Contents
- Schemas for data traffic and port usage
- Administration Server and managed devices on LAN
- Primary Administration Server on LAN and two secondary Administration Servers
- Administration Server on LAN, managed devices on internet, TMG in use
- Administration Server on LAN, managed devices on internet, connection gateway in use
- Administration Server in DMZ, managed devices on internet
- Interaction of Kaspersky Security Center components and security applications: more information
- Conventions used in interaction schemas
- Administration Server and DBMS
- Administration Server and Administration Console
- Administration Server and client device: Managing the security application
- Upgrading software on a client device through a distribution point
- Hierarchy of Administration Servers: primary Administration Server and secondary Administration Server
- Hierarchy of Administration Servers with a secondary Administration Server in DMZ
- Administration Server, a connection gateway in a network segment, and a client device
- Administration Server and two devices in DMZ: a connection gateway and a client device
- Administration Server and Kaspersky Security Center 13.1 Web Console
- Activating and managing the security application on a mobile device
Schemas for data traffic and port usage
This section provides schemas for data traffic between Kaspersky Security Center components, managed security applications, and external servers under various configurations. The schemas are provided with numbers for the ports that must be available on the local devices.
Administration Server and managed devices on LAN
The figure below shows the traffic of the data if Kaspersky Security Center is deployed on a local area network (LAN) only.
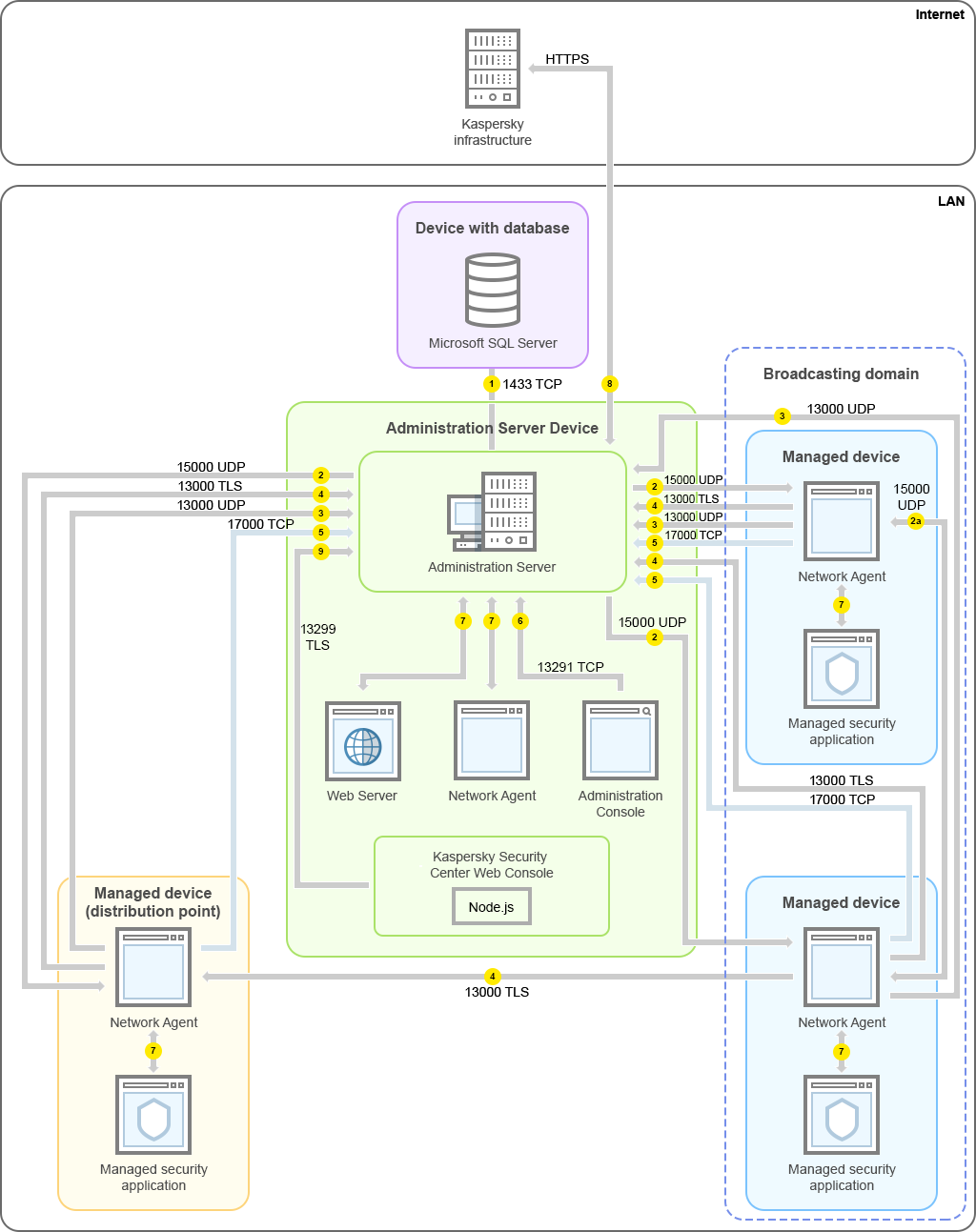
Administration Server and managed devices on a local area network (LAN)
The figure shows how different managed devices connect to the Administration Server in different ways: directly or via a distribution point. Distribution points reduce the load on the Administration Server during update distribution and optimize network traffic. However, distribution points are only needed if the number of managed devices is large enough. If the number of managed devices is small, all the managed devices can receive updates from the Administration Server directly.
The arrows indicate the initiation of traffic: each arrow points from a device that initiates the connection to the device that "answers" the call. The number of the port and the name of the protocol used for data transfer are provided. Each arrow has a number label, and details about the corresponding data traffic are as follows:
- Administration Server sends data to the database. If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
- Requests for communication from the Administration Server are transferred to all non-mobile managed devices through UDP port 15000.
Network Agents send requests to each other within one broadcasting domain. The data is then sent to the Administration Server and is used for defining the limits of the broadcasting domain and for automatic assignment of distribution points (if this option is enabled).
- Information about shutdown of the managed devices is transferred from Network Agent to the Administration Server through UDP port 13000.
- The Administration Server receives connection from Network Agents and from secondary Administration Servers through SSL port 13000.
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connection from Network Agents through non-SSL port 14000. Kaspersky Security Center also supports connection of Network Agents through port 14000, although using SSL port 13000 is recommended.
The distribution point was called "Update agent" in earlier versions of Kaspersky Security Center.
- The managed devices (except for mobile devices) request activation through TCP port 17000. This is not necessary if the device has its own access to the internet; in this case, the device sends the data to Kaspersky servers over the internet directly.
- Data from MMC-based Administration Console is transferred to the Administration Server through port 13291. (The Administration Console can be installed on the same or on a different device.)
- Applications on a single device exchange local traffic (either on the Administration Server or on a managed device). No external ports have to be opened.
- Data from the Administration Server to the Kaspersky servers (such as KSN data or information about licenses) and data from the Kaspersky servers to the Administration Server (such as application updates and anti-virus database updates) are transferred using the HTTPS protocol.
If you do not want your Administration Server to have access to the internet, you must manage this data manually.
- Kaspersky Security Center Web Console Server sends data to the Administration Server, which may be installed on the same or on a different device, through TLS port 13299.
Primary Administration Server on LAN and two secondary Administration Servers
The figure below shows the hierarchy of Administration Servers: the primary Administration Server is on a local area network (LAN). A secondary Administration Server is in the demilitarized zone (DMZ); another secondary Administration Server is on the internet.
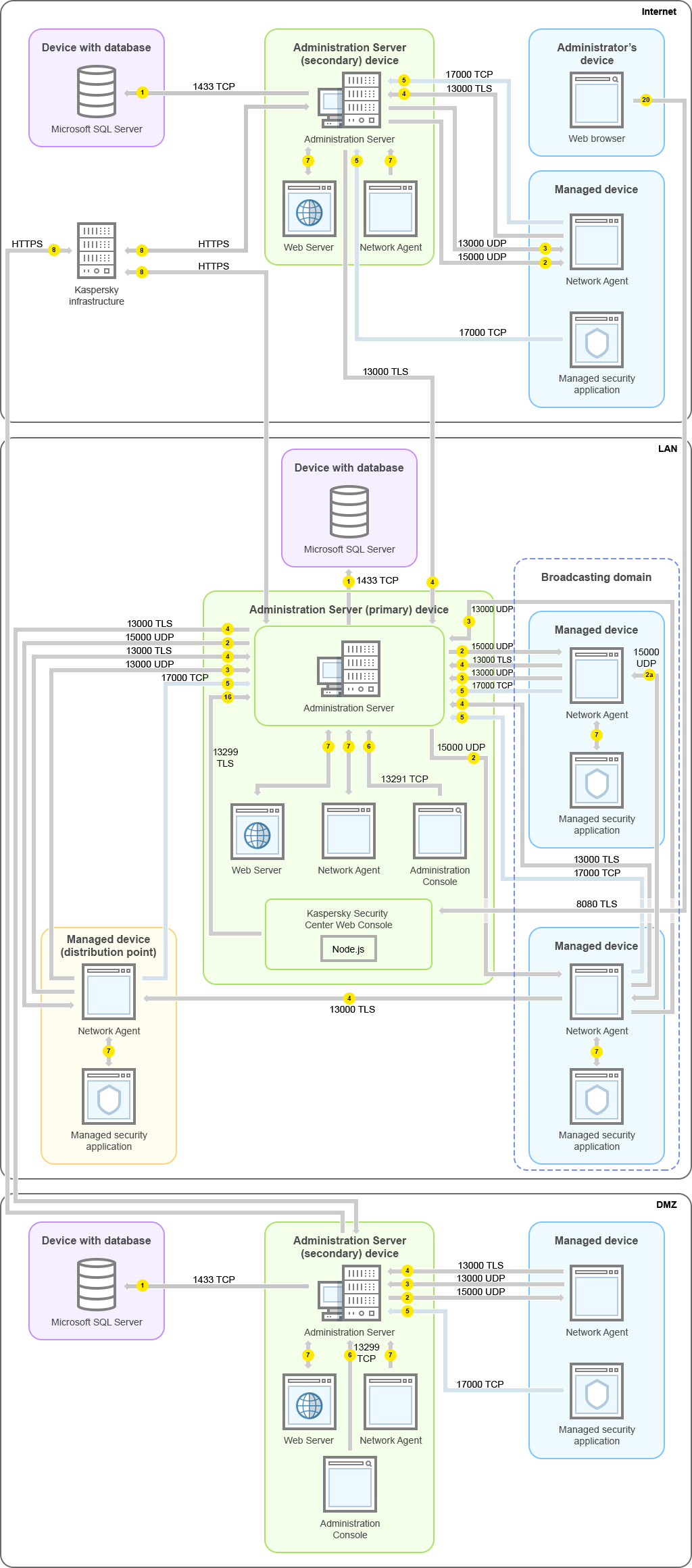
Hierarchy of Administration Servers: primary Administration Server and two secondary Administration Servers
The arrows indicate the initiation of traffic: each arrow points from a device that initiates the connection to the device that "answers" the call. The number of the port and the name of the protocol used for data transfer are provided. Each arrow has a number label, and details about the corresponding data traffic are as follows:
- Administration Server sends data to the database. If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
- Requests for communication from the Administration Server are transferred to all non-mobile managed devices through UDP port 15000.
Network Agents send requests to each other within one broadcasting domain. The data is then sent to the Administration Server and is used for defining the limits of the broadcasting domain and for automatic assignment of distribution points (if this option is enabled).
- Information about shutdown of the managed devices is transferred from Network Agent to the Administration Server through UDP port 13000.
- The Administration Server receives connection from Network Agents and from secondary Administration Servers through SSL port 13000.
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connection from Network Agents through non-SSL port 14000. Kaspersky Security Center also supports connection of Network Agents through port 14000, although using SSL port 13000 is recommended.
The distribution point was called "Update agent" in earlier versions of Kaspersky Security Center.
- The managed devices (except for mobile devices) request activation through TCP port 17000. This is not necessary if the device has its own access to the internet; in this case, the device sends the data to Kaspersky servers over the internet directly.
- Data from MMC-based Administration Console is transferred to the Administration Server through port 13291. (The Administration Console can be installed on the same or on a different device.)
- Applications on a single device exchange local traffic (either on the Administration Server or on a managed device). No external ports have to be opened.
- Data from the Administration Server to the Kaspersky servers (such as KSN data or information about licenses) and data from the Kaspersky servers to the Administration Server (such as application updates and anti-virus database updates) are transferred using the HTTPS protocol.
If you do not want your Administration Server to have access to the internet, you must manage this data manually.
- Kaspersky Security Center 13.1 Web Console Server sends data to the Administration Server, which may be installed on the same or on a different device, through TLS port 13299.
9a. Data from the browser, which is installed on a separate device of the administrator, is transferred to Kaspersky Security Center 13.1 Web Console Server through TLS port 8080. The Kaspersky Security Center 13.1 Web Console Server can be installed either on the Administration Server or on another device.
Administration Server on LAN, managed devices on internet, TMG in use
The figure below shows data traffic if the Administration Server is on a local area network (LAN) and the managed devices, including mobile devices, are on the internet. In this figure, Microsoft Forefront Threat Management Gateway (TMG) is in use. However, if you want to use a corporate firewall, you can use a different application; refer to the documentation of the application of your choice for details.
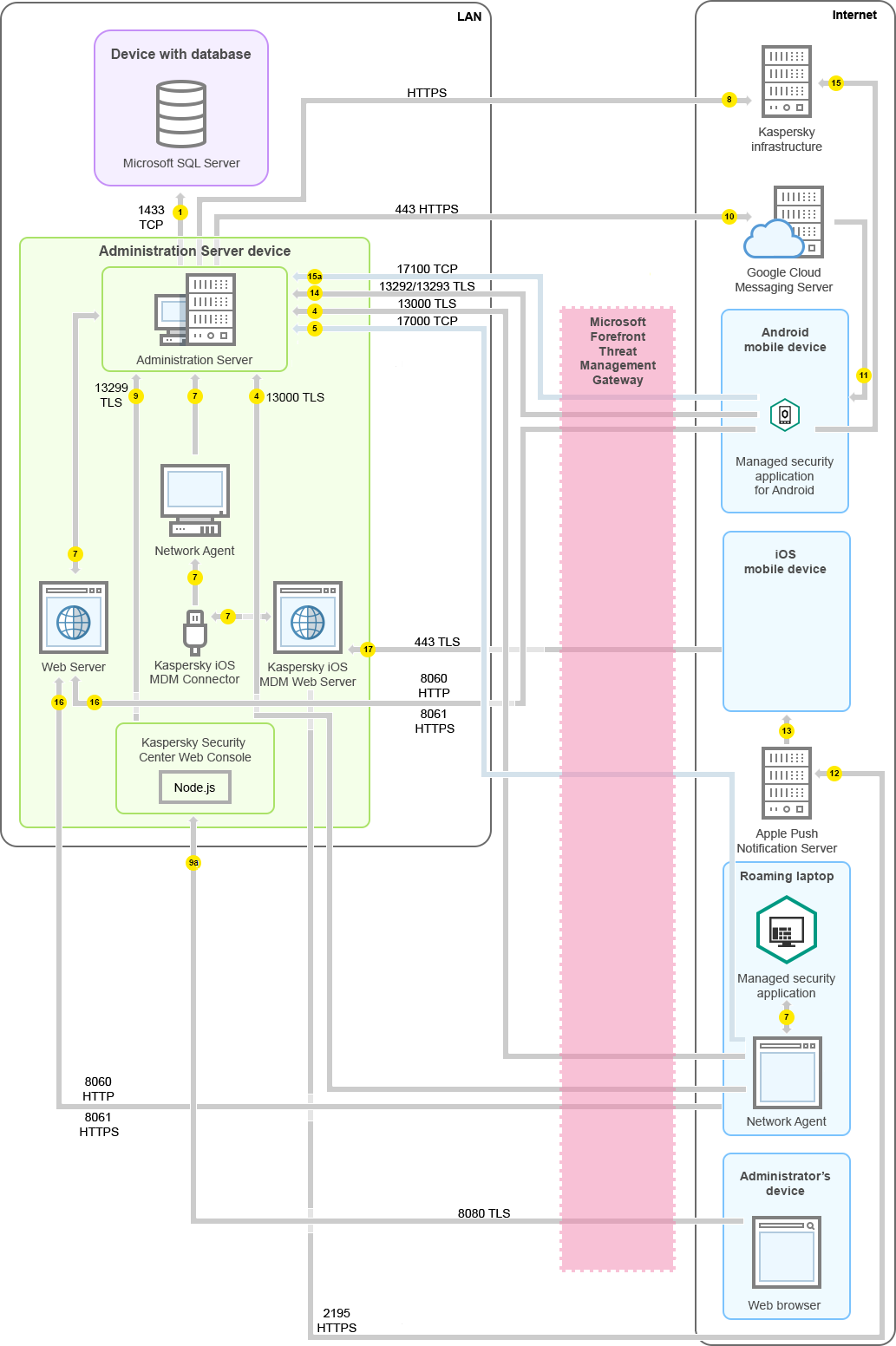
Administration Server on a local area network; managed devices connect to the Administration Server through Microsoft Forefront Threat Management Gateway
This deployment scheme is recommended if you do not want the mobile devices to connect to the Administration Server directly and do not want to assign a connection gateway in the DMZ.
The arrows indicate the initiation of traffic: each arrow points from a device that initiates the connection to the device that "answers" the call. The number of the port and the name of the protocol used for data transfer are provided. Each arrow has a number label, and details about the corresponding data traffic are as follows:
- Administration Server sends data to the database. If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
- Requests for communication from the Administration Server are transferred to all non-mobile managed devices through UDP port 15000.
Network Agents send requests to each other within one broadcasting domain. The data is then sent to the Administration Server and is used for defining the limits of the broadcasting domain and for automatic assignment of distribution points (if this option is enabled).
- Information about shutdown of the managed devices is transferred from Network Agent to the Administration Server through UDP port 13000.
- The Administration Server receives connection from Network Agents and from secondary Administration Servers through SSL port 13000.
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connection from Network Agents through non-SSL port 14000. Kaspersky Security Center also supports connection of Network Agents through port 14000, although using SSL port 13000 is recommended.
The distribution point was called "Update agent" in earlier versions of Kaspersky Security Center.
- The managed devices (except for mobile devices) request activation through TCP port 17000. This is not necessary if the device has its own access to the internet; in this case, the device sends the data to Kaspersky servers over the internet directly.
- Data from MMC-based Administration Console is transferred to the Administration Server through port 13291. (The Administration Console can be installed on the same or on a different device.)
- Applications on a single device exchange local traffic (either on the Administration Server or on a managed device). No external ports have to be opened.
- Data from the Administration Server to the Kaspersky servers (such as KSN data or information about licenses) and data from the Kaspersky servers to the Administration Server (such as application updates and anti-virus database updates) are transferred using the HTTPS protocol.
If you do not want your Administration Server to have access to the internet, you must manage this data manually.
- Kaspersky Security Center 13.1 Web Console Server sends data to the Administration Server, which may be installed on the same or on a different device, through TLS port 13299.
9a. Data from the browser, which is installed on a separate device of the administrator, is transferred to Kaspersky Security Center 13.1 Web Console Server through TLS port 8080. The Kaspersky Security Center 13.1 Web Console Server can be installed either on the Administration Server or on another device.
- For Android mobile devices only: data from the Administration Server is transferred to Google servers. This connection is used to notify Android mobile devices that they are required to connect to the Administration Server. Then push notifications are sent to the mobile devices.
- For Android mobile devices only: push notifications from Google servers are sent to the mobile device. This connection is used to notify mobile devices that they are required to connect to the Administration Server.
- For iOS mobile devices only: data from the iOS MDM Server is transferred to Apple Push Notification servers. Then push notifications are sent to the mobile devices.
- For iOS mobile devices only: push notifications are sent from Apple servers to the mobile device. This connection is used to notify iOS mobile devices that they are required to connect to the Administration Server.
- For mobile devices only: data from the managed application is transferred to the Administration Server (or to the connection gateway) through TLS port 13292 / 13293—directly or through a Microsoft Forefront Threat Management Gateway (TMG).
- For mobile devices only: data from the mobile device is transferred to the Kaspersky infrastructure.
15a. If a mobile device does not have internet access, the data is transferred to Administration Server through port 17100, and the Administration Server sends it to the Kaspersky infrastructure; however, this scenario applies very rarely.
- Requests for packages from managed devices, including mobile devices, are transferred to the Web Server, which is on the same device as the Administration Server.
- For iOS mobile devices only: data from the mobile device is transferred through TLS port 443 to the iOS MDM Server, which is on the same device as the Administration Server or on the connection gateway.
Administration Server on LAN, managed devices on internet, connection gateway in use
The figure below shows data traffic if the Administration Server is on a local area network (LAN) and the managed devices, including mobile devices, are on the internet. A connection gateway is in use.
This deployment scheme is recommended if you do not want the mobile devices to connect to the Administration Server directly and do not want to use a Microsoft Forefront Threat Management Gateway (TMG) or corporate firewall.
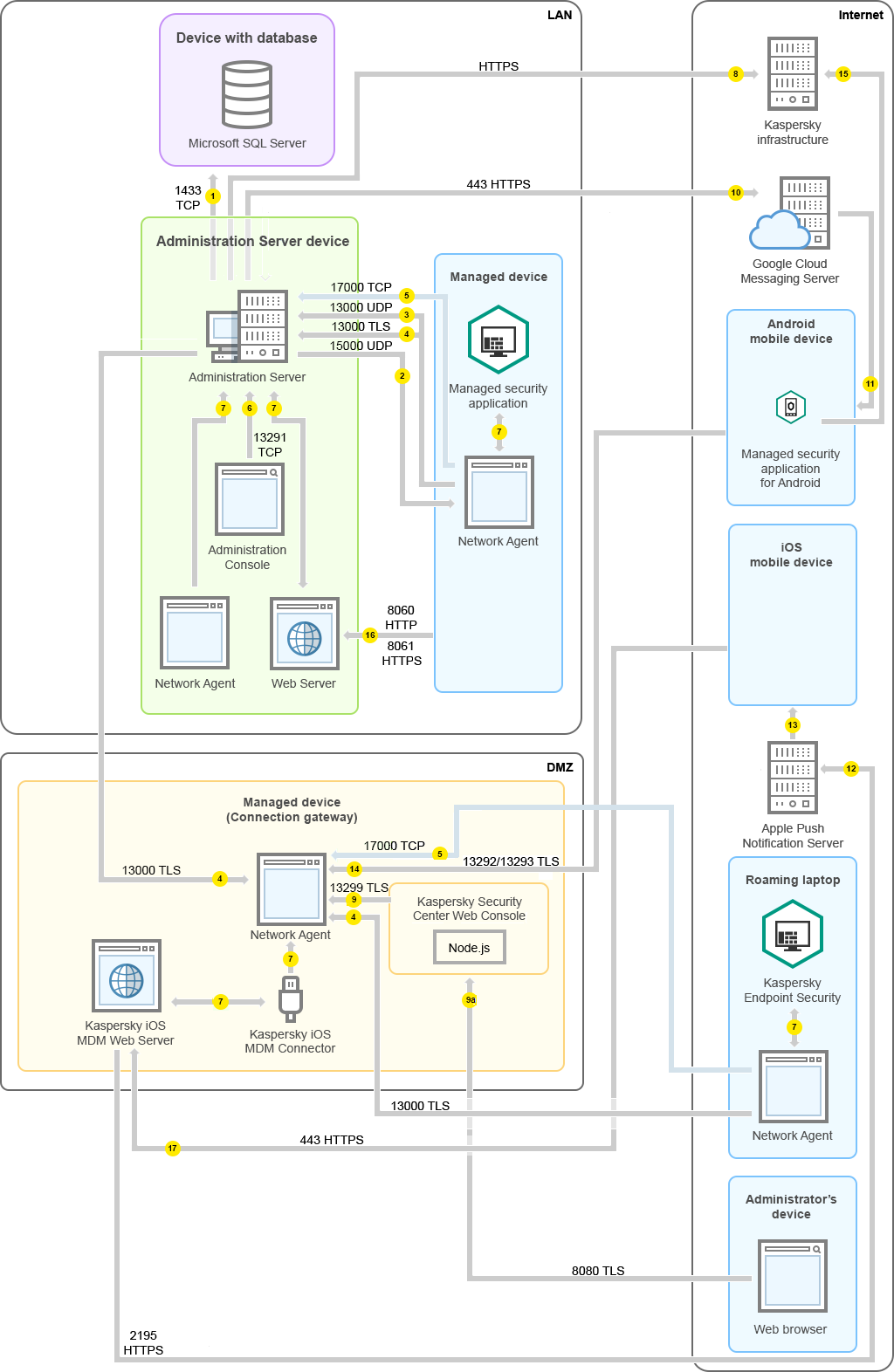
Managed mobile devices connected to the Administration Server through a connection gateway
In this figure, the managed devices are connected to the Administration Server through a connection gateway that is located in the DMZ. No TMG or corporate firewall is in use.
The arrows indicate the initiation of traffic: each arrow points from a device that initiates the connection to the device that "answers" the call. The number of the port and the name of the protocol used for data transfer are provided. Each arrow has a number label, and details about the corresponding data traffic are as follows:
- Administration Server sends data to the database. If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
- Requests for communication from the Administration Server are transferred to all non-mobile managed devices through UDP port 15000.
Network Agents send requests to each other within one broadcasting domain. The data is then sent to the Administration Server and is used for defining the limits of the broadcasting domain and for automatic assignment of distribution points (if this option is enabled).
- Information about shutdown of the managed devices is transferred from Network Agent to the Administration Server through UDP port 13000.
- The Administration Server receives connection from Network Agents and from secondary Administration Servers through SSL port 13000.
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connection from Network Agents through non-SSL port 14000. Kaspersky Security Center also supports connection of Network Agents through port 14000, although using SSL port 13000 is recommended.
The distribution point was called "Update agent" in earlier versions of Kaspersky Security Center.
- The managed devices (except for mobile devices) request activation through TCP port 17000. This is not necessary if the device has its own access to the internet; in this case, the device sends the data to Kaspersky servers over the internet directly.
- Data from MMC-based Administration Console is transferred to the Administration Server through port 13291. (The Administration Console can be installed on the same or on a different device.)
- Applications on a single device exchange local traffic (either on the Administration Server or on a managed device). No external ports have to be opened.
- Data from the Administration Server to the Kaspersky servers (such as KSN data or information about licenses) and data from the Kaspersky servers to the Administration Server (such as application updates and anti-virus database updates) are transferred using the HTTPS protocol.
If you do not want your Administration Server to have access to the internet, you must manage this data manually.
- Kaspersky Security Center 13.1 Web Console Server sends data to the Administration Server, which may be installed on the same or on a different device, through TLS port 13299.
9a. Data from the browser, which is installed on a separate device of the administrator, is transferred to Kaspersky Security Center 13.1 Web Console Server through TLS port 8080. The Kaspersky Security Center 13.1 Web Console Server can be installed either on the Administration Server or on another device.
- For Android mobile devices only: data from the Administration Server is transferred to Google servers. This connection is used to notify Android mobile devices that they are required to connect to the Administration Server. Then push notifications are sent to the mobile devices.
- For Android mobile devices only: push notifications from Google servers are sent to the mobile device. This connection is used to notify mobile devices that they are required to connect to the Administration Server.
- For iOS mobile devices only: data from the iOS MDM Server is transferred to Apple Push Notification servers. Then push notifications are sent to the mobile devices.
- For iOS mobile devices only: push notifications are sent from Apple servers to the mobile device. This connection is used to notify iOS mobile devices that they are required to connect to the Administration Server.
- For mobile devices only: data from the managed application is transferred to the Administration Server (or to the connection gateway) through TLS port 13292 / 13293—directly or through a Microsoft Forefront Threat Management Gateway (TMG).
- For mobile devices only: data from the mobile device is transferred to the Kaspersky infrastructure.
15a. If a mobile device does not have internet access, the data is transferred to Administration Server through port 17100, and the Administration Server sends it to the Kaspersky infrastructure; however, this scenario applies very rarely.
- Requests for packages from managed devices, including mobile devices, are transferred to the Web Server, which is on the same device as the Administration Server.
- For iOS mobile devices only: data from the mobile device is transferred through TLS port 443 to the iOS MDM Server, which is on the same device as the Administration Server or on the connection gateway.
Administration Server in DMZ, managed devices on internet
The figure below shows data traffic if the Administration Server is in the demilitarized zone (DMZ) and the managed devices, including mobile devices, are on the internet.
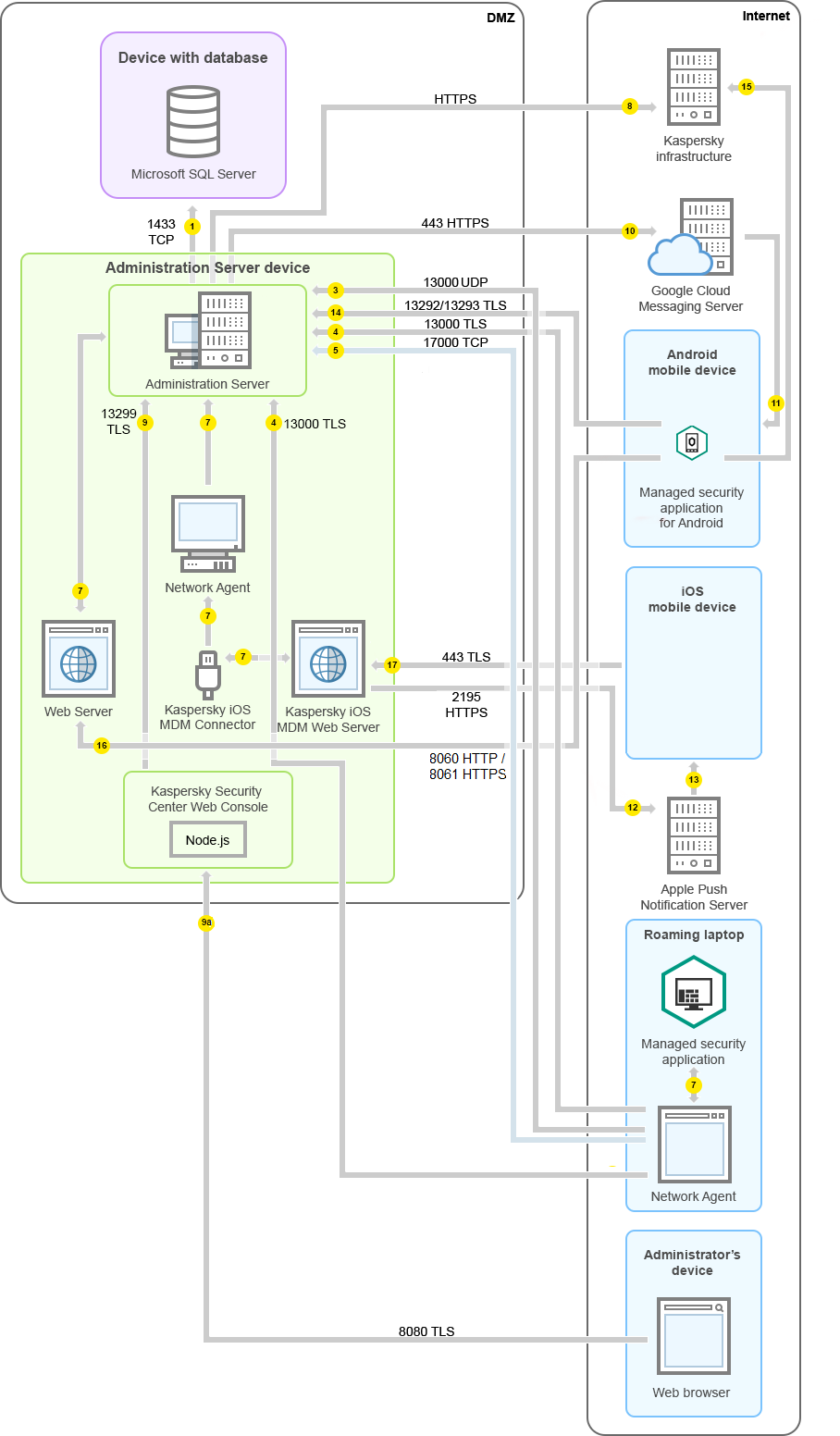
Administration Server in DMZ, managed mobile devices on the internet
In this figure, a connection gateway is not in use: the mobile devices connect to the Administration Server directly.
The arrows indicate the initiation of traffic: each arrow points from a device that initiates the connection to the device that "answers" the call. The number of the port and the name of the protocol used for data transfer are provided. Each arrow has a number label, and details about the corresponding data traffic are as follows:
- Administration Server sends data to the database. If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
- Requests for communication from the Administration Server are transferred to all non-mobile managed devices through UDP port 15000.
Network Agents send requests to each other within one broadcasting domain. The data is then sent to the Administration Server and is used for defining the limits of the broadcasting domain and for automatic assignment of distribution points (if this option is enabled).
- Information about shutdown of the managed devices is transferred from Network Agent to the Administration Server through UDP port 13000.
- The Administration Server receives connection from Network Agents and from secondary Administration Servers through SSL port 13000.
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connection from Network Agents through non-SSL port 14000. Kaspersky Security Center also supports connection of Network Agents through port 14000, although using SSL port 13000 is recommended.
The distribution point was called "Update agent" in earlier versions of Kaspersky Security Center.
4a. A connection gateway in DMZ also receives connection from the Administration Server through SSL port 13000. Because a connection gateway in DMZ cannot reach the Administration Server's ports, the Administration Server creates and maintains a permanent signal connection with a connection gateway. The signal connection is not used for data transfer; it is only used for sending an invitation to the network interaction. When the connection gateway needs to connect to the Server, it notifies the Server through this signal connection, and then the Server creates the required connection for data transfer.
Out-of-office devices connect to the connection gateway through SSL port 13000 as well.
- The managed devices (except for mobile devices) request activation through TCP port 17000. This is not necessary if the device has its own access to the internet; in this case, the device sends the data to Kaspersky servers over the internet directly.
- Data from MMC-based Administration Console is transferred to the Administration Server through port 13291. (The Administration Console can be installed on the same or on a different device.)
- Applications on a single device exchange local traffic (either on the Administration Server or on a managed device). No external ports have to be opened.
- Data from the Administration Server to the Kaspersky servers (such as KSN data or information about licenses) and data from the Kaspersky servers to the Administration Server (such as application updates and anti-virus database updates) are transferred using the HTTPS protocol.
If you do not want your Administration Server to have access to the internet, you must manage this data manually.
- Kaspersky Security Center 13.1 Web Console Server sends data to the Administration Server, which may be installed on the same or on a different device, through TLS port 13299.
9a. Data from the browser, which is installed on a separate device of the administrator, is transferred to Kaspersky Security Center 13.1 Web Console Server through TLS port 8080. The Kaspersky Security Center 13.1 Web Console Server can be installed either on the Administration Server or on another device.
- For Android mobile devices only: data from the Administration Server is transferred to Google servers. This connection is used to notify Android mobile devices that they are required to connect to the Administration Server. Then push notifications are sent to the mobile devices.
- For Android mobile devices only: push notifications from Google servers are sent to the mobile device. This connection is used to notify mobile devices that they are required to connect to the Administration Server.
- For iOS mobile devices only: data from the iOS MDM Server is transferred to Apple Push Notification servers. Then push notifications are sent to the mobile devices.
- For iOS mobile devices only: push notifications are sent from Apple servers to the mobile device. This connection is used to notify iOS mobile devices that they are required to connect to the Administration Server.
- For mobile devices only: data from the managed application is transferred to the Administration Server (or to the connection gateway) through TLS port 13292 / 13293—directly or through a Microsoft Forefront Threat Management Gateway (TMG).
- For mobile devices only: data from the mobile device is transferred to the Kaspersky infrastructure.
15a. If a mobile device does not have internet access, the data is transferred to Administration Server through port 17100, and the Administration Server sends it to the Kaspersky infrastructure; however, this scenario applies very rarely.
- Requests for packages from managed devices, including mobile devices, are transferred to the Web Server, which is on the same device as the Administration Server.
- For iOS mobile devices only: data from the mobile device is transferred through TLS port 443 to the iOS MDM Server, which is on the same device as the Administration Server or on the connection gateway.
Interaction of Kaspersky Security Center components and security applications: more information
This section provides the schemas for interaction of Kaspersky Security Center components and managed security applications. The schemas provide the numbers of the ports that must be available and the names of the processes that open those ports.
Conventions used in interaction schemas
The following table provides the conventions used across the schemas.
Document conventions
Icon |
Meaning |
|
Administration Server |
|
Secondary Administration Server |
|
DBMS |
|
Client device (that has Network Agent and an application from Kaspersky Endpoint Security family installed, or has a different security application installed that Kaspersky Security Center can manage) |
|
Connection gateway |
|
Distribution point |
|
Mobile client device with Kaspersky Security for Mobile |
|
Browser on the user's device |
|
Process running on the device and opening a port |
|
Port and its number |
|
TCP traffic (the arrow direction shows the traffic flow direction) |
|
UDP traffic (the arrow direction shows the traffic flow direction) |
|
COM invoke |
|
DBMS transport |
|
DMZ boundary |
Administration Server and DBMS
Data from the Administration Server enter the SQL Server, MySQL, or MariaDB database.
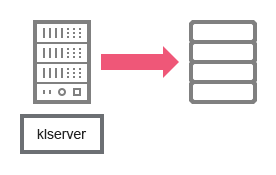
Administration Server and DBMS
If you install the Administration Server and the database on different devices, you must make available the necessary ports on the device where the database is located (for example, port 3306 for MySQL Server and MariaDB Server, or port 1433 for Microsoft SQL Server). Please refer to the DBMS documentation for the relevant information.
Administration Server and Administration Console
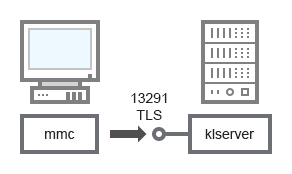
Administration Server and Administration Console
For schema clarifications, see the table below.
Administration Server and Administration Console (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Administration Server |
13291 |
klserver |
TCP |
Yes |
Receiving connections from Administration Console |
Administration Server and client device: Managing the security application
The Administration Server receives connection from Network Agents via SSL port 13000 (see figure below).
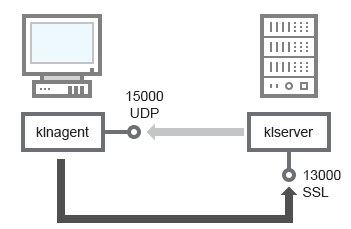
Administration Server and client device: managing the security application, connection via port 13000 (recommended)
If you used an earlier version of Kaspersky Security Center, the Administration Server on your network can receive connections from Network Agents via non-SSL port 14000 (see figure below). Kaspersky Security Center 13.1 also supports connection of Network Agents via port 14000, although using SSL port 13000 is recommended.
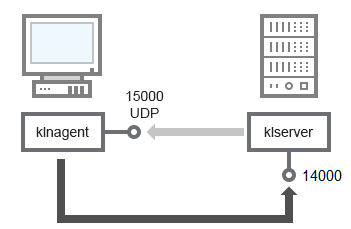
Administration Server and client device: managing the security application, connection via port 14000 (lower security)
For clarifications of schemas, see the table below.
Administration Server and client device: Managing the security application (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS (for TCP only) |
Port purpose |
|---|---|---|---|---|---|
Network Agent |
15000 |
klnagent |
UDP |
Null |
Multicasting for Network Agents |
Administration Server |
13000 |
klserver |
TCP |
Yes |
Receiving connections from Network Agents |
Administration Server |
14000 |
klserver |
TCP |
No |
Receiving connections from Network Agents |
Upgrading software on a client device through a distribution point
The client device connects to the distribution point via port 13000 and, if you are using the distribution point as a push server, also via port 13295; the distribution point multicasts to Network Agents via port 15000 (see figure below).
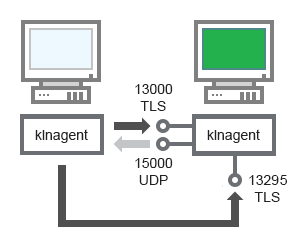
Upgrading software on a client device through a distribution point
For schema clarifications, see the table below.
Upgrading software through a distribution point (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS (for TCP only) |
Port purpose |
|---|---|---|---|---|---|
Network Agent |
15000 |
klnagent |
UDP |
Null |
Multicasting for Network Agents |
Distribution point |
13000 |
klnagent |
TCP |
Yes |
Receiving connections from Network Agents |
Distribution point |
13295 |
klnagent |
TCP |
Yes |
Sending push notifications to Network Agent |
Hierarchy of Administration Servers: primary Administration Server and secondary Administration Server
The schema (see figure below) shows how to use port 13000 to ensure interaction between Administration Servers combined into a hierarchy.
When combining two Administration Servers into a hierarchy, make sure that port 13291 is accessible on both Administration Servers. Administration Console connects to the Administration Server through port 13291.
Subsequently, when the Administration Servers are combined into a hierarchy, you will be able to administer both of them by using Administration Console connected to the primary Administration Server. Therefore, the accessibility of port 13291 of the primary Administration Server is the only prerequisite.
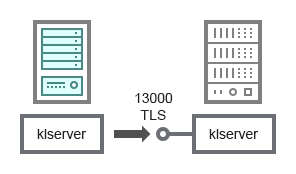
Hierarchy of Administration Servers: primary Administration Server and secondary Administration Server
For schema clarifications, see the table below.
Hierarchy of Administration Servers (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Primary Administration Server |
13000 |
klserver |
TCP |
Yes |
Receiving connections from secondary Administration Servers |
Hierarchy of Administration Servers with a secondary Administration Server in DMZ
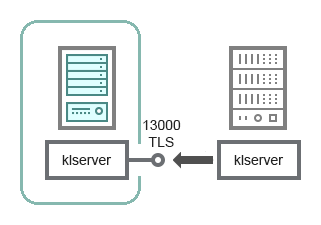
Hierarchy of Administration Servers with a secondary Administration Server in DMZ
The schema shows a hierarchy of Administration Servers in which the secondary Administration Server located in DMZ receives a connection from the primary Administration Server (see the table below for schema clarifications). When combining two Administration Servers into a hierarchy, make sure that port 13291 is accessible on both Administration Servers. Administration Console connects to the Administration Server through port 13291.
Subsequently, when the Administration Servers are combined into a hierarchy, you will be able to administer both of them by using Administration Console connected to the primary Administration Server. Therefore, the accessibility of port 13291 of the primary Administration Server is the only prerequisite.
Hierarchy of Administration Servers with a secondary Administration Server in DMZ (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Secondary Administration Server |
13000 |
klserver |
TCP |
Yes |
Receiving connections from the primary Administration Server |
Administration Server, a connection gateway in a network segment, and a client device
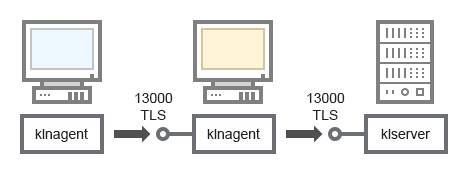
Administration Server, a connection gateway in a network segment, and a client device
For schema clarifications, see the table below.
Administration Server, a connection gateway in a network segment, and a client device (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Administration Server |
13000 |
klserver |
TCP |
Yes |
Receiving connections from Network Agents |
Network Agent |
13000 |
klnagent |
TCP |
Yes |
Receiving connections from Network Agents |
Administration Server and two devices in DMZ: a connection gateway and a client device
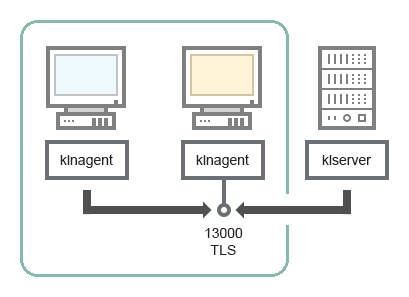
Administration Server with a connection gateway and a client device in DMZ
For schema clarifications, see the table below.
Administration Server with a connection gateway in a network segment and a client device (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Network Agent |
13000 |
klnagent |
TCP |
Yes |
Receiving connections from Network Agents |
Administration Server and Kaspersky Security Center 13.1 Web Console
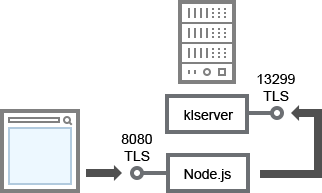
Administration Server and Kaspersky Security Center 13.1 Web Console
For schema clarifications, see the table below.
Administration Server and Kaspersky Security Center 13.1 Web Console (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Administration Server |
13299 |
klserver |
TCP |
Yes |
Receiving connections from Kaspersky Security Center 13.1 Web Console to the Administration Server over OpenAPI |
Kaspersky Security Center 13.1 Web Console Server or Administration Server |
8080 |
Node.js: Server-side JavaScript |
TCP |
Yes |
Receiving connections from Kaspersky Security Center 13.1 Web Console |
Kaspersky Security Center 13.1 Web Console can be installed on the Administration Server or on another device.
Activating and managing the security application on a mobile device
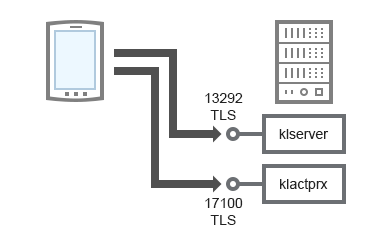
Activating and managing the security application on a mobile device
For schema clarifications, see the table below.
Activating and managing the security application on a mobile device (traffic)
Device |
Port number |
Name of the process that opens the port |
Protocol |
TLS |
Port purpose |
|---|---|---|---|---|---|
Administration Server |
13292 |
klserver |
TCP |
Yes |
Receiving connections from Administration Console to Administration Server |
Administration Server |
17100 |
klactprx |
TCP |
Yes |
Receiving connections for application activation from mobile devices |