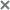Viewing the table of hosts with the Endpoint Agent component
To view the table of hosts with the Endpoint Agent component:
- Select the Assets section in the application web interface window.
- Go to the Endpoint Agents tab.
The table of hosts with the Endpoint Agent component is displayed.
If you are using the
and , the table contains information about hosts with the Endpoint Agent component connected to the PCN and all SCN servers.The table can display the following data:
- Number of hosts and activity indicators of the Endpoint Agent component:
- Critical inactivity is the number of hosts from which latest data was received a very long time ago.
- Warning is the number hosts from which latest data was received a long time ago.
- Normal activity is the number of hosts from which latest data was recently received.
- Host—Name of the host with the Endpoint Agent component.
- Servers is the name of the server to which the host with the Endpoint Agent component is connected.
This field is displayed if you are using the distributed solution and multitenancy mode.
- IP is the IP address of the host where the Endpoint Agent component is installed.
- OS is the version of the operating system that is installed on the host with the Endpoint Agent component.
- Version—Version of the Endpoint Agent component installed.
- Activity—Activity indicator of the Endpoint Agent component.
- Normal activity for hosts from which latest data was recently received.
- Warning for hosts from which latest data was received a long time ago.
- Critical inactivity for hosts from which latest data was received an extremely long time ago.
- Last connection for the date and time of the last connection of the Endpoint Agent component to the Central Node server.
Clicking the link with the host name opens a list in which you can select one of the following actions:
- Filter by this value.
- Exclude from filter.
- Run the following tasks:
- Kill process.
- Delete file.
- Kill by unique PID.
- Get file.
- Get forensics.
- Quarantine file.
- Run application.
- New prevention rule.
- Isolate from network.
- Find events.
- Find alerts.
- Copy value to clipboard.
The list of available actions depends on the type of Endpoint Agent component: for Windows, Linux, or Mac (for details, see the Operating principle of the application section).
Clicking the link with the IP opens a list in which you can select one of the following actions:
- Filter by this value.
- Exclude from filter.
- Find alerts.
- Copy value to clipboard.
If you are using only KATA functionality (the KATA key), the following actions are available in the list that is displayed by clicking the host name link:
- Find alerts (displayed for users with the Senior security officer role).
- Filter by this value.
- Exclude from filter.
- Copy value to clipboard.
Clicking a link in any other column of the table opens a list in which you can select one of the following actions:
- Filter by this value.
- Exclude from filter.
- Copy value to clipboard.