Contents
Building a structure of administration groups and assigning distribution points
A structure of administration groups in Kaspersky Security Center performs the following functions:
- Sets the scope of policies.
There is an alternate way of applying relevant settings on devices, by using policy profiles. In this case, the scope of policies is set with tags, device locations in Active Directory organizational units, membership in Active Directory security groups, etc.
- Sets the scope of group tasks.
There is an approach to defining the scope of group tasks that is not based on a hierarchy of administration groups: use of tasks for device selections and tasks for specific devices.
- Sets access rights to devices, virtual Administration Servers, and secondary Administration Servers.
- Assigns distribution points.
When building the structure of administration groups, you must take into account the topology of the organization's network for the optimum assignment of distribution points. The optimum distribution of distribution points allows you to save traffic on the organization's network.
Depending on the organizational schema and network topology adopted by the MSP client, the following standard configurations can be applied to the structure of administration groups:
- Single office
- Multiple small detached offices
Standard MSP client configuration: Single office
In a standard "single-office" configuration, all devices are on the organization's network so they can "see" each other. The organization's network may consist of a few separate parts (networks or network segments) linked by narrow channels.
The following methods of building the structure of administration groups are possible:
- Building the structure of administration groups taking into account the network topology. The structure of administration groups may not reflect the network topology with absolute precision. A match between the separate parts of the network and certain administration groups would be enough. You can use automatic assignment of distribution points or assign them manually.
- Building the structure of administration groups, without taking the network topology into account. In this case, you must disable automatic assignment of distribution points and then assign one or several devices to act as distribution points for a root administration group in each of the separate parts of the network, for example, for the Managed devices group. All distribution points will be at the same level and will feature the same scope spanning all devices on the organization's network. In this case, each of Network Agents will connect to the distribution point that has the shortest route. The route to a distribution point can be traced with the tracert utility.
Standard MSP client configuration: Multiple small remote offices
This standard configuration provides for a number of small remote offices, which may be communicated with the head office via the internet. Each remote office is located behind the NAT, that is, connection from one remote office to another is not possible because offices are isolated from one another.
The configuration must be reflected in the structure of administration groups: a separate administration group must be created for each remote office (groups Office 1 and Office 2 in the figure below).
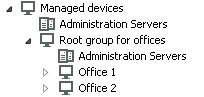
Remote offices are included in the administration group structure
One or multiple distribution points must be assigned to each administration group corresponding to an office. Distribution points must be devices at the remote office that have a sufficient amount of free disk space. Devices deployed in the Office 1 group, for example, will access distribution points assigned to the Office 1 administration group.
If some users move between offices physically, with their laptops, you must select two or more devices (in addition to the existing distribution points) in each remote office and assign them to act as distribution points for a top-level administration group (Root group for offices in the figure above).
Example: A laptop is deployed in the Office 1 administration group and then is moved physically to the office that corresponds to the Office 2 administration group. After the laptop is moved, Network Agent attempts to access the distribution points assigned to the Office 1 group, but those distribution points are unavailable. Then, Network Agent starts attempting to access the distribution points that have been assigned to the Root group for offices. Because remote offices are isolated from one another, attempts to access distribution points assigned to the Root group for offices administration group will only be successful when Network Agent attempts to access distribution points in the Office 2 group. That is, the laptop will remain in the administration group that corresponds to the initial office, but the laptop will use the distribution point of the office where it is physically located at the moment.