Contents
- Integration between Kaspersky Security Center and other solutions
- Configuring access to KATA/KEDR Web Console
- Establishing a background connection
- Exporting events to SIEM systems
- Scenario: configuring event export to SIEM systems
- Before you begin
- About events in Kaspersky Security Center
- About event export
- About configuring event export in a SIEM system
- Marking of events for export to SIEM systems in Syslog format
- About exporting events using CEF and LEEF formats
- About exporting events using Syslog format
- Configuring Kaspersky Security Center for export of events to a SIEM system
- Exporting events directly from the database
- Viewing export results
Integration between Kaspersky Security Center and other solutions
This section describes how to configure access from Kaspersky Security Center Web Console to another Kaspersky application, such as Kaspersky Endpoint Detection and Response, and Kaspersky Managed Detection and Response, also this section describes how to configure export to SIEM systems.
Configuring access to KATA/KEDR Web Console
Kaspersky Anti Targeted Attack (KATA) and Kaspersky Endpoint Detection and Response (KEDR) are two functional blocks of Kaspersky Anti Targeted Attack Platform. You can manage these functional blocks through Web Console for Kaspersky Anti Targeted Attack Platform (KATA / KEDR Web Console). If you use both Kaspersky Security Center 13.1 Web Console and KATA / KEDR Web Console, you can configure access to KATA / KEDR Web Console directly from the interface of Kaspersky Security Center 13.1 Web Console.
To configure access to KATA / KEDR Web Console:
- In the Console settings drop-down list, select Integration.
The Console settings window opens.
- Select the Integration tab.
- On the Integration tab, select the KATA section.
- Enter the URL of KATA / KEDR Web Console in the URL to KATA/KEDR Web Console field.
- Click the Save button.
The Advanced management drop-down list is added to the main application window. You can use this menu to open KATA / KEDR Web Console. After you click Advanced Cybersecurity, a new tab opens in your browser with the URL that you specified.
Establishing a background connection
To enable Kaspersky Security Center 13.1 Web Console perform its background tasks, you have to establish a background connection between Kaspersky Security Center Web Console and Administration Server. You can establish this connection only if your account has the Modify object ACLs right of the General features: User permissions functional area.
If you install plug-in of Kaspersky Endpoint Security for Windows 11.6.0, or if you update the Kaspersky Endpoint Security for Windows plug-in from the version earlier than 11.7 and a background connection is not established yet, a notification is displayed that you have to establish a background connection. Also, you will have to grant the service account with the rights of the General features: Operations on Administration Server functional area.
To establish a background connection:
- In the Console settings drop-down list, select Integration.
The Console settings window opens.
- Select the Integration tab.
- On the Integration tab, select the Cross-service integration section.
- Switch the toggle button for establishing a background connection to the position: Establish a background connection for cross-service integration Enabled.
- In the opened The service that establishes a background connection will be started on the device where the Kaspersky Security Center Web Console Server is installed section, click the OK button.
The background connection between Kaspersky Security Center Web Console and Administration Server is established. Administration Server creates an account for the background connection and this account is used as a service account to maintain interaction between Kaspersky Security Center and another Kaspersky application or solution. The name of this service account contains the NWCSvcUser prefix.
Administration Server automatically changes the password of the service account once every 30 days, for security reasons. You cannot delete the service account manually. Administration Server deletes this account automatically when you disable a cross-service connection. Administration Server creates a single service account for each Administration Console and assigns all the service accounts to the security group with the name ServiceNwcGroup. Administration Server creates this security group automatically during the Kaspersky Security Center installation process. You cannot delete this security group manually.
Exporting events to SIEM systems
This section describes how to configure export of events to the SIEM systems.
Scenario: configuring event export to SIEM systems
Kaspersky Security Center allows configuring by one of the following methods: export to any SIEM system that use Syslog format, export to QRadar, Splunk, ArcSight SIEM systems that use LEEF and CEF formats or export of events to SIEM systems directly from the Kaspersky Security Center database. When you complete this scenario, Administration Server sends events to SIEM system automatically.
Prerequisites
Before you start configuration export of events in the Kaspersky Security Center:
- Learn more about the methods of event export.
- Make sure that you have the values of system settings.
You can perform the steps of this scenario in any order.
The process of export of events to SIEM system consists of the following steps:
- Configuring SIEM system to receive events from Kaspersky Security Center
How-to instructions: Configuring event export in a SIEM system
- Selecting events you want to export to SIEM system:
How-to instructions:
- Administration Console: Marking events of a Kaspersky application for export in Syslog format, Marking general events for export in Syslog format
- Kaspersky Security Center 13.1 Web Console: Marking events of a Kaspersky application for export in Syslog format, Marking general events for export in Syslog format
- Configuring export of events to SIEM system using one of the following methods:
- Using TCP/IP, UDP or TLS over TCP protocols.
How-to instructions:
- Administration Console: Configuring export of events to SIEM systems
- Kaspersky Security Center 13.1 Web Console: Configuring export of events to SIEM systems
- Using export of events directly from the Kaspersky Security Center database (A set of public views is provided in the Kaspersky Security Center database; you can find the description of these public views in the klakdb.chm document.)
- Using TCP/IP, UDP or TLS over TCP protocols.
Results
After configuring export of events to SIEM system you can view export results if you selected events which you want to export.
Before you begin
When setting up automatic export of events in the Kaspersky Security Center, you must specify some of the SIEM system settings. It is recommended that you check these settings in advance in order to prepare for setting up Kaspersky Security Center.
To successfully configure automatic sending of events to a SIEM system, you must know the following settings:
About events in Kaspersky Security Center
Kaspersky Security Center allows you to receive information about events that occur during the operation of Administration Server and Kaspersky applications installed on managed devices. Information about events is saved in the Administration Server database. You can export this information to external SIEM systems. Exporting event information to external SIEM systems enables administrators of SIEM systems to promptly respond to security system events that occur on managed devices or administration groups.
Event types
In Kaspersky Security Center, there are the following types of events:
- General events. These events occur in all managed Kaspersky applications. An example of a general event is Virus outbreak. General events have strictly defined syntax and semantics. General events are used, for instance, in reports and dashboards.
- Managed Kaspersky applications-specific events. Each managed Kaspersky application has its own set of events.
Event sources
Events can be generated by the following applications:
- Kaspersky Security Center components:
- Managed Kaspersky applications
For details about the events generated by Kaspersky managed applications, refer to the documentation of the corresponding application.
You can view the full list of events that can be generated by an application on the Event configuration tab in the application policy. For Administration Server, you can additionally view the event list in the Administration Server properties.
Importance level of events
Each event has its own importance level. Depending on the conditions of its occurrence, an event can be assigned various importance levels. There are four importance levels of events:
- A critical event is an event that indicates the occurrence of a critical problem that may lead to data loss, an operational malfunction, or a critical error.
- A functional failure is an event that indicates the occurrence of a serious problem, error or malfunction that occurred during operation of the application or while performing a procedure.
- A warning is an event that is not necessarily serious, but nevertheless indicates a potential problem in the future. Most events are designated as warnings if the application can be restored without loss of data or functional capabilities after such events occur.
- An info event is an event that occurs for the purpose of informing about successful completion of an operation, proper functioning of the application, or completion of a procedure.
Each event has a defined storage term, during which you can view or modify it in Kaspersky Security Center. Some events are not saved in the Administration Server database by default because their defined storage term is zero. Only events that will be stored in the Administration Server database for at least one day can be exported to external systems.
About event export
You can use event export within centralized systems that deal with security issues on an organizational and technical level, provide security monitoring services, and consolidate information from different solutions. These are SIEM systems, which provide real-time analysis of security alerts and events generated by network hardware and applications, or Security Operation Centers (SOCs).
These systems receive data from many sources, including networks, security, servers, databases, and applications. SIEM systems also provide functionality to consolidate monitored data in order to help you avoid missing critical events. In addition, the systems perform automated analysis of correlated events and alerts in order to notify the administrators of immediate security issues. Alerting can be implemented through a dashboard or can be sent through third-party channels such as email.
The process of exporting events from Kaspersky Security Center to external SIEM systems involves two parties: an event sender, Kaspersky Security Center, and an event receiver, a SIEM system. To successfully export events, you must configure this in your SIEM system and in the Kaspersky Security Center Administration Console. It does not matter which side you configure first. You can configure the transmission of events in the Kaspersky Security Center and then configure the receipt of events by the SIEM system, or vice versa.
Methods for sending events from Kaspersky Security Center
There are three methods for sending events from Kaspersky Security Center to external systems:
- Sending events over the Syslog protocol to any SIEM system
Using the Syslog protocol, you can relay any events that occur on the Kaspersky Security Center Administration Server and in Kaspersky applications that are installed on managed devices. When exporting events over the Syslog protocol, you can select exactly which types of events will be relayed to the SIEM system. The Syslog protocol is a standard message-logging protocol. For this reason, you can use the Syslog protocol to export events to any SIEM system.
- Sending events over the CEF and LEEF protocols to QRadar, Splunk, and ArcSight systems
You can use the CEF and LEEF protocols to export general events. When exporting events over the CEF and LEEF protocols, you do not have the capability to select specific events to export. Instead, all general events are exported. Unlike the Syslog protocol, the CEF and LEEF protocols are not universal. CEF and LEEF are intended for the appropriate SIEM systems (QRadar, Splunk, and ArcSight). Therefore, when you choose to export events over one of these protocols, you use the required parser in the SIEM system.
To export events over the CEF and LEEF protocols, the Integration with the SIEM systems feature must be activated in Administration Server by using an active license key or valid activation code.
- Directly from the Kaspersky Security Center database to any SIEM system
This method of exporting events can be used to receive events directly from public views of the database by means of SQL queries. The results of a query are saved to an XML file that can be used as input data for an external system. Only events available in public views can be exported directly from the database.
Receipt of events by the SIEM system
The SIEM system must receive and correctly parse events received from Kaspersky Security Center. For these purposes, you must properly configure the SIEM system. The configuration depends on the specific SIEM system utilized. However, there are a number of general steps in the configuration of all SIEM systems, such as configuring the receiver and the parser.
About configuring event export in a SIEM system
The process of exporting events from Kaspersky Security Center to external SIEM systems involves two parties: an event sender—Kaspersky Security Center and an event receiver—SIEM system. You must configure the export of events in your SIEM system and in the Kaspersky Security Center.
The settings that you specify in the SIEM system depend on the particular system that you are using. Generally, for all SIEM systems you must set up a receiver and, optionally, a message parser to parse received events.
Setting up the receiver
To receive events sent by Kaspersky Security Center, you must set up the receiver in your SIEM system. In general, the following settings must be specified in the SIEM system:
Depending on the SIEM system that you use, you may have to specify some additional receiver settings.
The figure below shows the receiver setup screen in ArcSight.
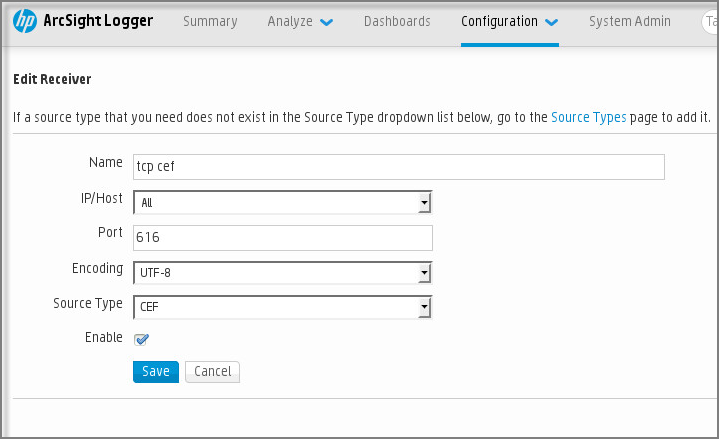
Receiver setup in ArcSight
Message parser
Exported events are passed to SIEM systems as messages. These messages must be properly parsed so that information on the events can be used by the SIEM system. Message parsers are part of the SIEM system; they are used to split the contents of the message into the relevant fields, such as event ID, severity, description, parameters and so on. This enables the SIEM system to process events received from Kaspersky Security Center so that they can be stored in the SIEM system database.
Each SIEM system has a set of standard message parsers. Kaspersky also provides message parsers for some SIEM systems, for example, for QRadar and ArcSight. You can download these message parsers from the websites of the corresponding SIEM systems. When configuring the receiver, you can select to use one of the standard message parsers or a message parser from Kaspersky.
Marking of events for export to SIEM systems in Syslog format
This section describes how to mark events for further export to SIEM systems in Syslog format.
About marking events for export to SIEM system in the Syslog format
After enabling automatic export of events, you must select which events will be exported to the external SIEM system.
You can configure export of events in the Syslog format to an external system based on one of the following conditions:
- Marking general events. If you mark events to export in a policy, in the settings of an event, or in the Administration Server settings, the SIEM system will receive the marked events that occurred in all applications managed by the specific policy. If exported events were selected in the policy, you will not be able to redefine them for an individual application managed by this policy.
- Marking events for a managed application. If you mark events to export for a managed application installed on a managed device, the SIEM system will receive only the events that occurred in this application.
Marking events of a Kaspersky application for export in the Syslog format
If you want to export events that occurred in a specific managed application installed on the managed devices, mark the events for export in the application policy. In this case, the marked events are exported from all of the devices included in the policy scope.
To mark events for export for a specific managed application:
- In the main menu, go to DEVICES → POLICIES & PROFILES.
- Click the policy of the application for which you want to mark events.
The policy settings window opens.
- Go to the Event configuration section.
- Select the check boxes next to the events that you want to export to a SIEM system.
- Click the Mark for export to SIEM system by using Syslog button.
You can also mark an event for export to a SIEM system in the Event registration section, which opens by clicking the link of the event.
- A check mark (
 ) appears in the Syslog column of the event or events that you marked for export to the SIEM system.
) appears in the Syslog column of the event or events that you marked for export to the SIEM system. - Click the Save button.
The marked events from the managed application are ready to be exported to a SIEM system.
You can mark which events to export to a SIEM system for a specific managed device. If previously exported events were marked in an application policy, you will not be able to redefine the marked events for a managed device.
To mark events for export for a managed device:
- In the main menu, go to DEVICES → MANAGED DEVICES.
The list of managed devices is displayed.
- Click the link with the name of the required device in the list of managed devices.
The properties window of the selected device is displayed.
- Go to the Applications section.
- Click the link with the name of the required application in the list of applications.
- Go to the Event configuration section.
- Select the check boxes next to the events that you want to export to SIEM.
- Click the Mark for export to SIEM system by using Syslog button.
Also, you can mark an event for export to a SIEM system in the Event registration section, that opens by clicking the link of the event.
- A check mark (
 ) appears in the Syslog column of the event or events that you marked for export to the SIEM system.
) appears in the Syslog column of the event or events that you marked for export to the SIEM system.
From now on, Administration Server sends the marked events to the SIEM system if export to the SIEM system is configured.
Marking general events for export in Syslog format
You can mark general events that Administration Server will export to SIEM systems by using the Syslog format.
To mark general events for export to a SIEM system:
- Do one of the following:
- Click the settings icon (
 ) next to the name of the required Administration Server.
) next to the name of the required Administration Server. - In the main menu, go to DEVICES → POLICIES & PROFILES, and then click a link of a policy.
- Click the settings icon (
- In the window that opens, go to the Event configuration tab.
- Click Mark for export to SIEM system by using Syslog.
Also, you can mark an event for export to SIEM system in the Event registration section, that opens by clicking the link of the event.
- A check mark (
 ) appears in the Syslog column of the event or events that you marked for export to the SIEM system.
) appears in the Syslog column of the event or events that you marked for export to the SIEM system.
From now on, Administration Server sends the marked events to the SIEM system if export to the SIEM system is configured.
About exporting events using CEF and LEEF formats
You can use the CEF and LEEF formats to export to SIEM systems general events, as well as the events transferred by Kaspersky applications to the Administration Server. The set of export events is predefined, and you cannot select the events to be exported.
To export events over the CEF and LEEF protocols, the Integration with the SIEM systems feature must be activated in Administration Server by using an active license key or valid activation code.
Select the format of export on the basis of the SIEM system used. The table below shows SIEM systems and the corresponding formats of export.
Formats of event export to a SIEM system
SIEM system |
Format of export |
|---|---|
QRadar |
LEEF |
ArcSight |
CEF |
Splunk |
CEF |
- LEEF (Log Event Extended Format)—A customized event format for IBM Security QRadar SIEM. QRadar can integrate, identify, and process LEEF events. LEEF events must use UTF-8 character encoding. You can find detailed information on LEEF protocol in IBM Knowledge Center.
- CEF (Common Event Format)—An open log management standard that improves the interoperability of security-related information from different security and network devices and applications. CEF enables you to use a common event log format so that data can easily be integrated and aggregated for analysis by an enterprise management system.
Automatic export means that Kaspersky Security Center sends general events to the SIEM system. Automatic export of events starts immediately after you enable it. This section explains in detail how to enable automatic event export.
About exporting events using Syslog format
You can use the Syslog format to export to SIEM systems the events that occur in Administration Server and other Kaspersky applications installed on managed devices.
Syslog is a standard for message logging protocol. It permits separation of the software that generates messages, the system that stores them, and the software that reports and analyzes them. Each message is labeled with a facility code, indicating the software type that generates the message, and is assigned a severity level.
The Syslog format is defined by Request for Comments (RFC) documents published by the Internet Engineering Task Force (internet standards). The RFC 5424 standard is used to export the events from Kaspersky Security Center to external systems.
In Kaspersky Security Center, you can configure export of the events to the external systems using the Syslog format.
The export process consists of two steps:
- Enabling automatic event export. At this step, Kaspersky Security Center is configured so that it sends events to the SIEM system. Kaspersky Security Center starts sending events immediately after you enable automatic export.
- Selecting the events to be exported to the external system. At this step, you select which event to export to the SIEM system.
Configuring Kaspersky Security Center for export of events to a SIEM system
This article describes how to configure export of events to SIEM systems.
To configure export to SIEM systems in the Kaspersky Security Center 13.1 Web Console:
- In the Console settings drop-down list, select Integration.
The Console settings window opens.
- Select the Integration tab.
- On the Integration tab, select the SIEM section.
- Click the Settings link.
The Export settings section opens.
- Specify the settings in the Export settings section:
If you select Syslog format, you must specify:
- Switch the option to the Automatically export events to SIEM system database ENABLED position.
- Click the Save button.
Export to SIEM system is configured.
Exporting events directly from the database
You can retrieve events directly from the Kaspersky Security Center database without having to use the Kaspersky Security Center interface. You can either query the public views directly and retrieve the event data or create your own views on the basis of existing public views and address them to get the data you need.
Public views
For your convenience, a set of public views is provided in the Kaspersky Security Center database. You can find the description of these public views in the klakdb.chm document.
The v_akpub_ev_event public view contains a set of fields that represent the event parameters in the database. In the klakdb.chm document you can also find information on public views corresponding to other Kaspersky Security Center entities, for example, devices, applications, or users. You can use this information in your queries.
This section contains instructions for creating an SQL query by means of the klsql2 utility and a query example.
To create SQL queries or database views, you can also use any other program for working with databases. Information on how to view the parameters for connecting to the Kaspersky Security Center database, such as instance name and database name, is given in the corresponding section.
Creating an SQL query using the klsql2 utility
This section describes how to download and use the klsql2 utility, and how to create an SQL query by using this utility. When you create an SQL query by means of the klsql2 utility, you do not have to provide database name and access parameters, because the query addresses Kaspersky Security Center public views directly.
To download and use the klsql2 utility:
- Download the klsql2 utility from Kaspersky website.
- Copy and extract the downloaded klsql2.zip file to any folder on the device with Kaspersky Security Center Administration Server installed.
The klsql2.zip package includes the following files:
- klsql2.exe
- src.sql
- start.cmd
- Open the src.sql file in any text editor.
- In the src.sql file, type the SQL query that you want, and then save the file.
- On the device with Kaspersky Security Center Administration Server installed, in the command line, type the following command to run the SQL query from the src.sql file and save the results to the result.xml file:
klsql2 -i src.sql -o result.xml - Open the newly created result.xml file to view the query results.
You can edit the src.sql file and create any query to the public views. Then, from the command line, execute your query and save the results to a file.
Example of an SQL query in the klsql2 utility
This section shows an example of an SQL query, created by means of the klsql2 utility.
The following example illustrates retrieval of the events that occurred on devices during the last seven days, and display of the events ordered by the time they occur, the most recent events are displayed first.
Example: SELECT e.nId, /* event identifier */ e.tmRiseTime, /* time, when the event occurred */ e.strEventType, /* internal name of the event type */ e.wstrEventTypeDisplayName, /* displayed name of the event */ e.wstrDescription, /* displayed description of the event */ e.wstrGroupName, /* name of the group, where the device is located */ h.wstrDisplayName, /* displayed name of the device, on which the event occurred */ CAST(((h.nIp / 16777216) & 255) AS varchar(4)) + '.' + CAST(((h.nIp / 65536) & 255) AS varchar(4)) + '.' + CAST(((h.nIp / 256) & 255) AS varchar(4)) + '.' + CAST(((h.nIp) & 255) AS varchar(4)) as strIp /* IP-address of the device, on which the event occurred */ FROM v_akpub_ev_event e INNER JOIN v_akpub_host h ON h.nId=e.nHostId WHERE e.tmRiseTime>=DATEADD(Day, -7, GETUTCDATE()) ORDER BY e.tmRiseTime DESC |
Viewing the Kaspersky Security Center database name
It can be helpful to know a database name if you need, for example, send an SQL query and connect to the database from your SQL script editor.
To view the name of the Kaspersky Security Center database:
- In the Kaspersky Security Center console tree, open the context menu of the Administration Server folder and select Properties.
- In the Administration Server properties window, in the Sections pane select Advanced and then Details of current database.
- In the Details of current database section, note the following database properties (see figure below):
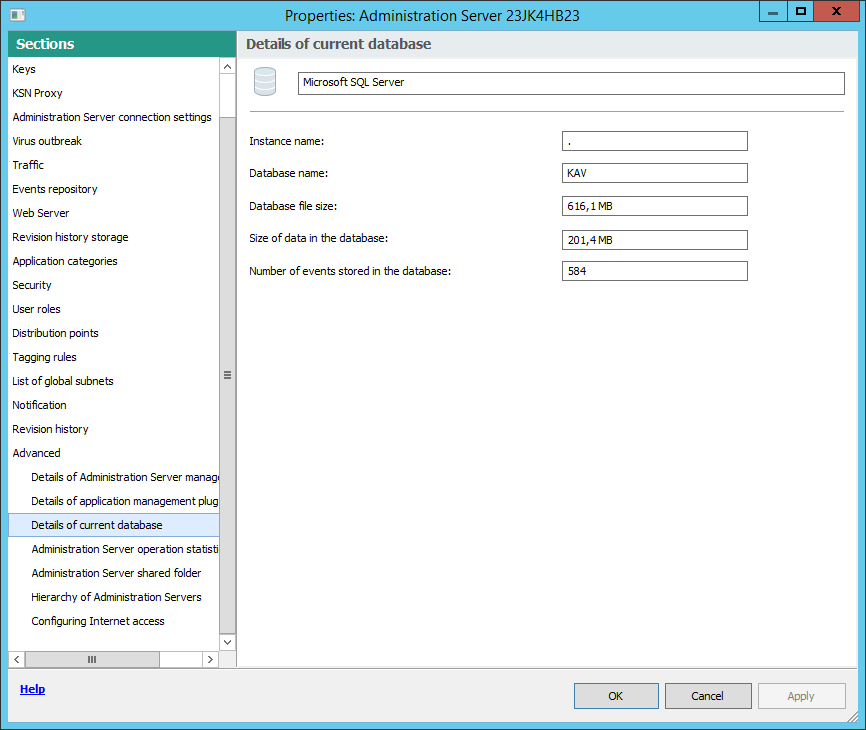
Section with information about the current Administration Server database
- Click the OK button to close the Administration Server properties window.
Use the database name to address the database in your SQL queries.
Viewing export results
You can control for successful completion of the event export procedure. To do this, check whether messages with export events are received by your SIEM system.
If the events sent from Kaspersky Security Center are received and properly parsed by your SIEM system, configuration on both sides is done properly. Otherwise, check the settings you specified in Kaspersky Security Center against the configuration in your SIEM system.
The figure below shows the events exported to ArcSight. For example, the first event is a critical Administration Server event: "Device status is Critical".
The representation of export events in the SIEM system varies according to the SIEM system you use.
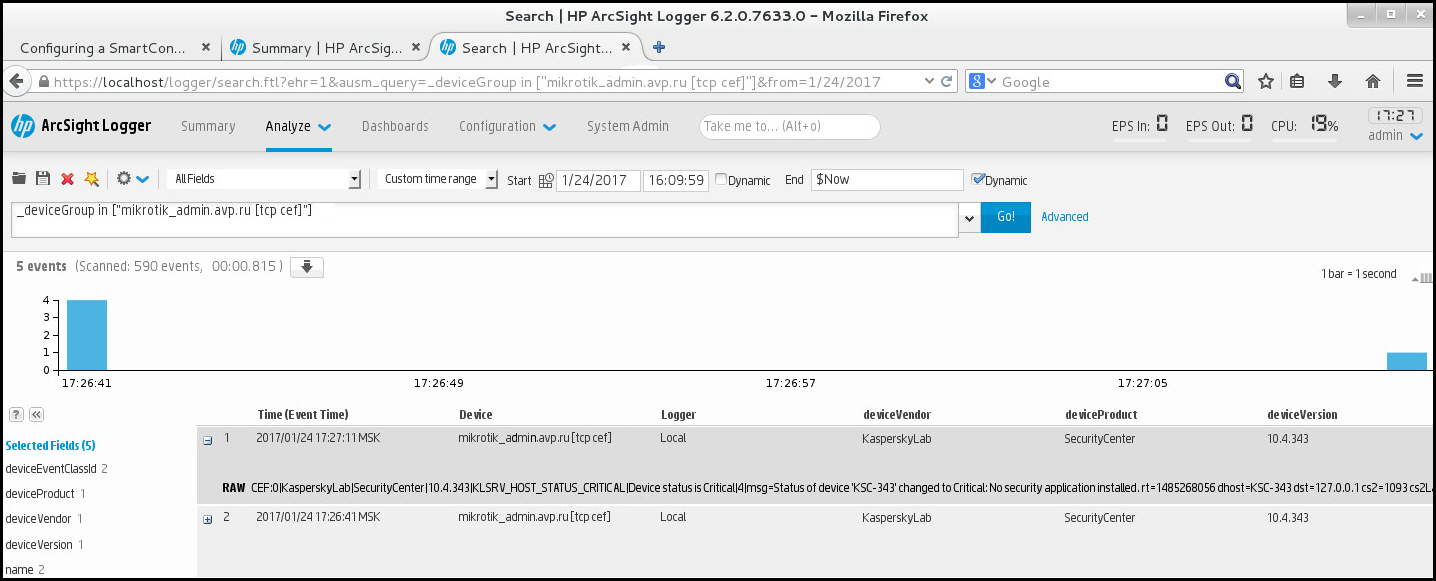
Example of events