . To do this, click the link to Kaspersky OpenTIP and Kaspersky TIP resources.A page with a threat description on the Kaspersky OpenTIP portal is publicly available. Users must enter their account credentials to access Kaspersky TIP.
Scanning Java packages in images
Kaspersky Container Security can scan Java packages contained in registry images. For this purpose, the solution uses Java vulnerability databases.
Scanning for Java packages is available in Kaspersky Container Security v1.2.1 and later. If you have an earlier version installed, you must update the solution to v1.2.1. to use this functionality.
You can configure scanning of Java packages by setting the value of the ENABLE_JAVA_VULN environment variable in the values.yaml file. If ENABLE_JAVA_VULN = true, Kaspersky Container Security performs scanning using the Java vulnerability databases. If ENABLE_JAVA_VULN = false, Java packages are not scanned.
By default, ENABLE_JAVA_VULN is set to false.
The kcs-updates component v1.2.1 provided in the distribution kit contains Java vulnerability databases. Using this component, you should make sure that the environment variables in the values.yaml file are defined as follows:
ENABLE_JAVA_VULN = true
KCS_UPDATES_TAG=v1.2.1
KCS_UPDATES=true
If Java packages scanning is activated (ENABLE_JAVA_VULN = true), the kcs-scanner solution component downloads Java vulnerability databases and notifies the kcs-middleware and kcs-ih components accordingly. Then the kcs-ih component receives the database files from kcs-scanner, assembles and validates the database, and uses it during scanning.
Vulnerabilities found using the Java vulnerability database are displayed in the image scanning results.
Kaspersky Container Security can also scan Java packages in images in external registries and during the CI/CD process when an external scanner is used. In this case, you must use the scanner with the v1.2.1-with-db-java tag, which contains a pre-installed Java vulnerability database. The specified scanner is configured and used similarly to the v1.2.1-with-db scanner.
Integration with CI/CD
Kaspersky Container Security lets you scan images of containers and IaC residing in code repository management systems in the
to detect vulnerabilities, malware, misconfigurations, and exposed sensitive data.At the project build stage in the repository management system, you can run the Kaspersky Container Security scanner to check the objects in the repository for compliance with the enabled security policies. The scanner is started from a registry using an agent, such as GitLab Runner in GitLab. Data on the scan job and sending scan results are forwarded through the application programming interface (API).
When running an object scan during the project build stage, you must make sure that the Fail CI/CD step is not selected in the settings of the applied assurance policy. If this setting is activated, the solution will notify you of an error during the scan.
The scan results are displayed in the list of images in the Inventory → CI/CD → Scanning in CI/CD section.
For each of the objects in the table, Kaspersky Container Security displays the following:
- Date and time of the last scan.
- Name.
- Risk rating.
- Summary scan results with an indication of the identified objects related to vulnerabilities, malware, sensitive data and misconfigurations.
- Artifact type.
- The number and pipeline of the build in which the image was scanned.
In the section Resources → CI/CD → Scanning in CI/CD section, you can also generate a report on images that are scanned within the CI/CD process.
Reports are generated only for objects with the Image artifact type. In this section, a report cannot be generated for other types of artifacts.
Image scanning in CI/CD processes
Kaspersky Container Security allows you to scan images that are used in CI/CD. To scan images from CI/CD, you should configure the integration of Kaspersky Container Security with CI/CD processes.
Data from listening to and intercepting network traffic must be securely transferred between the CI/CD environment and the solution.
To scan images or repositories (in order to scan configuration files) used in the CI/CD process, add a stage to the CI/CD pipeline that runs the Kaspersky Container Security scanner.
To scan images from CI/CD, in the configuration file used to integrate the repository, specify the API_BASE_URL (web-address of the Kaspersky Container Security API server) and API_TOKEN (token to access API of the Kaspersky Container Security) environment variables for the scanner. You must also specify API_CA_CERT (certificate for verifying host server of the API solution) or SKIP_API_SERVER_VALIDATION = true to skip this scan.
The scanning results are forwarded to the server and displayed in the Management Console in the Resources → CI/CD section. The provided table lists the images that were scanned, shows the results of the risk assessment, and indicates the detected vulnerabilities.
You can click the image name link to open a page with detailed information about image scanning results. This page is similar to the page showing the results of registry images scanning.
Kaspersky Container Security also displays the type of artifact for each object. Two main artifacts are used:
- File system is repository containing configuration files.
- Container image is template used for runtime implementation of the container.
For each scan object, you can specify the build number (BUILD_NUMBER) and the build
BUILD_PIPELINE). These parameters can be used to determine the specific stage where the object failed.
For CI/CD images, rescanning is not provided.
Kaspersky Container Security performs the following types of scans in CI/CD:
- Scanning images from the image registry. The solution runs a scan after a successful build and saves the image into the image registry.
- Scanning of images in TAR archives. A TAR archive is stored as a build artifact that the solution scans in the next build pipeline.
- Scanning a Git repository, which can be performed in one of the following ways:
- for a project branch (individual development path) in the Git repository
- for a commit (state snapshot or checkpoint in the project's timeline)
To scan an image from an image registry:
Start the scan by running a command in the following format:
/scanner [TARGET] --stdout
where:
<TARGET>—full address of the image in the registry;<--stdout>is the output to the security event log.
To access the registry, enter in the environment variables the login COMPANY_EXT_REGISTRY_USERNAME password (token) COMPANY_EXT_REGISTRY_PASSWORD.
Examples of scanning images in GitLab CI/CD and Jenkins CI/CD.
To scan an image from a TAR archive:
- Build an image and save it as a TAR archive using any application for creating containerized images.
- Start the scan by running a command in the following format:
/scanner [TARGET] --file --stdoutwhere:
<TARGET>—path to the file with the image to be scanned<--file>—flag indicating scanning of theTARGETfile<--stdout>is the output to the security event log.
Example of a configuration file with settings for scanning a TAR archive
To scan the Git repository:
- In the configuration file of the Git repository, in the environment variables specify the token to access the repository (
GITHUB_TOKENorGITLAB_TOKEN). - Start the scan by running a command in the following format:
/scanner [TARGET] --repo [--branch BRANCH] [--commit COMMIT] --stdoutwhere:
<TARGET>—web address (URL) of the Git repository<--repo>—flag indicating scanning of theTARGETfile<--branch BRANCH>—branch of the repository to be scanned<--commit COMMIT>—hash of the commit to be scanned<--stdout>is the output to the security event log.
Scan results can be viewed in Resources → CI/CD, or downloaded in the .SPDX, .JSON, and .HTML formats.
Page top
Configuring integration with GitLab CI/CD
This example uses a specific scanner image with the built-in vulnerability databases located in the image registry of the Kaspersky Container Security manufacturer.
To use the image scanning feature in the GitLab CI/CD process, you should enable the use of the GitLab Container Registry.
Integration configuration includes the following steps:
- Authorization of GitLab CI/CD in the image registry of the Kaspersky Container Security manufacturer.
- On the cluster operator's workstation, prepare a Base64 hash of the authorization data by running the following command:
printf "login:password" | openssl base64 -Awhere login and password are the user name and password of an account in the image registry of the Kaspersky Container Security manufacturer.
- In the GitLab CI/CD environment variables, create the DOCKER_AUTH_CONFIG variable (in the GitLab repository select Settings → CI/CD, click the Expand button to expand Variables, and then click the Add variable button).
- Specify the variable in the following form:
{"auths": {"repo.cloud.example.com": {"auth": "base64hash"}}}where base64hash is the string obtained in step 1a.
- On the cluster operator's workstation, prepare a Base64 hash of the authorization data by running the following command:
- Authorization of requests from GitLab CI/CD when sending data to Kaspersky Container Security.
- Copy the API token on the My profile page.
- Specify the copied API token value in the API_TOKEN variable in the .gitlab-ci.yml configuration file.
- Adding the image scanning stage to the CI/CD process.
To add scanning to the CI/CD pipeline, you should add the following lines to the .gitlab-ci.yml file:
- Add information about the scanner image that contains databases of vulnerabilities and other malicious objects after the code build stage in the following form:
scan_image:stage: scannerimage:name: repo.cloud.example.com/repository/company/scanner:v1.2-with-dbentrypoint: [""]pull_policy: alwaysWe recommend that you specify always for the
pull_policyparameter to receive relevant builds with updated databases of vulnerabilities and other malicious objects for each scan. - Specify the tag, build ID, pipeline ID and API token for authorization of the CI/CD scanner requests to Kaspersky Container Security as follows:
SCAN_TARGET: ${CI_REGISTRY_IMAGE}:master
BUILD_NUMBER: ${CI_JOB_ID}
BUILD_PIPELINE: ${CI_PIPELINE_ID}
API_TOKEN:
<API token value>The example here contains the
mastertag, you can also specify another tag. - If you configure scanning for a private repository, specify the authorization data to ensure the scanner can access an image. The authorization data can be set as variables.
COMPANY_EXT_REGISTRY_USERNAME: ${COMPANY_EXT_REGISTRY_USERNAME}
COMPANY_EXT_REGISTRY_PASSWORD: ${COMPANY_EXT_REGISTRY_PASSWORD}
- If necessary, specify a variable to check the data receiving server in CI/CD using the CA certificate of the Ingress controller:
API_CA_CERT: ${KCS_CA_CERT}
The CA certificate of the Ingress controller is specified in the text field as a string in the .PEM format:
----- BEGIN CERTIFICATE ----- \ n...
<certificate details>...\ n ----- END CERTIFICATE -----If the
API_CA_CERTvariable is not set, scanning will start but will not be completed.Use of the CA certificate of the Ingress controller allows the scanner running in CI/CD to verify the authenticity of the data receiving server.
If you use a self-signed certificate, or want to skip checking the data receiving server using the CA certificate of the Ingress controller, specify the value of the variable to skip the check as follows:
SKIP_API_SERVER_VALIDATION: 'true'
- Specify the web address of the API host server for Kaspersky Container Security:
API_BASE_URL:<web address>variables:
API_BASE_URL: ${API_BASE_URL}
script:
- /bin/sh /entrypoint.sh $SCAN_TARGET --stdout > artifact-result.json
artifacts:
paths:
- artifact-result.json
- Add information about the scanner image that contains databases of vulnerabilities and other malicious objects after the code build stage in the following form:
After configuring integration with an external registry, you can scan images within the CI/CD process, including scanning in SBOM mode. Scan results can be viewed in Resources → CI/CD, or downloaded in the .SPDX, .JSON, and .HTML formats.
Page top
Configuring integration with Jenkins CI/CD
Configuring integration with Jenkins CI / CD consists of the following steps:
- Authorization of Jenkins CI/CD in the image registry of the Kaspersky Container Security manufacturer. To do so, on the cluster operator's workstation, prepare a Base64 hash of the authorization data by running the following command:
printf "login:password" | openssl base64 -Awhere login and password are the user name and password of an account in the image registry of the Kaspersky Container Security manufacturer.
- Authorization of Kaspersky Container Security API. To perform authorization, complete the following steps:
- Copy the API token on the My profile page.
- Specify the copied API token value in the API_TOKEN variable in the Jenkinsfile configuration file.
- Authentication of the data receipt server in CI/CD using the CA certificate of the Ingress controller. To perform authentication, in the Jenkinsfile configuration file, specify one of the following variables:
-e API_CA_CERT=${KCS_CA_CERT}means the authentication is performed, and the scanner started in CI/CD can make sure the receiving server is authentic.-e SKIP_API_SERVER_VALIDATION=truemeans authentication of the receiving server using the CA certificate of the Ingress controller is not performed.
- Creating Jenkins environment variables.
To create environment variables, add the following lines to Jenkinsfile:
- Add information about the container registry where the scanner is located as follows:
LOGIN: the name of the account in the scanner registryPASS: the password for the scanner registry - If you configure scanning for a private repository, specify the following authorization data to ensure the scanner access to an image:
COMPANY_EXT_REGISTRY_USERNAME: the name of the account in the registry of the scanned imageCOMPANY_EXT_REGISTRY_PASSWORD: the password for the registry of the image being scanned
- Add information about the container registry where the scanner is located as follows:
- Adding information to start the scanner. Information for starting the scanner that contains databases of vulnerabilities and other malicious objects is added to the Jenkinsfile configuration file in the form of a declarative or scripted pipeline.
Example of information for starting the scanner in the form of a declarative pipeline
Example of data for starting a scanner in the form of a scripted pipeline
- Generating an artifact for downloading.
You can generate an artifact for downloading in the .HTML, or .JSON format to receive the scan results. You can specify an artifact format in
--stoutas follows:pipeline {agent anystages {stage('run scanner') {steps {sh 'docker login -u ${LOGIN} -p ${PASS} company.example.com'sh 'docker run -e API_BASE_URL=https://kcs.int.company.com -e SKIP_API_SERVER_VALIDATION=true -e API_TOKEN=${API_TOKEN} -e COMPANY_EXT_REGISTRY_USERNAME=${COMPANY_EXT_REGISTRY_USERNAME} -e COMPANY_EXT_REGISTRY_PASSWORD=${COMPANY_EXT_REGISTRY_PASSWORD} company.example.com:5050/company/kcs/scanner:v1.2.1-lite jfrog.company.com/demo-kcs/bad:bad-project-test --html --stdout > result.html'}}stage('archive') {steps {archiveArtifacts artifacts: 'result.html'}}}}To generate a .JSON artifact, rewrite the
--html --stdout> result.html'line in the example above as follows:--json --stdout > result.json',and in the
archiveArtifacts artifactsline, specify the file name in the defined format: 'result.json'.Scan results can be obtained in the format you specified and can also be viewed in the Resources → CI/CD section.
Configuring integration with TeamCity CI/CD
To configure integration with TeamCity CI/CD:
- Copy the API token on the My profile page to authorize the Kaspersky Container Security API in TeamCity.
- In the settings menu in the TeamCity web interface, select Build Configuration Home → Parameters.
- Click Add new parameters to add the values of the following environment variables:
API_TOKEN— specify the copied value of the Kaspersky Container Security API token.API_BASE_URL— specify the URL of Kaspersky Container Security.RUST_BACKTRACE— If necessary, specifyfullto use backtracing.SKIP_API_SERVER_VALIDATION— specifytrueif you are using a self-signed certificate or if you need to skip authentication of the receiving server using the CA certificate of the Ingress controller.
- Go to the Build Configuration Home → Build Step: Command Line section and click Add build step to add a build step.
- In the window that opens, specify the following settings of the build step:
- In the Runner type drop-down list, select Command Line.
- In the Run drop-down list, select Custom script.
- In the Custom script field, specify the path to the container for scanning (for example,
/bin/sh /entrypoint.sh nginx:latest).
- Under Docker Settings, specify the following settings:
- In the Run step within Docker container field, specify the address of the scanner in the Docker registry. For example,
company.gitlab.cloud.net:5050/companydev/example/scanner:v1.2.0-with-db. - In the Additional docker run arguments field, increase the privilege value to
--privileged.
- In the Run step within Docker container field, specify the address of the scanner in the Docker registry. For example,
- Click Save to save the settings.
- Click Run in the upper-right corner of the page to start the build.
- If necessary, download the scan results artifact, which is available on the Artifacts tab on the build scan results page in the TeamCity web interface.
Defining the path to container images
To start scanning, the solution needs to determine the path to the container images that need to be scanned. The path to container images can be specified in two ways:
- By specifying an image tag after the registry name, repository name, and image name. The tag is a changeable and easy-to-read description of the image.
In this case, the path looks as follows:
<registry>/<repository>/<image name>:<tag>. For example, http://docker.io/library/nginx:1.20.1. - By specifying an image digest after the registry name, repository, and image name. A digest is an integral internal property of an image, specifically a hash of its contents (the SHA256 hash algorithm is used).
When using a digest, the path is formed as follows:
<registry>/<repository>/<image name><digest>. For example, http://docker.io/library/nginx@sha256:af9c...69ce.
A tag can match different digests, whereas digests are unique for each image.
Depending on the method used to specify the image path, Kaspersky Container Security performs one of the following actions before scanning:
- Converts the tag to a trusted digest.
- Checks whether the digest specified in the image path is trusted. A digest is considered trusted if it ensures the required degree of confidence in maintaining the desired protection relative to the object encoded using the hash algorithm.
Only trusted digests are sent to the container runtime.
Before running a container, the content of the image is compared with the received digest. To recognize a digest as trusted and the image as not corrupted, Kaspersky Container Security checks the integrity and authenticity of the image signature.
Monitoring the integrity and origin of images
When scanning images in CI/CD, Kaspersky Container Security protects against image spoofing at the registry level. The integrity and origin of images of containers deployed in an orchestrator cluster is controlled by verifying image signatures, starting at the build stage in CI.
Image integrity is monitored in two stages:
- Container images are signed after they are created. This process is implemented using external signature applications.
- Image signatures are checked before images are deployed.
The solution saves a signature key, which is based on the SHA256 hash function and used as the code for signature validation. When deployed in an orchestrator, Kaspersky Container Security asks the signature server to confirm the authenticity of the signature.
Kaspersky Container Security checks image signatures as follows:
- In the Administration → Integrations → Image signature validators section, you can configure the settings for integrating the solution with external image signature validation applications.
- In the Policies → Runtime → Policies section, a runtime policy is added to protect the content of the image. This runtime policy validates the authenticity of signatures. Digital signatures are validated based on the configured image signature validators.
- The orchestrator starts image deployment and uses a to make a deployment request to the agent (kube-agent).
To send the request to the Kaspersky Container Security agent, configure the dynamic admission controller in the values.yaml configuration file.
- Based on the applicable runtime policy, the agent checks the signature validation settings configured in the Administration → Integrations → Image signature validators section.
- If the check confirms the authenticity and validity of the signature, the solution allows image deployment. Otherwise, deployment is blocked.
Running the scanner in SBOM mode
Kaspersky Container Security allows you to start a scanner to check images for vulnerabilities in
mode. In this case, the solution scans a specially created SBOM file instead of a TAR archive.The advantages of using SBOM are the following:
- Less resources required to scan images for vulnerabilities.
- Reduced scanning time due to automatic verification of correct operation and proper use of solution components.
- Capability to scan all existing vulnerabilities in an image without exceptions.
- High reliability of scanning results.
In CI/CD, the scanning process consists of two stages: receiving an SBOM file and scanning an image based on the received SBOM file. The image scanning process is implemented as follows:
- The CI/CD scanner generates a list of image components and sends the generated artifact to Kaspersky Container Security.
- Using the image handler, the solution forwards the received SBOM file to the scanner for scanning.
For subsequent scanning, Kaspersky Container Security generates an SBOM file in the
format. You can also generate an artifact to download within the CI/CD process in the format.To generate an SBOM file in the .SPDX format when the scanner operates with SBOM creation:
Enter the following command in the .gitlab-ci.yml configuration file:
- /bin/sh /entrypoint.sh $SCAN_TARGET --sbom-json --spdx --stdout > example.spdx
where:
<--sbom-json> indicates the creation of an SBOM file.
<--spdx> indicates that an artifact is generated in the .SPDX format.
<--stdout > example.spdx> indicates data output to a file in the .SPDX format.
To generate an SBOM file in the .JSON format when the scanner operates with SBOM creation:
Enter the following command in the .gitlab-ci.yml configuration file:
- /bin/sh /entrypoint.sh $SCAN_TARGET --sbom-json --stdout > example.json
where:
<--sbom-json> indicates the creation of an SBOM file.
<--stdout > example.json> indicates data output to a file in .JSON format.
The resulting file (for example, example.json) is specified as an artifact: artifacts: paths:
Scanning using an SBOM file is only applicable when scanning an image for vulnerabilities. If your CI/CD process requires scanning for other risks and threats (such as misconfigurations), you must separately run the corresponding scanning and add its results to the image handler in addition to the SBOM file.
Page top
Getting scan results in JSON or HTML format
When using Kaspersky Container Security to scan images in CI/CD, you can generate and save an artifact with the scan results within your CI/CD platform. This can be done using a configuration file of the external repository system that is integrated with the solution. For example, you can use a .gitlab-ci.yml configuration file in GitLab.
You can generate an artifact containing scan results in the following scenarios:
- When the scanner conducts a complete CI/CD scan - scanning results file can be generated in the .HTML format or the .JSON format.
- When the scanner operates with SBOM creation - file containing scanning results can be generated in the .SPDX format or the .JSON format.
To generate a scan results file in .HTML format:
Enter the following command in the .gitlab-ci.yml configuration file:
- /bin/sh /entrypoint.sh $SCAN_TARGET --html --stdout > example.html
where:
<--html> indicates that an artifact is generated in .HTML format.
<--stdout > example.html> indicates data output to a file in .HTML format.
To generate a scan results file in .JSON format when performing a complete CI/CD scan:
Enter the following command in the .gitlab-ci.yml configuration file:
- /bin/sh /entrypoint.sh $SCAN_TARGET --stdout > example.json
where:
<--stdout > example.json> indicates data output to a file in .JSON format.
The resulting file (for example, example.json) is specified as an artifact: artifacts: paths:
Running the scanner in lite SBOM mode
Kaspersky Container Security allows you to start a scanner to check images for vulnerabilities in the lite SBOM mode. In this case, the solution scans a specially created SBOM file, and the results of this scan become available at the CI/CD stage.
Data from listening to and intercepting network traffic must be securely transferred between the CI/CD environment and the solution.
You can generate an artifact for download in the .SPDX, .HTML, or .JSON format to receive the results.
Running a scanner in GitLab
To start the scanner in lite SBOM mode in GitLab, when configuring image scanning in CI/CD process, edit the .gitlab-ci.yml configuration file as follows:
- Add information about the image of the scanner that is started for image scanning in CI/CD as follows:
scan_image:stage: scannerimage:name:repo.cloud.example.com/repository/company/scanner:v.1.2-liteentrypoint: [""]pull_policy: always - Specify the orchestration platform tag as follows:
k8s
In the example provided, the
k8stag is specified for Kubernetes, you can also specify the tag for another supported orchestration platform. - Specify such variables as the build ID, private repository details, pipeline ID and API token for authorization of the CI/CD scanner requests to Kaspersky Container Security as follows:
SCAN_TARGET: ${CI_REGISTRY_IMAGE}:master
COMPANY_EXT_REGISTRY_USERNAME: ${COMPANY_EXT_REGISTRY_USERNAME}
COMPANY_EXT_REGISTRY_PASSWORD: ${COMPANY_EXT_REGISTRY_PASSWORD}
BUILD_NUMBER: ${CI_JOB_ID}
BUILD_PIPELINE: ${CI_PIPELINE_ID}
API_TOKEN:
<API token value> - If necessary, specify a variable to check the data receiving server in CI/CD using the CA certificate of the Ingress controller:
API_CA_CERT: ${KCS_CA_CERT}
If the
API_CA_CERTvariable is not set, scanning will start but will not be completed. - Specify the web address of the API host server for Kaspersky Container Security:
API_BASE_URL:
<web address> - Specify the command to create an SBOM file when the scanner is started in one of the following supported formats:
- To generate an artifact in the .JSON format:
script:
- /bin/sh /entrypoint.sh $SCAN_TARGET --stdout > artifact-result.json
artifacts:
paths:
- artifact-result.json
- To generate an artifact in the .HTML format:
script:
- /bin/sh /entrypoint.sh $SCAN_TARGET --html --stdout > artifact-result.html
artifacts:
paths:
- artifact-result.html
- To generate an artifact in the .SPDX format:
script:
- /bin/sh /entrypoint.sh $SCAN_TARGET --spdx --stdout > artifact-result.spdx
artifacts:
paths:
- artifact-result.spdx
- To generate an artifact in the .JSON format:
Running a scanner in Docker
To start the scanner in lite SBOM mode in Docker:
- Specify the web address of the API host server for Kaspersky Container Security:
-e API_BASE_URL=https://company.local
- Specify the value of the variable to skip checking the data receiving server using the CA certificate of the Ingress controller:
-e SKIP_API_SERVER_VALIDATION=true
- Specify the API token for authorization of the CI/CD scanner requests to Kaspersky Container Security as follows:
-e API_TOKEN=
<API token value> - Specify data to start the scanner:
repo.kcs.company.com/images/scanner:
v1.2-lite - If you need to generate an artifact for downloading in the .SPDX, .HTML, or .JSON format, specify the following:
-
<artifact format>--stdout> result.<file format>For example:
--html --stdout > result.html - Press the Enter key to start the scanner.
If a domain name resolution error -
Name does not resolve- appears when calling the scanner, you must specify the address before theAPI_BASE_URLvariable before the internal DNS server of your organization. For example:--dns 10.0.xx.x
API_BASE_URL: https://company.local/
Scan results can be obtained in the format you specified and can also be viewed in the Resources → CI/CD section.
Page top
Risk handling
Threats identified by Kaspersky Container Security (vulnerabilities, malware, sensitive data, and misconfigurations) are subject to the Risk acceptance procedure. If you accept the risk of a threat, it will not be considered by assurance policies when determining image security status (Compliant/Non-compliant with security policies) during the specified acceptance period. Image scanning continues to detect the threat, but does not label the image as Non-compliant.
If you accept the risk of a vulnerability detected in an image, this risk is accepted for the specific image registry. If the risk is accepted for all vulnerabilities in an image, the image is deemed compliant with security policy requirements and is given Compliant status.
If you change the settings of the assurance policy applied to images, the image security status also changes.
The risk from a threat is accepted for a period of 30 days by default. You can extend the period during which the risk is considered accepted. You can also cancel risk acceptance at any time. If you cancel risk acceptance, the associated threat will again affect the security status of the image.
You can view the list of all accepted risks in the Policies → Risk acceptance section.
Risk acceptance
You can accept the risks found by the solution taking into account the following:
- In case of vulnerabilities, configuration errors, and sensitive data, you can accept risks with all severity levels.
- In case of malware, you can accept risks only with the Medium, Low, and Negligible severity levels.
You cannot accept risks with the High and Critical severity levels.
To accept the risk:
- In the image scanning results window, open the tab with information about the required type of detected threats.
- In the table, select a threat and click Accept or Accept risk in the action menu (depending on selected tab) to start risk acceptance.
- In the window that opens, specify the risk acceptance parameters:
- Select the extent of risk acceptance:
- For the selected image with the detected risk;
- For all images in the repository containing the image with the detected security threat;
- For all images in which this security threat has been or will be detected.
- If required, specify the period after which this security threat must be considered again when determining image security status.
- Specify the reason for risk acceptance.
- Select the extent of risk acceptance:
- Click the Accept button.
The selected threat does not affect the security status of this specific image, images in the repository, or all images for the defined number of days (or for an unlimited term).
An accepted risk can be viewed in the Policies → Risk acceptance section.
Page top
Viewing information about accepted risks
The list of all accepted risks is displayed in the Policies → Risk acceptances section.
You can use the list to do the following:
- Search by risk name, repository name, image, or resource where the risk is detected.
- Filter the list by risk type and manufacturer fix availability.
- Generate a Risk acceptance report by clicking the Create report button above the table.
- Sort the list by date of acceptance, risk name, scope (applied to all images or just one image), and acceptance period. Sorting is performed using the (
 ) sort icon.
) sort icon. - View detailed information about risk acceptance and the associated threat. Click the risk name link to open the window with the related detailed information.
Use the buttons in the detailed information window to do the following:
- Specify or extend the time period after which this security threat must be considered again when determining image security status.
- Cancel risk acceptance.
You can also view information about the accepted risk in the list of detected threats in the image scanning results. In the row with the threat with accepted risk, you can find the time of risk acceptance. You can click the link to open a window with detailed information about the risk acceptance and the associated threat.
Page top
Cancelling risk acceptance
To cancel risk acceptance:
- Open the window that shows detailed information about the risk acceptance and the associated threat. You can open the window by clicking the risk name link in the list of accepted risks. Or you can click the link in the row with the security risk with accepted risk, in the list of detected security risks in the image scanning results.
- Click the Cancel risk acceptance button and confirm the action in the window that opens.
Canceling risk acceptance means that the associated threat will again affect the security status of the image(s) for which the risk was accepted.
Page top
Compliance check
Kaspersky Container Security agents can check Kubernetes cluster nodes for compliance with the Kubernetes information security benchmarks.
Kaspersky Container Security checks for compliance with the Kubernetes benchmarks on Kubernetes versions 1.15–1.25.
The agent checks the state of the node where it is installed and sends the results to the server. Check results are displayed in the Compliance section.
You can view the results of checks on cluster nodes for compliance with the Kubernetes benchmarks in the Compliance → Kubernetes benchmarks section. The node scan results are displayed in a table. By default, Kaspersky Container Security displays a list with the results of the last scan of all nodes in all clusters. The nodes in the list are not grouped; you can use the filter to build a list of objects according to the cluster name.
Above the scan results table, there is the Control status section that displays the number of controls each status was assigned to during the scan. Kaspersky Container Security displays this information for the following scan statuses:
- Passed—check completed successfully.
- Warning—check shows that problems may occur during the execution of operations or tasks.
- Failed—check revealed non-compliance with the benchmark.
You can select nodes with which statuses you want to display after the scan. To do this, in the Control status section, select the button with the status that you want to hide. After that, the scan results table will only display the nodes whose benchmarks received this status (besides others) when scanned.
In Kaspersky Container Security, you can generate reports on the results of checks on compliance with the Kubernetes benchmarks. Depending on the level of detail you require, you can generate a Kubernetes benchmarks summary or detailed report. The list of generated reports is displayed under Administration → Reports.
Click the node name link to open a page with detailed information about the results of the node check.
The solution displays summary information at the top of the window. In the table, each benchmark is correlated with node compliance status.
You can check a node against the standard benchmarks by clicking the Rescan button.
Configuring and generating reports
Kaspersky Container Security provides the capability to generate reports based on the results of scanning registries, clusters, and images. The list of generated reports is displayed under Administration → Reports.
Reports generated by the solution display the following information:
- Events related to the operating logic of Kaspersky Container Security, such as the results of scanning images or analyzing nodes.
- Statistical data, such as a list of images and their identified security issues.
Kaspersky Container Security provides the following report templates:
- Summary images report.
- Images detailed report.
- Risk acceptance report.
- Kubernetes benchmarks summary report
- Kubernetes benchmarks detailed report
Depending on the applied report template, reports are created and generated in different sections of the solution.
The report generation process may take several minutes.
A list of generated reports is displayed under Administration → Reports. Reports are available for download in HTML, PDF or CSV format.
In Kaspersky Container Security, reports are generated only in English.
Image reports
In Kaspersky Container Security, you can generate reports on image scan results. Depending on the required level of detail, image reports can be summary reports or detailed reports.
Images summary report.
A summary report provides consolidated information on the selected images. This report provides the names of images and the names of the clusters containing these images. A summary report contains data on image compliance with security policy requirements, the names of policies that invoked the image scans, and the scan status. For each image, the report contains data on the number of identified risks related to vulnerabilities, malware, sensitive information, and misconfigurations.
Images detailed report
A detailed report provides more detailed information about selected images, completed scans, and identified security issues. Each report includes the date and time of the last scan, the cluster containing the selected image, a risk assessment, and an assessment of compliance with security policy requirements. Kaspersky Container Security displays the number of objects with different severity levels based on identified vulnerabilities, malware, sensitive data, and misconfigurations.
In the block with the description of the applied image security policies, the application provides a list of image security policies and indicates whether this scan stage was completed successfully or with errors. The report also specifies the action performed by Kaspersky Container Security in accordance with a specific policy. In this case, the report may show that the CI/CD stage was blocked, that images were marked as non-compliant with security requirements, or that both of these actions were performed.
The Vulnerabilities section provides a list of identified vulnerabilities, their severity levels, the resource in which they were detected, and the image version in which the vulnerabilities were fixed.
The Malware and Sensitive data sections display lists of detected malicious objects and objects containing sensitive data. For each object, the severity level and path are indicated.
The Misconfigurations block provides a list indicating the names of files in which misconfigurations were identified, the severity levels of the misconfigurations, and the types of files (for example, a Docker file). It also specifies the detected issue and provides recommendations on resolving the issue.
Kaspersky Container Security receives a description of misconfiguration-related issues from the internal database for configuration file analysis. This includes modules that scan configuration files from: Kubernetes, Dockerfile, Containerfile, Terraform, Cloudformation, Azure ARM Template, and Helm Chart. The description of misconfigurations and remediation recommendations are presented in the same language as the specified scan modules. For example, the description of misconfigurations from Kubernetes is provided in English.
This database is updated when a new version of the application is released.
Risk acceptance report
The Risk acceptance report contains data on accepted risks, including the date and time they were accepted. You can generate a report on all accepted risks or a group of accepted risks based on a filter.
For each selected risk that you accepted, its name is specified in the following format:
- Risk type (vulnerability, malware, sensitive data, or misconfiguration).
- Risk name or ID.
- Risk severity.
Kaspersky Container Security provides the image name, name of the resource and repository where the specific risk was detected, and the image version in which the risk was fixed. The report table also displays the following information about risk acceptance:
- Risk acceptance scope.
- Time period after which the risk should be considered again when determining image security status.
- User who accepted the risk.
Kubernetes benchmarks reports
In Kaspersky Container Security, you can generate reports based on the results of objects checking for compliance with the Kubernetes benchmarks.
By default, reports are generated for nodes with all statuses - Passed, Warning, and Failed. If you need to generate a report for nodes with a specific scan status, in the Control status section located above the table, click the appropriate status button. Kaspersky Container Security updates the display of the compliance check results, and a report is generated for nodes with the relevant status.
Depending on the level of detail, the reports can be summary reports or detailed reports.
Kubernetes benchmarks summary report
A summary report provides consolidated information on the selected clusters. It lists the names of nodes with the specified compliance check status, as well as the date and time of the last check of each node. The report for all nodes displays information on the number of Kubernetes benchmarks with selected statuses that were detected during object scanning.
Kubernetes benchmark detailed report
A detailed report provides more detailed information about the nodes of the selected cluster or about a specific node of the cluster. It depends on which subsection of the solution you are generating the report from:
- A detailed report on the nodes of the selected cluster is created from the table with a list of clusters.
- A report on a node is generated on the page with the detailed description of that node.
For each node in the cluster selected for generating the report, the date and time of the last scan performed, the number of Kubernetes benchmarks with the scan statuses assigned to them, and the benchmarks that were assigned the statuses selected before the report generation are also listed.
Kubernetes benchmarks provide configuration baselines and recommendations for secure configuration of solutions and applications to improve protection against cyberthreats. Hardening is a process that helps protect against unauthorized access, denial of service, and other security events by elimination of potential risks.
Example of Kubernetes benchmarks
Page top
Generating reports
In Kaspersky Container Security, reports are generated in different sections of the application depending on the specific report template that you are using.
The report generation process may take several minutes.
You can view a list of generated reports under Administration → Reports. In this section, generated reports can be downloaded as .HTML, .PDF, or .CSV.
Page top
Generating Images reports
To generate an Images summary report:
- Go to one of the following sections:
- Resources → Assets → Registries to generate a report on images from registries integrated with the solution.
- Resources → CI/CD to generate a report on images that are scanned in CI/CD.
Under Resources → CI/CD, reports are generated only for objects with the image artifact type (
container_imageorimage). In this section, a report cannot be generated for other types of artifacts.
- Depending on the section that you selected, do one of the following:
- In the Resources → Assets → Registries section, select a repository or one or more images for which you want to generate a report.
You can select all repositories and images by selecting the check box in the table header.
- In the Resources → CI/CD section, select one or more images for which you want to generate a report.
You can specify all images in all repositories by selecting the check box in the table header.
- In the Resources → Assets → Registries section, select a repository or one or more images for which you want to generate a report.
- Click the Create report button above the table, and select Images summary report in the drop-down list.
- In the window that opens, confirm report generation.
To generate an Images detailed report:
- Go to one of the following sections:
- Resources → Assets → Registries to generate a report on images from registries integrated with the solution.
- Resources → CI/CD to generate a report on images that are scanned in CI/CD.
Under Resources → CI/CD, reports are generated only for objects with the image artifact type (
container_imageorimage). In this section, a report cannot be generated for other types of artifacts. - Components → Scanners → Scanner tasks to generate a report based on an image scanned as part of a scan task.
- Depending on the section that you selected, do one of the following:
- Under Resources → Assets → Registries, perform the following steps:
- Select a repository or one or more images for which you want to generate a report.
- Click the Create report button above the table, and select Images detailed report in the drop-down list.
- Under Resources → CI/CD, complete the following steps:
- Select a repository or one or more images for which you want to generate a report.
- Click the Create report button above the table, and select Images detailed report in the drop-down list.
- Under Components → Scanners → Scanner jobs, complete the steps specified below:
- In the list of scanner tasks, select the scanned object for which you want to generate a report. You can select only one image from the page with a detailed description of the scan results for this image.
- In the window containing the object scan results, click the Create report button located to the right of the description of the object's compliance with security policy requirements.
A scan results window with a Create report button opens only for scanner jobs that have Finished status.
- Under Resources → Assets → Registries, perform the following steps:
- In the window that opens, confirm report generation.
Generating Risk acceptance reports
To generate a Risk acceptance report:
- Go to the Policies → Risk acceptance section.
By default, a report is generated for all accepted risks, which are displayed in the table. If necessary, you can generate a report for specific objects. To specify the objects for which you want to generate a report, perform one or more of the following actions:
- In the Search field, enter a risk name, repository name, or image name.
- Use the Risk type drop-down list above the table to select objects by risk type.
- Use the Vendor fix drop-down list above the table to select objects by risk type.
- Click the Create report button above the table.
Kaspersky Container Security will start generating a report, and will prompt you to follow a link to a page containing a list of generated reports.
Generating Kubernetes benchmark reports
To generate a Kubernetes benchmarks summary report:
- Go to Compliance → Kubernetes benchmarks.
- In the Cluster field, select one or more clusters to generate a report for.
You can generate a report on all clusters by selecting All from the Cluster drop-down list.
- Above the table, under Control status, select check statuses for which you want to generate a report: Passed, Warning, or Failed.
All statuses are selected by default.
- Click the Create report button above the table, and select Summary report from the drop-down list.
- In the window that opens, confirm report generation. You can download the generated report in .HTML, .PDF, and .CSV formats in the Administration → Reports section.
To generate a Kubernetes benchmarks summary report:
- Go to Compliance → Kubernetes benchmarks.
- Above the table, under Control status, select check statuses for which you want to generate a report: Passed, Warning, or Failed.
All statuses are selected by default.
- Do one of the following:
- In the Cluster field, select the cluster for which you want to generate a report, and complete the following steps:
- Click the Create report button above the table.
- Select Detailed report from the drop-down list.
- In the table with the check results, click the cluster name and complete the following steps:
- Click the name of a node in the selected cluster.
Kaspersky Container Security displays the available data on the Kubernetes benchmarks that was obtained for this node during the scan.
- Click the Create report button above the table.
- Click the name of a node in the selected cluster.
- In the Cluster field, select the cluster for which you want to generate a report, and complete the following steps:
- In the window that opens, confirm report generation. You can download the generated report in .HTML, .PDF, and .CSV formats in the Administration → Reports section.
A Kubernetes benchmarks detailed report is generated for one cluster only. However, it contains information about all nodes in this cluster.
To get detailed reports for multiple clusters, you must generate a report for each cluster separately.
Downloading and deleting reports
Kaspersky Container Security displays a list of generated reports in the table in the Administration → Reports section.
For each generated report, the table provides the name that the application assigned to the report, the report template, the date and time of report creation, and the report generation status. The table also lets you download a successfully generated report in the desired format, or delete a report.
To download a report:
In the row containing the report, click the button for the relevant format: PDF, HTML, or CSV.
To delete a report:
- In the row containing the name of the report that you want to delete, click the delete icon (
 ).
). - In the window that opens, confirm the action.
Security policies configuration
Kaspersky Container Security components use the following security policies:
- Scanner policies determine the settings for scanning different types of resources. Scan policies use rules to detect sensitive data, as well as vulnerabilities, malware, and misconfiguration.
- Assurance policies define Kaspersky Container Security actions to provide security if vulnerabilities, malware, sensitive data and misconfigurations detected during image scanning meet the criteria specified in the policy.
- Response policies define the actions of the solution in case events specified in the policy occur. For example, Kaspersky Container Security can notify the user about an event.
- Runtime policies allow you to control and, where appropriate, restrict the deployment and operation of containers on the cluster in line with your corporate security requirements.
Kaspersky Container Security applies only enabled policies during its operation. Disabled policies cannot be used during checks.
Scanner policies
Scanner policy determines the settings for scanning different types of resources.
When installing Kaspersky Container Security, a default scanner policy is created; it can be applied to all resources and executed in all environments. It is called the global scan policy (default). This policy is assigned global scope by default.
You can enable, disable, or configure global scanner policy settings if your role has been assigned the rights to manage scanner policies and view the global scope.
The following actions cannot be performed on a global scanner policy:
- Change the assigned global scope.
- Remove the global scanner policy.
The list of configured scanner policies is displayed as a table in the Policies → Scanner policies section.
You can use the list to do the following:
- Add new policies. Click the Add policy button located above the table to open the policy settings window.
- Enable or disable policies by using the Disabled / Enabled toggle button in the Status column of the table.
- Change policy settings. You can open the editing window by clicking the policy name link.
You can also enable and disable policies in the edit window. Kaspersky Container Security does not use disabled policies when operating.
- Configure rules for detecting sensitive data. To do this, go to the Sensitive data tab.
- Delete policies.
Creating a scanner policy
Rights to manage scanner policy settings are required to add a scanner policy in Kaspersky Container Security.
To add a scanner policy:
- In the Policies → Scanner policies section, click the Add policy button.
The policy settings window opens.
- Use the Disabled / Enabled toggle switch to disable the added policy, if necessary. In this case, it will be added but not applied until it is activated.
By default, the status of a newly added scanner policy is Enabled.
- Enter a policy name and, if required, policy description.
- In the Scope field, select the scope for the scanner policy from the available options.
If you plan to implement the policy with the global scope, one of your user roles must be granted the rights to view global scopes.
- In the Vulnerabilities section, configure the following settings:
- Use the Disabled / Enabled toggle switch to configure scanning using the National Vulnerability Registry (NVD) databases.
- Use the Disabled / Enabled toggle switch to configure scanning using the Vulnerability Database (VDB).
- In the Malware section, use the Disabled / Enabled toggle switch to configure scanning for malware in the image as part of the File Threat Protection component.
- In the Misconfigurations section, use the Disabled / Enabled toggle switch to configure a scan for configuration errors.
- Click Save.
Editing scanner policy settings
You can edit the scanner policy settings in Kaspersky Container Security if your account has been assigned at least one role that the policy's creator had at the time of the policy's creation.
To change scanner policy settings:
- In the Policies → Scanner policies section, click the policy name link.
The policy settings editing window opens.
- If required, use the Disable / Enable toggle switch to change the policy status (enabled / disabled).
- Make changes to the policy settings. The following settings are open for editing:
- The policy's name, description, and scope.
- Vulnerability control settings. Select the check boxes for the vulnerabilities database(s) to check images against.
- Malware control settings. Select the check box if you need to scan images for malware and other file threats. This control is conducted by using the File Threat Protection component.
- Misconfiguration control settings. Select the check box if you need to check images for misconfigurations. The control is conducted with the default settings configured by the Kaspersky Container Security manufacturer.
- Click Save.
Configuration of sensitive data detection rules
The list of configured rules for detecting sensitive data (hereinafter referred to as Secrets) during image scanning is displayed in the Policies → Scanner policies → Sensitive data section.
The rules are grouped into categories depending on the purpose and scope of secrets to be detected. The list of categories is determined by the Kaspersky Container Security manufacturer. Categories contain predefined rules.
You can use the list to do the following:
- View and change the settings for secrets detection rules. You can open the editing window by clicking the rule ID link.
- Add new rules to the selected category. Click the Add rule button located above the table to open the integration settings window. To add rules that do not belong to any of the preset categories, use the Other category.
- Delete rules. Check the box next to one or more rules in the list. The delete icon is then displayed.
To change the settings of sensitive data detection rules:
- In the table, in the Policies → Scanner policies → Policies section, select the scanner policy.
- In the Sensitive data section, select the necessary rules by selecting the check boxes in the rule lines.
- Use the Disable / Enable toggle switch in the Status column in the table with the list of policy rules to enable or disable this policy component.
Do not click the Save button.
Kaspersky Container Security immediately applies the changes to the sensitive data settings and displays the corresponding notification. You can also refresh the page to see the settings change.
Assurance policies
Assurance policy defines Kaspersky Container Security actions to provide security if threats detected during image scanning meet the criteria specified in the policy.
The configured assurance policies are displayed as a table in the Policies → Assurance policies section.
You can use the list to do the following:
- Add new policies. Click the Add policy button located above the table to open the policy settings window.
- Change policy settings. You can open the editing window by clicking the policy name link.
- Enable and disable policies. Policies are disabled and enabled by using the Disable/Enable toggle button in the Status column of the table containing the list of created policies.
- Delete policies.
If you add an assurance policy, modify its settings, or delete a policy, the compliance status is reviewed (Compliant / Non-compliant) for the images to which the policy is applied.
Creating an assurance policy
Rights to manage security policy settings are required to add a security policy in Kaspersky Container Security.
To add an assurance policy:
- In the Policies → Assurance policy section, click the Add policy button.
The policy settings window opens.
- Enter a policy name and, if required, policy description.
- In the Scope field, select the scope for the image security policy from the available options.
If you plan to implement the policy with the global scope, one of your user roles must be granted the rights to view global scopes.
- Specify the actions that Kaspersky Container Security should perform in accordance with the policy:
- Fail CI/CD step—if Kaspersky Container Security scanner detects threats while scanning the image in the CI/CD pipeline matching the severity level specified in the policy, the scanning ends with an error (Failed). This result is transferred to the CI system.
- Label images as non-compliant—Kaspersky Container Security labels images containing detected threats that meet the criteria specified in the policy.
- In the Vulnerability level section, configure the following settings:
- Use the Disabled / Enabled toggle switch to configure the scan based on the vulnerability severity level.
- Set the assigned severity level based on the vulnerability databases. You can select it from the Severity level drop-down list or specify a severity score from 0 to 10.
- Use the Disabled / Enabled toggle switch to configure blocking in case of specific vulnerabilities and specify these vulnerabilities in the Vulnerabilities field.
- In the Malware section, use the Disabled / Enabled toggle switch to configure scanning for malware in the image.
- In the Misconfigurations section, configure the following settings:
- Use the Disabled / Enabled toggle switch to configure the scan based on the misconfiguration severity level.
- Select the misconfiguration severity level from the Severity level drop-down list.
The severity level is assigned based on the vulnerability databases.
- In the Sensitive data section, configure the following settings:
- Use the Disabled / Enabled toggle switch to configure the scan based on the sensitive data severity level.
- Select the sensitive data severity level from the Severity level drop-down list.
The severity level is assigned based on the vulnerability databases.
- Click Save.
By default, the added policy is Enabled.
Page top
Editing assurance policy settings
You can edit the image security policy settings in Kaspersky Container Security if your account has been assigned at least one role that the policy's creator had at the time of the policy's creation.
To change assurance policy settings:
- In the Policies → Assurance policies section, click the policy name in the list of existing assurance policies.
The policy settings window opens.
- Make changes to the relevant policy settings:
- The policy's name, description, and scope.
- Actions of the solution in accordance with this policy.
- Required scans.
- Severity level of vulnerabilities detected during scans.
- Identify number of vulnerabilities for blocking purposes.
- Click Save.
Response policies
Response policy defines the actions of the solution in the case that events specified in the policy occur. For example, Kaspersky Container Security can notify the user about the detected threats.
If you want to configure response policies to notify the user, you should first set up integration with notification outputs.
The configured response policies are displayed as a table in the Policies → Response policies section.
You can use the list to do the following:
- Add new policies. Click the Add policy button located above the table to open the policy settings window.
- Change policy settings. You can open the editing window by clicking the policy name link.
- Enable and disable policies. Policies are disabled and enabled by using the Disable/Enable toggle button in the Status column of the table containing the list of created policies.
If you disable a policy, Kaspersky Container Security will not perform the actions specified in that policy.
- Search for policies. To find a policy, use the search field above the list of response policies to specify the policy name or part of it.
- Delete policies.
In this version of the solution, response policies define only the actions that Kaspersky Container Security takes to notify the user when a specific event detailed in the policy occurs. For example, if an object with a critical vulnerability is detected, the solution can send an email notification to the user.
Creating a response policy
Rights to manage response policy settings are required to add a response policy in Kaspersky Container Security.
To add a response policy:
- In the Policies → Response policies section, click the Add policy button.
The policy settings window opens.
- Enter a policy name and, if required, policy description.
- In the Scope field, select the scope for the response policy from the available options.
If you plan to implement the policy with the global scope, one of your user roles must be granted the rights to view global scopes.
- In the Trigger field, use the drop-down list to select an event that will trigger Kaspersky Container Security to notify the user if this event occurs during a scan. One of the following events can be selected as a trigger event:
- Sensitive data. A notification is sent if the solution detects signs of exposed sensitive data in an object during a scan.
- Non-compliant. Kaspersky Container Security notifies you if a scanned object contains images that do not comply with the requirements of security policies.
- Critical vulnerabilities. A notification is sent if a scanned object contains vulnerabilities with Critical status.
- Malware. A notification is sent if a scan finds malware.
- Risk acceptance expiration. Kaspersky Container Security notifies you if a scanned object contains risks that you had previously accepted but the risk acceptance period has expired.
- Configure the required notification methods:
- Select an Output: Email or Telegram.
- From the drop-down list in the Integration name field, select the name of the pre-configured integration with the selected notification output.
- To add another notification method, click the Add button and fill in the fields as described in paragraphs a and b above.
- If needed, you can remove the added notification methods by clicking the icon located to the right of the Integration name field.
- Click Save.
By default, the added policy is Enabled.
Page top
Editing response policy settings
You can edit the response policy settings in Kaspersky Container Security if your account has been assigned at least one role that the policy's creator had at the time of the policy's creation.
To change response policy settings:
- In the Policies → Response policies section, click the policy name in the list of existing response policies.
The policy settings window opens.
- If necessary, make changes to the relevant policy settings:
- Change the policy name.
- Add or edit the policy description.
- Add or edit the policy scope.
- Change the trigger event by selecting it from the drop-down list.
- Add an output by clicking the Add button.
- Delete the output by clicking the delete icon (
 ) located next to the line of the selected output.
) located next to the line of the selected output.
- Click Save.
Runtime policies
A runtime policy determines the actions that are taken by the solution when monitoring and controlling runtime operations of containers in accordance with the security policies. Kaspersky Container Security maintains control based on security threats detected in an image, the severity level of these threats, and the availability of
.Containers in the runtime may run from verified images or from images that are still unknown to the solution.
On the Policies tab, under Policies → Runtime policies, a table lists configured runtime policies.
You can use the list to do the following:
- Add new policies. Click the Add policy button located above the table to open the policy settings window.
- Change policy settings. You can open the editing window by clicking the policy name link.
- Enable and disable policies. Policies are disabled and enabled by using the Disable/Enable toggle button in the Status column of the table containing the list of created policies.
If you disable a policy, Kaspersky Container Security will not perform the actions specified in that policy.
- Search for policies. To find a policy, use the search field above the list of response policies to specify the policy name or part of it.
- Delete policies.
To work optimally, a runtime policy must be supplemented by runtime container profiles, which define the rules and restrictions for running containers in the runtime environment.
Creating a runtime policy
Rights to manage runtime policy settings are required to add a runtime policy in Kaspersky Container Security.
To add a runtime policy:
- Under Policies → Runtime policies, select the Policies tab.
- Click the Add policy button.
The policy settings window opens.
- Enter a policy name and, if required, policy description.
- In the Scope field, select the scope for the runtime policy from the available options. Since runtime policies are only used for deployed and/or running containers, scopes containing resources across clusters can be selected.
Scopes containing only registry resources are not available for selection. If necessary, you can specify individual images and pods for the runtime policy that you are creating in the Container runtime profiles section, as specified in step 11.
If you plan to implement the policy with the global scope, one of your user roles must be granted the rights to view global scopes.
- If necessary, select the Exclusions check box to define exclusions to which the runtime policy will not be applied. To do so, select the relevant objects in the drop-down list, specify their names, and then click Add.
Existing exclusions in the policy are checked when deploying a container.
- In the Mode section, select one of the following policy enforcement modes:
- Audit. In this mode, a scan takes into account the contents of containers.
- Enforce. In this mode, the solution blocks all objects that do not comply with the rules and criteria defined in the policy.
- In the Best practice check section, use the Disabled / Enabled toggle switch to activate the scan for compliance with best security practices. From the list of settings, select the scan settings that guarantee that the correct image is run and that the CPU and RAM usage settings are correctly configured.
- In the Block non-compliant images section, use the Disabled / Enabled toggle switch to prevent containers running from images that do not comply with the requirements. This check will be performed only for scanned images that are registered in the solution and have the Compliant status.
- In the Block unregistered images section, use the Disabled / Enabled toggle switch to block image deployment if the image is unknown to Kaspersky Container Security. To deploy the image, you must register it in the solution and wait for it to appear in the registry.
- In the Capabilities block section, use the Disabled / Enabled toggle switch to block the use of specified Unix functions. To do so, select specific system functions from the drop-down list. You can also lock the use of all Unix system functions by selecting ALL from the drop-down list.
- In the Container runtime profiles section, use the Disabled / Enabled toggle switch to block processes inside containers and network connections for pods. To do this, perform the following actions:
- In the drop-down list, select an attribute to define the pods that the container runtime profiles will be applied to.
- Depending on the selected attribute, do the following:
- If you selected By pod labels, enter the pod label key and the pod label value.
You can add additional pod labels for pod selection by clicking the Add label pair button.
- If you selected Image URL template, enter the template for the web address of the image registry.
If the cluster contains images from the public Docker Hub registry, the solution equally considers the full path and the short path to the images. For example, if you specify the URL of the container image in the cluster as docker.io/library/ubuntu:focal, the solution accepts it equally as ubuntu: focal.
You can add additional web addresses for pod selection by clicking the Add Image URL button.
- If you selected By pod labels, enter the pod label key and the pod label value.
- In the Container runtime profile field, specify one or more runtime profiles that will be applied to pods that match the attributes you defined.
- If necessary, you can add pods for mapping using the Add pod mapping button. Pods with different attributes or applied runtime profiles will be mapped under the same runtime policy.
- Under File Threat Protection, use the Disabled / Enabled toggle to activate File Threat Protection. It is used to find and analyze potential file threats, and provides security for containerized objects, such as archives and email files.
When a runtime policy is applied with the File Threat Protection component enabled, Kaspersky Container Security activates real-time file threat protection on all nodes within the scopes defined for that policy. The configuration of the deployed agents depends on the settings that you specify for File Threat Protection. You can configure the File Threat Protection settings by clicking Settings in the Policies tab under Policies → Runtime policies.
File Threat Protection settings are applied to all active runtime policies.
- In the Image content protection section, use the Disabled / Enabled toggle switch to enable verification of digital signatures that confirm the integrity and origin of images in the container. To do this, perform the following actions:
- In the Image registry URL template field, enter the template for the web address of the image registry in which you want to verify signatures.
- In the drop-down list, select Check to enable verification or Don't check to disable verification.
- In the drop-down list, select one of the configured image signature validators.
- If necessary, add signature verification rules by using the Add signature verification rule button. The solution will apply multiple signature verification rules under a single runtime policy.
- In the Limit container privileges section, use the Disabled / Enabled toggle switch to block the start of containers with a specific set of rights and permissions. In the list of settings, select the rights and permissions configuration to block pod settings.
- In the Registries allowed section, use the Disabled / Enabled toggle switch to allow deployment of containers in a cluster only from specific registries. To do so, select the relevant registries from the Registries drop-down list.
- In the Volumes blocked section, use the Disabled / Enabled toggle switch to prevent the selected volumes from being mounted in containers. To do this, specify the volume mount points on the host system in the Volumes field.
The Volumes field must begin with a forward slash ("/") because this represents the operating system path.
- Click Save.
By default, the added policy is Enabled.
Page top
Editing runtime policy settings
You can edit the runtime policy settings in Kaspersky Container Security if your account has been assigned at least one role that the policy's creator had at the time of the policy's creation.
To change runtime policy settings:
- In the Policies → Runtime policies → Policies section, click the policy name in the list of existing runtime policies.
The policy settings window opens.
- Change the policy name.
- Add or edit the policy description.
- Make changes to the relevant sections of the policy:
- Mode.
- Scope of application.
- Bypass criteria.
- Best practice check.
- Block non-compliant images.
- Block unregistered images.
- Capabilities block.
- Container runtime profiles.
- File threat protection.
- Image content protection.
- Limit container privileges.
- Registries allowed.
- Blocking volumes.
- Click Save.
Deleting policies
You can delete security policies if your account has been assigned at least one role that the policy's creator had at the time of the policy's creation. You also need rights to manage the corresponding types of policies in order to delete them.
To delete a policy:
- Open the list of configured scanner policies, assurance policies, response policies or runtime policies.
- In the line containing the name of the policy that you want to delete, click the delete icon (
 ).
). - In the window that opens, confirm the action.
If security policy configuration errors block Kaspersky Container Security and you cannot manage the solution using the Management Console, the security policies must be deleted manually.
To manually delete a policy and recover the solution:
- Run the following command to remove the agents (kube-agent and node-agent) as applicable:
kubectl delete deployment kube-agentkubectl delete daemonset node-agent - Delete all customer resources in the target cluster by running the following command:
kubectl get crd -o name | grep 'kcssecurityprofiles.securityprobe.kcs.com' | xargs kubectl delete - Restart all Kaspersky Container Security pods and access the Management Console.
- Make the necessary changes to the security policies.
- Install the agents using the instruction in the .YAML format.
Managing container runtime profiles
When implementing runtime policies, Kaspersky Container Security can apply user-defined rules for monitoring processes and the network. To do so, add runtime profiles to the appropriate runtime policies. Runtime profiles are essentially lists of restrictions for containers. Image profiles define the settings for secure image deployment and safe activities of an application deployed from an image. The actions assigned in profiles can significantly reduce the capabilities of cybercriminals who could potentially infiltrate a facility, and can improve security during the runtime operation of containers.
The following settings specify restrictions in an image profile:
- Executable files that should be blocked.
- Network restrictions for inbound and outbound connections.
The list of configured profiles is displayed as a table on the Container runtime profiles tab under Policies → Runtime policies. In this section, you can also do the following:
- Create new container runtime profiles. Open the profile settings window by clicking the Add profile button above the list.
- Edit profile settings by clicking the link in the runtime profile name.
- Delete runtime profiles.
Creating a runtime profile
To add a container runtime profile:
- Under Policies → Runtime policies → Container runtime profiles, click the Add profile button.
The profile settings input window opens.
- Enter a name for the runtime profile and, if necessary, a description.
- In the Restrict container executable files section, use the Disabled / Enabled toggle switch to restrict executable files according to rules. In the list, select the blocking option that guarantees optimal container performance:
- Block process from all executable files - application blocks all executable files from starting while the container is running.
- Block specified executable files - application blocks the executable files that you select in the Block the specified executable files field. You can block all executable files or a list of specific executable files. You can also use an
*mask (for example,/bin/*) to apply a rule to an entire directory and its subdirectories.You can fine-tune the list of allowed and blocked executable files by specifying exclusions for blocking rules. For example, you can specifically exclude the path
/bin/catfor a rule applied to/bin/*. In this case, all executable files from the directory/bin/will be blocked from running except the/bin/catapplication.Example path to executable files
If you select the Allow exclusions check box, the application will block all executable files except those specified in the Allow exclusions field when a container is started and running.
All rules and exceptions specified for this group of parameters are regular expressions (regexp). The solution uses the specified patterns and indicators to find all files that match a specific regular expression.
- In the Restrict ingress container connections section, use the Disabled / Enabled toggle switch to activate the capability to restrict inbound connections of a container. When this restriction is active, Kaspersky Container Security will block all sources of inbound connections except those that you specified as exclusions.
If you select the Allow exclusions check box, you can specify the parameters of one or more allowed sources of inbound network connections. To define exclusions, you must specify at least one of the following parameters:
- Sources. In the Sources field, enter an IP address or a range of IP addresses for the inbound connection source in CIDR4 or CIDR6 notation.
- In the TCP ports field and in the UDP ports field, enter a specific port or range of ports for the connection.
If you need to specify multiple ports, use a comma, e.g. 8080, 8082.
If you do not specify a value for the ports, the application will allow a connection over all ports.
- In the Restrict egress container connections section, use the Disabled / Enabled toggle switch to activate the capability to restrict outbound connections for defined destinations.
If you select the Allow exclusions check box, you can specify the parameters of one or more allowed destinations for outbound network connections. To define exclusions, you must specify at least one of the following parameters:
- Destinations. In the Destinations field, enter an IP address or a range of IP addresses for an outbound connection destination in CIDR4 or CIDR6 notation, or the web address (URL) of a destination.
- In the TCP ports field and in the UDP ports field, enter a specific port or range of ports for the connection.
If you need to specify multiple ports, use a comma, e.g. 8080, 8082.
If you do not specify a value for the ports, the application will allow a connection to be made through all ports.
- Click Save.
The added runtime profile is displayed in the Policies → Runtime policies → Container runtime profiles section.
Page top
Examples of configured runtime profiles
The table below presents a few of the images that are most frequently used by the application, and the settings for their configured restrictions in runtime profiles.
Images and their configured settings
Image name |
Restrict container executable modules |
Restrict network connections |
|---|---|---|
Nginx |
Allowed executable file:
|
Block outbound connections |
Mysql |
Allowed executable files:
|
Block outbound connections |
Wordpress |
Allowed executable files:
|
|
Node |
Allowed executable file:
|
Block outbound connections |
MongoDB |
Allowed executable files:
|
|
HAProxy |
Allowed executable files:
|
|
Hipache |
Allowed executable files:
|
|
Drupal |
Allowed executable files:
|
|
Redis |
Allowed executable files:
|
Block outbound connections |
Tomcat |
Allowed executable files:
|
Block outbound connections |
Celery |
Allowed executable files:
|
|
Changing runtime profile settings
To change container runtime profile settings:
- Under Policies → Runtime policies → Container runtime profiles, click the name of the profile in the list of existing container runtime profiles.
- In the window that opens, change the values of one or more of the following settings:
- Name of the runtime profile.
- Description of the runtime profile.
- Restrict container executable files.
- Restrict inbound network connections.
- Restrict outbound network connections.
- Click Save.
Changes made to runtime profile settings are immediately applied to the running container and affect its operation.
Page top
Deleting a runtime profile
To delete a container runtime profile:
- In the table of configured runtime profiles under Policies → Runtime policies → Image profiles, click the delete icon (
 ) in the row containing the name of the profile that you want to delete.
) in the row containing the name of the profile that you want to delete. - In the window that opens, confirm the action.
File Threat Protection
Kaspersky Container Security uses the File Threat Protection component to search and analyze potential file threats in order to protect containerized files (including files in archives and email) from malware. If malware is detected, Kaspersky Container Security can block or delete the infected object, and terminate the malicious process started using that object. The results of malware scan are displayed together with the overall scan results.
You can enable or disable File Threat Protection and configure protection settings:
- Select the file interceptor operation mode (audit or blocking objects).
- Select a file scan mode (when opened, when opened and modified).
- Enable or disable scanning of archives, mail databases, email messages in text format.
- Temporarily exclude plain text files from re-scanning.
- Limit the size of an object to be scanned and the scan duration.
- Select the actions that the solution will perform on infected objects.
- Configure scan scopes. Kaspersky Container Security will scan objects in the specified area of the file system.
- Configure the use of the heuristic analyzer and the iChecker technology during a scan.
- Enable or disable the recording of information about scanned uninfected objects, scanning of archived objects, and unprocessed objects to the security event log.
The File Threat Protection settings can be activated under Policies → Runtime policies → Container runtime profiles, configured in the File Threat Protection settings window, and applied to all existing runtime policies.
If you do not want File Threat Protection to be activated when a certain security environment policy is started, disable it in the policy settings using the Disabled / Enabled toggle. Also, make sure that File Threat Protection is not running under a different applicable runtime policy.
Configuring the File Threat Protection settings
Configuring File Threat Protection requires the IS Administrator permissions.
To configure File Threat Protection:
- In the Policies → Runtime policies → Container runtime profiles section, click the Settings button.
The window for configuring the File Threat Protection settings opens.
- Under File interceptor mode, select one of the following object scan modes:
- In the Audit mode, the solution scans and keeps track of the content of objects.
- In the Enforce mode, the solution blocks all objects that do not satisfy the configured rules and criteria.
- Under Scan mode, select a File Threat Protection mode:
- Smart mode (default): a file is scanned on attempts to open it, and then scanned again on attempts to close it if the file has been modified. If a process accesses an object multiple times in the course of its operation and modifies it, the solution scans the object again only when the process closes it for the last time.
- Open and modify: a file is scanned on attempts to open it, and then scanned again on attempts to close it if the file has been modified.
- Open: a file is scanned on attempts to open it for reading, execution, or modification.
- Under Actions on detected objects, select the following from the drop-down lists:
- The First action that the File Threat Protection component will perform on a detected infected object:
- Perform recommended action that depends on the risk severity level detected in the file and the possibility of disinfecting it (default).
For example, Trojans are deleted immediately as they do not infect other files and disinfection is not applicable here.
- Disinfect the object. A copy of the infected object will be moved to backup.
- Block access to the object.
- Remove an object. A copy of the infected object will be moved to backup.
- Perform recommended action that depends on the risk severity level detected in the file and the possibility of disinfecting it (default).
- The Second action that the File Threat Protection component will perform on a detected infected object if the first action fails:
- Perform recommended action that depends on the risk severity level detected in the file and the possibility of disinfecting it (default).
- Disinfect the object. A copy of the infected object will be moved to backup.
- Block access to the object.
- Remove an object. A copy of the infected object will be moved to backup.
We recommend specifying both actions for detected objects.
Consider the following when selecting actions to perform on detected objects:
- If Block or Remove is selected as the first action, the second action does not need to be specified.
- If the second action is not selected, the default action is Block.
- If the applicable runtime policy mode is set to Audit, no action is taken on detected objects.
- The First action that the File Threat Protection component will perform on a detected infected object:
- Under Scan settings, use the check boxes to define the scan objects that contain files and directories to scan. If a check box is selected, the solution scans the selected objects. You can select one or several scan settings from the following list:
- Scan archives: this check box enables or disables archive scanning. By default, the check box is cleared and the solution does not scan archives.
The solution scans archives in such formats as .ZIP, .7Z *, .7-Z, .RAR, .ISO, .CAB, .JAR, .BZ, .BZ2, .TBZ, .TBZ2, .GZ, .TGZ, .ARJ, as well as .SFX self-extracting archives. The list of supported archive formats depends on the databases used.
If archive scanning is enabled and Perform recommended action is set as the first action on a detected object, the solution deletes the infected object or the entire archive containing the threat, depending on the archive type.
You can define the scope of archives for scanning by specifying Self-extracting archives or All archives. If you choose to scan self-extracting archives, the solution scans only archives that contain an executable unpacker.
To start scanning, the solution first unpacks the archive, which may slow down the scan. You can reduce the duration of archive scanning by enabling and configuring the Skip object if scan takes longer than (sec) and Skip objects larger than (MB) settings.
- Scan mail databases: this check box enables or disables scanning of Microsoft Outlook, Outlook Express, The Bat! and other mail application databases. By default, the check box is cleared, and the solution does not scan mail database files.
- Scan plain mail: this check box enables or disables scanning of plain text email message files. By default, the check box is cleared and the solution does not scan plain text messages.
- Skip text files: this check box enables or temporarily disables scanning of plain text files if they are reused by the same process within 10 minutes after the last scan. This setting allows you to optimize scanning of application logs. By default, the check box is cleared and the solution does not scan plain text files.
- Skip object larger than (MB): this check box enables or disables scanning of objects with the specified maximum size in megabytes. If the size of an object to be scanned exceeds the specified value, the solution skips the object during scanning.
Available values: 0–999999. If the value is set to 0, the solution scans files of any size.
Default value: 0.
- Skip object if scan takes longer than (sec): this check box enables or disables time limit in seconds for scanning an object. After the specified time expires, the solution stops scanning the file.
Available values: 0–9999. If the value is set to 0, the scan time is unlimited.
Default value: 60.
- Scan archives: this check box enables or disables archive scanning. By default, the check box is cleared and the solution does not scan archives.
- In the Technologies section, select the check boxes to define the technology that the solution will use to scan objects. You can select one of the following options:
- Use iChecker: this check box enables or disables scanning of only new files and files that have been modified since the last scan. iChecker is a scanning method that reduces the overall scan time by skipping some of the previously scanned files that have not been modified since the scan.
If the check box is selected, the solution scans only new files and those modified since the last scan. If the check box is cleared, the solution scans files regardless of their creation or modification dates.
The check box is selected by default.
- Use heuristic analysis: this check box enables or disables the use of heuristic analysis when scanning objects. Heuristic analysis enables the solution to identify security threats unknown to malware analysts.
The check box is selected by default.
If the Use heuristic analysis check box is selected, you can select the heuristic analysis level. A heuristic analysis level balances the rigor of security threat scanning, the load on the operating system, and the scan duration. The higher the level, the more resources the scan requires, and the longer it takes. You can select one of the following options:
- Recommended (default): the optimal level recommended by Kaspersky experts. This provides an optimal combination of protection quality and impact on the performance of protected servers.
- Light: the least detailed scan, minimal system load.
- Medium: medium scan detail, balanced system load.
- Deep: the most detailed scan, maximum system load.
- Use iChecker: this check box enables or disables scanning of only new files and files that have been modified since the last scan. iChecker is a scanning method that reduces the overall scan time by skipping some of the previously scanned files that have not been modified since the scan.
- Under Event logging, select the check boxes to determine whether the event will be recorded in the security event log. You can select one or several options for event logging:
- Log clean objects: this check box enables or disables the logging of information about scanned objects that the solution has recognized as uninfected.
- Log unprocessed objects: this check box enables or disables the logging of information about scanned objects that have not been processed for any reason.
- Log packed objects: this check box enables or disables logging of information about scanned objects that are part of composite objects, such as archives.
If the check box is selected, the solution logs the event for all objects. If the check box is cleared, the event is not logged. The check box is cleared by default.
- Click Save.
File interceptor operation
When running object scan jobs, File Threat Protection uses the file operation interceptor. It is set to one of the following file interception modes (InterceptorProtectionMode):
- Enforce (default): blocks files for the duration of the scan job that uses the file interceptor. No file can be accessed until the scan has been completed. When detecting infected objects, the solution performs the actions specified in the settings under Actions on detected objects.
- Audit: does not block files during the scan job that uses a file interceptor. Access to any file is allowed; scanning is performed asynchronously. When infected objects are detected, the solution only records an event in the Event Log. The actions specified in the settings under Actions on detected objects are not performed.
If the Audit value is selected, the solution enables the notification mode of File Threat Protection.
The configured component settings are applied when File Threat Protection is activated in runtime policies. These settings are the same for all created runtime policies. If the applicable runtime policy is set to audit mode and InterceptorProtectionMode in File Threat Protection is set to Enforce, the solution blocks the files.
Database updates
The File Threat Protection databases are kept up to date to ensure the maximum level of containerized object protection against file threats. Updates run automatically on a schedule or on demand.
When a new agent is deployed, the solution updates and then applies the updated File Threat Protection databases.
The databases are updated from the Kaspersky Container Security update server. You can use Kaspersky Update Utility to set up database and component updates from a shared directory on the corporate LAN. To do this, a device on the corporate LAN must receive update packages from Kaspersky update servers and use the utility to copy the packages to the shared directory. The other devices on the corporate LAN will be able to pull the update package from the shared directory.
When the solution is deployed in a public corporate network, an update is performed directly from the update server. When installing the solution in a private corporate network, the updated File Threat Protection databases are added to the kcs-updates container for subsequent running and updating.
Applying updated databases to a running agent does not violate active runtime protection of nodes. Database updates are recorded in the event log.
If an error occurs while updating the databases, the solution cancels the File Threat Protection updates and continues using the previously installed databases. Errors that occur during the update are logged to the events.db file located in the node-agent pod.
The events.db file is available if File Threat Protection is enabled for the group of agents.
Page top
Force disabling of File Threat Protection
In Kaspersky Container Security 1.2, you can completely disable the File Threat Protection component. This can be necessary if you experience problems with the component.
You can forcibly disable the File Threat Protection component in two ways—by modifying the file for deploying agents on the cluster, and by modifying running agents.
To forcibly disable File Threat Protection using an agent deployment file:
- Open the .YAML file with instructions for deploying agents on the cluster that you downloaded when you deployed the agents.
- In the
DaemonSetsection for the node-agent, set theFILE_THREAT_PROTECTION_ENABLEDenvironment variable tofalse.name: FILE_THREAT_PROTECTION_ENABLEDvalue: false - Save changes to the instructions file.
- In the console, apply the instructions file by running
kubectl apply -f agents.yamlThe orchestrator redeploys the node-agent pods with File Threat Protection disabled.
To forcibly disable File Threat Protection when agents are running:
- In the console, open running agents using the
kubectl editcommand. - In the
DaemonSetsection for the node-agent, set theFILE_THREAT_PROTECTION_ENABLEDenvironment variable tofalse.name: FILE_THREAT_PROTECTION_ENABLEDvalue: false - Save your changes.
The orchestrator applies the saved changes and disables File Threat Protection.
Configuring integration with image signature validators
Kaspersky Container Security can verify the authenticity and validity of the digital signatures of images. To use this functionality, you need to configure integration of the solution with one or more external signature applications. The specifics of signing an image digest, the location of signatures, and protecting signatures depend on the signature application you have selected. The solution supports two configurable external signature validation applications:
- Notary v1 is a web service developed by Docker that is used to ensure the security of containers at various stages of their life cycle, including the creation and subsequent storage of signatures.
- Cosign is a web service designed to create signatures for containers, verify signatures, and place signed containers in repositories. The tool was developed as part of the project.
You can configure integration with an image signature validator in the Administration → Integrations → Image signature validators section.
Page top
Viewing the list of integrations with signature validators
In the Administration → Integrations → Image signature validators section, a table of all configured integrations with image signature validators is displayed.
The table displays the following information about the integrated image signature validators:
- Name of the validator
- Description, if one was specified when creating the integration
- Type of the image signature validator—Notary v1 or Cosign.
- Web address to which the image signature validator connects
In the table, you can:
- Add new integrations with signature verification modules. Click Add signature validator above the list to open the integration settings window.
- View and edit the settings for integration with an image signature verification module. You can open the editing window by clicking the link on the verification module name.
- Remove an integration with an image signature validator.
Adding an integration with an image signature validator
To add an integration with an image signature validator:
- In the Administration → Integrations → Image signature validators section, click the Add signature validator button.
The integration settings window opens.
- In the General information section, enter a policy name and, if necessary, a policy description.
- In the Type section, select one of the following signature validators:
- Notary v1.
- Cosign.
- Depending on the selected signature validator, specify the server authentication credentials:
- For Notary v1, specify the following settings:
- Web address – the full web address of the server where image signatures are stored.
- Signature server authentication secret name – the name of the orchestrator secret with credentials for accessing the server where image signatures are stored.
The secret must be in the Kaspersky Container Security namespace.
- Certificate – a self-generated certificate for the server where signatures are stored. The certificate is provided in .PEM format.
- Delegations – list of signature holders participating in the signing process.
- Under Trusted roots, specify the pairs of all public keys that the solution will check during signature verification. A key pair includes the name and value of the key.
If necessary, you can add additional keys by clicking the Add key pair button. The solution supports up to 20 key pairs.
- For Cosign, specify the following settings:
- Signature server authentication secret name – the name of the orchestrator secret with credentials for accessing the server where image signatures are stored.
The secret must be in the Kaspersky Container Security namespace.
- Certificate – a self-generated certificate for the server where signatures are stored. The certificate is provided in .PEM format.
- Under Trusted roots, specify the pairs of all public keys that the solution will check during signature verification. A key pair includes the name and value of the key.
For Cosign, specify the public keys for the ECDSA or RSA algorithms provided by cosign.pub.
If necessary, you can add additional keys by clicking the Add key pair button. The solution supports up to 20 key pairs.
- In the Signature requirements section, specify the minimum number of signatures and signature holders who must sign the image.
- Signature server authentication secret name – the name of the orchestrator secret with credentials for accessing the server where image signatures are stored.
- For Notary v1, specify the following settings:
- Click the Save button in the top of the window to save the settings for integration with an image signature validator.
You can use the configured integration in runtime policies to ensure protection of the image content.
Page top
Viewing and editing information about integration with an image signature validator
To view and edit the settings for integration with an image signature validator:
- In the Administration → Integrations → Image signature validators section, click the integration name link in the list of integrations with signature validators.
- If necessary, in the window that opens, edit the integration settings, which depend on the selected signature validator, as follows:
- For Notary v1, you can modify the following settings:
- Validator name.
- Description.
- URL.
- Signature server authentication secret name.
- Certificate.
- Delegations.
- Key name.
- Key value.
- For Cosign, you can modify the following settings:
- Signature server authentication secret name.
- Certificate.
- Key name.
- Key value.
- Threshold.
- Required signers.
- For Notary v1, you can modify the following settings:
- If necessary, add key pairs by clicking the Add key pair button.
- Click the Save button in the upper part of the window.
Removing an integration with an image signature validator
To remove an integration with an image signature validator:
- Open the list of the configured integrations with image signature validators.
- Select the integration that you want to delete by selecting the check box in the row with the integration name.
- Click Delete above the table.
The Delete button becomes enabled after you select one or more integrations.
- In the window that opens, confirm the deletion.
Setting up integration with notification outputs
Kaspersky Container Security can notify users about events while operating in accordance with the response policy settings. To use the notification feature, you should set up an integration of Kaspersky Container Security with one or more notification outputs.
Kaspersky Container Security can use the following outputs:
- Telegram instant messaging system
Viewing the list of integrations with outputs
To view the list of configured integrations with outputs:
- Go to the Administration → Integrations → Notifications section.
- Depending on the type of notification you want, go to the Email tab or the Telegram tab.
The table with a list of all configured integrations displays the following information about existing integrations:
- Integration name.
- Updated by.
- Date and time of the last update.
- Status of the last connection to the output—Success or Error. If Error is displayed, the solution also displays a brief description of the connection error.
In the table, you can:
- Add new integrations with email or Telegram. Click Add integration above the table to open the integration settings window.
- View and edit the settings of integration with outputs. You can open the editing window by clicking the integration name link.
In this window, you can also click Test connection to see if integration with an output is completed.
- Delete integration with outputs.
Adding email integrations
To add an email integration:
- Under Administration → Integrations → Notifications, in the Email section, click Add integration.
The integration settings window opens.
- Specify the following information in the form:
- Name of the integration — Displayed in the response policy settings.
- User name and password of the account used to send messages.
- SMTP server name.
- E-mail encryption method.
- Port that the SMTP server uses.
- Email address of the message sender.
- Email addresses of message recipients. You can enter one or more addresses in this field.
- Click Test connection to see if a connection with email can be established.
- Click Add to save the email integration settings.
Example email integration settings
You can use the configured integration in response policies.
Page top
Viewing information about email integration
To view and change an email integration:
- In the Email section, under Administration → Integrations → Notifications, click the integration name link in the list of integrations.
- In the editing window that opens, change the following integration settings if necessary:
- Name.
- User name.
- Password of the user account that is used to send messages.
- SMTP server name.
- E-mail encryption method.
- Port that the SMTP server uses.
- Email address of the message sender.
- Email addresses of message recipients.
- Click Test connection to see if a connection with email can be established.
- Click Save.
Adding Telegram integrations
To add a Telegram integration:
- Under Administration → Integrations → Notifications, under Telegram, click Add integration.
The integration settings window opens.
- Specify the following information in the form:
- Name of the integration — Displayed in the response policy settings.
- ID of the chat to post the messages — you can get the ID in the following way:
- Write the first message to the message bot. The chat ID is generated the first time a message is sent.
- In the address bar of your browser, type:
https://api.telegram.org/bot<token>/getUpdateswhere <token> is the token of the message bot.
- In the received .json response file, find the "ID" value in the "chat" object. This is the chat ID.
After changing the message history visibility settings for new participants in a Telegram chat, the chat ID is also changed. In this case, you must change the Telegram integration settings and specify the new value for the chat ID.
- Token of the message bot — you receive this token as a result of executing the
/newbotcommand in the BotFather bot to create a bot. You can also get the token of a previously created bot by running the/tokencommand.
- Click Test connection to see if a connection with Telegram can be established.
- Click Add to save the Telegram integration settings.
Example Telegram integration settings
You can use the configured integration in response policies.
Page top
Viewing and editing information about integration with Telegram
To view and change a Telegram integration:
- Under Telegram in the Administration → Integrations → Notifications section, click the integration name link in the list of integrations.
- In the editing window that opens, change the following integration settings if necessary:
- Name.
- Chat ID.
- Bot token.
- Click Test connection to see if a connection with Telegram can be established.
- Click Save.
Deleting integrations with notification outputs
To delete email integration or Telegram integration:
- Open the list of configured email or Telegram integrations in the Administration → Integrations → Notifications section.
- Select the integration that you want to delete by selecting the check box in the row with the integration name.
- Click Delete above the table.
The Delete button becomes enabled after you select one or more integrations.
- In the window that opens, confirm the deletion.
You cannot delete an integration that is used in one or more response policies.
Page top
Configuring LDAP server integration
Kaspersky Container Security lets you connect to servers of external
that are used in your organization . This is an integration with a specific group in .Connection to an external directory service over the LDAP protocol enables you to perform the following tasks:
- Configure user accounts to take into account data from an external directory service for working with Kaspersky Container Security.
- Correlate user roles in Kaspersky Container Security to groups of users from Active Directory. Users in these groups will be able to use their domain account credentials to log in to the solution web interface and access application functionality based on their assigned role.
We recommended that you create these user groups in Active Directory in advance to allow them to complete authorization using their domain accounts in the Kaspersky Container Security web interface.
An email address must be indicated for user accounts in Active Directory.
Creating LDAP server integration
To create an integration with an LDAP server:
- In the Administration → Integrations → LDAP section, click the Connect server button.
The LDAP server settings window opens.
- Specify the following mandatory settings in the form fields:
- Web address (URL) of your company's LDAP server.
The web address of the LDAP server is specified as follows:
ldap://<host>:<port>. For example:ldap://ldap.example.com:389. - Base distinguished name—in the context of an LDAP name, this is the name that uniquely identifies and describes a record of the LDAP directory server.
For example, the base distinguished name for example.com is
dc=example, dc=com. - User authorization filter—in the context of an LDAP search, this is a filter that generates a user authorization request and indicates where to start searching for a user in the Active Directory catalog tree.
The filter for user authorization must be specified as follows:
sAMAccountName =% s, ou = Accounts. - Group filter for defining the group search settings in Active Directory.
- User filter for defining the user search settings in Active Directory.
- Web address (URL) of your company's LDAP server.
- Under Base schema, specify the values of the following attributes and classes of objects:
- Object class is the type of object to search for.
- Organizational unit class is the LDAP object class that identifies the object as a container object within the domain.
- User class is the LDAP object class that identifies the object as a user.
- Organization unit name is the attribute of a group that identifies its name.
- Group class is the class that identifies the LDAP object as a group.
- Distinguished name attribute is the unique distinguishing name of the record.
- Under User settings, specify the values of the following object attributes:
- User first name attribute.
- User lastname attribute.
- Group name attribute.
- User username attribute.
When authorizing with a user account, the username may need to be specified together with the realm in the following format:
<username @ realm>, for example, user@example.com. - User password.
- Group member.
- User email attribute.
- User member of.
- Click the Save button above the form for LDAP server integration data.
- To verify that the values were filled in correctly, click the Test connection button above the form for LDAP server integration data.
Kaspersky Container Security will display a notification informing you of the successful connection to the LDAP server or a failure to establish the connection.
Example of completed fields when configuring LDAP server integration
If the LDAP server certificate changes, reconfigure the integration.
You can use the configured integration when creating and assigning user roles.
Page top
Viewing, configuring, or deleting an LDAP server integration
To view the LDAP server connection:
Go to the Administration → Integrations → LDAP section.
Kaspersky Container Security displays the following information about the connected LDAP server:
- The web address of the connected LDAP server.
- The status of the last server connection—Success, Not available, or Error. If Error is displayed, the solution also displays a brief description of the connection error.
To edit LDAP server integration settings:
In the Administration → Integrations → LDAP section, click the Edit settings button.
Kaspersky Container Security opens the page containing the form for LDAP server integration data.
To delete an integration with an LDAP server:
- In the Administration → Integrations → LDAP section, click Delete integration.
- In the window that opens, confirm the deletion.
Testing connection with LDAP server
To test connection with the LDAP server:
- Go to the Administration → Integrations → LDAP section.
- Do one of the following:
- If the integration with the LDAP server is created, click the Test connection button.
- If you are creating an integration with an LDAP server, click the Test connection button above the form for LDAP server integration data.
Kaspersky Container Security will display a notification informing you of the connection to the LDAP server or a failure to establish the connection.
Gaining access to Active Directory group
After the integration with the LDAP server is configured, you can specify an Active Directory group for each Kaspersky Container Security role. After authorizing their account credentials, the users from this group gain access to solution functionality based on their defined roles.
Page top
Users, roles, and scopes
This section describes how to work with users and user roles, and provides instructions on how to create, edit, and delete them. This section also describes how to use scopes to give different levels of access to different user roles.
Managing users
Multiple users can have access to Kaspersky Container Security. A user account is created for each user, and one or more user roles are assigned to them.
The list of Kaspersky Container Security users is displayed in the table in the Administration → Access management → Users section.
You can do the following:
- Add users.
- View and edit user account settings.
- Reset password for the selected accounts.
- Delete users.
- Sort values in the list of users by clicking the
 icon in the corresponding column (displayed user name, user name, assigned role). Sorting can be done in alphabetic order and reverse alphabetical order.
icon in the corresponding column (displayed user name, user name, assigned role). Sorting can be done in alphabetic order and reverse alphabetical order. - Search by user name by using the Search by user name field above the table.
About user roles
A user role in Kaspersky Container Security is a set of permissions to perform certain actions in the solution web interface. Depending on their role, users have access to different sections and functional capabilities.
Kaspersky Container Security provides user roles as well as system roles, which have predefined sets of access permissions to perform common tasks for protecting container environments.
The following system roles are provided during initial installation of the solution:
- The Administrator of Kaspersky Container Security role is intended for users who are tasked with deploying and supporting the infrastructure and system software required for the solution to work (for example, operating systems, application servers, and databases). These users manage user accounts, roles and access permissions in Kaspersky Container Security.
In the web interface, this role is indicated by the KCSADM abbreviation.
- The Information Security Administrator (IS Administrator) role is intended for users who are tasked with creating and managing user accounts, roles and access permissions of users, changing settings, connecting public image registries, Agents and outputs, and configuring security policies.
In the web interface, this role is indicated by the ISADM abbreviation.
- The IS auditor role is intended for users who view the resources and user list of a solution, and who monitor the results of scans and compliance checks.
In the web interface, this role is indicated by the ISAUD abbreviation.
- The IS officer role is intended for users who view and manage security policies, connect public image registries, and view the results of runtime container analyses for projects in which these users are directly involved.
In the web interface, this role is indicated by the ISOFF abbreviation.
- The Developer role is intended for users who perform compliance checks and view the results of scanning images from registries and CI/CD, cluster resources and accepted risks.
In the web interface, this role is indicated by the DEV abbreviation.
You can assign system roles to user accounts when creating or viewing these user accounts.
Multiple user roles can be assigned to a user.
If a specific system role is not needed, you can delete it.
However, you cannot delete the last active system role that has permissions to manage other roles.
If the available system roles do not offer the required access permissions, you can create your own unique sets of permissions as custom roles.
When creating custom roles, consider the necessary set of permissions for accessing related functionalities. For example:
- To view and configure the settings of the response policies, you need permission to view integrations with notification services. If this permission is not granted, Kaspersky Container Security will display an error when you try to configure a response policy.
- Permissions to manage response policies must be granted with permissions to manage notifications, otherwise, you will not be able to select the outputs in the policy settings.
- To create a user, you need permission to view and manage roles. If such permission is not granted, only the dashboard is displayed to the created user.
- The permission to manage users must be granted together with the permission to manage roles, otherwise you will not be able to assign a role when creating a user.
You can assign user roles to user accounts just like with system roles. In addition, you can also change the settings of user roles and delete user roles.
When assigning the scopes to roles, you must take into account that a security policy can be implemented within a specific scope only if this scope is assigned to one of your roles.
If you integrated the solution with an LDAP server, Kaspersky Container Security also receives and displays the roles and user groups from the Active Directory service.
Page top
Working with system roles
The table below lists the main actions that are available to users with system roles in the Kaspersky Container Security web interface after installation.
User roles and their available actions
Action |
Administrator of Kaspersky Container Security |
IS Administrator |
IS auditor |
IS officer |
Developer |
|---|---|---|---|---|---|
View image scan results |
|
|
|
|
|
Manually start scanning images |
|
|
|
|
|
Manage risks (accept a risk, edit a risk and cancel risk acceptance) |
|
|
|
|
|
View accepted risks |
|
|
|
|
|
View clusters |
|
|
|
|
|
Manage clusters |
|
|
|
|
|
View registries |
|
|
|
|
|
Add an image to a registry |
|
|
|
|
|
Delete a repository/image from a registry |
|
|
|
|
|
View CI/CD scan results |
|
|
|
|
|
Manage CI/CD scanning |
|
|
|
|
|
View and manage agents |
|
|
|
|
|
View benchmark compliance results |
|
|
|
|
|
Start benchmark compliance check |
|
|
|
|
|
View scanner policies |
|
|
|
|
|
Manage scanner policies |
|
|
|
|
|
View assurance policies |
|
|
|
|
|
Manage assurance policies |
|
|
|
|
|
View response policies |
|
|
|
|
|
Manage response policies |
|
|
|
|
|
View runtime policies |
|
|
|
|
|
Manage runtime policies |
|
|
|
|
|
Viewing the File Threat Protection settings |
|
|
|
|
|
Managing the File Threat Protection settings |
|
|
|
|
|
View the list of users |
|
|
|
|
|
Manage users |
|
|
|
|
|
View roles and permission sets |
|
|
|
|
|
Manage roles and permission sets |
|
|
|
|
|
View scopes |
|
|
|
|
|
Manage scopes |
|
|
|
|
|
View the global scope |
|
|
|
|
|
Manage the global scope |
|
|
|
|
|
View the event log |
|
|
|
|
|
Viewing license information |
|
|
|
|
|
Manage licensing settings |
|
|
|
|
|
View image registry integrations |
|
|
|
|
|
View image registry integrations |
|
|
|
|
|
View integrations with image signature validators |
|
|
|
|
|
Manage integrations with image signature validators |
|
|
|
|
|
View integrations with notification systems |
|
|
|
|
|
Manage integrations with notification systems |
|
|
|
|
|
View reports |
|
|
|
|
|
Manage reports |
|
|
|
|
|
View and manage integration with LDAP server |
|
|
|
|
|
View and manage authentication settings |
|
|
|
|
|
Displaying list of roles
Kaspersky Container Security displays the list of active roles in the Administration → Access management → Roles section.
The table presents all active system roles and user roles and indicates ID, name, and number of users assigned to the specific role. If you have configured integration with LDAP, the table also shows Active Directory user groups that correspond to the user roles in Kaspersky Container Security.
Page top
About scopes
In Kaspersky Container Security, a scope is a resource list of reasons why the solution is being used (e.g. specific cluster, multiple external registries, or specific namespaces).
Scopes are used for the following purposes:
- To differentiate access to resources, for example, in order to monitor the operation of clusters, registries, or namespaces.
This access control is performed by assigning a scope when creating a scope or editing its settings.
- To distinguish the objects that policies and scans are applied to.
These objects are differentiated by assigning a scope when creating security policies or editing their settings.
In Kaspersky Container Security, you can add your own scopes or assign the default global scope to users.
The global scope includes access to all solution resources. This scope is added by default during installation of Kaspersky Container Security.
You cannot change the settings of the global scope or delete it.
Only a user with the appropriate rights can access the global scope. To assign global scope to other users and roles, you need to have permission to manage the global scope.
If you assign the global scope to a policy, the policy will be applied to all resources and applied in all environments.
Page top
Scopes and enforcement of security policies
In Kaspersky Container Security, scopes are specified for all security policies. To ensure that all necessary resources are scanned, each policy can be assigned one or more scopes. Moreover, the same scope can be specified in multiple policies.
Regardless of the number of policies implemented in a scope (for example, when scanning an image or scanning a cluster in a runtime), all security policies are applied.
When multiple security policies and multiple scopes are applied simultaneously, the following rules apply:
- For scanner policies: scanning is performed using a cumulative list of settings that is obtained by combining all scanner policies in force within the scope.
- For assurance policies: when scanning images, all policies applicable to the scanned resources are applied, in line with specified scopes.
- For response policies: when events occur, the user is notified using the notification tools specified in all response policies applicable to resources specified in the assigned scopes.
- For runtime policies: containers are monitored and, if necessary, blocked from running in the runtime in accordance with all applicable policies assigned to the scope.
Switching between scopes
In Kaspersky Container Security, several scopes can be assigned to a role. You can view the list of available scopes or switch scopes in order to access resources available in a different scope.
When switching between scopes, bear in mind the following:
- If you select the scope with resources by registry, in the section Resources → Assets → Clusters, Kaspersky Container Security does not display a list of clusters, namespaces, and pods. A full visual representation of the links between resources is displayed, but you cannot view information about an object that is outside of the available scope.
- Select the scope with resources by cluster, in the Resources → Assets → Registries section. Kaspersky Container Security then displays a list of the images used to start the containers in clusters.
- In the Scanners section, you can view lists of all scanners and scan tasks. However, you will not be able to view information about a scanned object if it is not within a scope that is available to you.
- In the Compliance → Kubernetes benchmarks section, Kaspersky Container Security displays a list of all nodes within clusters in the scope, regardless of the level of cluster detail in the scope. However, you cannot view information about a cluster node if it is not within a scope that is available to you.
- In the Policies section, Kaspersky Container Security shows the following:
- All policies in which at least one of the author's roles matches your role.
- All policies in which at least one scope matches the scope you selected.
- All policies that are linked to scopes assigned to your roles. However, you cannot delete these policies or edit their settings.
To switch the scope:
- Go to one of the following sections:
- Resources → Assets → Clusters.
- Resources → Assets → Registries.
- Compliance → Kubernetes benchmarks.
- Subsections of the Policies section: Scanner policies, Assurance policies, Response policies, or Runtime policies.
- In the drop-down list of available scopes in the upper right part of the window, select the required scope.
You can also activate all the scopes by selecting All in the list.
Adding users, roles, and scopes
To add a user account:
- In the Administration → Access management → Users section, click the Add user button above the list of users.
- In the window that opens, specify the following settings:
- User name is a unique value that must be assigned to a user for identification within Kaspersky Container Security.
A user name can include only letters of the English alphabet and numerals. The minimum user name length is 4 characters, and the maximum user name length is 254 characters.
- Display name (optional) is the value that is displayed in the solution web interface. If this parameter is not specified, the user name is displayed in the web interface.
- Email (optional).
- User name is a unique value that must be assigned to a user for identification within Kaspersky Container Security.
- Enter the password in the Password field.
Passwords have the following requirements:
- The password must contain numerals, special characters, and uppercase and lowercase letters.
- The minimum password length is 6 characters, and the maximum password length is 72 characters. The default password length is 8 characters.
- Confirm the entered password in the Confirm password field.
- Select the check box if the user should change the password the next time the solution starts.
- Assign a role to the user by selecting from the list of available roles.
While you are not required to assign a role when creating a user, a new user without an assigned role will not be able to interact with Kaspersky Container Security.
- Click Add.
To add a user, permission to view and configure settings is required. If you do not have this permission, any user you add will only be able to view the main page of the solution.
To add a user role:
- In the Administration → Access management → Roles section, click the Add role button above the list of roles.
- In the window that opens, specify the following values:
- Role ID is a unique value that must be assigned to a role for identification within Kaspersky Container Security.
The role ID can include uppercase Latin letters and numbers. A role ID cannot contain special characters or spaces.
- Role name is the value displayed in the solution web interface.
- Description (optional).
- Scope is a setting that is used to differentiate access to resources.
- Role ID is a unique value that must be assigned to a role for identification within Kaspersky Container Security.
- In the Active Directory mapping field, specify the Active Directory groups that the user belongs to.
- Select the check boxes next to the permissions that will be available for the role being added.
- Click Add.
To add a scope:
- In the Administration → Access management → Scopes section, click the Add scope button above the table with the list of scopes.
- In the window that opens, specify the scope name and, if necessary, a scope description.
- In the Resources section, select the resources for the scope:
- Click the Add resources by registry button, and in the drop-down list, select the registries for the scope. You can define a more specific scope by selecting specific repositories and images from these repositories in the drop-down list.
- Click the Add resources by cluster button and select the orchestrators for the scope from the drop-down list. You can define a more specific scope by selecting specific clusters, namespaces, and images from the orchestrators used to deploy the containers in the clusters.
You must specify at least one resource for which access is granted for monitoring.
- Click Set objects to scope.
- Save the scope by clicking the Save button.
Resetting password for user accounts
To reset the password for a user account,
- Go to the Administration → Access management → Users section.
- Do one of the following:
- In the user list, select the row of the specific user account, then click the Reset password link above the table.
- In the user account row, open the menu (
 ) and select Reset password.
) and select Reset password.
Changing settings for users, roles, and scopes
To edit a user account:
- In the Administration → Access management → Users section, click the user name in the list of users.
- In the opened window, make the necessary changes.
If you make changes to a user account with the administrator privileges, do not delete all roles, since doing so results in the loss of administrator access to the solution.
- Click Save.
To edit a user role:
- In the Administration → Access management → Roles section, click the role identifier in the Role ID column in the list of roles.
- In the opened window, make the necessary changes.
- Click Save.
After a role is modified, all users with the assigned role must be reauthorized.
You cannot edit a role if it is the last active system role with rights to manage user accounts, user roles, or the global scope.
To edit a scope:
- In the Administration → Access management → Scopes section, click on the scope name in the Scope name column of the table with the list of scopes.
- In the opened window, make the necessary changes.
- Click Save.
Removing users, roles, and scopes
To delete a user account:
- In the Administration → Access management → Users section, do one of the following:
- Select the user from the row of the specific user account, then click the Delete link above the table containing the list of users.
You can select one or more user accounts.
- In the row with the user account, open the menu (
 ) and select Delete user.
) and select Delete user.
- Select the user from the row of the specific user account, then click the Delete link above the table containing the list of users.
- In the window that opens, confirm deletion by clicking Delete.
The user account used for authorization in Kaspersky Container Security cannot be deleted.
To delete a user role:
- In the Administration → Access management → Roles section, in the role row in the list of roles, click the deletion icon (
 ).
). - In the window that opens, confirm deletion by clicking Delete.
You cannot delete the last active system role with rights to manage other user accounts, user roles, or the global scope.
You also cannot delete a role if it is assigned to any user.
To delete a scope:
- In the Administration → Access management → Scopes section, in the role row in the list of scopes, click the delete icon (
 ).
). - In the window that opens, confirm deletion by clicking Delete.
You cannot delete the default global scope.
You also cannot delete a scope if it is assigned to a different active user role.
Using Kaspersky Container Security OpenAPI
Kaspersky Container Security implements an Open Application Programming Interface (OpenAPI) that provides access to the functionality of the solution. For example, you can use Kaspersky Container Security OpenAPI to get information about solution components, create, modify, and delete objects, generate reports, and perform other actions.
For a full list of actions that you can perform using Kaspersky Container Security OpenAPI, please refer to the documentation describing OpenAPI requests.
The documentation for OpenAPI requests is available under Technical documentation in the Settings → About section. The documentation is a developer's guide in English. The developer's guide also provides code examples and detailed descriptions of callable items that are available in requests to the API server.
JSON is used to represent data in requests and responses.
Security event log
In the Administration → Events section, Kaspersky Container Security displays the occurred events that can be used for informational purposes, to track ongoing processes, to analyze security threats, and to determine what caused the solution failures.
Kaspersky Container Security displays the following types of events:
- Audit events. This group of events includes user activity audit data, such as information about configured settings of the solution, user authentications, changes in groups, and modifications or deletion of information within the solution.
- Solution operating results. These events include alerts about a triggered response policy.
- Records of the internal operations of solution applications.
Kaspersky Container Security shows the following security event categories:
- Administration—all events related to solution administration are logged.
- Policies (scanner policies, assurance policies, response policies, runtime policies) — events related to compliance or non-compliance of an image with applicable policies.
- Malware — events that occur when malware is detected during a scan of images and nodes.
- Sensitive data — events related to the detection of exposed sensitive data during a scan (for example, scanned images, functions, and nodes).
- Non-compliance — the following events are recorded:
- Detection of non-compliant images.
- Functions that do not comply with requirements, and runtime implementation of these functions.
- Nodes that do not comply with requirements, and runtime actions of these nodes.
A list of security events is displayed for a specific period. You can select one of the provided options or define your own time period. For any period you select, the time count begins from the current day. Events for the last week are displayed by default.
Kaspersky Container Security displays the events that occurred during scans. The events are displayed as a table for the following components:
- Administration.
- Alerts.
- CI/CD.
- Policies.
- Resources.
- Runtime.
- Scanners.
- API.
For each event, the table indicates the date and time of the event, IP address of the user, description, and status. The user name is listed for some events, such as those involving Administration, Malware, and Sensitive data categories. The security threat level is also indicated for Alerts. For events related to the Scanners component, the identifiers generated by the solution and the status of the scan jobs are also logged. For Runtime, the mode (Audit or Block), cluster, and deployed pod are indicated.
The security event log of Kaspersky Container Security is maintained and stored in PostgreSQL and does not have data protection mechanisms.
Exporting events to SIEM systems
Kaspersky Container Security allows you to send event messages to
for collection, analysis, and subsequent response to potential threats. The messages contain data for the same types and categories of events that are logged in the security event log.The data about the system events is transmitted as the integration with the SIEM system is configured during the installation of the solution. Event messages are forwarded to the SIEM registration server in the CEF format over TCP or UDP using the provided port (typically port 514). When the solution is deployed, these parameters are specified in the values.yaml configuration file:
CEF_PROTOCOL=tcp
CEF_HOST=<ip address>
CEF_PORT=<port>
The transmitted message consists of the following components:
- The header, which specifies the date, time, and host name.
- Prefix and CEF version number.
- Device vendor.
- Solution name.
- Solution version.
- Solution-generated unique event type code.
- Event description.
- Event severity assessment.
- Additional information, such as device IP address, event reason, event result, and event status.
Example of a message forwarded to a SIEM system
Page top
Information about the status of solution components
Kaspersky Container Security lets you view information about the status of components and integrations to diagnose and improve the operation of solution components and integrated third-party services. Status monitoring with the provision of performance data is conducted for the following components:
- Core components. Information is provided in the Components → Core section.
- Agents. The data is displayed in the Components → Agents section.
- Active integrations. Information is provided in the Administration → Integrations section.
Up-to-date data on the status of Kaspersky Container Security components is also recorded in the security event log.
You can view information about the status of solution components regardless of the status of the license (a license can be valid or expired).
Core status
Information on the status of the core components of Kaspersky Container Security is displayed in a table in the Components → Core section.
The following data is provided for each core component:
- Component name. The solution displays the components included in the distribution kit.
- Pod name (for example, kcs-postgres-0, kcs-scanner-xxx, or kcs-ih-xxx).
- Status. The solution assigns one of the following statuses:
- Good—the component is operating normally.
- Warning—the component detected malfunctions that do not impede the overall implementation of the component.
- Error—the component cannot be implemented due to its incorrect operation.
If the solution assigns the Warning or Error status to a kernel component, Kaspersky Container Security displays a brief description of the component failure.
The status is assigned in accordance with the data of the last heartbeat message for the component, according to the entry in the security event log.
- A log with a record of component events (for example, errors). You can download the log in text document format by clicking the Download log button in the Pod log column.
To view data on the status of kernel components, you must have rights to view the Core component. By default, these permissions are granted to the IS Administrator role.
Agent status
Information on the status of Kaspersky Container Security agents is presented as a table in the Components → Agents section; it is also expanded in the sidebar for the selected agent.
The table displays the following information for each agent within an agent group:
- Agent name.
- Status. The solution assigns one of the following connection statuses:
- Connected means the agent is connected and is functioning normally.
- Disconnected means the agent is disconnected.
- Pending means the solution is in the process of connecting the agent.
The status is assigned in accordance with the data of the last heartbeat message for the agent, according to the entry in the security event log.
- Version. The solution displays the current version of the agent. If a new version of the agent is available for the installed version of Kaspersky Container Security, the latest available agent version is displayed.
- Pod. The solution displays the name of the pod in which the agent is deployed.
- Information received as part of node status monitoring. The solution provides information about network activity monitoring and analysis actions, processes in containers, and File Threat Protection. For each action (Container processes, Network connections, and File Threat Protection), its status is displayed—Enabled or Disabled. If an agent is disconnected, all node status monitoring actions have the Disabled status.
If the agent is connected, the last status of the agent is also displayed for each action—Success, Not available, or Error. If Error is displayed, the solution displays a brief description of the error and associated details.
Agent statuses are displayed only for connected node-agents in which installed runtime agents scan the node. The status of kube-agents is always Not available because runtime agents are not deployed to them.
The solution displays this information based on the security event log records.
- Date and time of last connection.
You can view information about the status of a specific agent in the sidebar. To open the sidebar, double-click the agent name in the table. Kaspersky Container Security displays the following information about the selected agent:
- Agent name.
- IP address of the agent.
- The name of the pod with which the agent is associated.
- Name of the node where the agent is deployed.
- Agent type.
- Version of the node where the agent is deployed (primary or worker)
- The agent connection status—Connected, Disconnected, or Pending.
- Date and time when the agent last connected
- Under Node monitoring statuses, the solution displays information about the last registered state of the agent (Success, Not available, or Error) for each node monitoring action (Container processes, Network connections, and File Threat Protection). If an action is disabled to avoid unnecessary workload on nodes, the Disabled status is displayed.
- Under Agent group, the solution displays the following information about the agent group to which the selected agent belongs:
- Group name
- Namespace
- Orchestrator
To view information about the status of agents, you need permissions to view and manage the Agents component. By default, these permissions are granted to the IS Administrator role.
Integrations status
Information about the status of active Kaspersky Container Security integrations is displayed in the Administration → Integrations section. The solution displays status information for the following types of integrations:
To view information about the integration status, you need the following permissions:
- Permissions to view integrations with image registries. By default, these permissions are granted to the IS Administrator, IS Auditor, and IS Officer roles.
- Rights to view integrations with outputs. By default, these permissions are granted to the IS Administrator and IS Auditor roles.
- Permissions to view and manage the LDAP server integration. By default, these permissions are granted to the IS Administrator role.
Ensuring safety and reliability of components
To ensure safety and reliability of components, the following Auto Care mechanisms are implemented in Kaspersky Container Security:
- Automatic deletion of image scan history and system events. If data is kept for more than 90 days, it is considered obsolete and deleted.
Obsolete entries are checked once an hour.
- Automatic reconnection in case of a connection failure. Kaspersky Container Security conducts reconnection attempts every 30 seconds until the connection is restored.
Automatic reconnection is not performed for integrations with external registries and the LDAP server. They are connected when the solution sends a connection request.
- Image rescanning after a failed scan attempt. The scanner re-scans images until they are scanned or the number of scan attempts is exceeded.
Managing the dynamics of data accumulation
The operation of the Kaspersky Container Security components results in accumulation of a large amount of data, which require considerable disk space resources for storage. You can manage the dynamics of data accumulation by limiting the storage period and cleaning the database.
The following components of the solution carry the greatest load on the disk space:
- PostgreSQL DBMS
- S3 compatible file storage
- ClickHouse DBMS
PostgreSQL DBMS
We recommend that you contact the solution deployment engineer or Technical Support to connect to the PostgreSQL DBMS using the port forward option and the vacuum command.
You can reduce the risk of full database filling by adjusting the storage period of the most resource-intensive data: scan results and event logs. For this purpose, during the middleware (kcs-middleware) deployment you must specify the values of the following variables:
EVENT_LIFETIME_HOURSis a variable that defines the storage time for records in the event log.SCAN_LIFETIME_HOURSis a variable that determines the storage period for scan results.
Variable values are indicated in hours, the minimum allowable value is 1 hour. The default value is 2160 hours (90 days).
Before the middleware deployment with the adjusted values of the specified variables, you must stop the operation of the middleware (kcs-middleware) and the agent broker (kcs-ab). Otherwise, these components continue to process data while cleaning is conducted and may block this process.
In test (pilot) infrastructures where data integrity and consistency is not required or data can even be lost, you can use a faster cleaning method. To do this, you must delete PostgreSQL PV and create PostgreSQL PV again without data. The created Persistent Volume can be of the same size or larger.
S3-compatible file storage
The solution uses s3-compatible file storage only to store report files.
To clean up the storage when it is full, the cluster administrator must perform the following:
- Connect to the Minio file storage component (kcs-s3) using the port forward option.
- Download all reports and, if necessary, save them in another place for further storage.
- Delete data.
If necessary, you can increase Persistent Volume by using standard cluster tools.
ClickHouse DBMS
The settings of the tables in the Сlickhouse database of the solution require their constant clearing. If the load in the infrastructure is very high, resources may not have time to be cleaned. In this case, you can increase Persistent Volume by using standard cluster tools.
You must organize monitoring of free disk space and the dynamics of its use independently using third-party tools approved within the framework of the solution infrastructure.
Page top
Backing up and restoring data
PostgreSQL mechanisms can be used for PostgreSQL database backup and data recovery. You can use these for the PostgreSQL database in Kaspersky Container Security or an existing PostgreSQL database you may have.
Database backup copies are created using the pg_dump utility. The backup copy includes all main settings and PostgreSQL database objects, even if the database is used in parallel. If you have a backup copy, you can quickly restore the database.
Without a backup copy, a malfunction may lead to an irrecoverable loss of the information stored in the PostgreSQL database.
The pg_dump utility lets you export a PostgreSQL database as a script or in an archive format such as .TAR.
Example of using the pg_dump utility
To restore a PostgreSQL database from a backup copy, you can use the pg_restore utility. This allows you to restore a PostgreSQL database from an archive file created by the pg_dump utility. The pg_restore utility executes commands that restore the database to the state that existed when the database was saved.
Example of using the pg_restore utility
Page top
Contacting Technical Support
If you cannot find a solution to your problem in the application documentation or in other sources of information about the application, you should contact Technical Support. Technical Support experts will answer your questions about installing and using the application.
Kaspersky provides technical support for this application throughout its lifecycle (please refer to the product support lifecycle page). Before contacting Technical Support, please read the technical support rules.
You can contact Technical Support experts in one of the following ways:
- Visit the Technical Support website.
- Submit a request to Kaspersky Technical Support through the Kaspersky CompanyAccount portal.
Sources of information about the application
Kaspersky Container Security page on the Kaspersky website
On the Kaspersky Container Security page, you can view general information about the application, its functions and features.
Discussing Kaspersky applications on the Forum
If your question does not require an immediate answer, you can discuss it with Kaspersky experts and other users on our Forum.
On this Forum, you can view existing threads, leave your own comments, and create new discussion threads.
Page top
Limitations and warnings
Kaspersky Container Security 1.2 has a number of limitations that are not critical to the operation of the solution:
- To ensure maximum compatibility of BPF programs used by Kaspersky Container Security with numerous Linux distributions and Linux kernel versions, the solution uses eBPF CO-RE technology. Kaspersky Container Security works directly with the kernel of the Linux host server (node), thus the following requirements and restrictions must be observed:
- To use eBPF CO-RE, the Linux kernel must be compiled with configuration value
CONFIG_DEBUG_INFO_BTF = y. Most Linux distributions have this configuration value enabled when building the kernel that is supplied with the distribution. - If kernel versions are updated manually, you must check the availability of the above mentioned configuration value.
For earlier versions of Linux distributions and Linux kernels that do not have built-in support for eBPF CO-RE, backward compatibility is ensured by Kaspersky Container Security.
- To use eBPF CO-RE, the Linux kernel must be compiled with configuration value
- If a manually compiled Linux kernel is used on a host server (node), the following settings must be enabled during the kernel configuration to ensure runtime monitoring using container runtime profiles:
CONFIG_BPF=yCONFIG_BPF_SYSCALL=yCONFIG_BPF_EVENTS=yCONFIG_NET_CLS_BPF=mCONFIG_NET_ACT_BPF=mTo ensure better BPF code performance, we recommend enabling the following settings:
CONFIG_BPF_JIT = y
CONFIG_HAVE_BPF_JIT = y - If runtime monitoring using Kaspersky Container Security container runtime profiles is to be conducted simultaneously with CNI Cilium (node-agent pods are deployed on the same host servers with cilium-agent), the following actions must be performed:
- In the cluster with the deployed node-agent, specify the value of the
data.bpf-filter-priorityparameter for the ConfigMap cilium-config greater than 1.We recommend to specify 5 for the
data.bpf-filter-priorityparameter. - Restart the cilium-agent pods to apply the specified setting.
- In the cluster with the deployed node-agent, specify the value of the
- To access Kubernetes, Kaspersky Container Security uses the functionality of the dynamic admission controller provided in Kubernetes. The security of your cluster can be hardened by configuring authorization between the Kubernetes API and kube-agent, which ensures the operation of the solution's dynamic admission controller. Authorization must be configured in accordance with the Kubernetes instructions.
We recommend to limit access to kube-agent to data exchange with the Kubernetes API server. For this purpose, the following Kubernetes network policy must be applied:
---apiVersion: networking.k8s.io/v1kind: NetworkPolicymetadata:labels:app: kcsname: allow-kube-api-to-kube-agentnamespace: {{ $.Release.Namespace }}spec:podSelector:matchLabels:app: kube-agentingress:- from:- podSelector:matchLabels:component: kube-apiserverports:- protocol: TCPport: 8443
Glossary
CI/CD
Continuous Integration/Continuous Delivery is the combination of continuous software integration and continuous delivery in the development process.
CNI
Container Networking Interface is a project dedicated to standardized management of network interfaces in Linux containers and flexible extension of their network capabilities. CNI plug-ins ensure that the network interface is included in the container namespace and performs all necessary configuration on the host node.
CRI
The Container Runtime Interface (CRI) is used by the orchestrator to work with various container runtimes, without the need to recompile cluster components. The CRI defines the main protocol used for communication between cluster components and the container runtime.
CSI
Container Storage Interface is a specification that defines API parameters for adding and configuring storage in clusters.
CVE
Common Vulnerabilities and Exposures is the database for generally known information security vulnerabilities. Each vulnerability is given an identifier in the CVE-year-number format, description and several open links with descriptions.
CVSS
Common Vulnerability Scoring System is an open standard for scoring vulnerabilities. CVSS specifies a set of metrics and formulas for scoring vulnerability severity, with values from 0 (minimum) to 10 (maximum). CVSS makes it possible to allocate vulnerability response efforts based on vulnerability severity.
CycloneDX
CycloneDX is an SBOM standard that was developed for application security contexts and analysis of application components by assessing the availability and state of all software components.
Dynamic admission controller
A configurable Kubernetes admission controller that helps enforce policies and supports management and control.
Exploit
Program code that takes advantage of some vulnerability in the system or in application software. Exploits are frequently used to install malware on a computer without the user's knowledge.
FSTEC
The Russian Federal Service for Technical and Export Control.
IaC
Infrastructure as a Code is an approach to managing and describing infrastructure through configuration files instead of manually editing server configurations.
Init container
A special container that is started when the pod is initialized before the main containers are started. Init containers prepare the environment for operation (for example, they access secrets or redirect network traffic) and may contain utilities that are not necessary or desirable in the main container.
Kaspersky OpenTIP
The publicly available Kaspersky Threat Intelligence Portal information system. Contains information about cyberthreats, safe objects, and the relationships between them.
Kaspersky TIP
The Kaspersky Threat Intelligence Portal information system that is available with premium access. Provides additional tools for analyzing cyberthreats, including threat lookup and Kaspersky Cloud Sandbox, as well as analytical reports about APTs, financial crime software, industrial cybersecurity threats, and the digital activity of a specific organization.
LDAP
Lightweight Directory Access Protocol is a lightweight client-server protocol for accessing directory services.
Namespace
A virtual cluster inside a Kubernetes cluster which isolates cluster resources. Each namespace has its resources: services, pods, and deployments. The Resource names must be unique to operate in one namespace, although you can use the same names in other namespaces.
Node
A physical or virtual machine on which containers with applications are deployed and run. A Kubernetes cluster consists of several nodes. The cluster has a master node which manages the cluster and worker nodes where containers operate.
NVD
The National Vulnerability Database is the United States Government repository of standards-based vulnerability management data represented using the Security Content Automation Protocol.
PCI SSC
PCI Security Standards Council is a global forum dedicated to the ongoing development, enhancement, storage, dissemination, and implementation of security standards for payment card data protection.
Pipeline
Continuous software integration and continuous delivery (CI/CD) is performed in sequence one by one.
Pod
An abstract Kubernetes object, a group of one or more application containers, including shared storage (volumes), network settings, and information about application launch. Pod is the Kubernetes management unit.
RED OS
Russian general-purpose operating system RED OS supports scanning for vulnerabilities that can threaten the functioning of services and workstations.
SBOM
A Software Bill of Materials (SBOM) is a list of all object components. It also describes component dependencies and ways to validate and confirm source authenticity.
SIEM
Security information and event management is a class of software solutions that obtain and analyze data about security events.
Sigstore
It is a project aimed at developing and providing tools and services for the verification of software through the use of digital signatures. Sigstore also maintains a public registry to confirm the authenticity of changes to an image.
SPDX
Software Package Data Exchange (SPDX) is an international open standard for security, license compliance, and other artifacts of the software supply chain that is used to provide information about the origin, licensing, and security of software packages and their dependencies.
Syslog
A standard for sending and logging system event messages used for the UNIX and GNU/Linux platforms.
VDB (DSTD)
The Data Security Threats Database (DSTD or VDB) is a national vulnerability database maintained by the Russian Federal Service for Technical and Export Control (FSTEC).
Page top
Third party code information
Information about third-party code is provided under Settings → About platform. It can be found in the following files:
- legal_notices.txt, which can be downloaded in the Management console by clicking Third party code information in Kaspersky Container Security
- ftp_legal_notices.txt, which can be downloaded in the management console by clicking Third party code information in the File Threat Protection component
- kuu_legal_notices.txt, which can be downloaded in the Management console by clicking Third party code information in Kaspersky Update Utility
Trademark notices
Registered trademarks and service marks are the property of their respective owners.
Adobe is either a registered trademark or a trademark of Adobe in the United States and/or other countries.
Amazon and AWS are trademarks of Amazon.com, Inc. or its affiliates.
Apple and Safari are trademarks of Apple Inc.
Ubuntu is a registered trademark of Canonical Ltd.
ClamAV is a registered trademark or trademark of Cisco Systems, Inc. and/or its affiliates in the United States and certain other countries.
The Grafana Word Mark and Grafana Logo are either registered trademarks/service marks or trademarks/service marks of Coding Instinct AB, in the United States and other countries and are used with Coding Instinct’s permission. We are not affiliated with, endorsed or sponsored by Coding Instinct, or the Grafana community.
Docker and the Docker logo are trademarks or registered trademarks of Docker, Inc. in the United States and/or other countries. Docker, Inc. and other parties may also have trademark rights in other terms used herein.
Dropbox is a trademark of Dropbox, Inc.
Google, Google Chrome, Chromium, and Nexus are trademarks of Google LLC.
S3 is a trademark of International Business Machines Corporation registered in many jurisdictions around the world.
LinkedIn is a registered trademark or trademark of LinkedIn Corporation and its affiliates in the United States and/or other countries.
Linux is the registered trademark of Linus Torvalds in the U.S. and other countries.
CVE is a registered trademark of The MITRE Corporation.
OpenAPI is a trademark of the Linux Foundation.
Helm, Kubernetes is a registered trademark of The Linux Foundation in the United States and other countries.
Microsoft, Active Directory, Excel, Microsoft Edge, Windows, and Windows Server are trademarks of the Microsoft group of companies.
CVE is a registered trademark of The MITRE Corporation.
Mozilla and Firefox are trademarks of the Mozilla Foundation in the U.S. and other countries.
Oracle is a registered trademark of Oracle and/or its affiliates.
Red Hat, Red Hat Enterprise Linux, and CentOS are trademarks or registered trademarks of Red Hat, Inc. or its subsidiaries in the United States and other countries.
OpenShift is a registered trademark of Red Hat, Inc. in the United States and other countries.
Debian is a registered trademark of Software in the Public Interest, Inc.
Sonatype Nexus is a trademark of Sonatype, Inc.
SUSE is a registered trademark of SUSE LLC in the United States and other countries.
TWITCH is a trademark of Twitch Interactive, Inc. or its affiliates.
UNIX is a registered trademark in the United States and other countries, licensed exclusively through X/Open Company Limited.
ClickHouse is a trademark of YANDEX LLC.
Page top