Contents
- Configuring protection on a client organization's network
- Manual setup of Kaspersky Endpoint Security policy
- Manual setup of the group update task for Kaspersky Endpoint Security
- Manual setup of the group task for scanning a device with Kaspersky Endpoint Security
- Scheduling the Find vulnerabilities and required updates task
- Manual setup of the group task for updates installation and vulnerabilities fix
- Building a structure of administration groups and assigning distribution points
- Hierarchy of policies, using policy profiles
- Tasks
- Device moving rules
- Software categorization
- About multi-tenant applications
Configuring protection on a client organization's network
After Administration Server installation is complete, Administration Console launches and prompts you to perform the initial setup through the relevant wizard. When the Quick Start Wizard is running, the following policies and tasks are created in the root administration group:
- Policy of Kaspersky Endpoint Security
- Group task for updating Kaspersky Endpoint Security
- Group task for scanning a device with Kaspersky Endpoint Security
- Policy of Network Agent
- Vulnerability scan task (task of Network Agent)
- Updates installation and vulnerabilities fix task (task of Network Agent)
Policies and tasks are created with the default settings, which may turn out to be sub-optimal or even inadmissible for the organization. Therefore, you must check the properties of objects that have been created and modify them manually, if necessary.
This section contains information about manual configuration of policies, tasks, and other settings of Administration Server, and information about the distribution point, building an administration group structure and hierarchy of tasks, and other settings.
Manual setup of Kaspersky Endpoint Security policy
This section provides recommendations on how to configure the Kaspersky Endpoint Security policy, which is created by the Quick Start Wizard. You can perform the setup in the policy properties window.
When editing a setting, please keep in mind that you must click the lock icon above the relevant setting in order to allow using its value on a workstation.
Configuring the policy in the Advanced Threat Protection section
For a full description of the settings in this section, please refer to the Kaspersky Endpoint Security for Windows documentation.
In the Advanced Threat Protection section, you can configure the use of Kaspersky Security Network for Kaspersky Endpoint Security for Windows. You can also configure Kaspersky Endpoint Security for Windows modules, such as Behavior Detection, Exploit Prevention, Host Intrusion Prevention, and Remediation Engine.
In the Kaspersky Security Network subsection, we recommend that you enable the Use KSN Proxy option. Using this option helps to redistribute and optimize traffic on the network. If the Use KSN Proxy option is disabled, you can enable direct use of KSN servers.
Configuring the policy in the Essential Threat Protection section
For a full description of the settings in this section, please refer to the Kaspersky Endpoint Security for Windows documentation.
In the Essential Threat Protection section of the policy properties window, we recommend that you specify additional settings in the Firewall and File Threat Protection subsections.
The Firewall subsection contains settings that allow you to control the network activity of applications on the client devices. A client device uses a network to which one of the following statuses is assigned: public, local, or trusted. Depending on the network status, Kaspersky Endpoint Security can allow or deny network activity on a device. When you add a new network to your organization, you must assign an appropriate network status to it. For example, if the client device is a laptop, we recommend that this device use the public or trusted network, because the laptop is not always connected to the local network. In the Firewall subsection, you can check whether you correctly assigned statuses to the networks used in your organization.
To check the list of networks:
- In the policy properties, go to Essential Threat Protection → Firewall.
- In the Available networks section, click the Settings button.
- In the Firewall window that opens, go to the Networks tab to view the list of networks.
In the File Threat Protection subsection, you can disable the scanning of network drives. Scanning network drives can place a significant load on network drives. It is more convenient to perform indirect scanning, on file servers.
To disable scanning of network drives:
- In the policy properties, go to Essential Threat Protection → File Threat Protection.
- In the Security level section, click the Settings button.
- In the File Threat Protection window that opens, on the General tab clear the All network drives check box.
Configuring the policy in the General Settings section
For a full description of the settings in this section, please refer to the Kaspersky Endpoint Security for Windows documentation.
In the General Settings section of the policy properties window, we recommend that you specify additional settings in the Reports and Storage and Interface subsections.
In the Reports and Storage subsection, go to the Data transfer to Administration Server section. The About started application check box specifies whether the Administration Server database saves information about all versions of all software modules on the networked devices. If this check box is selected, the saved information may require a significant amount of disk space in the Kaspersky Security Center database (dozens of gigabytes). Clear the About started applications check box if it is selected in the top-level policy.
If Administration Console manages the Anti-Virus protection on the organization's network in centralized mode, disable the display of the Kaspersky Endpoint Security for Windows user interface on workstations. To do this, in the Interface subsection, go to the Interaction with user section, and then select Do not display option.
To enable password protection on workstations, in the Interface subsection, go to the Password protection section, click the Settings button, and then select the Enable password protection check box.
Configuring the policy in the Event configuration section
In the Event configuration section, you should disable the saving of any events on Administration Server, except for the following ones:
- On the Critical event tab:
- Application autorun is disabled
- Access denied
- Application startup prohibited
- Disinfection not possible
- License Agreement violated
- Could not load encryption module
- Cannot start two tasks at the same time
- Active threat detected. Start Advanced Disinfection
- Network attack detected
- Not all components were updated
- Activation error
- Error enabling portable mode
- Error in interaction with Kaspersky Security Center
- Error disabling portable mode
- Error changing application components
- Error applying file encryption / decryption rules
- Policy cannot be applied
- Process terminated
- Network activity blocked
- On the Functional failure tab: Invalid task settings. Settings not applied
- On the Warning tab:
- Self-Defense is disabled
- Incorrect reserve key
- User has opted out of the encryption policy
- On the Info tab: Application startup prohibited in test mode
Manual setup of the group update task for Kaspersky Endpoint Security
Information from this subsection is only applicable to Kaspersky Security Center 10 Maintenance Release 1 and later versions.
If the Administration Server acts as the update source, the optimal and recommended schedule option for Kaspersky Endpoint Security 10 and later versions is When new updates are downloaded to the repository with the Use automatically randomized delay for task starts check box selected.
For a group update task in Kaspersky Endpoint Security version 8 you must explicitly specify the launch delay (1 hour or longer) and select the Use automatically randomized delay for task starts check box.
If a local task for downloading updates from Kaspersky servers to the repository is created on each distribution point, periodic scheduling will be optimal and recommended for the Kaspersky Endpoint Security group update task. In this case, the randomization interval value should be set on 1 hour.
Page topManual setup of the group task for scanning a device with Kaspersky Endpoint Security
The Quick Start Wizard creates a group task for scanning a device. By default, the task is assigned a Run on Fridays at 7:00 PM schedule with automatic randomization, and the Run missed tasks check box is cleared.
This means that if devices in an organization are shut down on Fridays, for example, at 6:30 PM, the device scan task will never run. You must set up the most convenient schedule for this task based on the workplace rules adopted in the organization.
Scheduling the Find vulnerabilities and required updates task
The Quick Start Wizard creates the Find vulnerabilities and required updates task for Network Agent. By default, the task is assigned a Run on Tuesdays at 7:00 PM schedule with automatic randomization, and the Run missed tasks check box is selected.
If the organization's workplace rules provide for shutting down all devices at this time, the Find vulnerabilities and required updates task will run after the devices are turned on again, that is, on Wednesday morning. Such activity may be undesirable because a vulnerability scan may increase the load on CPUs and disk subsystems. You must set up the most convenient schedule for the task based on the workplace rules adopted in the organization.
Manual setup of the group task for updates installation and vulnerabilities fix
The Quick Start Wizard creates a group task for updates installation and vulnerabilities fix for Network Agent. By default, the task is set up to run every day at 01:00 AM, with automatic randomization, and the Run missed tasks option is not enabled.
If the organization's workplace rules provide for shutting down devices overnight, the update installation will never run. You must set up the most convenient schedule for the vulnerability scan task based on the workplace rules adopted in the organization. It is also important to keep in mind that installation of updates may require restarting the device.
Building a structure of administration groups and assigning distribution points
A structure of administration groups in Kaspersky Security Center performs the following functions:
- Sets the scope of policies.
There is an alternate way of applying relevant settings on devices, by using policy profiles. In this case, the scope of policies is set with tags, device locations in Active Directory organizational units, membership in Active Directory security groups, etc.
- Sets the scope of group tasks.
There is an approach to defining the scope of group tasks that is not based on a hierarchy of administration groups: use of tasks for device selections and tasks for specific devices.
- Sets access rights to devices, virtual Administration Servers, and secondary Administration Servers.
- Assigns distribution points.
When building the structure of administration groups, you must take into account the topology of the organization's network for the optimum assignment of distribution points. The optimum distribution of distribution points allows you to save traffic on the organization's network.
Depending on the organizational schema and network topology adopted by the MSP client, the following standard configurations can be applied to the structure of administration groups:
- Single office
- Multiple small detached offices
Standard MSP client configuration: Single office
In a standard "single-office" configuration, all devices are on the organization's network so they can "see" each other. The organization's network may consist of a few separate parts (networks or network segments) linked by narrow channels.
The following methods of building the structure of administration groups are possible:
- Building the structure of administration groups taking into account the network topology. The structure of administration groups may not reflect the network topology with absolute precision. A match between the separate parts of the network and certain administration groups would be enough. You can use automatic assignment of distribution points or assign them manually.
- Building the structure of administration groups, without taking the network topology into account. In this case, you must disable automatic assignment of distribution points and then assign one or several devices to act as distribution points for a root administration group in each of the separate parts of the network, for example, for the Managed devices group. All distribution points will be at the same level and will feature the same scope spanning all devices on the organization's network. In this case, each of Network Agents will connect to the distribution point that has the shortest route. The route to a distribution point can be traced with the tracert utility.
Standard MSP client configuration: Multiple small remote offices
This standard configuration provides for a number of small remote offices, which may be communicated with the head office via the internet. Each remote office is located behind the NAT, that is, connection from one remote office to another is not possible because offices are isolated from one another.
The configuration must be reflected in the structure of administration groups: a separate administration group must be created for each remote office (groups Office 1 and Office 2 in the figure below).
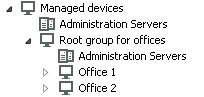
Remote offices are included in the administration group structure
One or multiple distribution points must be assigned to each administration group corresponding to an office. Distribution points must be devices at the remote office that have a sufficient amount of free disk space. Devices deployed in the Office 1 group, for example, will access distribution points assigned to the Office 1 administration group.
If some users move between offices physically, with their laptops, you must select two or more devices (in addition to the existing distribution points) in each remote office and assign them to act as distribution points for a top-level administration group (Root group for offices in the figure above).
Example: A laptop is deployed in the Office 1 administration group and then is moved physically to the office that corresponds to the Office 2 administration group. After the laptop is moved, Network Agent attempts to access the distribution points assigned to the Office 1 group, but those distribution points are unavailable. Then, Network Agent starts attempting to access the distribution points that have been assigned to the Root group for offices. Because remote offices are isolated from one another, attempts to access distribution points assigned to the Root group for offices administration group will only be successful when Network Agent attempts to access distribution points in the Office 2 group. That is, the laptop will remain in the administration group that corresponds to the initial office, but the laptop will use the distribution point of the office where it is physically located at the moment.
Hierarchy of policies, using policy profiles
This section provides information about how to apply policies to devices in administration groups. This section also provides information about policy profiles supported in Kaspersky Security Center, starting from version 10 Service Pack 1.
Hierarchy of policies
In Kaspersky Security Center, you use policies for defining a single collection of settings to multiple devices. For example, the policy scope of application P defined for administration group G includes managed devices with application P installed that have been deployed in group G and all of its subgroups, except for subgroups where the Inherit from parent group check box is cleared in the properties.
A policy differs from any local setting by lock icons ( ) next to its settings. If a setting (or a group of settings) is locked in the policy properties, you must, first, use this setting (or group of settings) when creating effective settings and, second, you must write the settings or group of settings to the downstream policy.
) next to its settings. If a setting (or a group of settings) is locked in the policy properties, you must, first, use this setting (or group of settings) when creating effective settings and, second, you must write the settings or group of settings to the downstream policy.
Creation of the effective settings on a device can be described as follows: the values of all settings that have not been locked are taken from the policy, then they are overwritten with the values of local settings, and then the resulting collection is overwritten with the values of locked settings taken from the policy.
Policies of the same application affect each other through the hierarchy of administration groups: Locked settings from the upstream policy overwrite the same settings from the downstream policy.
There is a special policy for out-of-office users. This policy takes effect on a device when the device switches into out-of-office mode. Out-of-office policies do not affect other policies through the hierarchy of administration groups.
The out-of-office policy will not be supported in further versions of Kaspersky Security Center. Policy profiles will be used instead of out-of-office policies.
Page topPolicy profiles
Applying policies to devices only through the hierarchy of administration groups may be inconvenient in many circumstances. It may be necessary to create several instances of a single policy that differ in one or two settings for different administration groups, and synchronize the contents of those policies in the future.
To help you avoid such problems, Kaspersky Security Center, starting from version 10 Service Pack 1, supports policy profiles. A policy profile is a named subset of policy settings. This subset is distributed on target devices together with the policy, supplementing it under a specific condition called the profile activation condition. Profiles only contain settings that differ from the "basic" policy, which is active on the client device (computer or mobile device). Activation of a profile modifies the policy settings that were active on the device before the profile was activated. Those settings take values that have been specified in the profile.
The following restrictions are currently imposed on policy profiles:
- A policy can include a maximum 100 profiles.
- A policy profile cannot contain other profiles.
- A policy profile cannot contain notification settings.
Contents of a profile
A policy profile contains the following constituent parts:
- Name Profiles with identical names affect each other through the hierarchy of administration groups with common rules.
- Subset of policy settings. Unlike the policy, which contains all the settings, a profile only contains settings that are actually required (locked settings).
- Activation condition is a logical expression with the device properties. A profile is active (supplements the policy) only when the profile activation condition becomes true. In all other cases, the profile is inactive and ignored. The following device properties can be included in that logical expression:
- Status of out-of-office mode.
- Properties of network environment—Name of the active rule for Network Agent connection.
- Presence or absence of specified tags on the device.
- Device location in Active Directory unit: explicit (the device is right in the specified OU), or implicit (the device is in an OU, which is within the specified OU at any nesting level).
- Device's membership in an Active Directory security group (explicit or implicit).
- Device owner's membership in an Active Directory security group (explicit or implicit).
- Profile disabling check box. Disabled profiles are always ignored and their respective activation conditions are not verified.
- Profile priority. The activation conditions of different profiles are independent, so several profiles can be activated simultaneously. If active profiles contain non-overlapping collections of settings, no problems will arise. However, if two active profiles contain different values of the same setting, an ambiguity will occur. This ambiguity is to be avoided through profile priorities: The value of the ambiguous variable will be taken from the profile that has the higher priority (the one that is rated higher in the list of profiles).
Behavior of profiles when policies affect each other through the hierarchy
Profiles with the same name are merged according to the policy merge rules. Profiles of an upstream policy have a higher priority than profiles of a downstream policy. If editing settings is prohibited in the upstream policy (it is locked), the downstream policy uses the profile activation conditions from the upstream one. If editing settings is allowed in the upstream policy, the profile activation conditions from the downstream policy are used.
Since a policy profile may contain the Device is offline property in its activation condition, profiles completely replace the feature of policies for out-of-office users, which will no longer be supported.
A policy for out-of-office users may contain profiles, but its profiles can only be activated after the device switches into out-of-office mode.
Page topTasks
Kaspersky Security Center manages Kaspersky security applications installed on devices by creating and running tasks. Tasks are required for installing, launching, and stopping applications, scanning files, updating databases and software modules, and performing other actions on applications.
Tasks for a specific application can be created only if the management plug-in for that application is installed.
Tasks can be performed on the Administration Server and on devices.
The following tasks are performed on the Administration Server:
- Automatic distribution of reports
- Downloading of updates to the repository of the Administration Server
- Backup of Administration Server data
- Maintenance of the database
- Windows Update synchronization
- Creation of an installation package based on the operating system (OS) image of a reference device
The following types of tasks are performed on devices:
- Local tasks—Tasks that are performed on a specific device
Local tasks can be modified either by the administrator, by using Administration Console tools, or by the user of a remote device (for example, through the security application interface). If a local task has been modified simultaneously by the administrator and the user of a managed device, the changes made by the administrator will take effect because they have a higher priority.
- Group tasks—Tasks that are performed on all devices of a specific group
Unless otherwise specified in the task properties, a group task also affects all subgroups of the selected group. A group task also affects (optionally) devices that have been connected to secondary and virtual Administration Servers deployed in the group or any of its subgroups.
- Global tasks—Tasks that are performed on a set of devices, regardless of whether they are included in any group
For each application, you can create any number of group tasks, global tasks, or local tasks.
You can make changes to the settings of tasks, view the progress of tasks, and copy, export, import, and delete tasks.
A task is started on a device only if the application for which the task was created is running.
Results of tasks are saved in the Microsoft Windows event log and the Kaspersky Security Center event log, both centrally on the Administration Server and locally on each device.
Do not include private data in task settings. For example, avoid specifying the domain administrator password.
Device moving rules
We recommend that you automate the allocation of devices to administration groups on the virtual server that corresponds to an MSP client, using device moving rules. A device moving rule consists of three main parts: a name, an execution condition (logical expression with the device attributes), and a target administration group. A rule moves a device to the target administration group if the device attributes meet the rule execution condition.
All device moving rules have priorities. The Administration Server checks the device attributes as to whether they meet the execution condition of each rule, in ascending order of priority. If the device attributes meet the execution condition of a rule, the device is moved to the target group, so the rule processing is complete for this device. If the device attributes meet the conditions of multiple rules, the device is moved to the target group of the rule with the highest priority (that is, has the highest rank in the list of rules).
Device moving rules can be created implicitly. For example, in the properties of an installation package or a remote installation task, you can specify the administration group to which the device must be moved after Network Agent is installed on it. Also, device moving rules can be created explicitly by the administrator of Kaspersky Security Center, in the list of moving rules. The list is located in Administration Console, in the properties of the Unassigned devices group.
By default, a device moving rule is intended for one-time initial allocation of devices to administration groups. The rule moves devices from the Unassigned devices group only once. If a device once was moved by this rule, the rule will never move it again, even if you return the device to the Unassigned devices group manually. This is the recommended way of applying moving rules.
You can move devices that have already been allocated to some of the administration groups. To do this, in the properties of a rule, clear the Move only devices that do not belong to an administration group check box.
Applying moving rules to devices that have already been allocated to some of the administration groups, significantly increases the load on the Administration Server.
You can create a moving rule that would affect a single device repeatedly.
We strongly recommend that you avoid moving a single device from one group to another repeatedly (for example, in order to apply a special policy to that device, run a special group task, or update the device through a specific distribution point).
Such scenarios are not supported, because they increase the load on Administration Server and network traffic to an extreme degree. These scenarios also conflict with the operating principles of Kaspersky Security Center (particularly in the area of access rights, events, and reports). Another solution must be found, for example, through the use of policy profiles, tasks for device selections, assignment of Network Agents according to the standard scenario, and so on.
Page topSoftware categorization
The main tool for monitoring the running of applications are Kaspersky categories (hereinafter also referred to as KL categories). KL categories help Kaspersky Security Center administrators to simplify the support of software categorization and minimize traffic going to managed devices.
User categories must only be created for applications that cannot be classified in any of the existing KL categories (for example, for custom-made software). User categories are created on the basis of an application installation package (MSI) or a folder with installation packages.
If a large collection of software is available, which has not been categorized through KL categories, it may be useful to create an automatically updated category. The checksums of executable files will be automatically added to this category on every modification of the folder containing distribution packages.
Do not create automatically updated categories of software for the folders My Documents, %windir%, %ProgramFiles%, and %ProgramFiles(x86)%. The pool of files in these folders is subject to frequent changes, which leads to an increased load on Administration Server and increased network traffic. You must create a dedicated folder with the collection of software and periodically add new items to it.
Page topAbout multi-tenant applications
Kaspersky Security Center enables administrators of service providers and tenant administrators to use Kaspersky applications with multitenancy support. After a multi-tenant Kaspersky application is installed in the infrastructure of a service provider, tenants can start using the application.
To separate tasks and policies related to different tenants, you must create a dedicated virtual Administration Server in Kaspersky Security Center for each tenant. All tasks and policies for multi-tenant applications running for a tenant must be created for the Managed devices administration group of the virtual Administration Server corresponding to that tenant. The tasks created for the administration groups related to the primary Administration Server do not affect the devices of tenants.
Unlike service provider administrators, a tenant administrator can create and view tasks and application policies only for the devices of the corresponding tenant. The sets of tasks and policy settings available to service provider administrators and tenant administrators are different. Some of the tasks and policy settings are not available to tenant administrators.
Within a hierarchical structure of a tenant, the policies created for multi-tenant applications are inherited to lower-level administration groups as well as to upper-level administration groups: the policy is propagated to all client devices that belong to the tenant.