Advanced configuration of the application
Page top
[Topic kes123256]
Computer protection scope
Objects detected by Kaspersky Endpoint Security are divided into categories based on various attributes. The application always searches for viruses, worms, Trojans, and malicious utility tools. These programs may cause significant damage to your computer. To ensure more reliable protection for your computer, you can extend the list of detectable objects by enabling the application to check for legitimate software that an intruder could exploit to damage your computer or personal data.
The objects that Kaspersky Endpoint Security protects against are grouped as follows:
- Viruses, worms, Trojans, malicious tools. This category includes all types of malware. Protection against all types of malware ensures the minimum necessary security level. In accordance with the recommendations of Kaspersky Lab experts, Kaspersky Endpoint Security always monitors objects that belong to this category.
- Adware. This category includes software that can inconvenience the user.
- Auto-dialers. This category includes applications that establish phone connections through a modem in hidden mode.
- Other applications. This category includes legitimate programs that may be used by intruders to harm the user's computer or data.
Select the categories of objects to detect
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Threats tab, in the Categories of objects to detect section, select the checkboxes next to the categories of objects to detect.
Note: Kaspersky Endpoint Security always protects your computer against viruses, worms, Trojans, and malicious tools. Therefore, it is not possible to deselect the checkbox for this category.
Depending on the selected categories of objects to detect, Kaspersky Endpoint Security uses some or all of its application databases when running File Anti-Virus, Web Anti-Virus, and virus scan tasks.
Note: Kaspersky Lab specialists recommend that you keep protection enabled against adware and auto-dialers. If Kaspersky Endpoint Security classifies an application as malware but you believe it is safe, you can add this application to Trusted Zone.
Trusted Zone is a list of objects that Kaspersky Endpoint Security does not scan or monitor. You may need to add objects to Trusted Zone if, for example, Kaspersky Endpoint Security blocks access to a file, application folder, or website even though you are absolutely sure that this object or web address is harmless.
Add/remove a file or folder to/from the list of trusted files and folders
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Threats tab, in the Exclusions section, click the Trusted Zone button.
The Trusted Zone preferences window opens.
- On the Trusted files and folders tab, edit the list of trusted files and folders:
- To add a file or folder to the list:
- Click
 .
.The dialog where you can select a file or folder opens.
- Select a file or folder that you want to add.
- Click the Open button.
- To remove a file or folder from the list:
- Select a file or folder that you want to remove from the list of trusted files and folders.
- Click
 .
.
- Click the OK button.
Add/remove a trusted web address to/from the list of trusted web addresses
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Threats tab, in the Exclusions section, click the Trusted Zone button.
The Trusted Zone preferences window opens.
- On the Trusted web addresses tab, edit the list of trusted web addresses:
- To add a web address to the list:
- Click
 .
. - Enter the web address that you want to add to the list.
- Click the OK button.
- To remove a web address from the list:
- Select a web address that you want to remove.
- Click
 .
.
- Click the OK button.
By default, the list of trusted web addresses is empty.
Enable monitoring of a trusted web address
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Threats tab, in the Exclusions section, click the Trusted Zone button.
The Trusted Zone preferences window opens.
- On the Trusted web addresses tab, deselect the checkbox next to a web address that you want Kaspersky Endpoint Security to monitor.
- Click the OK button.
[Topic kes96925]
File Anti-Virus
File Anti-Virus prevents infection of the computer's file system. The component starts during startup of the operating system, remains in the computer RAM, and scans for viruses and other malware all files that are opened, saved, or run on your computer and on all connected drives. If you disable File Anti-Virus, it will not start at operating system startup. You will have to re-enable File Anti-Virus manually.
Enable/disable File Anti-Virus
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the File Anti-Virus section, select/deselect the Enable File Anti-Virus checkbox.
You can also enable File Anti-Virus in Protection Center. Disabling computer protection or disabling protection components puts your computer at much higher risk of infection. This is why Protection Center informs you when protection is disabled.
You can create a protection scope for File Anti-Virus.
Add/remove a file or folder from the protection scope
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the File Anti-Virus section, click the Protection Scope button.
A window with a list of objects that File Anti-Virus scans opens. By default, File Anti-Virus scans all objects that are located on internal, removable, and network drives connected to your computer.
- Add/remove the objects to/from the protection scope:
- To add a file or folder to the protection scope:
- Click
 .
.A drop-down list where you can select objects to add to the protection scope opens.
- In the drop-down list, choose the Files and Folders item.
The window where you can select a file or folder opens.
- Select a file or folder that you want to add to the protection scope.
- Click the Open button.
- To remove a file or folder from the protection scope:
- Select an object in the list of protection scope objects.
- Drag the selected object from the window or click
 .
.
- Click the Save button.
Add/remove an object of the default protection object list from the protection scope
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the File Anti-Virus section, click the Protection Scope button.
A window with a list of objects that File Anti-Virus scans opens. By default, File Anti-Virus scans all objects that are located on internal, removable, and network drives connected to your computer.
- Add/remove the objects on the list of default objects to/from the protection scope:
- To add an object on the list of default objects to the protection scope:
- Click
 .
.A drop-down list where you can select objects to add to the protection scope opens.
- In the drop-down list, select an object that you want to add to the protection scope (for example, All Internal Drives).
- To remove an object on the list of default objects from the protection scope:
- Select the object in the list of protection scope objects.
- Drag the selected object from the window or click
 .
.
- Click the Save button.
Disable protection of an object in the protection scope
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the File Anti-Virus section, click the Protection Scope button.
A window with a list of objects that File Anti-Virus scans opens. By default, File Anti-Virus scans all objects that are located on internal, removable, and network drives connected to your computer.
- Deselect the checkbox next to an object in the list of protection scope objects.
- Click the Save button.
When you or an application attempt to access a file included in the protection scope, File Anti-Virus checks iSwift databases for information about the file, and uses this information to decide whether to scan the file.
Recognizing malicious objects is possible thanks to signature analysis, a way of searching for threats based on threat descriptions included in the anti-virus databases. In addition to signature analysis, File Anti-Virus uses heuristic analysis and other scanning technologies.
If a threat is detected in a file, Kaspersky Endpoint Security identifies the type of the detected malicious program (for example, virus or Trojan). After that the application displays a notification about the detected object and takes the action on the object based on your File Anti-Virus preferences.
Select the action that File Anti-Virus performs after detecting an infected file
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the File Anti-Virus section, select the action that File Anti-Virus performs after detecting an infected file.
Before attempting to disinfect or delete an infected file, Kaspersky Endpoint Security saves a backup copy for subsequent restoration or disinfection.
Information about File Anti-Virus operation and all detected objects is logged in a report.
Note: If File Anti-Virus stops running with an error, you can view the report and try to start the component again. If the problem is not solved, you can contact Technical Support at Kaspersky Lab.
View the File Anti-Virus report
- Open the main application window.
- In the upper pane of the main application window, click the
 button.
button.The Kaspersky Endpoint Security reports window opens.
- Open the File Anti-Virus tab.
Note: If File Anti-Virus stops running with an error, you can view the report and try to start the component again. If the problem is not solved, you can contact Technical Support at Kaspersky Lab.
[Topic kes96931]
Web Anti-Virus
When you use the Internet, the information on your computer is at risk of infection by viruses and other computer security threats. Computer security threats may penetrate your computer when you download free programs or visit websites that have been attacked by hackers. In addition, network worms may attack your computer as soon as your computer establishes an Internet connection, even before you open a web address or download a file.
The Web Anti-Virus component protects information that your computer sends and receives via the HTTP and HTTPS protocols in Safari, Chrome, or Firefox.
Note: Web Anti-Virus monitors web traffic on the ports most frequently used for HTTP and HTTPS data transfer.
Enable/disable Web Anti-Virus
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the Web Anti-Virus section, select/deselect the Enable Web Anti-Virus checkbox.
You can also enable Web Anti-Virus via Protection Center. Disabling computer protection or disabling protection components puts your computer at much higher risk of infection. This is why Protection Center informs you when protection is disabled.
Important: If you have disabled Web Anti-Virus, it will not be re-enabled automatically when Kaspersky Endpoint Security starts again or when the operating system restarts. You have to re-enable Web Anti-Virus manually.
Web Anti-Virus scans web traffic based on the settings recommended by Kaspersky Lab. When Web Anti-Virus detects a threat, it performs the action that you specify. Malicious objects are recognized using signature analysis, heuristic analysis, and data from Kaspersky Security Network.
Select the action that Web Anti-Virus performs after detecting dangerous web traffic objects
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the Web Anti-Virus section, select the action that Web Anti-Virus performs after detecting dangerous web traffic objects.
Checking links on webpages for phishing threats and malicious web addresses makes it possible to avoid phishing attacks. Phishing attacks usually take the form of email messages from criminals, who pretend to be financial institutions (such as banks) and send links to fraudulent websites. In these emails, the criminals try to trick the user into visiting a phishing website and entering confidential data (such as your bank card number or the name and password for your online bank account). A phishing attack can be disguised, for example, as a message from your bank with a link to its official website, but in reality the link takes you to an exact copy of the bank's official website created by impostors.
Web Anti-Virus monitors your web traffic for attempts to visit a phishing website; it blocks access to such websites. To check links on webpages for phishing threats and malicious web addresses, Kaspersky Endpoint Security uses the application databases, heuristic analysis, and data from Kaspersky Security Network.
Web traffic scan algorithm
Each website or file that you or an application accesses via the HTTP and HTTPS protocols is intercepted and scanned for malicious code by Web Anti-Virus:
- If a website or file contains malicious code, Kaspersky Endpoint Security can block it and display a notification that the requested file or webpage is infected.
- If the file or website does not contain malicious code, you can access it immediately.
Information about Web Anti-Virus operation and all detected dangerous web traffic objects is logged in a report.
Note: If Web Anti-Virus stops running with an error, you can view the Web Anti-Virus report and try to restart the component. If the problem is not solved, you can contact Technical Support at Kaspersky Lab.
View the Web Anti-Virus report
- Open the main application window.
- In the upper pane of the main application window, click the
 button.
button.The Kaspersky Endpoint Security reports window opens.
- Open the Web Anti-Virus tab.
[Topic kes58556]
Network Attack Blocker
Kaspersky Endpoint Security protects your computer against network attacks.
A network attack is an attempt to break into the operating system of a remote computer. Criminals attempt network attacks to establish control over the operating system, cause operating system denial of service, or access sensitive information. To achieve these goals, criminals either carry out direct attacks such as port scanning and brute force attacks, or use malware installed on a computer under attack.
Network attacks can be divided into the following types:
- Port scanning. This type of network attack is usually performed to prepare for a more dangerous network attack. An intruder scans UDP/TCP ports that use network services on the target computer and determines the vulnerability of the target computers to other, more dangerous types of network attacks. Port scanning also enables the intruder to determine the operating system on the target computer and select appropriate network attacks for that operating system.
- DoS attacks or network attacks causing a denial of service. Such network attacks cause the target operating system to become unstable or completely inoperable.
The following main types of DoS attacks exist:
- Transmission of specially designed network packets that are not expected by the target computer and therefore cause the target operating system to malfunction or crash.
- Sending a large number of network packets to a remote computer over a short period. All of the resources of the target computer are used to process the network packets sent by the intruder. As a result, the computer stops performing its functions.
- Network intrusion attacks. Such network attacks are designed to "hijack" the operating system of the target computer. This is the most dangerous type of network attack because, if the attack is successful, the intruder gains total control over the operating system.
This type of network attack is used when the intruder wants to obtain confidential data from a remote computer (such as bank card numbers or passwords) or secretly use the remote computer for the intruder’s purposes (such as for attacking other computers from this computer).
Enable/disable Network Attack Blocker
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the Network Attack Blocker section, select/deselect the Enable Network Attack Blocker checkbox.
You can also enable Network Attack Blocker in Protection Center. Disabling computer protection or disabling protection components puts your computer at much higher risk of infection. This is why Protection Center informs when protection is disabled.
Important: If you have disabled Network Attack Blocker, it will not be re-enabled automatically when Kaspersky Endpoint Security starts again or after the operating system restarts. You have to re-enable Network Attack Blocker manually.
When the application detects dangerous network activity, Kaspersky Endpoint Security automatically adds the IP address of the attacking computer to the list of blocked computers, unless the attacking computer is in the list of trusted computers.
Edit the list of blocked computers
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the Network Attack Blocker section, select the Enable Network Attack Blocker checkbox.
- Click the Exclusions button.
A window with a list of trusted computers and a list of blocked computers opens.
- Open the Blocked computers tab.
- If you are sure that the blocked computer is not a threat, select the IP address of the computer in the list and click the Unblock button.
The confirmation dialog opens.
- In the confirmation dialog, select one of the following:
- Click the Save button to save changes.
You can create and edit the list of trusted computers. Kaspersky Endpoint Security doesn't block the IP addresses of these computers automatically even after dangerous network activity is detected from them.
Edit the list of trusted computers
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Protection tab, in the Network Attack Blocker section, select the Enable Network Attack Blocker checkbox.
- Click the Exclusions button.
A window with a list of trusted computers and a list of blocked computers opens.
- Open the Exclusions tab.
- Edit the list of trusted computers:
- To add an IP address to the list of trusted computers:
- Click
 .
. - In the field that appears, enter the IP address of the computer that you trust to be safe.
- To remove an IP address from the list of trusted computers:
- Select an IP address in the list.
- Click
 .
.
- To edit an IP address in the list of trusted computers:
- Select an IP address in the list.
- Click the Edit button.
- Change the IP address.
- Click the Save button to save changes.
When a network attack is detected, Kaspersky Endpoint Security logs information about the attack in a report.
Note: If the Network Attack Blocker component stops running with an error, you can view the report and try to restart the component. If the problem is not solved, you can contact Technical Support at Kaspersky Lab
View the Network Attack Blocker report
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- Open the Network Attack Blocker tab.
You can view overall statistics on protection against network attacks (number of blocked computers and number of events since last startup of the Network Attack Blocker component) in Protection Center by clicking the Details button in the right pane of the main application window.
Page top
[Topic kes88075]
Virus Scan
In addition to the real-time computer protection provided by File Anti-Virus and Web Anti-Virus, you are advised to regularly scan your computer for viruses and other computer security threats. Computer scanning is necessary to prevent the spread of malware that has not been detected by the protection components.
Kaspersky Endpoint Security contains the following built-in virus scan tasks:
-
 Full Scan.
Full Scan.A virus scan of memory, startup objects, and all internal drives of the computer.
-
 Quick Scan.
Quick Scan.A virus scan of only critical areas of the computer: memory, startup objects, and system folders.
-
 Custom Scan.
Custom Scan.A virus scan of a specified object (file, folder, drive, or removable drive).
Each scan task is performed within a specified scan scope and is started manually. Malicious objects are recognized through signature analysis. In addition to signature analysis, Kaspersky Endpoint Security uses heuristic analysis and other scanning technologies.
Start Full Scan and Quick Scan tasks
- Open the main application window and click
 .
.The Virus Scan window opens.
- In the Virus Scan window, click the Full Scan or Quick Scan button.
The scan task starts.
Start a Custom Scan task
- Open the main application window and click
 .
.The Virus Scan window opens.
- To start the Custom Scan task, do one of the following:
- Drag a file or folder to the To scan files and folders, drag them onto this window pane.
- Click the Choose button and open a file or folder.
The scan task starts.
Stop a virus scan task
- Open the main application window and click
 .
.The Virus Scan window opens.
- In the Virus Scan window, click the Stop button next to the scan task that you want to stop.
The confirmation dialog opens.
- In the confirmation dialog, click the Stop button.
The scan task stops.
You can also configure the Full Scan and Quick Scan tasks to run automatically according to a specified schedule.
Configure Full Scan and Quick Scan schedule preferences
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Virus Scan tab, in the list on the left, select Full Scan or Quick Scan.
- In the Schedule section, select a checkbox corresponding to a configured schedule for the selected virus scan task.
- To change the virus scan task schedule, click the Schedule button.
A window opens, in which you can configure the virus scan task schedule.
- Specify the virus scan task launch frequency and time.
- Click the Save button to save changes made to the virus scan task schedule.
The Full Scan and Quick Scan tasks already contain scan scopes. While performing the Full Scan task, Kaspersky Endpoint Security scans memory, startup objects, and all internal drives of the computer. While performing the Quick Scan task, Kaspersky Endpoint Security scans computer memory, startup objects, and system folders. You can change the scan scope of the Full Scan and Quick Scan tasks.
Add/remove a file or folder to/from the scan scopes of the Full Scan and Quick Scan tasks
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Virus Scan tab, in the list on the left, select the Full Scan or Quick Scan task.
- In the Scan scope section, click the Edit button.
A window with the list of Full Scan or Quick Scan task scan scope objects opens.
- Edit the list of scan scope objects:
- To add a file or folder to the scan scope:
- Click the
 button.
button.A drop-down list where you can select objects to add to the scan scope opens.
- In the drop-down list, choose the File or Folder item.
A dialog where you can select a file or folder opens.
- Select a file or folder that you want to add to the scan scope.
- Click the Open button.
- To remove a file or folder from the scan scope:
- Select an object that you want to remove.
- Drag the selected object from the window or click the
 button.
button.
- Click the Save button.
Add an object from the default list of Full Scan and Quick Scan objects to the scan scope
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button. The application preferences window opens.
- On the Virus Scan tab, in the list on the left, select the Full Scan or Quick Scan task.
- In the Scan scope section, click the Edit button.
A window with the list of objects in the scan scope opens.
- Click the
 button.
button.A drop-down list where you can select objects to add to the scan scope opens.
- In the drop-down list, select an object that you want to add to the scan scope (for example, Memory).
- Click the OK button.
Disable protection of an object in the Full Scan or Quick Scan task scan scope
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button. The application preferences window opens.
- On the Virus Scan tab, in the list on the left, select the Full Scan or Quick Scan task.
- In the Scan scope section, click the Edit button.
A window with the list of scan scope objects opens.
- Deselect the checkbox next to the object in the list of scan scope objects.
- Click the OK button.
For each scan task you can choose one of the preset security levels:
- Maximum protection – a security level ensuring a full scan of the entire computer or individual disks, folders, or files. This security level is recommended when you suspect that the computer is infected.
- Recommended – a security level with the preferences recommended by Kaspersky Lab.
- Maximum speed – this security level enables you to use other applications that require significant system resources, since the scope of files scanned at this security level is smaller.
By default, virus scan tasks are performed at the Recommended security level. You can increase or decrease the thoroughness of the scan by selecting Maximum protection or Maximum speed, respectively. You can also edit the preferences of the current security level. This will change the name of the security level to Custom.
Select the security level
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Virus Scan tab, select the name of the virus scan task in the task list on the left.
- In the Security level section, move the slider to the required position.
Changing the security level changes the balance between scan speed and the total number of files scanned: the fewer files scanned for viruses, the higher the scan speed.
Edit the preferences of the current security level
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button. The application preferences window opens.
- On the Virus Scan tab in the application preferences window, select the name of the virus scan task in the task list on the left.
- In the Security level section, click the Preferences button.
A window opens, in which you can edit the preferences of the current security level.
- In the window that opens, edit the security level preferences:
- In the File types section, select the types of files that should be scanned by Kaspersky Endpoint Security when running the virus scan task.
- In the Optimization section, select or deselect checkboxes and specify the relevant values in the entry fields to configure the preferences for scan performance and use of iSwift technology.
- In the Compound files section, select or deselect checkboxes next to the types of compound files to be scanned.
- In the Heuristic analyzer section, select or deselect the Use Heuristic Analyzer checkbox. If the checkbox is selected, move the slider up or down the scale to select the level of heuristic analysis during virus scan tasks.
- Click OK to save changes made to the security level preferences.
Restore default scan preferences
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Virus Scan tab in the application preferences window, select the name of the virus scan task in the task list on the left.
- In the Security level section, click the Default button.
This restores the recommended virus scan task preferences. The name of the security level changes to Recommended.
Upon detecting an infected object, the application displays a notification prompting the user to select the action to be taken on the object. You can modify the action to perform when an object is detected.
If a threat is detected in a file, Kaspersky Endpoint Security identifies the type of the detected malicious program (for example, virus or Trojan).
Select the action to take on objects during scanning
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Virus Scan tab, select the name of the virus scan task in the task list on the left.
- In the Action section, select the action for Kaspersky Endpoint Security to perform on the detected malicious object.
Before disinfecting or deleting an infected file, Kaspersky Endpoint Security saves a copy of it in Backup so you can restore the original file, if necessary.
Information about the results of virus scan tasks and all detected objects is logged in a virus scan task report.
View the virus scan task report
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- In the reports window that opens, in the Tasks section, select Virus Scan.
Note: If any errors occur while running a virus scan task, start the task again. If the new attempt to run the scan also results in an error, contact Kaspersky Lab Technical Support.
[Topic kes58390]
Update tasks
Timely updates of application databases ensure that your computer remains protected. File Anti-Virus, Web Anti-Virus and virus scan tasks use application databases to detect and neutralize malware on your computer. Application databases are updated regularly with new threats and ways to neutralize them, so it is important that you update the databases.
By default, Kaspersky Endpoint Security downloads application databases and new application modules from Kaspersky Lab update servers and installs them on your computer.
Start an application database update
Dedicated Kaspersky Lab update servers are the main source of updates for Kaspersky Endpoint Security. You can also use Kaspersky Security Center servers, local folders, or other web servers as an update source.
Select an update source
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Application section, click the Preferences button.
A window opens, in which you can select the update sources.
- On the Update sources tab, select the checkboxes next to the update sources that you want to use.
Note: By default, the list of update sources contains only Kaspersky Lab update servers and Kaspersky Security Center servers. When running an update, Kaspersky Endpoint Security refers to the list of update sources for the address of the first server and attempts to download the updates from this server. If the updates cannot be downloaded from the selected server, the application tries to connect and retrieve the updates from the next server. This continues until a connection is successfully established or all the available update servers have been tried. For subsequent updates the application first tries to access the server from which the most recent update was successfully made.
You can perform the following actions:
- Add a new update source to the list.
Click the
 button and select the most suitable option from the dropdown list:
button and select the most suitable option from the dropdown list:
- To add a local or network folder as an update source, select Add folder. Select the required folder in the Finder window that opens.
- To add a web resource as an update source, select Add web address. In the window that opens, enter the server's web address in the Web address of update source field.
- Change the update source.
Select an update source in the list by double-clicking and make changes.
Note: Kaspersky Lab update servers and Kaspersky Security Center servers are update sources that cannot be edited or deleted.
- Temporarily disable retrieval of updates from the source.
Deselect the checkbox next to an update source that you want to disable. Kaspersky Endpoint Security will not be updated from this source until the checkbox is selected again.
- Delete an update source (available only for update sources added by the user).
Select the update source in the list and click the
 button.
button.
- Click the Save button to save the changes made to the update preferences.
Note: An Internet connection is required to download an update package from update servers. If you connect to the Internet via a proxy server, you may need to configure the network preferences.
Application database updates can be downloaded in one of the following modes:
- Automatically. Kaspersky Endpoint Security periodically checks for updates on Kaspersky Lab update servers. During a virus outbreak the frequency of these checks may increase and then decrease afterwards. If a set of the latest updates is stored on a server, Kaspersky Endpoint Security downloads them in the background and installs them on your computer. This is the default update mode.
- Manually. In this case, you start updates of Kaspersky Endpoint Security manually.
- By schedule. Kaspersky Endpoint Security is automatically updated according to a schedule.
By default, Kaspersky Endpoint Security module updates are downloaded and installed on the computer automatically.
Select the Kaspersky Endpoint Security update mode
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Application databases section, select one of the options:
- If you want anti-virus databases and application modules to be automatically downloaded from Kaspersky Lab update servers and installed, select the Download updates automatically option.
- To start the application update process manually, select the Download updates manually option.
- If you want the application update to start automatically according to a schedule you specify, select the option corresponding to the update schedule.
Configure a Kaspersky Endpoint Security update schedule
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Application databases section, select the option corresponding to a configured application update schedule.
- Click the Schedule button.
A window opens, in which you can configure the update schedule.
- Specify the application update frequency and time.
- Click the Save button to save changes made to the application update startup schedule.
During an update the application databases and modules are compared with those currently available at the update source. If the latest version of the databases is installed on your computer, the Update window or Protection Center display a message to inform you that the application databases are up-to-date. If the application version and application databases differ from those currently available from the update source, then only the missing update components are installed on your computer. Application databases are not copied in their entirety, which increases update speed and reduces Internet traffic.
Disable automatic download and installation of updates of application modules on the computer
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Application section, deselect the Update application modules checkbox.
Note: If at the time of the update both application databases updates and application modules updates are available from the update source, Kaspersky Endpoint Security downloads the application module updates and installs them after the computer is restarted. The downloaded application module updates are not installed until the computer restarts. If the next application update becomes available on Kaspersky Lab servers before the computer is restarted and before the previously downloaded application module updates are installed, then Kaspersky Endpoint Security only updates the application databases.
If you connect to the Internet via a proxy server, you can configure the proxy server connection preferences. Kaspersky Endpoint Security uses these preferences to update application databases and download application module updates.
Configure a connection to a proxy server
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Proxy section, select the Use proxy server checkbox and click the Preferences button.
A window opens, in which you can configure the proxy server connection preferences.
- Configure the connection to a proxy server.
- Click the Save button to save the changes made to the proxy server connection preferences.
Before updating the application databases Kaspersky Endpoint Security creates backup copies of them so a rollback can be performed, if necessary. The rollback feature is useful if a new version of the application databases contains an incorrect signature that makes Kaspersky Endpoint Security block a safe application.
Note: If Kaspersky Endpoint Security databases become corrupted, you are advised to start an update to download and install the latest version of application databases.
Roll back the last update
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Rollback section, click the Roll Back Update button.
While updating Kaspersky Endpoint Security you can copy the downloaded updates to a local source. You can use a local copy of downloaded updates to update application databases and modules of Kaspersky Endpoint Security on other computers on the corporate network in order to reduce the amount of Internet traffic.
You can set up update distribution as follows:
- One of the computers on the network receives the Kaspersky Endpoint Security update package from Kaspersky Lab update servers or a different update source. The updates retrieved are placed in a shared folder.
Note: The shared folder must be created in advance.
- Other computers on the network refer to the shared folder as the update source.
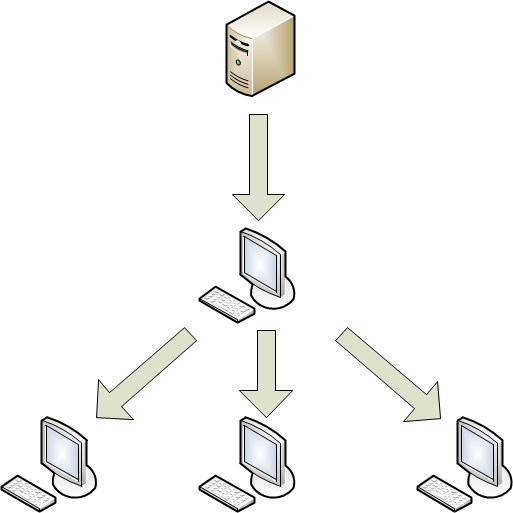
Distribution of updates via a local computer
Enable copying of updates to a local folder
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- Select the Update tab.
- In the Application section, click the Preferences button.
A window opens, in which you can enable copying of updates to a local folder.
- On the Advanced tab, select the Copy update files to folder checkbox and click the Select button.
The Finder window opens.
- In the Finder window, select a shared folder to which Kaspersky Endpoint Security will save the updates.
- Click the Save button to save the changes made to the update preferences.
Information about the progress of the current update task (percent complete) is shown in the lower part of the Update window and also in the main application window and in Protection Center.
Detailed information about the results of the Update task is logged in the update task report.
View the update task report
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- In the Tasks section, select the Update task.
[Topic kes58397]
Backup
Sometimes the integrity of infected files cannot be preserved during the disinfection process. If a disinfected file contained important information that is partly or completely inaccessible following disinfection, you can restore the original file from Backup.
A backup copy is a copy of a dangerous file that is created when the file is disinfected or deleted. It is stored in Backup.
Backup is a special storage area that contains backup copies of files that have been deleted or modified during disinfection. The main function of Backup is enabling the user to restore an original file at any time. Files in Backup are saved in a special format and are not dangerous for the computer.
View the contents of Backup
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- In the left pane of the Reports window, select Backup.
The list of backed up files is displayed in the right pane of the window.
You can restore or remove backup copies of files from Backup.
Restore a backup copy of a file from Backup
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- In the left pane of the Reports window, select Backup.
The list of backed up files is displayed in the right pane of the window.
- In the list, select the backup copy of the file you want to restore and click the Restore button.
A window for specifying the file name, tag, and folder to which the file will be restored opens. By default, the original file name and location are already specified.
- Specify the file name and folder to which the file will be restored.
- Click the Save button.
The application restores the file to the specified location with the specified name.
You need to scan the file for viruses immediately after restoring it. It is possible that the object can be disinfected using updated databases without becoming corrupted.
Important: It is not recommended that you restore backup copies of files unless restoring is absolutely necessary, because doing so could lead to an infection of your computer.
Remove a backup copy of a file from Backup
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- In the left pane of the Reports window, select Backup.
The list of backed up files is displayed in the right pane of the window.
- Select the backup copies you want to delete in the list of backup copies:
- To delete one or more backup copies of files, select the backup copies you want to delete and click the Delete button.
- To delete all backup copies, click the Delete All button.
By default, the storage term for files in Backup is 30 days. When this term expires the files are deleted. You can change the maximum Backup storage period for files or remove the limit on the storage period.
Configure the storage period for files in Backup
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Reports tab, in the Backup section, select the Delete objects after <number> days checkbox and specify the time period after which files stored in Backup are automatically deleted.
[Topic kes59231]
Reports
You can view a Kaspersky Endpoint Security report listing all detected objects. Additionally, a separate detailed report is created for each of the following application components: File Anti-Virus, Web Anti-Virus, Network Attack Blocker, virus scan and update tasks.
Open the Reports window
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
Kaspersky Endpoint Security can save reports in text format. This functionality may be useful if File Anti-Virus, Web Anti-Virus, Network Attack Blocker, a virus scan task, or the update task results in an error that you can't fix on your own and you need assistance from Kaspersky Lab Technical Support. In this case, send a text report to Kaspersky Lab Technical Support so our specialists can study the problem and fix it as quickly as possible.
Export a report on a Kaspersky Endpoint Security component or task to a text file
- Open the main application window.
- On the navigation panel in the upper part of the main application window, click the
 button.
button.The Reports window opens.
- In the left pane of the reports window, select the required report tab.
- In the lower-left corner, click the Export button.
- In the window that opens, specify the file name, tags, and destination folder for the report.
- Click the Save button.
By default, Kaspersky Endpoint Security doesn't log informational events in reports. You can allow logging of informational events.
Enable logging of informational events in reports
- Open the main application window.
- On the navigation panel in the upper pane of the main application window, click the
 button.
button.The application preferences window opens.
- On the Reports tab, in the Reports section, select the Log non-critical events checkbox.
[Topic kes59232]
FileVault disk encryption
Note: The FileVault disk encryption feature will be available in Kaspersky Security Center 10 SP3. For more information, contact Kaspersky Lab Technical Support.
Kaspersky Endpoint Security allows managing FileVault encryption remotely. Encryption prevents other users from unauthorized access to sensitive data stored on the startup disk of the user's computer.
When an administrator starts FileVault encryption of a computer from Kaspersky Security Center, Kaspersky Endpoint Security prompts a user of this computer to enter his or her credentials. Disk encryption only starts after the user provides the credentials and the computer is restarted.
Note: If FileVault encryption management isn't enabled in Kaspersky Security Center, users with administrator rights can encrypt and decrypt their Mac startup disks from System Preferences. For more information on FileVault, refer to Apple's documentation.
If the computer has multiple computer accounts, FileVault encryption makes the disk inaccessible to all users except for the user who entered the credentials.
Allow other users to unlock the disk
- Choose Apple menu > System Preferences, then click Security&Privacy.
- On the FileVault tab, at the bottom of the window, click the lock.
- In the prompt for administrator credentials, enter the user name and password.
- Click the Enable Users button.
- In the window that opens, select a user to authorize to unlock the computer and click the Enable User button next to his or her name.
- In the window that opens, enter the password of the user's computer account and click the OK button.
- Click the Done button.
The user can access the encrypted disk.
Note: Administrator rights are required to allow other users to unlock the disk.
Page top
[Topic kes159877] Full Scan.
Full Scan. Quick Scan.
Quick Scan. Custom Scan.
Custom Scan.



