Contents
Solution architecture
The Kaspersky Container Security platform consists of three main components:
- The Kaspersky Container Security Server has the following functions:
- Provides an interface for interactive management of the solution (Management Console).
- Ensures integration with external software components (SIEM, CI, image registries, LDAP, Telegram, email) and the receipt of information from them.
- Coordinates the operation of other solution components.
- Ensures the creation and management of security policies.
- Displays the results of solution operations.
- Kaspersky Container Security Agent (hereinafter also referred to as the Agent). This component runs as a containerized application and ensures the appropriate level of node security in accordance with the configured security policies, including control of the following:
- Runtime security of containers running on the nodes.
- Network interaction between pods and applications inside containers.
- Integration with the orchestration platform and flow of data necessary for analysis of the orchestrator configuration and its components.
- Startup of containers from trusted images to prevent unverified images from running.
Agents are installed to all nodes of clusters and all clusters requiring protection. Kaspersky Container Security works with two types of agents: cluster protection agents (csp-kube-agent) and node protection agents (csp-node-agent). Together they form groups of Agents. A separate group of Agents is created for each cluster. Many groups of Agents can be created for one installation of the solution.
If the cluster contains no agents, some of the solution functionality is unavailable (for example, runtime policies, resource monitoring).
- Kaspersky Container Security Scanner. This component scans configuration files and images in the connected registries, searches for and analyzes detected malware, and conducts checks when the solution is integrated into CI/CD.
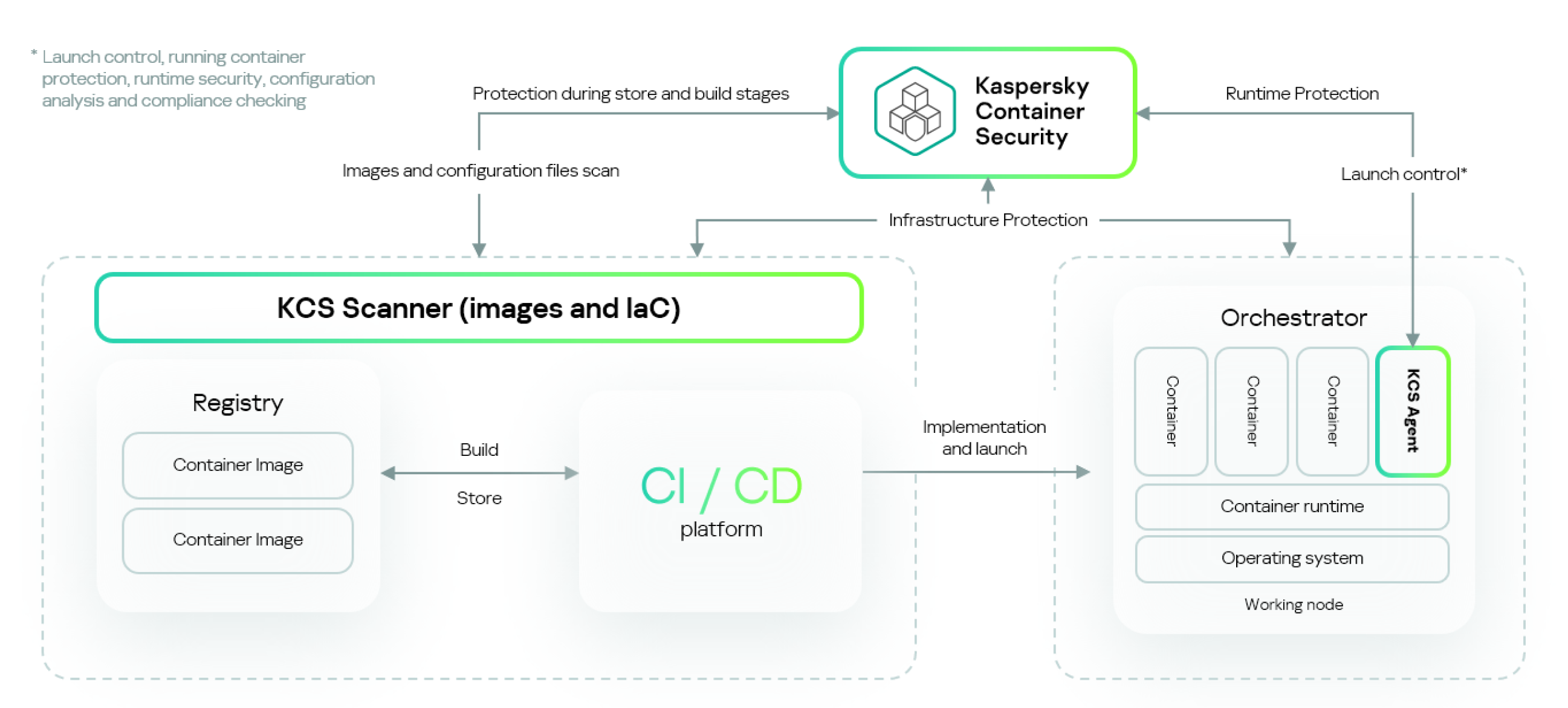
Overall architecture scheme of Kaspersky Container Security
Kaspersky Container Security can be deployed in a public or private corporate network.
Scanner
Scanner is a Kaspersky Container Security software component that scans objects in real time to assess their security and detect known vulnerabilities, malware, signs of sensitive data, and misconfigurations. The scanner lets you conduct security checks based on active security policies.
Kaspersky Container Security employs the following types of scanners:
- Vulnerability scanner based on the Common Vulnerabilities and Exposures (CVE) database
- File threat scanner within the File Threat Protection component
- Configuration file scanner
- Sensitive data (secrets) scanner
About object scans
Kaspersky Container Security checks objects deployed in the solution during the scanning process.
The scanning process searches for and analyzes threats and security risks associated with objects in the solution. Object scans must be performed regularly to keep track of emerging security threats.
When scanning, Kaspersky Container Security identifies the following security threats:
- Vulnerabilities
- Malware
- Misconfigurations
- Sensitive data
- Non-compliance with security policy requirements
Scanning process
The scanner receives scan jobs through the image handler. The image handler is an application deployed in the Kaspersky Container Security infrastructure that forwards scan jobs to the scanner and receives the scan results from the scanner.
When scan jobs are forwarded, the current status of the scanner is determined as one of the following:
- Free — the scanner is not processing objects and can accept a job from the image handler application if requested.
- Busy — the scanner is currently processing a scan job. A new job from the image handler application is put in the queue.
The scan job queue includes all forwarded scan jobs and is generated in the following cases:
- An image registry scan is manually started.
- An image registry scan is automatically started.
- A bulk scan of cluster objects is started.
Jobs in the scan queue receive the following statuses:
- Pending — status assigned by default when a job is created.
- In progress — the job is being processed by the image handler.
- Parsing results — the solution processes the job scanning results to display them in the interface.
- Error— scan job failed.
- Finished — the results of the scan job are available.
Scan tasks from the queue are submitted to the image handler in the order of their receipt. A job then goes to a scanner with Free status and is scanned for security issues. The scan results are sent back to the image handler. The job is considered completed and finished if scanning results are received. If a scan job was performed three or more times but received no results, the job is given the Error status.
Actions after scanning
After scanning, the solution displays the scan results. If security threats are detected in an object, Kaspersky Container Security prompts you to perform one of the following actions:
- Delete the security threat.
- Accept the security risk
File Threat Protection
When scanning registries and objects in CI/CD, Kaspersky Container Security uses the File Threat Protection component to search for and analyze potential file threats. The results of this malware scan are displayed together with the overall scan results.
The databases of the File Threat Protection component are updated from the Kaspersky Container Security update server.
After starting the utility, the File Threat Protection databases are downloaded and saved in the dedicated folder in the solution vendor's cloud object storage.
When the solution is deployed in a public corporate network, an update is performed directly from the update server. When installing the solution in a private corporate network, the updated File Threat Protection databases are added to the kcs-db-server container for subsequent running and updating.
Standard deployment schemes
Kaspersky Container Security supports the following deployment scenarios:
- Deployment in a public corporate network (Internet access from the Kubernetes cluster is allowed):
- Images from which the Kaspersky Container Security components are deployed are located in a public repository.
- After installation, the solution components refer to the vulnerability databases on the Internet.
- Databases are updated using the Update server on the Internet.
A private corporate network with access to servers in the allowed servers list may be considered a public corporate network.
- Deployment in a private corporate network (Internet access from the Kubernetes cluster is prohibited):
- An internal repository is used to host the images from which the Kaspersky Container Security components are deployed.
- Components are installed from a dedicated image with the vulnerability databases and security standards required to operate the solution.
- After installation, the solution components refer to vulnerability databases and security standards located in the corporate network.
- The Update server providing threat database updates is deployed as a separate component in the corporate network.
A private corporate network also allows for a deployment with a proxy server.
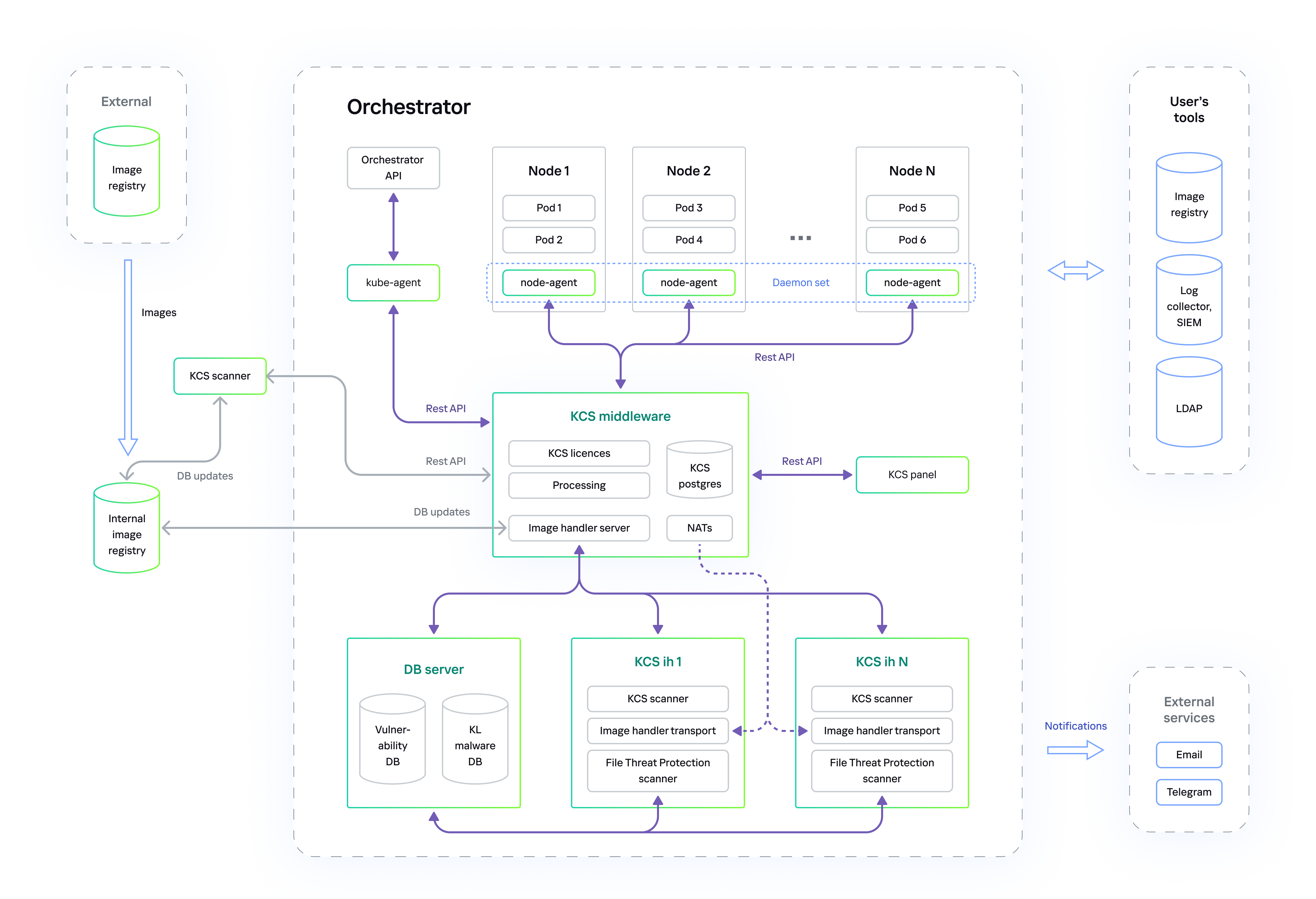
Deployment in a private corporate network
When deployed in a private corporate network, Kaspersky Container Security is prohibited from accessing the Internet from a cluster. The solution databases are updated by updating the images of the scanner that is run from the CI / CD and the image scanner.
Solution architecture when deployed in a private corporate network
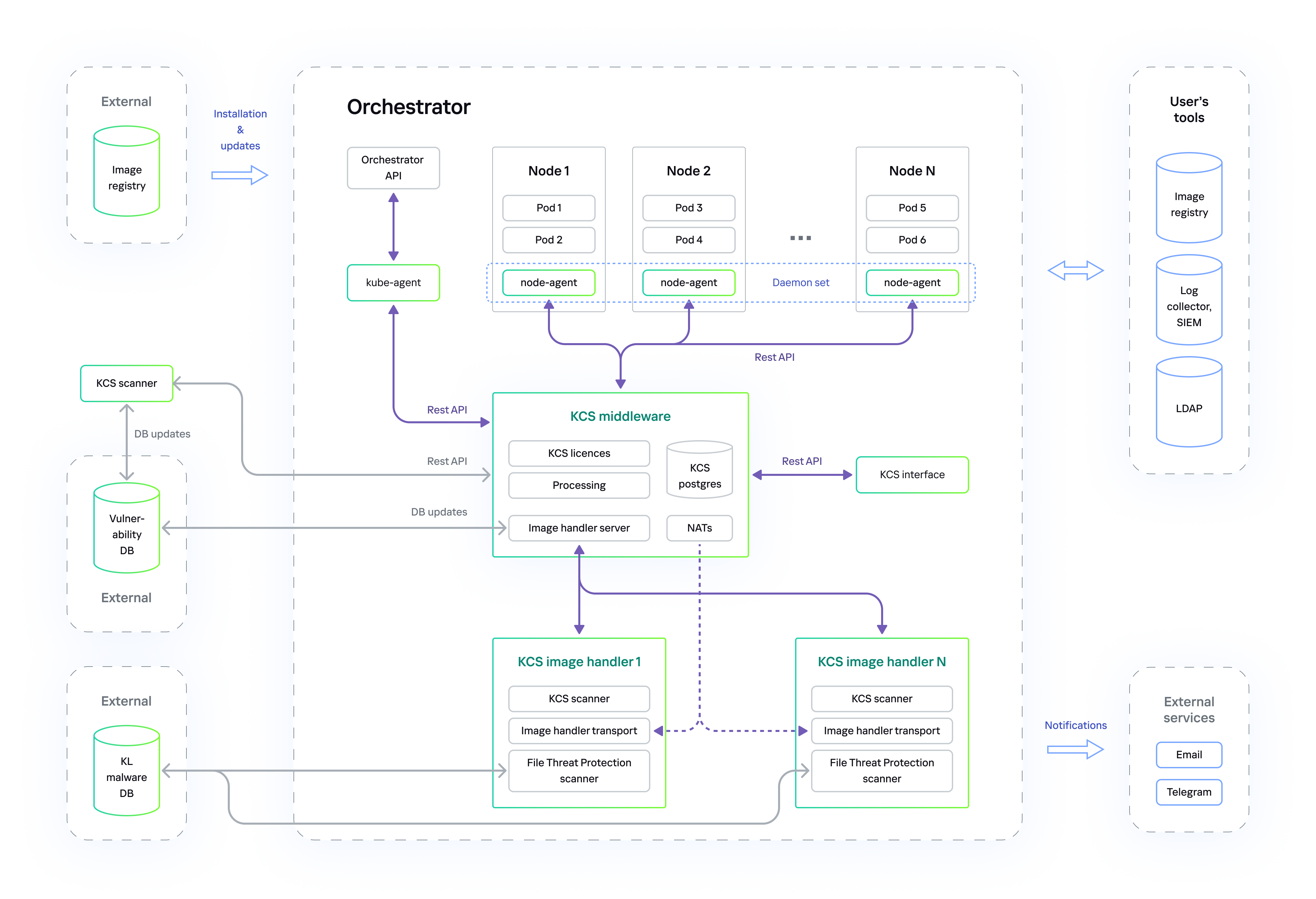
Page topDeployment in a public corporate network
When deployed in a public corporate network, Kaspersky Container Security is allowed to access the Internet from a cluster. The solution databases are updated from external databases containing updates for the vulnerabilities and malware databases.
Solution architecture when deployed in a public corporate network
Page top